本人写了个CM参加比赛,可惜,由于种种原因,与比赛无缘了,相当遗憾
现就本人的写的这个CM的加密方法做些简要的介绍吧,恳请大家批评指正啊~~~
(1)
从文本框获取注册名,如"MYHEARTRED",如果注册名长度小于32字节,则添加0x07补充至32字节,处理后十六进制结果如下,用h1表示:
4D59484541525452454407070707070707070707070707070707070707070707
(2)
对(1)中的十六进制结果h1按如下置换表进行置换:
RP1[64] = {
1, 9,17,25,33,41,49,57,
7,15,23,31,39,47,55,63,
3,11,19,27,35,43,51,59,
5,13,21,29,37,45,53,61,
8,16,24,32,40,48,56,64,
2,10,18,26,34,42,50,58,
6,14,22,30,38,46,54,62,
4,12,20,28,36,44,52,60
};
置换后十六进制结果h2为:
4440000045000000554000004500000052777777D15777778477777792477777
其二进制结果b1为:
0100010001000000000000000000000001000101000000000000000000000000010101010100000000000000000000000100010100000000000000000000000001010010011101110111011101110111110100010101011101110111011101111000010001110111011101110111011110010010010001110111011101110111
(3)
对上一步得到的二进制串b1进行处理后得到b2,处理方法如下:
b2首位与b1首位相同,b2的第2位等于b2的第1位与b1的第2位的异或,b2的第3位等于b2的第2位与b1的第3位的异或,...,即,b2的第N位为b2的第N-1位与b1的第N位的异或.
这么处理后得到的二进制串b2为:
0111100001111111111111111111111110000110000000000000000000000000011001100111111111111111111111111000011000000000000000000000000001100011101001011010010110100101011000011001101001011010010110101111100001011010010110100101101011100011100001011010010110100101
(4)
采用流密钥生成器,生成256位的密钥,流密钥生成器示意图如下:
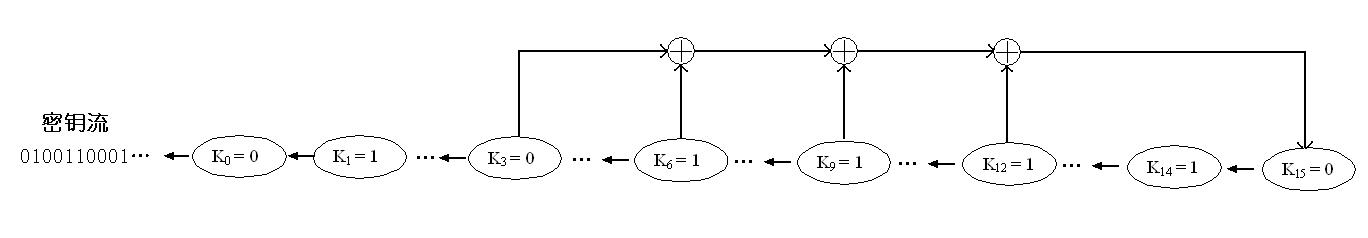
生成密钥为b3:
0100110001110101110010011101001010110100000100011001111000110100010100010000010010001000100111101011010101100100011111010001011111111101011011001010001100111000001001011101111000000101001010011010101011011111101001000001110111000000000111111100010011001010
(5)
这一步就是用流密钥生成的密钥加密b2,即按位异或,得到二进制串b4:
0011010000001010001101100010110100110010000100011001111000110100001101110111101101110111011000010011001101100100011111010001011110011110110010010000011010011101010001000100010001011111011100110101001010000101111111100100011100100011100110100110000101101111
(6)
我还用了一个加密盒子来加密b4,用如下初始加密矩阵进行变换得到
EN16_A[64]={
1,0,0,1,1,1,0,1,
0,1,0,1,0,1,1,0,
1,1,1,1,0,1,1,1,
1,0,1,0,1,0,1,1,
0,1,0,0,0,0,1,1,
1,0,0,1,0,1,1,0,
1,1,1,1,1,0,0,1,
1,1,1,1,1,1,1,1
};
EN16_A经过变换可以得到多个加密盒子,具体变化大致如下:
第i列往第i+1列循环右移,第i行往第i+1行循环下移,大致如下图所示,可能表达的不太清楚,这个加密盒子的变换比较复杂,但是其实这不是重点,加密盒子只是为得到加密密钥。
(7)
这一步对b4用加密盒子进行加密,b4是256位,而加密盒子是64位,故用四个加密盒子对b4进行加密。其实,(6)(7)步的加密也就相当于一个线性变换,但是,变换的密钥来的比较复杂,主要也是为了迷惑。
加密后的b4成为如下的b5:
1100111111010011011100100111101110110011001100100100100110011010010001111101111110001101110001001010110000101001000110010000001000101101000000001000101010001111000000111110111000000000100010010001101000110000100101010110100010111000010101100100100100011110
将其转换为十六进制的数据cmpA:
CFD3727BB332499A47DF8DC4AC2919022D008A8F03EE00891A309568B856491E
这样就得到了注册名加密后的cmpA,但是,这只是算法的一部分,还要对序列号进行加密.
