-
-
[原创]【银行逆向百例】13小程序逆向之自动化反编译 云数据库获取密钥
-
发表于: 2025-9-21 16:39 1228
-
“ 最无奈他自己 总是会慢人家一拍,没有钱在那口袋。——《笨小孩》 ”
01环境版本
环境:
电脑,Windows 11 专业版 23H2
JiaoSuInfoSec/JiaoSuInfoSec_T00ls_Win11: 角宿武器库官方发布页面
软件:
Yakit,v1.4.4-0808
Yak Language Yak Program Language | Yak Program Language
微信,Windows 3.9.10.19
wechat-windows-versions
KillWxapkg,2.4.1
Ackites/KillWxapkg: 自动化反编译微信小程序
02自动化反编译
1、开启内置浏览器F12
1 | .\WechatOpenDevTools-Python.exe -c |
2、搜索银行关键字,点击检查打开控制台
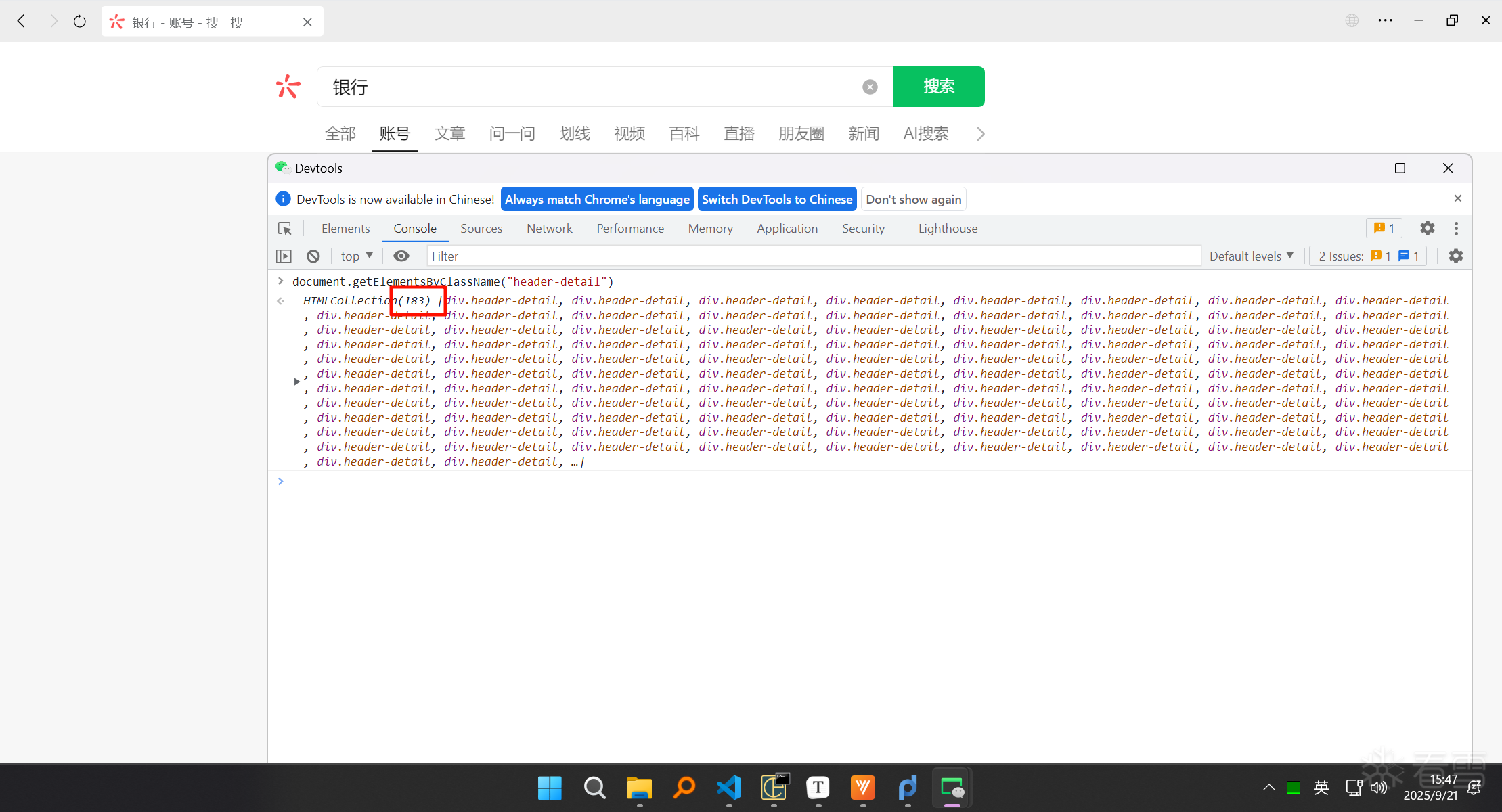
3、一直下滑直到末尾,加载了183个小程序
1 | document.getElementsByClassName("header-detail") |
4、每次打开20个小程序,等待1分钟,手动关闭打开的小程序,继续打开剩下的小程序
