一道不常见的 aarch64 kernel pwn,这题很简单就简单栈溢出,msr 返回用户态 orw 即可
但就是返回用户态的机制不太好了解,然后流程控制也跟常规的 x86 那种有很大区别
device_read 函数
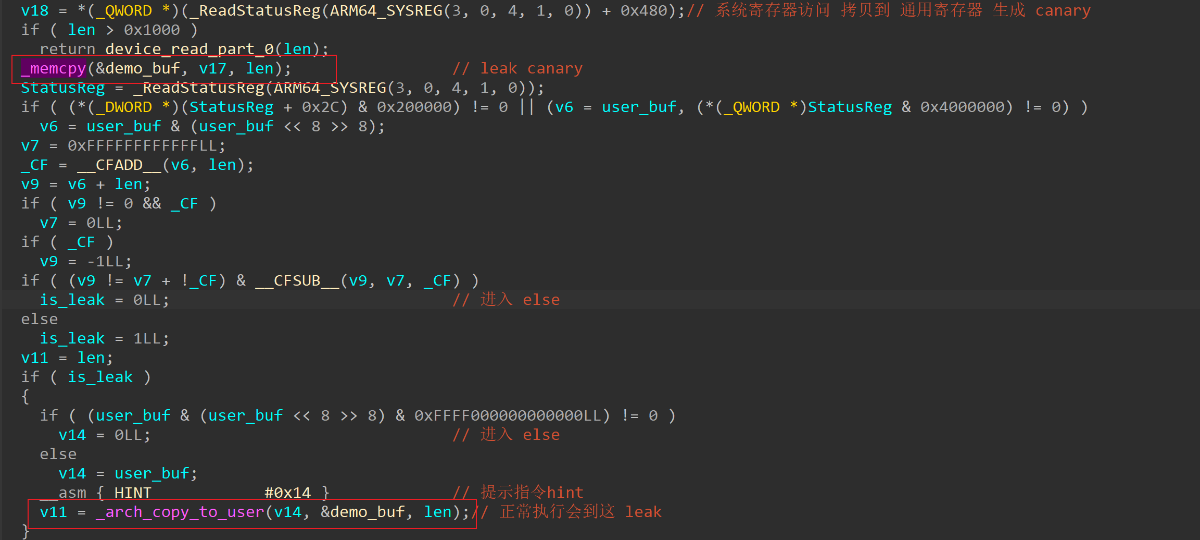
device_write 函数
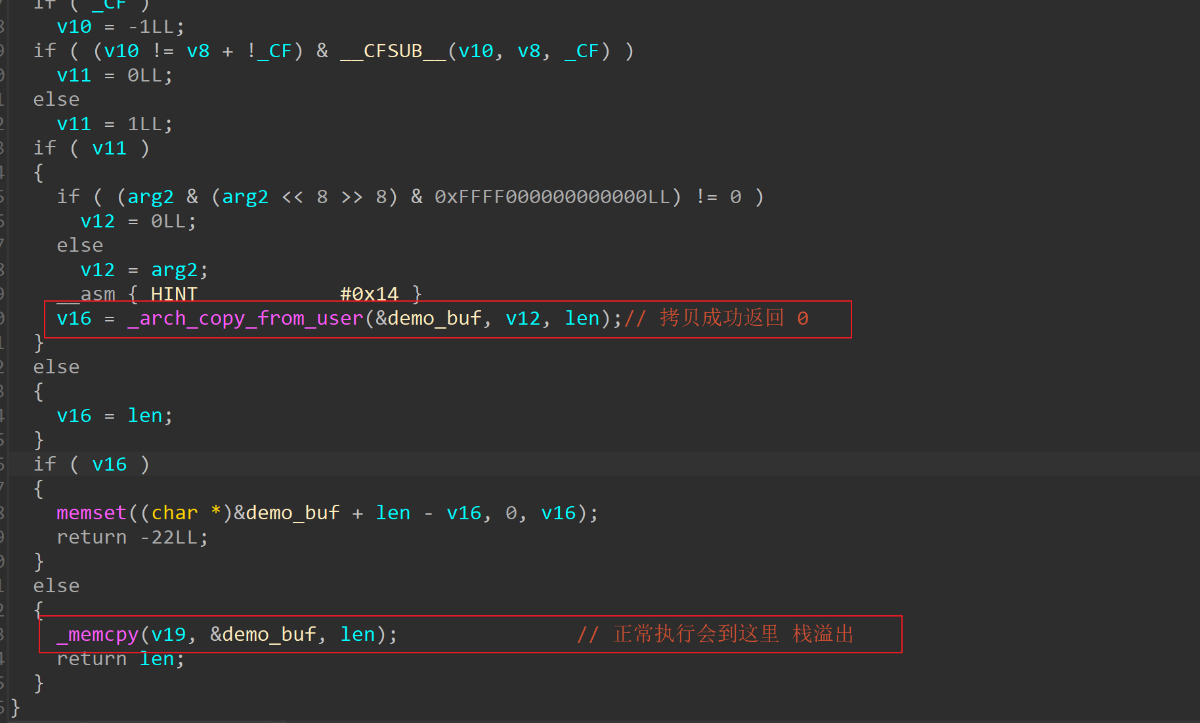
存在栈溢出漏洞
审一下代码就可以知道,红色框框中的东西一定会进,read 用来 leak,write 用来 rop
其实不怎么审代码,下好断点调试也可以知道进入哪里
vmlinux 从镜像中拉出来地址全是乱的。。。
gadgets 可以通过调试去找,直接在 gdb 里面找,还好这题 rop 不复杂,不然痛苦死了
但这个方法也不好,后面发现这个 aarch64 的 Image 文件可以直接 ida,但是只有偏移地址,但没关系
这题没开 kaslr,直接查内核基址再加上偏移就可以了
然后说说 aarch64 的一些简单的汇编指令和知识
寻址格式,# 代表立即数
寄存器
在 aarch64 汇编中寄存器是 64 位的,使用 X[n] 表示,低32 位以 W[n] 表示
在 64 位架构中有 31 个 64 位的通用寄存器
使用如下指令在 pwndbg 中查看
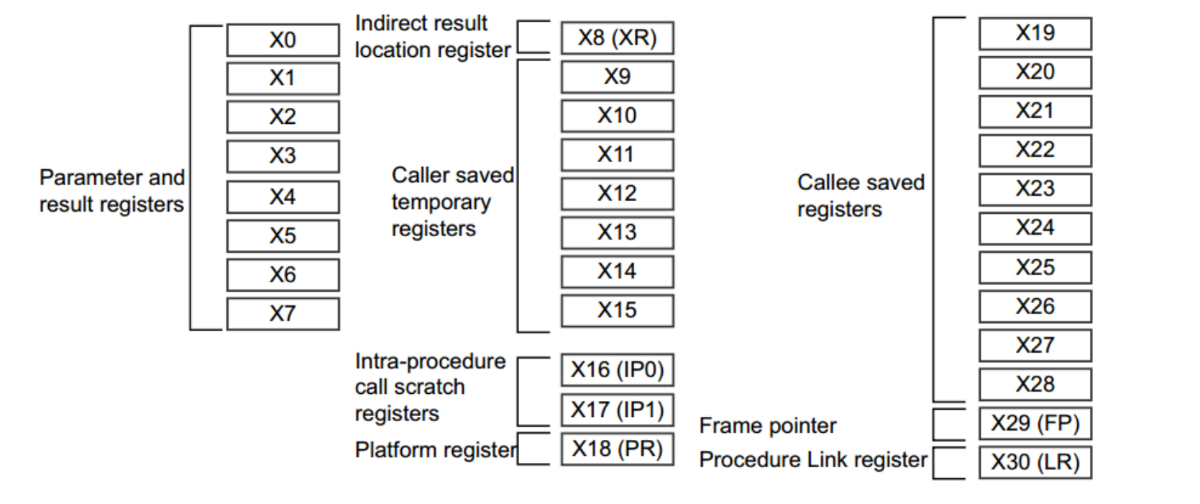
x0~x7:一般是函数的参数,大于8个的会通过堆栈传参
x0 还用作返回值
X9-X15:调用者保存的临时寄存器
X19-X29:被调用者保存的寄存器
关于 aarch64 架构下的开辟栈帧
x86 下一般是 push、pop 指令
而 aarch 64 下就是 LDP、STP 指令
例如:
关于返回用户态
使用 gdb 单步调试可以找到如下 gadgets,也就是利用 msr 指令进行寄存器的恢复
msr 指令会分别将 x21、x22、x23 的值还原给上面三个重要寄存器
所以伪造这三个值即可返回用户态
先改一下 init 文件
注释掉 cd /home/pwn,是为了运行 exp 更方便,不然还得 cd 一下才能运行 exp
这两条指令
这使得普通用户无法查看 dmesg 和 kallsyms 中的值(kallsyms 中显示会全部为 0)
主要影响的是查看与 moudle 相关的调试信息,也就是在 /sys/moudle/core/section 查看地址会受到限制
还有就是会造成无法直接通过 /proc/kallsyms 来进行 leak kernel 基址
所以直接设置了 root 权限,方便本地调试,root 可以直接查看地址
改动如下
启动脚本
我把下面这条注释了,不然调试一段时间会自动退出
编译的话,先要装个工具链
https://releases.linaro.org/components/toolchain/binaries/latest-7/aarch64-linux-gnu/
这个网站下载压缩包即可
交叉编译 aarch64
或者是直接装交叉编译环境
利用思路:
根据 aarch64 的特点,我们需要控制 x30(返回地址),x0(第一个参数),然后 ret 即可,ret 不会改变 sp,这跟 x86 也是不一样的
我用到的三个 gadgets
因为 x0 寄存器用作第一个参数,所以找了个有 MOV W0, #0 的 gadgets,w0 只是 X0的 低三十二位,因为高三十二位本来就是 0
然后 commit_creds 和 prepare_kernel_cred 的地址都加了四,为了跳过 stp 指令对 x30 寄存器的修改,也就是下面这条
这样才方便我们伪造 x30 方便后续 rop 的利用
构造 rop 的时候,要注意 sp 的变化,建议是多写一些 0xaaaaaaaaaaaaaaaa 这样的数据进去,方便调试,调试完再做替换即可,还有就是可以直接写 0xaaaaaaaa...0xbbbbbb...,这样的东西,写多一些,然后看错误回显,看看执行了哪个地址,比如错误回显提示 call:0xaaaaaaaaaaaaaaaa,那就可以将 0xaaaaaaaaaaaaaaaa 替换为我们要执行的地址,这样很快很方便
grep demo /proc/modules
grep "0x" /sys/module/demo/sections/.*
grep prepare_kernel_cred /proc/kallsyms
grep commit_creds /proc/kallsyms
grep _text /proc/kallsyms
grep demo /proc/modules
grep "0x" /sys/module/demo/sections/.*
grep prepare_kernel_cred /proc/kallsyms
grep commit_creds /proc/kallsyms
grep _text /proc/kallsyms
[sp,
[sp,
[sp],
pwndbg> i reg
x0 0x0 0
x1 0x0 0
x2 0x8 8
x3 0x20 32
x4 0xffffffffffffffe0 -32
x5 0x40 64
x6 0x3f 63
x7 0x0 0
x8 0xffff000002eaebe8 -281474927760408
x9 0x0 0
x10 0x0 0
x11 0x0 0
x12 0x438614 4425236
x13 0x60001000 1610616832
x14 0x1200011 18874385
x15 0xdc 220
x16 0x0 0
x17 0x0 0
x18 0xcfab 53163
x19 0xffff000002ead100 -281474927767296
x20 0xffff80000a2b3da0 -140737317749344
x21 0x1200000 18874368
x22 0x0 0
x23 0xffff80000a2b8000 -140737317732352
x24 0xffff80000a2bbeb0 -140737317716304
x25 0x0 0
x26 0xffff000002eae480 -281474927762304
x27 0xffff80000a0417e0 -140737320314912
x28 0xffff000002eade80 -281474927763840
x29 0xffff80000a2b3bc0 -140737317749824
x30 0xffff800008016950 -140737354045104
sp 0xffff80000a2b3bc0 0xffff80000a2b3bc0
pc 0xffff800008016958 0xffff800008016958
cpsr 0x5 5
fpsr 0x0 0
fpcr 0x0 0
MVFR6_EL1_RESERVED 0x0 0
MVFR7_EL1_RESERVED 0x0 0
MAIR_EL3 0x0 0
ID_AA64PFR1_EL1 0x1 1
ID_AA64PFR2_EL1_RESERVED 0x0 0
ID_AA64PFR3_EL1_RESERVED 0x0 0
SCTLR 0x200002034f4d91d 144115326403270941
ID_AA64ZFR0_EL1 0x0 0
CNTKCTL 0xc6 198
DACR32_EL2 0x0 0
ID_AA64PFR5_EL1_RESERVED 0x0 0
ACTLR_EL1 0x0 0
CPACR 0x300000 3145728
ID_AA64PFR6_EL1_RESERVED 0x0 0
FPEXC32_EL2 0x0 0
ID_AA64PFR7_EL1_RESERVED 0x0 0
ID_AA64DFR0_EL1 0x10305106 271601926
ID_AA64DFR1_EL1 0x0 0
ID_AA64DFR2_EL1_RESERVED 0x0 0
ID_AA64DFR3_EL1_RESERVED 0x0 0
ID_AA64AFR0_EL1 0x0 0
ID_AA64AFR1_EL1 0x0 0
ID_AA64AFR2_EL1_RESERVED 0x0 0
CNTFRQ_EL0 0x3b9aca0 62500000
ID_AA64AFR3_EL1_RESERVED 0x0 0
SPSR_EL1 0x60001000 1610616832
ID_AA64ISAR0_EL1 0x1021111110212120 1162228943821021472
DBGBVR 0x0 0
ELR_EL1 0x438614 4425236
ID_AA64ISAR1_EL1 0x11101011010 1172542918672
PMEVTYPER0_EL0 0x0 0
DBGBCR 0x0 0
ID_AA64ISAR2_EL1_RESERVED 0x0 0
PMEVTYPER1_EL0 0x0 0
DBGWVR 0x0 0
ID_AA64ISAR3_EL1_RESERVED 0x0 0
ZCR_EL1 0x0 0
DBGWCR 0x0 0
RVBAR_EL1 0x0 0
ID_AA64ISAR4_EL1_RESERVED 0x0 0
PMEVTYPER2_EL0 0x0 0
PMEVTYPER3_EL0 0x0 0
MDCCSR_EL0 0x1000 4096
ID_AA64ISAR5_EL1_RESERVED 0x0 0
ID_AA64ISAR6_EL1_RESERVED 0x0 0
ID_AA64ISAR7_EL1_RESERVED 0x0 0
SP_EL0 0xffff000002ead100 -281474927767296
ID_AA64MMFR0_EL1 0x1124 4388
DBGBVR 0x0 0
ID_AA64MMFR1_EL1 0x11000 69632
DBGBCR 0x0 0
ID_AA64MMFR2_EL1_RESERVED 0x0 0
PMINTENSET_EL1 0x0 0
DBGWVR 0x0 0
ID_AA64MMFR3_EL1_RESERVED 0x0 0
PMINTENCLR_EL1 0x0 0
DBGWCR 0x0 0
ID_AA64MMFR4_EL1_RESERVED 0x0 0
PMCNTENSET_EL0 0x0 0
ACTLR_EL2 0x0 0
PMCR_EL0 0x2000 8192
ID_AA64MMFR5_EL1_RESERVED 0x0 0
PMCNTENCLR_EL0 0x0 0
VBAR 0xffff800008010800 -140737354070016
ID_AA64MMFR6_EL1_RESERVED 0x0 0
PMOVSCLR_EL0 0x0 0
MDSCR_EL1 0x1000 4096
ID_AA64MMFR7_EL1_RESERVED 0x0 0
CNTP_CTL_EL0 0x0 0
PMSELR_EL0 0x0 0
CNTP_CVAL_EL0 0x0 0
DBGBVR 0x0 0
DBGBCR 0x0 0
PMCEID1_EL0 0x0 0
PMCEID0_EL0 0x20001 131073
DBGWVR 0x0 0
PMCCNTR_EL0 0x0 0
DBGWCR 0x0 0
L2ACTLR 0x0 0
TTBR0_EL1 0x42eca000 1122803712
TTBR1_EL1 0x280000418b0000 11259000168054784
CNTV_CTL_EL0 0x1 1
TCR_EL1 0x400034b5503510 18014624889713936
DBGBVR 0x0 0
DBGBCR 0x0 0
ACTLR_EL3 0x0 0
CNTV_CVAL_EL0 0x2aff26ff 721364735
DBGWVR 0x0 0
ZCR_EL2 0x0 0
PMUSERENR_EL0 0x0 0
DBGWCR 0x0 0
PMOVSSET_EL0 0x0 0
APIAKEYLO_EL1 0x0 0
APIAKEYHI_EL1 0x0 0
SP_EL1 0xffff80000a2b4000 -140737317748736
MDRAR_EL1 0x0 0
APIBKEYLO_EL1 0x0 0
PMCCFILTR_EL0 0x0 0
DBGBVR 0x0 0
APIBKEYHI_EL1 0x0 0
DBGBCR 0x0 0
CPUACTLR_EL1 0x0 0
CPUECTLR_EL1 0x0 0
CONTEXTIDR_EL1 0x0 0
APDAKEYLO_EL1 0x0 0
APDAKEYHI_EL1 0x0 0
CNTPS_CTL_EL1 0x0 0
CPUMERRSR_EL1 0x0 0
CNTPS_CVAL_EL1 0x0 0
L2MERRSR_EL1 0x0 0
DBGBVR 0x0 0
APDBKEYLO_EL1 0x0 0
MAIR_EL1 0x40044ffff 17184391167
APDBKEYHI_EL1 0x0 0
DBGBCR 0x0 0
TPIDR_EL1 0xffff80000673f000 -140737380093952
AFSR0_EL1 0x0 0
OSLSR_EL1 0x8 8
AFSR1_EL1 0x0 0
PAR_EL1 0x0 0
CBAR_EL1 0x8000000 134217728
APGAKEYLO_EL1 0x0 0
APGAKEYHI_EL1 0x0 0
SPSR_IRQ 0x0 0
MDCR_EL3 0x0 0
SPSR_ABT 0x0 0
AMAIR0 0x0 0
FPCR 0x0 0
SPSR_UND 0x0 0
SPSR_FIQ 0x0 0
FPSR 0x0 0
ESR_EL1 0x56000000 1442840576
CLIDR 0xa200023 169869347
REVIDR_EL1 0x0 0
ID_PFR0 0x131 305
ID_DFR0 0x3010066 50397286
ID_AFR0 0x0 0
ID_MMFR0 0x10101105 269488389
CSSELR 0x0 0
LORSA_EL1 0x0 0
ID_MMFR1 0x40000000 1073741824
AIDR 0x0 0
TPIDR_EL0 0x11439700 289642240
LOREA_EL1 0x0 0
ID_MMFR2 0x1260000 19267584
TPIDRRO_EL0 0x0 0
LORN_EL1 0x0 0
ID_MMFR3 0x2102211 34611729
IFSR32_EL2 0x0 0
LORC_EL1 0x0 0
ID_ISAR0 0x2101110 34607376
ID_ISAR1 0x13112111 319889681
PMEVCNTR0_EL0 0x0 0
ID_ISAR2 0x21232042 555950146
PMEVCNTR1_EL0 0x0 0
ID_ISAR3 0x1112131 17899825
CTR_EL0 0x8444c004 2219098116
LORID_EL1 0x0 0
PMEVCNTR2_EL0 0x0 0
ID_ISAR4 0x11142 69954
PMEVCNTR3_EL0 0x0 0
ID_ISAR5 0x11011121 285282593
ID_MMFR4 0x0 0
ID_ISAR6 0x11111 69905
L2CTLR_EL1 0x0 0
MVFR0_EL1 0x10110222 269550114
L2ECTLR_EL1 0x0 0
FAR_EL1 0xffffce1148b0 281474138982576
MVFR1_EL1 0x12111111 303108369
MVFR2_EL1 0x43 67
MVFR3_EL1_RESERVED 0x0 0
MVFR4_EL1_RESERVED 0x0 0
MVFR5_EL1_RESERVED 0x0 0
pwndbg> i reg
x0 0x0 0
x1 0x0 0
x2 0x8 8
x3 0x20 32
x4 0xffffffffffffffe0 -32
x5 0x40 64
x6 0x3f 63
x7 0x0 0
x8 0xffff000002eaebe8 -281474927760408
x9 0x0 0
x10 0x0 0
x11 0x0 0
x12 0x438614 4425236
x13 0x60001000 1610616832
x14 0x1200011 18874385
x15 0xdc 220
x16 0x0 0
x17 0x0 0
x18 0xcfab 53163
x19 0xffff000002ead100 -281474927767296
x20 0xffff80000a2b3da0 -140737317749344
x21 0x1200000 18874368
x22 0x0 0
x23 0xffff80000a2b8000 -140737317732352
x24 0xffff80000a2bbeb0 -140737317716304
x25 0x0 0
x26 0xffff000002eae480 -281474927762304
x27 0xffff80000a0417e0 -140737320314912
x28 0xffff000002eade80 -281474927763840
x29 0xffff80000a2b3bc0 -140737317749824
x30 0xffff800008016950 -140737354045104
sp 0xffff80000a2b3bc0 0xffff80000a2b3bc0
pc 0xffff800008016958 0xffff800008016958
cpsr 0x5 5
fpsr 0x0 0
fpcr 0x0 0
MVFR6_EL1_RESERVED 0x0 0
MVFR7_EL1_RESERVED 0x0 0
MAIR_EL3 0x0 0
ID_AA64PFR1_EL1 0x1 1
ID_AA64PFR2_EL1_RESERVED 0x0 0
ID_AA64PFR3_EL1_RESERVED 0x0 0
SCTLR 0x200002034f4d91d 144115326403270941
ID_AA64ZFR0_EL1 0x0 0
CNTKCTL 0xc6 198
DACR32_EL2 0x0 0
ID_AA64PFR5_EL1_RESERVED 0x0 0
ACTLR_EL1 0x0 0
CPACR 0x300000 3145728
ID_AA64PFR6_EL1_RESERVED 0x0 0
FPEXC32_EL2 0x0 0
ID_AA64PFR7_EL1_RESERVED 0x0 0
ID_AA64DFR0_EL1 0x10305106 271601926
ID_AA64DFR1_EL1 0x0 0
ID_AA64DFR2_EL1_RESERVED 0x0 0
ID_AA64DFR3_EL1_RESERVED 0x0 0
ID_AA64AFR0_EL1 0x0 0
ID_AA64AFR1_EL1 0x0 0
ID_AA64AFR2_EL1_RESERVED 0x0 0
CNTFRQ_EL0 0x3b9aca0 62500000
ID_AA64AFR3_EL1_RESERVED 0x0 0
SPSR_EL1 0x60001000 1610616832
ID_AA64ISAR0_EL1 0x1021111110212120 1162228943821021472
DBGBVR 0x0 0
ELR_EL1 0x438614 4425236
ID_AA64ISAR1_EL1 0x11101011010 1172542918672
PMEVTYPER0_EL0 0x0 0
DBGBCR 0x0 0
ID_AA64ISAR2_EL1_RESERVED 0x0 0
PMEVTYPER1_EL0 0x0 0
DBGWVR 0x0 0
ID_AA64ISAR3_EL1_RESERVED 0x0 0
ZCR_EL1 0x0 0
DBGWCR 0x0 0
RVBAR_EL1 0x0 0
ID_AA64ISAR4_EL1_RESERVED 0x0 0
PMEVTYPER2_EL0 0x0 0
PMEVTYPER3_EL0 0x0 0
MDCCSR_EL0 0x1000 4096
ID_AA64ISAR5_EL1_RESERVED 0x0 0
ID_AA64ISAR6_EL1_RESERVED 0x0 0
ID_AA64ISAR7_EL1_RESERVED 0x0 0
SP_EL0 0xffff000002ead100 -281474927767296
ID_AA64MMFR0_EL1 0x1124 4388
DBGBVR 0x0 0
ID_AA64MMFR1_EL1 0x11000 69632
DBGBCR 0x0 0
ID_AA64MMFR2_EL1_RESERVED 0x0 0
PMINTENSET_EL1 0x0 0
DBGWVR 0x0 0
ID_AA64MMFR3_EL1_RESERVED 0x0 0
PMINTENCLR_EL1 0x0 0
DBGWCR 0x0 0
ID_AA64MMFR4_EL1_RESERVED 0x0 0
PMCNTENSET_EL0 0x0 0
ACTLR_EL2 0x0 0
PMCR_EL0 0x2000 8192
ID_AA64MMFR5_EL1_RESERVED 0x0 0
PMCNTENCLR_EL0 0x0 0
VBAR 0xffff800008010800 -140737354070016
ID_AA64MMFR6_EL1_RESERVED 0x0 0
PMOVSCLR_EL0 0x0 0
MDSCR_EL1 0x1000 4096
ID_AA64MMFR7_EL1_RESERVED 0x0 0
CNTP_CTL_EL0 0x0 0
PMSELR_EL0 0x0 0
CNTP_CVAL_EL0 0x0 0
DBGBVR 0x0 0
DBGBCR 0x0 0
PMCEID1_EL0 0x0 0
PMCEID0_EL0 0x20001 131073
DBGWVR 0x0 0
PMCCNTR_EL0 0x0 0
DBGWCR 0x0 0
L2ACTLR 0x0 0
TTBR0_EL1 0x42eca000 1122803712
TTBR1_EL1 0x280000418b0000 11259000168054784
CNTV_CTL_EL0 0x1 1
TCR_EL1 0x400034b5503510 18014624889713936
DBGBVR 0x0 0
DBGBCR 0x0 0
ACTLR_EL3 0x0 0
CNTV_CVAL_EL0 0x2aff26ff 721364735
DBGWVR 0x0 0
ZCR_EL2 0x0 0
PMUSERENR_EL0 0x0 0
DBGWCR 0x0 0
PMOVSSET_EL0 0x0 0
APIAKEYLO_EL1 0x0 0
APIAKEYHI_EL1 0x0 0
SP_EL1 0xffff80000a2b4000 -140737317748736
MDRAR_EL1 0x0 0
APIBKEYLO_EL1 0x0 0
PMCCFILTR_EL0 0x0 0
DBGBVR 0x0 0
APIBKEYHI_EL1 0x0 0
DBGBCR 0x0 0
CPUACTLR_EL1 0x0 0
CPUECTLR_EL1 0x0 0
CONTEXTIDR_EL1 0x0 0
APDAKEYLO_EL1 0x0 0
APDAKEYHI_EL1 0x0 0
CNTPS_CTL_EL1 0x0 0
CPUMERRSR_EL1 0x0 0
CNTPS_CVAL_EL1 0x0 0
L2MERRSR_EL1 0x0 0
DBGBVR 0x0 0
APDBKEYLO_EL1 0x0 0
MAIR_EL1 0x40044ffff 17184391167
APDBKEYHI_EL1 0x0 0
DBGBCR 0x0 0
TPIDR_EL1 0xffff80000673f000 -140737380093952
AFSR0_EL1 0x0 0
OSLSR_EL1 0x8 8
AFSR1_EL1 0x0 0
PAR_EL1 0x0 0
CBAR_EL1 0x8000000 134217728
APGAKEYLO_EL1 0x0 0
APGAKEYHI_EL1 0x0 0
SPSR_IRQ 0x0 0
MDCR_EL3 0x0 0
SPSR_ABT 0x0 0
AMAIR0 0x0 0
FPCR 0x0 0
SPSR_UND 0x0 0
SPSR_FIQ 0x0 0
FPSR 0x0 0
ESR_EL1 0x56000000 1442840576
CLIDR 0xa200023 169869347
REVIDR_EL1 0x0 0
ID_PFR0 0x131 305
ID_DFR0 0x3010066 50397286
ID_AFR0 0x0 0
ID_MMFR0 0x10101105 269488389
CSSELR 0x0 0
LORSA_EL1 0x0 0
ID_MMFR1 0x40000000 1073741824
AIDR 0x0 0
TPIDR_EL0 0x11439700 289642240
LOREA_EL1 0x0 0
ID_MMFR2 0x1260000 19267584
TPIDRRO_EL0 0x0 0
LORN_EL1 0x0 0
ID_MMFR3 0x2102211 34611729
IFSR32_EL2 0x0 0
LORC_EL1 0x0 0
ID_ISAR0 0x2101110 34607376
ID_ISAR1 0x13112111 319889681
PMEVCNTR0_EL0 0x0 0
ID_ISAR2 0x21232042 555950146
PMEVCNTR1_EL0 0x0 0
ID_ISAR3 0x1112131 17899825
CTR_EL0 0x8444c004 2219098116
LORID_EL1 0x0 0
PMEVCNTR2_EL0 0x0 0
ID_ISAR4 0x11142 69954
PMEVCNTR3_EL0 0x0 0
ID_ISAR5 0x11011121 285282593
[招生]科锐逆向工程师培训(2024年11月15日实地,远程教学同时开班, 第51期)
最后于 2022-5-19 21:05
被gxh1911编辑
,原因: 写错了