(9)
获得文本框的序列号,例如序列号h3为:
1V9ZZTPYZPYMYVBB2B2VK88B2Z2214949841TZP6ZM9BZ6UZ2YBBY19MU4M64XZ6
然后对序列号h3中的字符做替换,替换表如下:
hex<==>序列号
'0'<==>'6'
'1'<==>'9'
'2'<==>'2'
'3'<==>'4'
'4'<==>'X'
'5'<==>'Y'
'6'<==>'Z'
'7'<==>'M'
'8'<==>'U'
'9'<==>'8'
'A'<==>'T'
'B'<==>'K'
'C'<==>'B'
'D'<==>'P'
'E'<==>'V'
'F'<==>'1',
h3转换后为h4:
FE166AD56D575ECC2C2EB99C2622F313193FA6D0671C608625CC5F1783703460
(10)
在第(9)步对序列号初步变换后,进行类似对注册名加密的方式进行加密,但是,加密使用的密钥不同.
对h4按如下置换表进行置换:
RP2[64] = {
2,10,18,26,34,42,50,58,
4,12,20,28,36,44,52,60,
6,14,22,30,38,46,54,62,
8,16,24,32,40,48,56,64,
1, 9,17,25,33,41,49,57,
3,11,19,27,35,43,51,59,
5,13,21,29,37,45,53,61,
7,15,23,31,39,47,55,63,
};
置换后十六进制结果h2为:
EDC6975367E2FCC0AE9360F45CC30670F6221628152231C765BFA653DC91D816
其二进制结果b6为:
1110110111000110100101110101001101100111111000101111110011000000101011101001001101100000111101000101110011000011000001100111000011110110001000100001011000101000000101010010001000110001110001110110010110111111101001100101001111011100100100011101100000010110
(11)
采用与第(4)步类似的流密钥生成器,生成256位的密钥,生成密钥为b7:
0100110001110101111111000101110101011010011010100010100001111110111101001101010100001101001100100111011001111001111101010110101100010011001111101100010001110100100010100010101100110110010000111011101010010000111101001110000110000110010001001000111110100101
(12)
这一步雷同于第(5)步,将b6用b7加密得b8:
1010000110110011011010110000111000111101100010001101010010111110010110100100011001101101110001100010101010111010111100110001101111100101000111001101001001011100100111110000100100000111100001001101111100101111010100101011001001011010110101010101011110110011
(13)
这里的一步同第(6)(7)步的方法,产生加密盒子然后加密,加密后得到b9:
0011111110101100111001011110100110011100110001010110101110111101011011101010111100011010001101101101001101011011100010110000010101011010000000000001110100011111000011000111011100000000000110111000110111000000101100100100000110010001001001000110101110000111
将其转换为十六进制的数据cmpB:
3FACE5E99CC56BBD6EAF1A36D35B8B055A001D1F0C77001B8DC0B24191246B87
这样就得到了序列号加密后16进制的cmpB.
(14)
得到cmpA和cmpB后,就对它们是否匹配进行比较.
cmpA:CFD3727BB332499A47DF8DC4AC2919022D008A8F03EE00891A309568B856491E
cmpB:3FACE5E99CC56BBD6EAF1A36D35B8B055A001D1F0C77001B8DC0B24191246B87
从cmpA和cmpB的每四位进行匹配检查,如cmpA的前四位C,和cmpB的前四位3.
是否匹配是看(C+1)和(3+1)的乘积除17是否余1,从专业的角度来说,就是检查(C+1)和(3+1)是否互为关于17的逆元.
如果64个都匹配,那么就是合法的注册名和序列号.
附件是简化版的CM,简化版的CM只保留了加密算法
PS:注册机也附上了
PS:所有加密方法均非COPY,其中加密盒子为本人原创
[注意]传递专业知识、拓宽行业人脉——看雪讲师团队等你加入!