主题:filemonitor
工具:vc6.0
语言:c/c++,其实就是用C++写的sdk,知道很戳。。。莫笑。。。。
所用技术:利用detour的形式hook api,dll注入....
思想:filemonitor,主要是拦截一些程序运行途中所有的相关文件操作,所以无非是hook 一下ceatefile....,然后再所有新进程启动前,hook这些函数,这里就注入自己的dll实现hook,本来想用汇编写的....哈哈,上网一搜,就有看雪的大大写了一个,用win32汇编写的,hook技术用的是Hookapi的形式,自己就用detour技术写一个,语言就用其他的.....也算是对寒假学习《win32循序渐进》这本书的一个小小总结,对了!还不能忘了感谢这本书的作者以及看雪论坛.....谢谢你们,给我知识,给我力量!附(虽然东西想起来很简单,但对我来说还是信奉这句话:。。(纸上谈来终觉浅,绝知此事要躬行)
声明:
也没啥含量,所以就往这个板块发,如果斑竹觉得不是很合适,随便处置。(大大们请飘过....旨在和像我一样的新手交流为主,不要骂我就行....)
昨天星期五,有课,但心情很不爽,所以没去,就有了此拙作,上午写完了,心情就好了,不知道为什么。。。哈哈,我又在抒情。。。
代码很简单所有我就全部端上来了,里面有注释,不会论坛的代码那种漂亮显示技术(谁会的教教我。。)
1.主程序部分代码(完整程序及代码见附件):
#define DEF_BUF_SIZE 1024
// 用于存储注入模块DLL的路径全名
char szDllPath[DEF_BUF_SIZE] = {0} ;
OPENFILENAME ofn;
PROCESS_INFORMATION info;
char szPathname[MAX_PATH]={0};
char szName[MAX_PATH]={0};
HINSTANCE hInst;
//注入远程注入通用函数
BOOL InjectModuleToProcessById(DWORD pID)
{
if(pID==NULL)
return FALSE;
HANDLE hProcess =::OpenProcess(PROCESS_ALL_ACCESS,FALSE,pID);
if(hProcess == NULL)
return FALSE;
UINT nLen =(UINT)strlen(szDllPath)+1;
LPVOID lpRemoteDllName = ::VirtualAllocEx(hProcess,NULL,nLen,MEM_COMMIT,PAGE_READWRITE);
if(lpRemoteDllName == NULL)
{
::MessageBox(NULL,"errorAlloc","error",MB_OK);
return FALSE;
}
if(::WriteProcessMemory(hProcess,lpRemoteDllName,szDllPath,nLen,NULL)==FALSE)
{
::MessageBox(NULL,"errorWriting","error",MB_OK);
return FALSE;
}
HMODULE hModule = ::GetModuleHandle("kernel32.dll");
LPTHREAD_START_ROUTINE fnStartAddr = (LPTHREAD_START_ROUTINE)GetProcAddress(hModule,"LoadLibraryA");
if((DWORD)fnStartAddr == 0)
{
::MessageBox(NULL,"errorAddress","error",MB_OK);
return FALSE;
}
HANDLE hRemoteThread = ::CreateRemoteThread(hProcess,NULL,0,fnStartAddr,lpRemoteDllName,0,NULL);
if(hRemoteThread ==NULL)
{
::MessageBox(NULL,"errorRemoteThread","error",MB_OK);
return FALSE;
}
if(::WaitForSingleObject(hRemoteThread,INFINITE)!=WAIT_OBJECT_0)
{
::MessageBox(NULL,"errorWaiting","error",MB_OK);
return FALSE;
}
::CloseHandle(hRemoteThread);
::CloseHandle(hModule);
::CloseHandle(hProcess);
return true;
}
...........此处略去*字....
2.dll部分代码:
/************************hook函数相关挂靠赋值****************
static HFILE (WINAPI*OLD_OpenFile)(LPCSTR lpFileName, LPOFSTRUCT lpReOpenBuff,UINT uStyle)=OpenFile;
static HANDLE (WINAPI*OLD_CreateFileA)(LPCTSTR lpFileName,DWORD dwDesiredAccess,\
DWORD dwShareMode,\
LPSECURITY_ATTRIBUTES lpSecurityAttributes,\
DWORD dwCreationDisposition,\
DWORD dwFlagsAndAttributes,\
HANDLE hTemplateFile\
)=CreateFileA;
static HANDLE (WINAPI*OLD_CreateFileW)(LPCWSTR lpFileName,DWORD dwDesiredAccess,\
DWORD dwShareMode,\
LPSECURITY_ATTRIBUTES lpSecurityAttributes,\
DWORD dwCreationDisposition,\
DWORD dwFlagsAndAttributes,\
HANDLE hTemplateFile\
)=CreateFileW;
.....此处略去*字....
//********************************************************
//********************** myfunctions 定义*****************
HFILE WINAPI myOpenFile(LPCSTR lpFileName, LPOFSTRUCT lpReOpenBuff,UINT uStyle)
{
char szNameTemp[200]={0};
lstrcpy(szNameTemp,"OpenFileName:");
lstrcat(szNameTemp,lpFileName);
SendMessage(hWndList,LB_ADDSTRING,0,(LPARAM)szNameTemp);//发送消息给listBox
return OLD_OpenFile(lpFileName,lpReOpenBuff,uStyle);
}
HANDLE WINAPI myCreateFileA(LPCTSTR lpFileName,DWORD dwDesiredAccess,\
DWORD dwShareMode,\
LPSECURITY_ATTRIBUTES lpSecurityAttributes,\
DWORD dwCreationDisposition,\
DWORD dwFlagsAndAttributes,\
HANDLE hTemplateFile\
)
{
char szNameTemp[MAX_PATH]={0};
GetModuleFileName(NULL,szNameTemp,sizeof(szNameTemp));
lstrcpy(szNameTemp,"CreateFileA-FileName:");
lstrcat(szNameTemp,lpFileName);
SendMessage(hWndList,LB_ADDSTRING,0,(LPARAM)szNameTemp);
return OLD_CreateFileA(lpFileName,\
dwDesiredAccess,\
dwShareMode,\
lpSecurityAttributes,\
dwCreationDisposition,\
dwFlagsAndAttributes,\
hTemplateFile);
}
......继续略.....
//***********detour 定义器******************
void WINAPI Hook()
{
DetourTransactionBegin();
DetourUpdateThread(GetCurrentThread());
//**********************detour加载开始点*******
DetourAttach(&(PVOID&)OLD_OpenFile,myOpenFile);
DetourAttach(&(PVOID&) OLD_CreateFileA,myCreateFileA);
DetourAttach(&(PVOID&) OLD_CreateFileW,myCreateFileW);
DetourAttach(&(PVOID&) OLD_ReadFile,myReadFile);
DetourAttach(&(PVOID&) OLD_ReadFileEx,myReadFileEx);
DetourAttach(&(PVOID&) OLD_WriteFile,myWriteFile);
DetourAttach(&(PVOID&) OLD_WriteFileEx,myWriteFileEx);
DetourAttach(&(PVOID&) OLD_DeviceIoControl,myDeviceIoControl);
//**********************加入结束点*******
DetourTransactionCommit();
}
void WINAPI UnHook()
{
DetourTransactionBegin();
DetourUpdateThread(GetCurrentThread());
//**********************detour恢复开始点***********
DetourDetach(&(PVOID&)OLD_OpenFile,myOpenFile);
DetourDetach(&(PVOID&) OLD_CreateFileA,myCreateFileA);
DetourDetach(&(PVOID&) OLD_CreateFileW,myCreateFileW);
DetourDetach(&(PVOID&) OLD_ReadFile,myReadFile);
DetourDetach(&(PVOID&) OLD_ReadFileEx,myReadFileEx);
DetourDetach(&(PVOID&) OLD_WriteFile,myWriteFile);
DetourDetach(&(PVOID&) OLD_WriteFileEx,myWriteFileEx);
DetourDetach(&(PVOID&) OLD_DeviceIoControl,myDeviceIoControl);
//**********************detour恢复结束点***********
DetourTransactionCommit();
}
BOOL APIENTRY DllMain( HANDLE hModule,
DWORD ul_reason_for_call,
LPVOID lpReserved
)
{
switch(ul_reason_for_call)
{
case DLL_PROCESS_ATTACH:
{ 保存listbox句柄
HWND hParent=::FindWindow(NULL,"FileMonitor by ycmint");
hWndList = ::FindWindowEx(hParent,0,"ListBox",0);
Hook();
break;
}
case DLL_PROCESS_DETACH:
{
UnHook();
break;
}
}
return TRUE;
}
运行效果图:
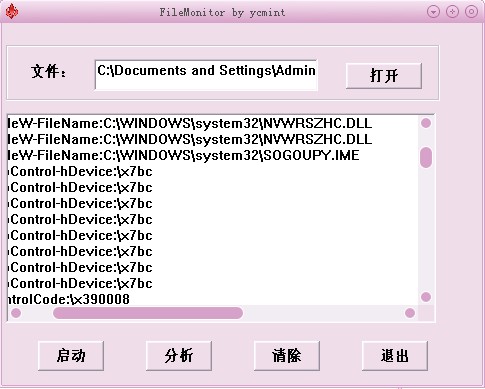
源文件及用户程序(如果您的系统上没有detoured.dll,请搜索下载,一大批...)
Release.rar
注意由于涉及到系统的操作,可能会报毒什么的。。。相信俺的看官就下下看看。。。不信的,那就。。。
[招生]科锐逆向工程师培训(2024年11月15日实地,远程教学同时开班, 第51期)