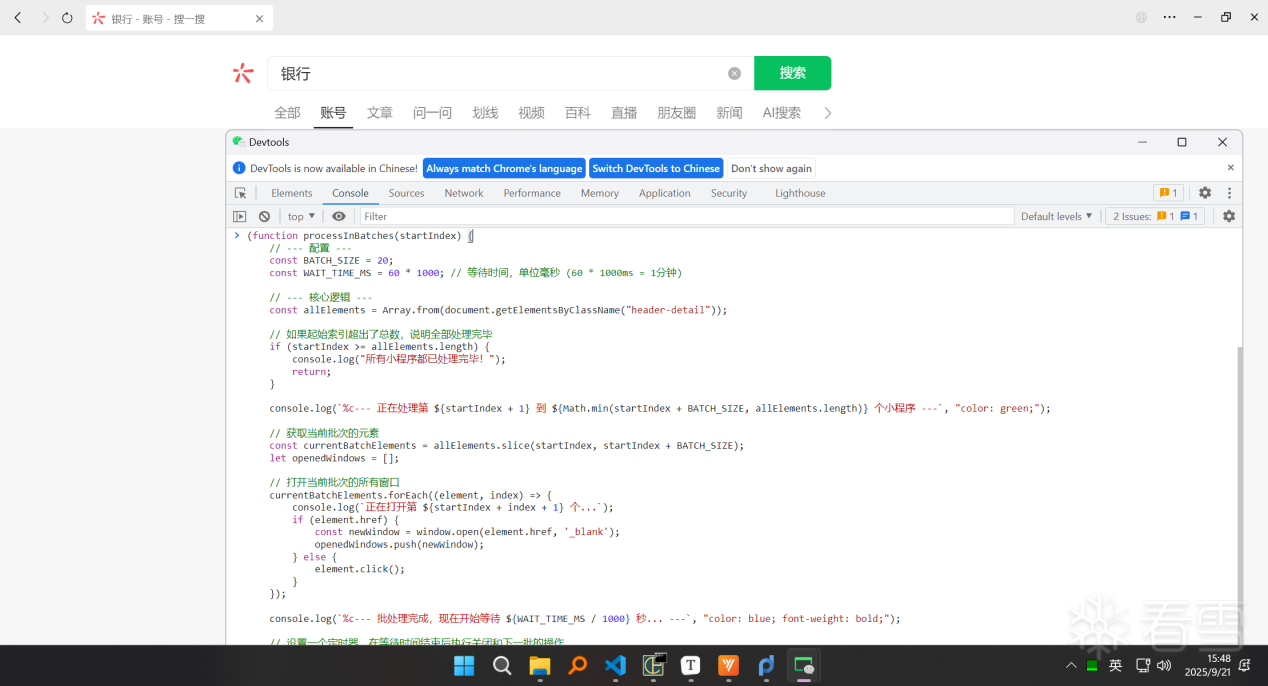
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 | (function processInBatches(startIndex) { // --- 配置 --- const BATCH_SIZE = 20; const WAIT_TIME_MS = 60 * 1000; // 等待时间,单位毫秒 (60 * 1000ms = 1分钟) // --- 核心逻辑 --- const allElements = Array.from(document.getElementsByClassName("header-detail")); // 如果起始索引超出了总数,说明全部处理完毕 if (startIndex >= allElements.length) { console.log("所有小程序都已处理完毕!"); return; } console.log(`%c--- 正在处理第 ${startIndex + 1} 到 ${Math.min(startIndex + BATCH_SIZE, allElements.length)} 个小程序 ---`, "color: green;"); // 获取当前批次的元素 const currentBatchElements = allElements.slice(startIndex, startIndex + BATCH_SIZE); let openedWindows = []; // 打开当前批次的所有窗口 currentBatchElements.forEach((element, index) => { console.log(`正在打开第 ${startIndex + index + 1} 个...`); if (element.href) { const newWindow = window.open(element.href, '_blank'); openedWindows.push(newWindow); } else { element.click(); } }); console.log(`%c--- 批处理完成,现在开始等待 ${WAIT_TIME_MS / 1000} 秒... ---`, "color: blue; font-weight: bold;"); // 设置一个定时器,在等待时间结束后执行关闭和下一批的操作 setTimeout(function() { console.log(`%c正在关闭 ${openedWindows.length} 个已打开的小程序...`, "color: red;"); openedWindows.forEach(win => { if (win && !win.closed) { win.close(); } }); // 递归调用自身,处理下一批 processInBatches(startIndex + BATCH_SIZE); }, WAIT_TIME_MS);})(0); // 立即执行函数,并从索引 0 开始 |
5、下载全部__APP__.wxapkg
1 | C:\Users\Administrator\Documents\WeChat Files\Applet |
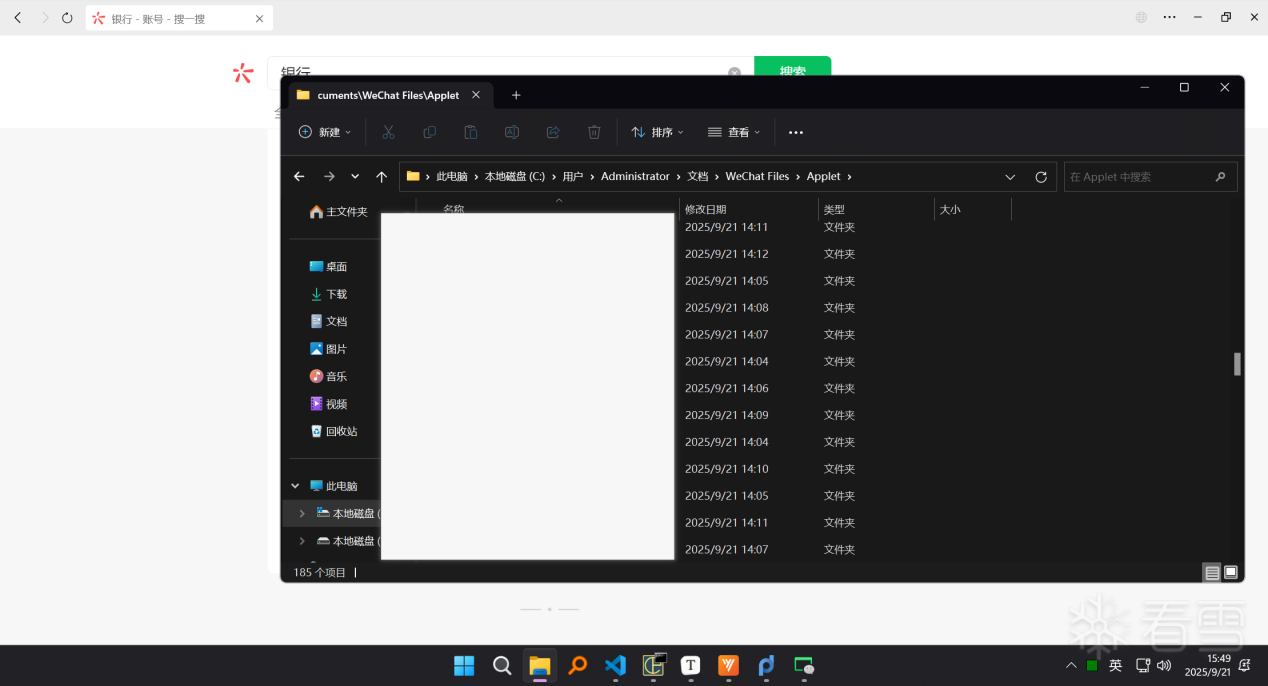
6、批量反编译小程序
1 | .\u.ps1 |
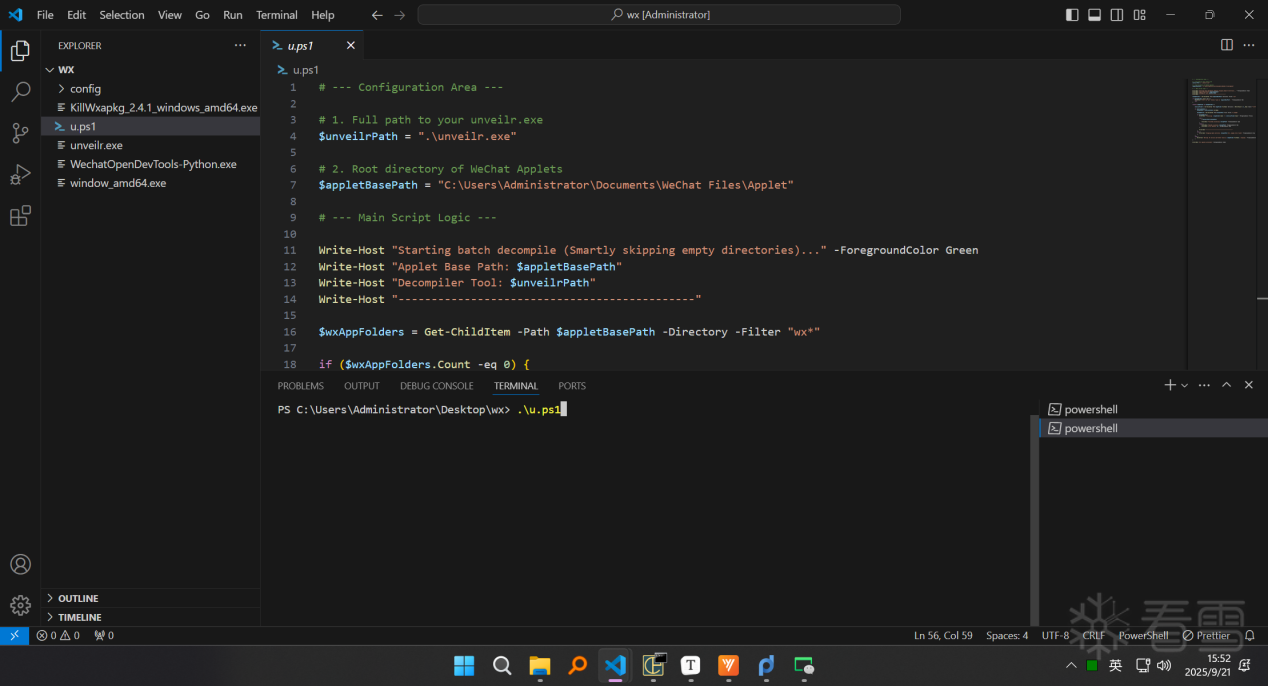
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 | # --- Configuration Area ---# 1. Full path to your unveilr.exe$unveilrPath = ".\unveilr.exe"# 2. Root directory of WeChat Applets$appletBasePath = "C:\Users\Administrator\Documents\WeChat Files\Applet"# --- Main Script Logic ---Write-Host "Starting batch decompile (Smartly skipping empty directories)..." -ForegroundColor GreenWrite-Host "Applet Base Path: $appletBasePath"Write-Host "Decompiler Tool: $unveilrPath"Write-Host "---------------------------------------------"$wxAppFolders = Get-ChildItem -Path $appletBasePath -Directory -Filter "wx*"if ($wxAppFolders.Count -eq 0) { Write-Host "Error: No 'wx*' folders found in '$appletBasePath'." -ForegroundColor Red exit}foreach ($appFolder in $wxAppFolders) { $versionFolder = Get-ChildItem -Path $appFolder.FullName -Directory | Where-Object { $_.Name -match "^\d+$" } | Select-Object -First 1 if ($versionFolder) { $targetPath = $versionFolder.FullName $wxapkgFiles = Get-ChildItem -Path $targetPath -File -Filter "*.wxapkg" if ($wxapkgFiles) { Write-Host "Processing: $($appFolder.Name) -> $($versionFolder.Name)" -ForegroundColor Yellow try { & $unveilrPath $targetPath Write-Host "Finished processing: $targetPath" -ForegroundColor Cyan } catch { Write-Host "Failed to process: $targetPath" -ForegroundColor Red Write-Host "Error details: $_" -ForegroundColor Red } Write-Host "---------------------------------------------" } else { Write-Host "Skipping empty directory: $targetPath (No .wxapkg files found)" -ForegroundColor Gray } } else { Write-Host "Warning: No version sub-folder found in $($appFolder.FullName), skipping." -ForegroundColor Magenta }}Write-Host "All applets processed!" -ForegroundColor Green |
03逆向分析
7、打开Applet目录全局搜索wx.cloud.init云函数初始化关键字
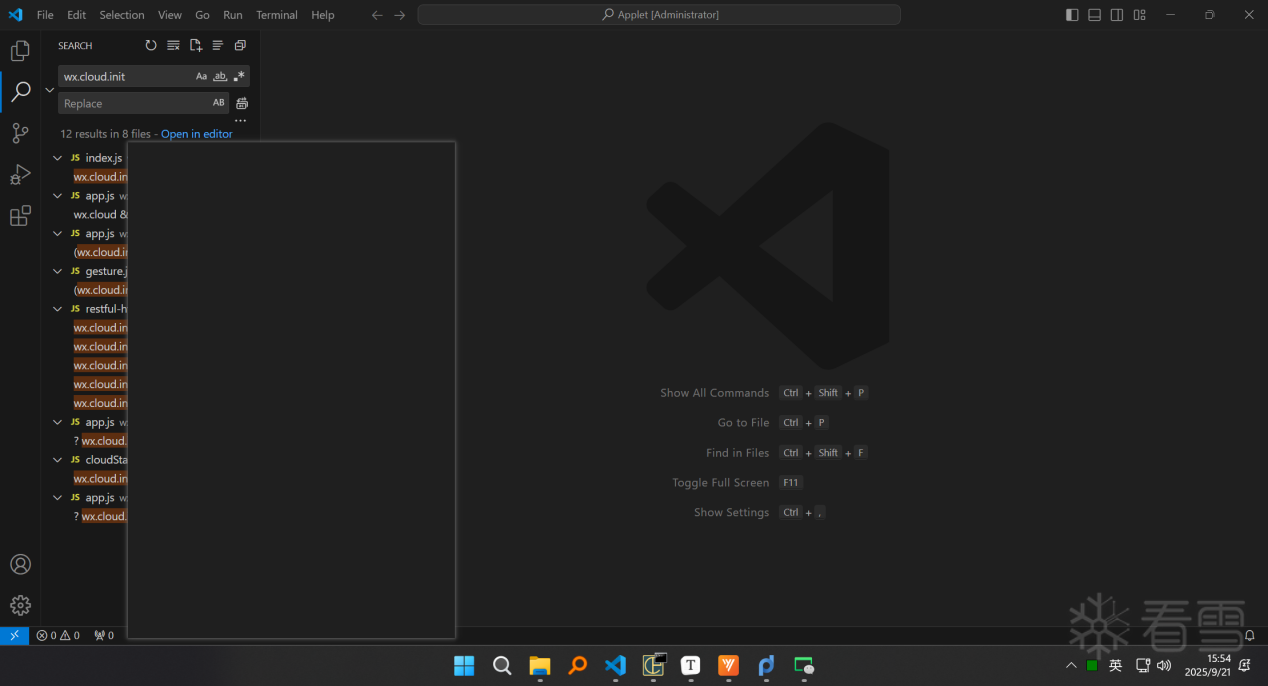
8、请求响应加密
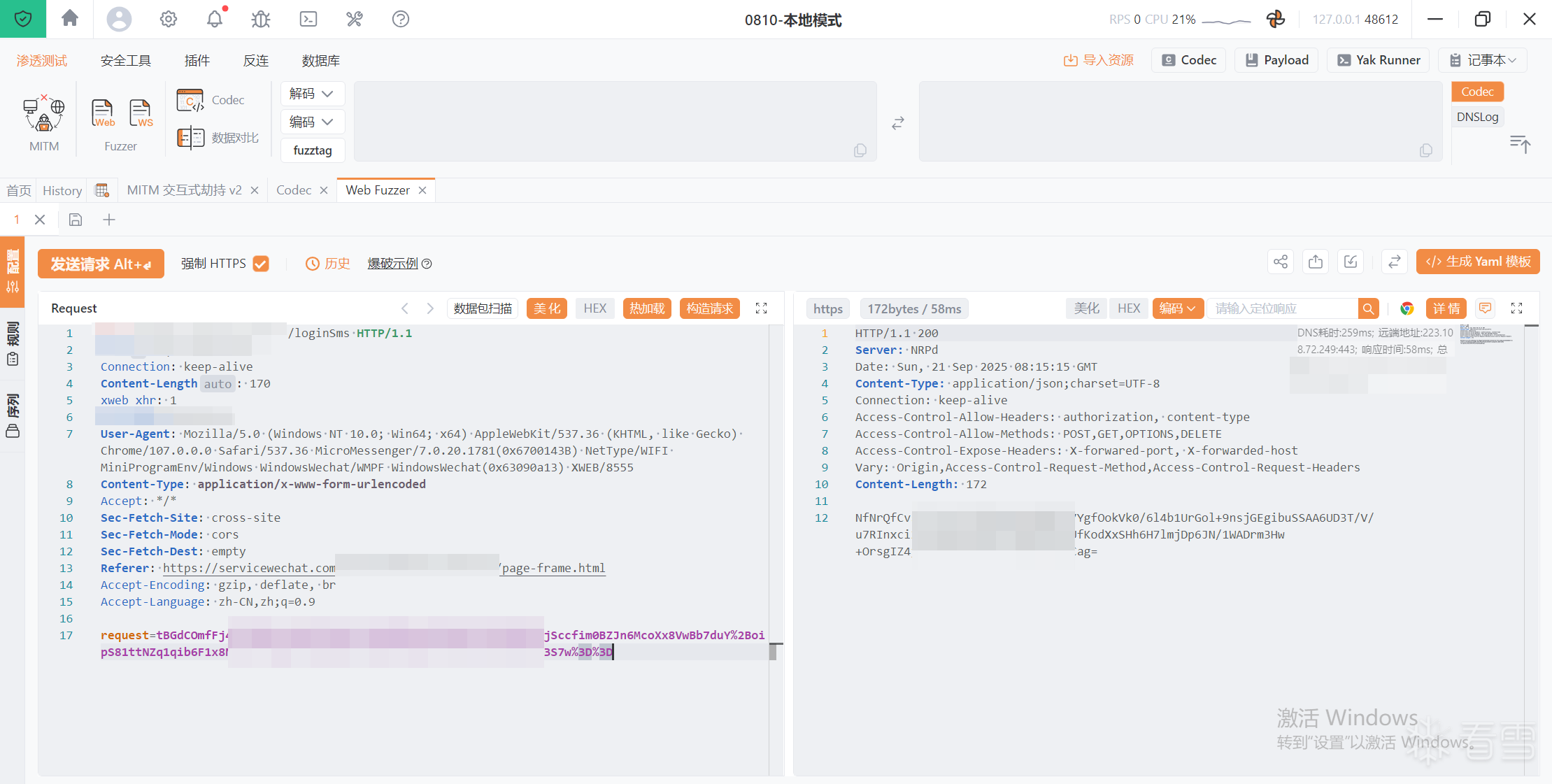
9、分析目标小程序,从云数据库中获取aesKey,赋值给全局变量i.app.globalData.aesKey
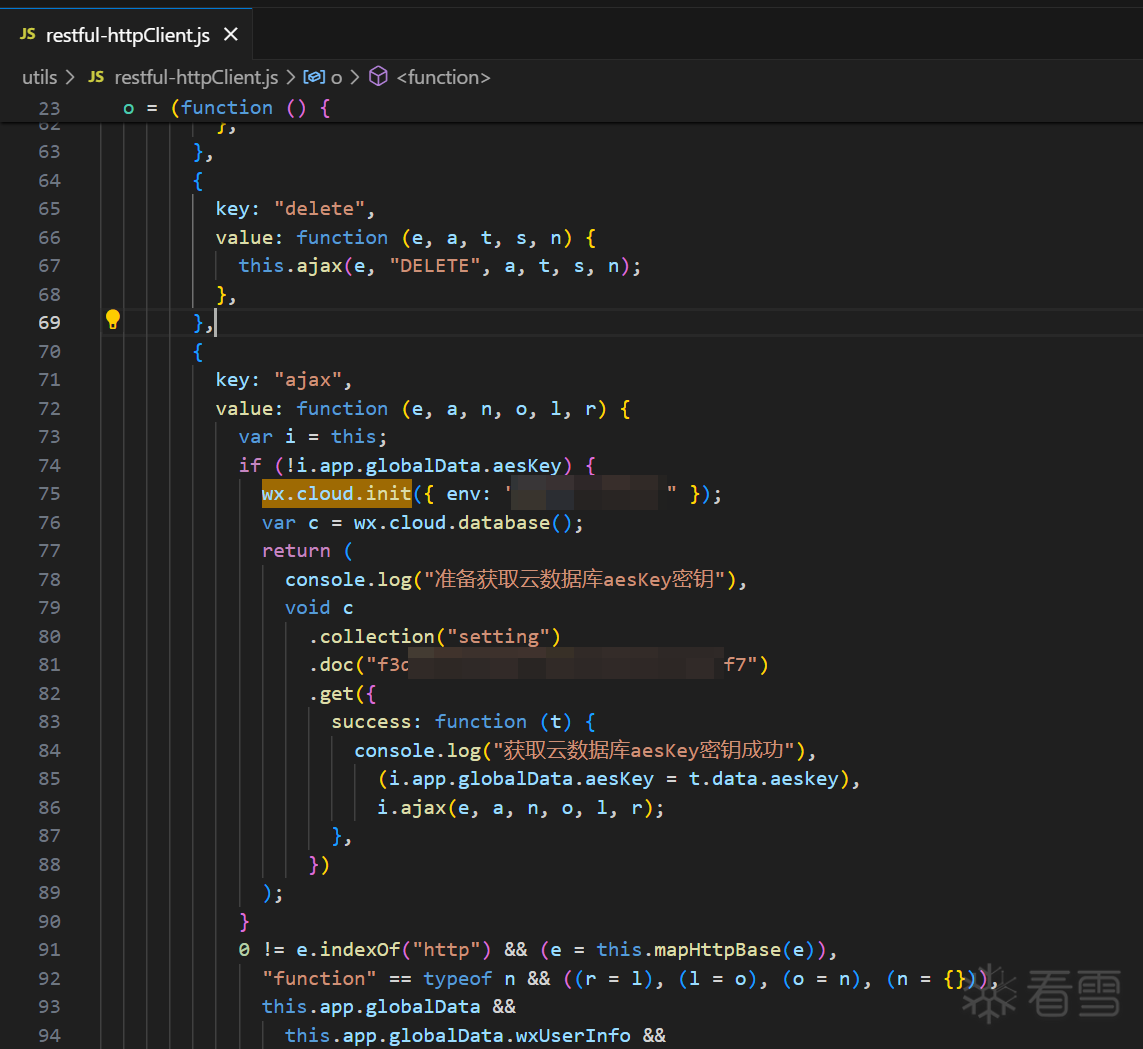
10、开启小程序控制台
1 | .\KillWxapkg_2.4.1_windows_amd64.exe -hook |
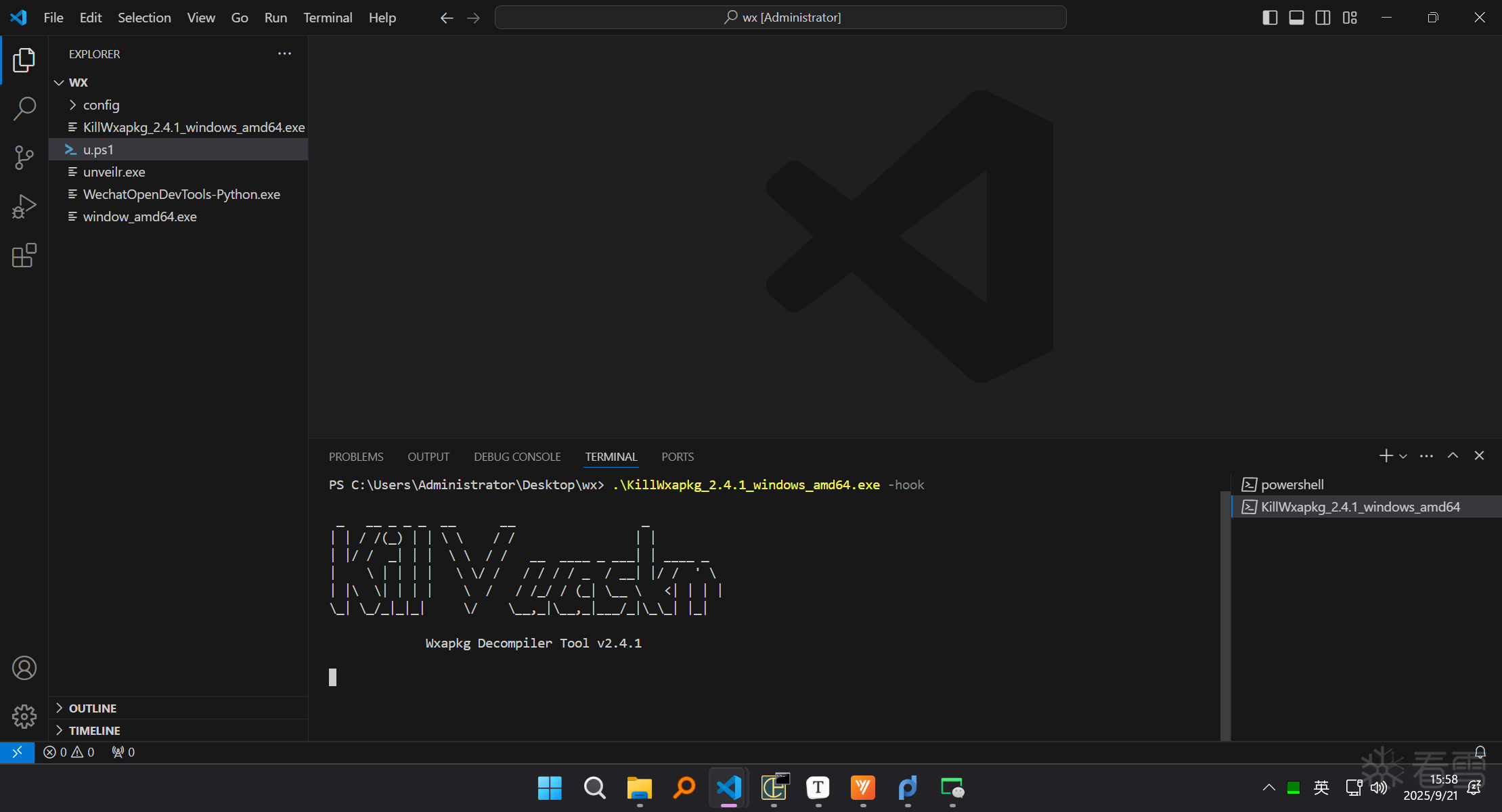
11、点击获取验证码
12、控制台点击js
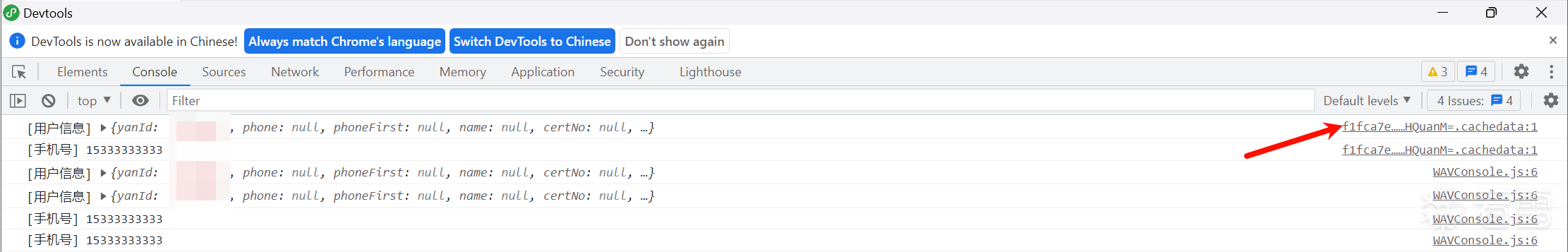
13、断点重新触发请求,依次点击调用堆栈
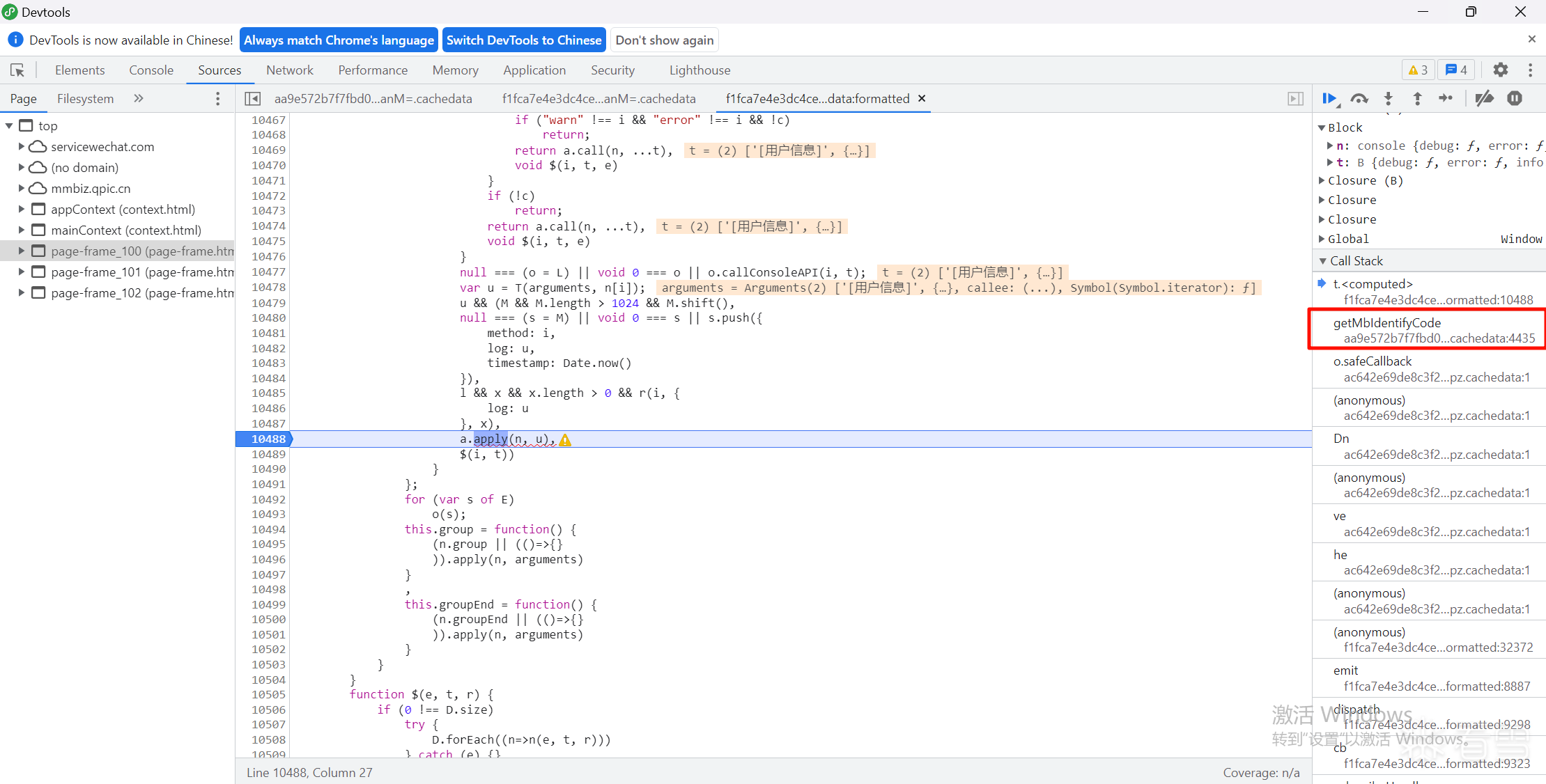
14、搜索wx.cloud.init关键字定位到第九步的restful-httpClient.js
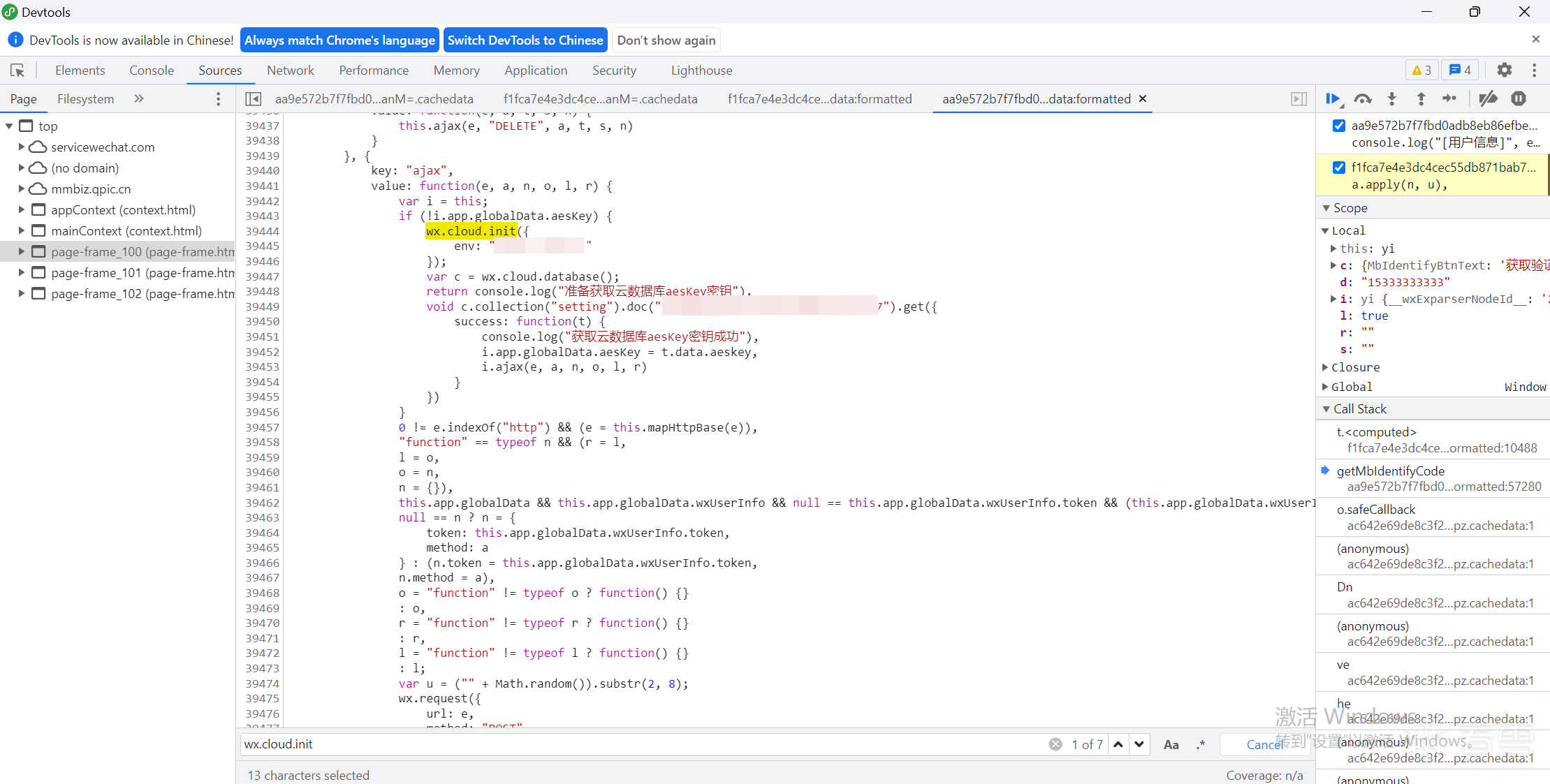
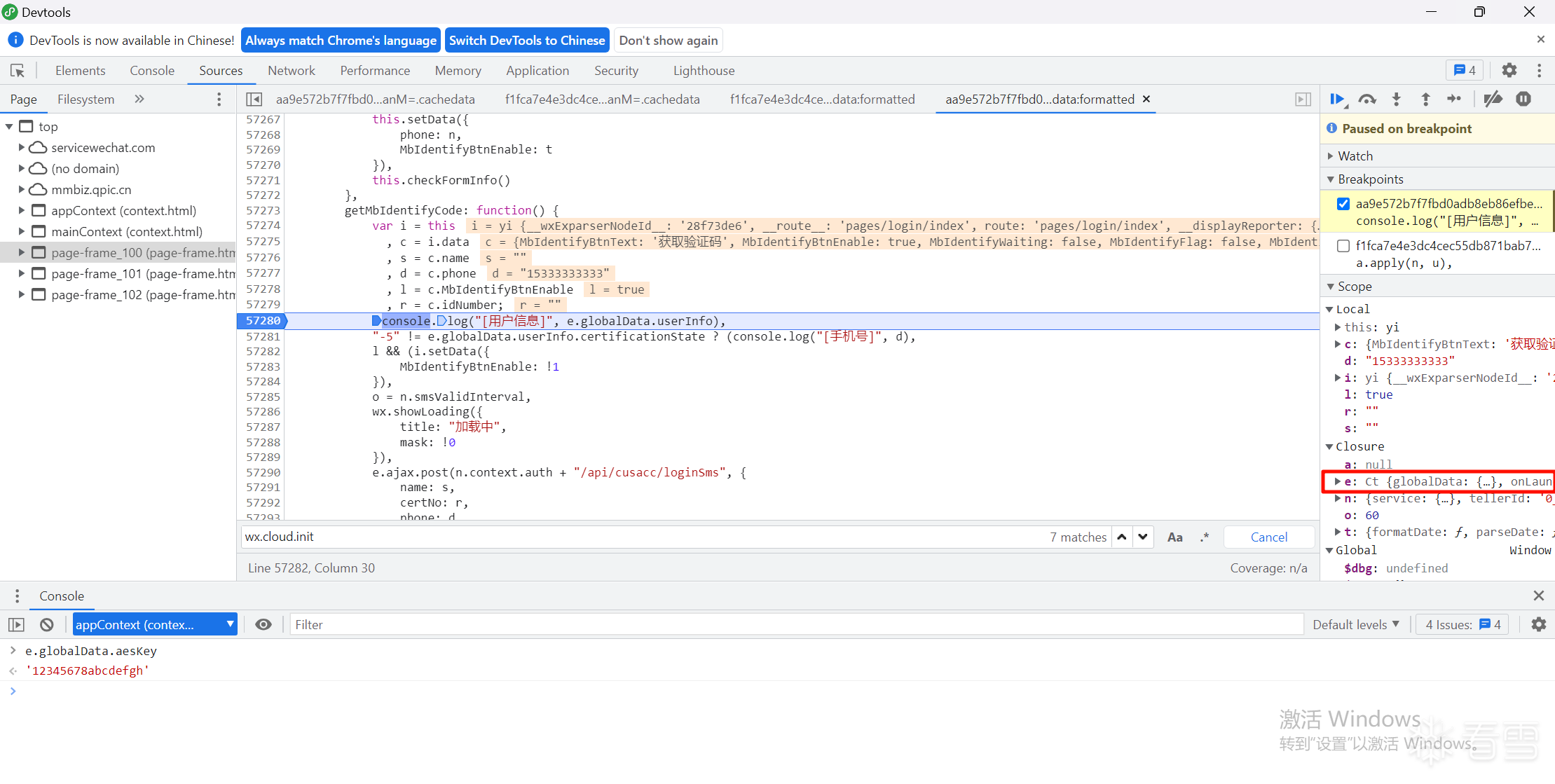
15、断点,控制台获取作用域e的aeskey
1 | e.globalData.aesKey |
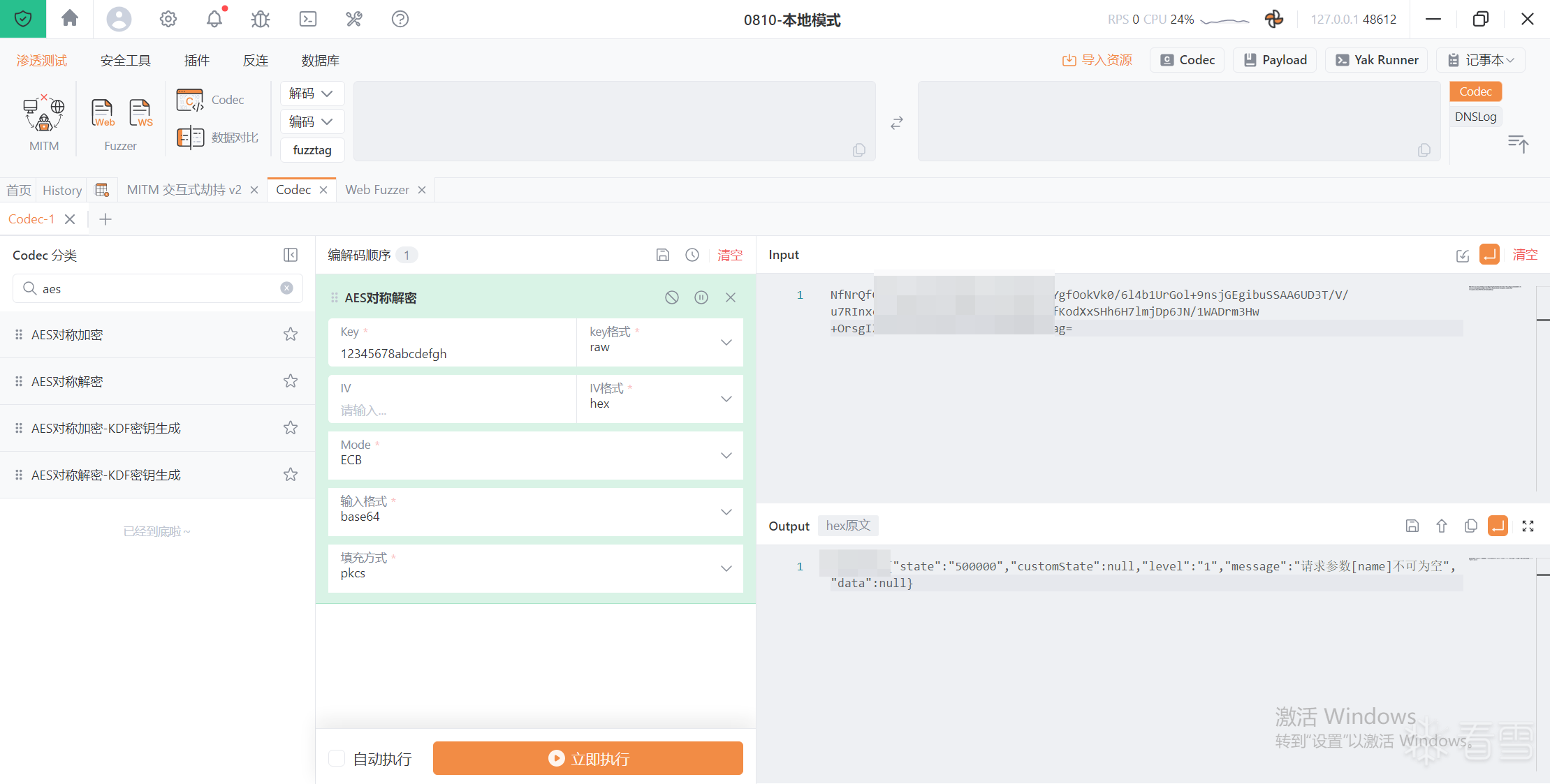
16、解密成功
[培训]Windows内核深度攻防:从Hook技术到Rootkit实战!
最后于 2025-9-21 17:01
被差不多的张三编辑
,原因: 添加歌词文案
赞赏记录
参与人
雪币
留言
时间
NxXB1
感谢你的积极参与,期待更多精彩内容!
2026-1-21 15:51
taibai
你的帖子非常有用,感谢分享!
2026-1-8 17:58
赞赏
他的文章
赞赏
雪币:
留言:




