版本 : AX3000_Pro_V16.03.49.26
分析工具 : qiling
首先使用binwalk -E查看固件的熵,显然固件是经过了加密。
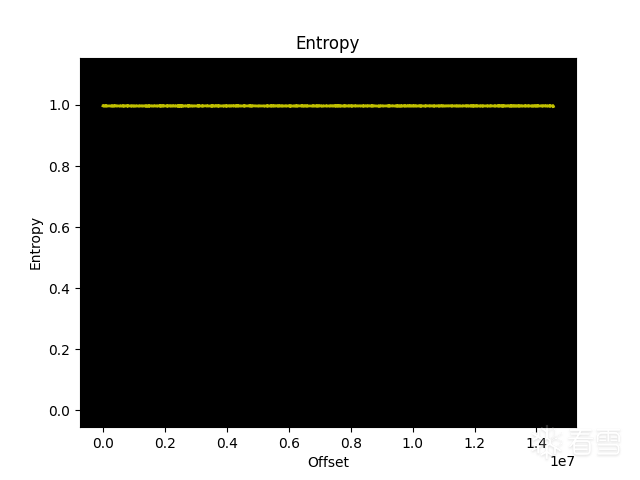
使用binwalk是无法分析的,但是使用在线binwalk竟然可以正常解压固件,于是把固件都下载下来进行分析,发现解密固件程序是decry_firm。
由于是aarch64程序,可以使用qiling进行模拟执行。固件的rootfs目录结构如下:
qiling代码如下:
运行完成后US_AX3000.Pro_V16.03.49.26_cn_JAX01.bin就解密了,本来是希望使用qiling的debugger功能来调试的,可能是由于调试程序不支持aarch64架构,没有调试成功。
使用IDA进行静态分析,调用流程还是非常简单的。
start()->sub_4056F8()->sub_4052FC()->sub_404E1C()
sub_4052FC()函数代码如下:
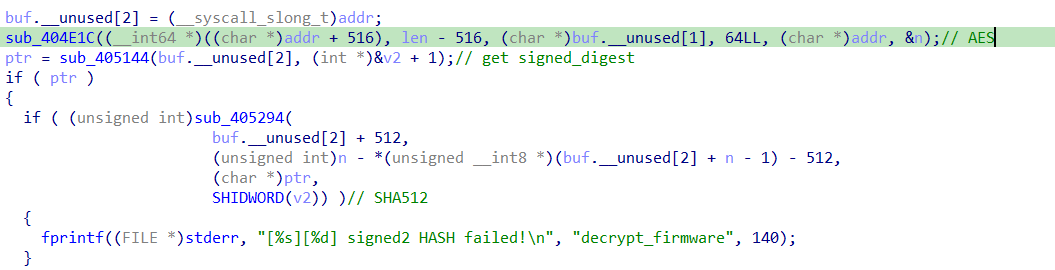
sub_404E1C()函数代码如下:
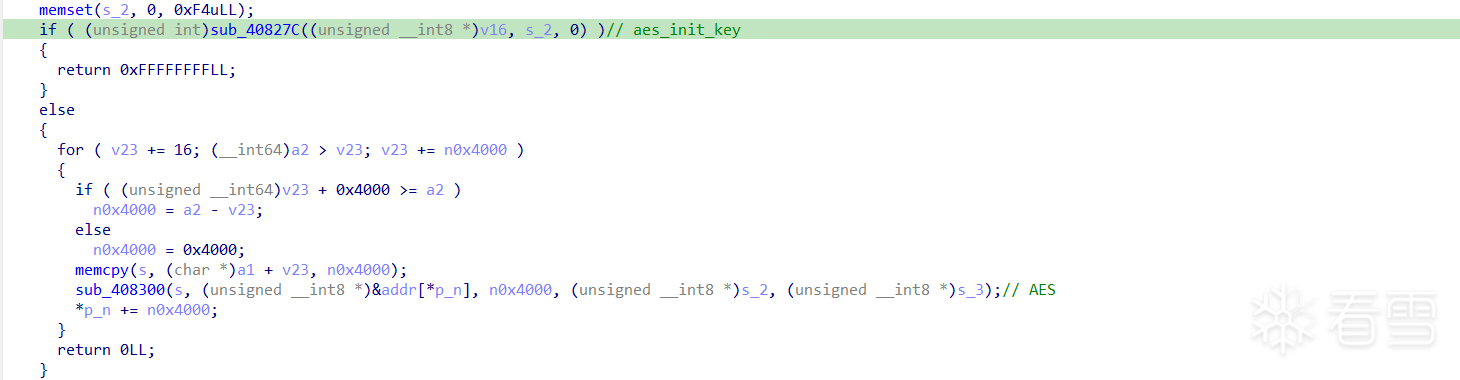
现在只需要HOOK sub_40827C() 来获取AES的KEY。
HOOK sub_408300() 来获取AES的IV。
HOOK AES KEY 代码:
HOOK AES 代码:
hook_aes x0-x4的参数依次是:原始密文/明文地址/大小/轮密钥/IV。
qiling的完整代码如下:
file decry_firm
decry_firm: ELF 64-bit LSB executable, ARM aarch64, version 1 (SYSV), dynamically linked, interpreter /lib/ld-musl-aarch64.so.1, stripped
file decry_firm
decry_firm: ELF 64-bit LSB executable, ARM aarch64, version 1 (SYSV), dynamically linked, interpreter /lib/ld-musl-aarch64.so.1, stripped
tree rootfs/arm64_linux_tenda/
rootfs/arm64_linux_tenda/
├── bin
│ ├── arm64_hello_static
│ └── decry_firm
├── lib
│ ├── ld-musl-aarch64.so.1
│ ├── libc.so
│ └── libgcc_s.so.1
├── proc
│ └── sys
│ └── kernel
│ └── osrelease
└── temp
└── US_AX3000.Pro_V16.03.49.26_cn_JAX01.bin
7 directories, 7 files
tree rootfs/arm64_linux_tenda/
rootfs/arm64_linux_tenda/
├── bin
│ ├── arm64_hello_static
│ └── decry_firm
├── lib
│ ├── ld-musl-aarch64.so.1
│ ├── libc.so
│ └── libgcc_s.so.1
├── proc
│ └── sys
│ └── kernel
│ └── osrelease
└── temp
└── US_AX3000.Pro_V16.03.49.26_cn_JAX01.bin
7 directories, 7 files
import sys
sys.path.append("..")
from qiling import Qiling
from qiling.const import QL_VERBOSE
from qiling.const import QL_INTERCEPT
import struct
import hexdump
def run_sandbox(path, rootfs):
ql = Qiling(path, rootfs, verbose=QL_VERBOSE.DEFAULT, multithread=False)
ql.run()
if __name__ == "__main__":
run_sandbox(["rootfs/arm64_linux_tenda/bin/decry_firm","/temp/US_AX3000.Pro_V16.03.49.26_cn_JAX01.bin"], "rootfs/arm64_linux_tenda")
import sys
sys.path.append("..")
from qiling import Qiling
from qiling.const import QL_VERBOSE
from qiling.const import QL_INTERCEPT
import struct
import hexdump
def run_sandbox(path, rootfs):
ql = Qiling(path, rootfs, verbose=QL_VERBOSE.DEFAULT, multithread=False)
ql.run()
if __name__ == "__main__":
run_sandbox(["rootfs/arm64_linux_tenda/bin/decry_firm","/temp/US_AX3000.Pro_V16.03.49.26_cn_JAX01.bin"], "rootfs/arm64_linux_tenda")
def hook_key(ql: Qiling) -> None:
ql.log.info('--------- hook_key ---------')
ql.log.info(f"0x{ql.arch.regs.x1:08X}")
struct_data = ql.mem.read(ql.arch.regs.x0,0X0F)
hexdump.hexdump(struct_data)
ql.hook_address(hook_key, 0x405018)
def hook_key(ql: Qiling) -> None:
ql.log.info('--------- hook_key ---------')
ql.log.info(f"0x{ql.arch.regs.x1:08X}")
struct_data = ql.mem.read(ql.arch.regs.x0,0X0F)
hexdump.hexdump(struct_data)
ql.hook_address(hook_key, 0x405018)
def hook_aes(ql: Qiling) -> None:
ql.log.info('--------- hook_aes ---------')
ql.log.info(f"0x{ql.arch.regs.x0:08X}")
struct_data = ql.mem.read(ql.arch.regs.x0,0X80)
hexdump.hexdump(struct_data)
ql.log.info(f"0x{ql.arch.regs.x1:08X}")
struct_data = ql.mem.read(ql.arch.regs.x1,0X80)
hexdump.hexdump(struct_data)
ql.log.info(f"0x{ql.arch.regs.x2:08X}")
ql.log.info(f"0x{ql.arch.regs.x3:08X}")
struct_data = ql.mem.read(ql.arch.regs.x3,0X80)
hexdump.hexdump(struct_data)
ql.log.info(f"0x{ql.arch.regs.x4:08X}")
struct_data = ql.mem.read(ql.arch.regs.x4,0X0F)
hexdump.hexdump(struct_data)
ql.emu_stop()
ql.hook_address(hook_aes, 0x4050E0)
def hook_aes(ql: Qiling) -> None:
ql.log.info('--------- hook_aes ---------')
ql.log.info(f"0x{ql.arch.regs.x0:08X}")
struct_data = ql.mem.read(ql.arch.regs.x0,0X80)
hexdump.hexdump(struct_data)
ql.log.info(f"0x{ql.arch.regs.x1:08X}")
struct_data = ql.mem.read(ql.arch.regs.x1,0X80)
hexdump.hexdump(struct_data)
ql.log.info(f"0x{ql.arch.regs.x2:08X}")
ql.log.info(f"0x{ql.arch.regs.x3:08X}")
struct_data = ql.mem.read(ql.arch.regs.x3,0X80)
hexdump.hexdump(struct_data)
ql.log.info(f"0x{ql.arch.regs.x4:08X}")
struct_data = ql.mem.read(ql.arch.regs.x4,0X0F)
hexdump.hexdump(struct_data)
ql.emu_stop()
ql.hook_address(hook_aes, 0x4050E0)
[=] --------- hook_key ---------
[=] 0x7FFFFFFFFAA0
00000000: ................................................ ................
[=] --------- hook_aes ---------
[=] 0x7FFFFFFFBAA0
00000000: 7E 5D C6 3A BC D3 87 27 48 BD 9D 2B 7F 4D E6 68 ~].:...'H..+.M.h
00000010: 95 A8 AC 34 69 EE 7A 07 42 50 D4 EB 9E 7C 4C F6 ...4i.z.BP...|L.
00000020: 00 10 5C A3 28 5F 3F C1 49 4E 74 40 9C 49 C3 7B ..\.(_?.INt@.I.{
00000030: 68 AA ED 16 E8 E8 86 A3 9F 69 9B BD 77 C4 B8 23 h........i..w..
00000040: 73 60 24 AB 1C F5 0A 2A 6B 5B 34 66 F2 1E 75 76 s`$....*k[4f..uv
00000050: 46 2D 83 E4 08 FF A8 73 5A 75 C0 EE B9 01 79 A8 F-.....sZu....y.
00000060: 7C AB E2 97 96 C9 8D 5D 75 3F 2B 23 A8 1B DF 25 |......]u?+
00000070: EB BB 7A 80 61 14 B2 04 8C FE 91 42 D3 99 FC C8 ..z.a......B....
[=] 0x7FFFB7DF9000
00000000: 00 DE 14 60 7F 73 E9 2B 3E 18 D5 85 D6 8A E4 CC ...`.s.+>.......
00000010: A3 06 35 B1 17 9C BC 3E 73 64 01 92 4C A5 F3 D0 ..5....>sd..L...
00000020: C6 39 88 FE 66 65 A1 11 19 8A F1 D3 F5 CB 04 1A .9..fe..........
00000030: 9A C9 6C B7 34 00 2C 62 7A 8E E1 4D 31 B0 57 35 ..l.4.,bz..M1.W5
00000040: 10 11 19 44 09 47 97 AF 67 ED F2 AC C8 6E A9 5A ...D.G..g....n.Z
00000050: C3 D0 C0 10 23 B3 3E EE 92 81 7B 18 AB 45 D4 0C ....
00000060: CD 34 06 9E 18 EF 9F 05 41 CF 13 8F F5 CA 52 BE .4......A.....R.
00000070: C2 C7 C2 A8 6A C7 11 20 A1 4E 96 79 6C CB 84 A9 ....j.. .N.yl...
[=] 0x00004000
[=] 0x7FFFFFFFFAA0
00000000: 1B F0 5A 24 1F FE F5 E1 CA E0 A5 8B 54 9B 9B 5C ..Z$........T..\
00000010: 41 CD 45 FC 4A 56 21 5D AA 60 D6 ED D6 40 6E F4 A.E.JV!].`...@n.
00000020: 00 2B 33 2D 0B 9B 64 A1 E0 36 F7 B0 7C 20 B8 19 .+3-..d..6..| ..
00000030: CD 67 6B 19 0B B0 57 8C EB AD 93 11 9C 16 4F A9 .gk...W.......O.
00000040: 4A 07 FB 65 C6 D7 3C 95 E0 1D C4 9D 77 BB DC B8 J..e..<.....w...
00000050: B6 C9 9F F0 8C D0 C7 F0 26 CA F8 08 97 A6 18 25 ........&......%
00000060: 08 83 CA FB 3A 19 58 00 AA 1A 3F F8 B1 6C E0 2D ....:.X...?..l.-
00000070: D8 6D 00 92 32 9A 92 FB 90 03 67 F8 1B 76 DF D5 .m..2.....g..v..
[=] 0x7FFFFFFFFBD8
00000000: ................................................ ................
[=] --------- hook_key ---------
[培训]Windows内核深度攻防:从Hook技术到Rootkit实战!
最后于 2025-11-18 11:37
被易之生生编辑
,原因: