今天看了pendan2001的关于脱SoftSentry 2.11 -> 20/20 Software的教程
试脱了一下这个程序。有点迷惑。请大家指教:
原程序下载:
KD.rar
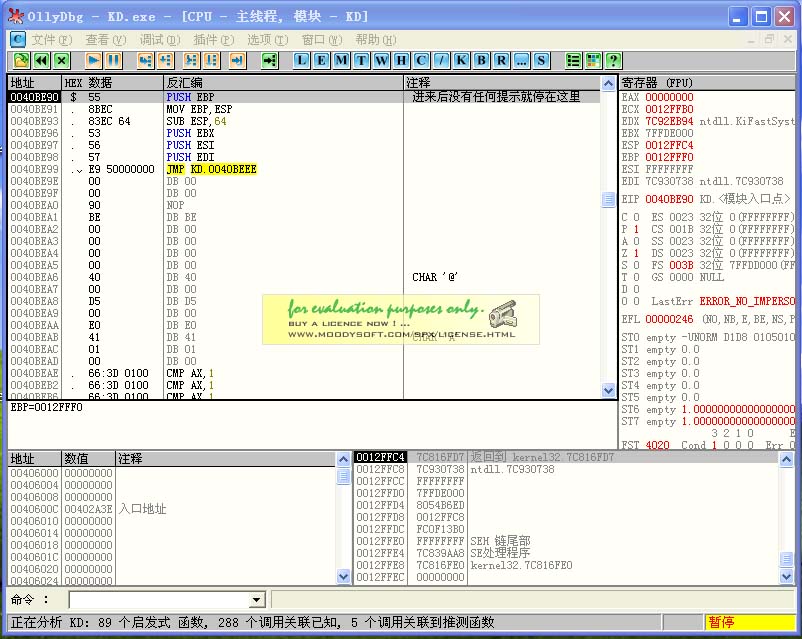
0040BE90 > $ 55 PUSH EBP ; 进来后没有任何提示就停在这里
0040BE91 . 8BEC MOV EBP,ESP ; F8单步向下走
0040BE93 . 83EC 64 SUB ESP,64
0040BE96 . 53 PUSH EBX
0040BE97 . 56 PUSH ESI
0040BE98 . 57 PUSH EDI
0040BE99 . E9 50000000 JMP KD.0040BEEE
//F8从这里跳转
0040BEEE \C745 E8 0000000>MOV DWORD PTR SS:[EBP-18],0
//到这里0040BEF5 8D45 BC LEA EAX,DWORD PTR SS:[EBP-44]
0040BEF8 50 PUSH EAX
0040BEF9 FF15 BC534100 CALL DWORD PTR DS:[<&KERNEL32.GetStartup>; kernel32.GetStartupInfoA
0040BEFF F645 E8 01 TEST BYTE PTR SS:[EBP-18],1
0040BF03 0F84 10000000 JE KD.0040BF19
0040BF09 8B45 EC MOV EAX,DWORD PTR SS:[EBP-14]
0040BF0C 25 FFFF0000 AND EAX,0FFFF
0040BF11 8945 14 MOV DWORD PTR SS:[EBP+14],EAX
0040BF14 E9 07000000 JMP KD.0040BF20
0040BF19 C745 14 0A00000>MOV DWORD PTR SS:[EBP+14],0A
0040BF20 6A 00 PUSH 0
0040BF22 FF15 C4534100 CALL DWORD PTR DS:[<&KERNEL32.GetModuleH>; kernel32.GetModuleHandleA
0040BF28 8945 08 MOV DWORD PTR SS:[EBP+8],EAX
0040BF2B C745 0C 0000000>MOV DWORD PTR SS:[EBP+C],0
0040BF32 FF15 A8534100 CALL DWORD PTR DS:[<&KERNEL32.GetCommand>; kernel32.GetCommandLineA
0040BF38 8945 10 MOV DWORD PTR SS:[EBP+10],EAX
0040BF3B 8B45 08 MOV EAX,DWORD PTR SS:[EBP+8]
0040BF3E 8945 B4 MOV DWORD PTR SS:[EBP-4C],EAX
0040BF41 66:C705 B811410>MOV WORD PTR DS:[4111B8],0
0040BF4A 66:C705 424C410>MOV WORD PTR DS:[414C42],0
0040BF53 837D 0C 00 CMP DWORD PTR SS:[EBP+C],0
0040BF57 0F85 17000000 JNZ KD.0040BF74
0040BF5D 8B4D 08 MOV ECX,DWORD PTR SS:[EBP+8]
0040BF60 E8 8B0E0000 CALL KD.0040CDF0
0040BF65 85C0 TEST EAX,EAX
0040BF67 0F85 07000000 JNZ KD.0040BF74
0040BF6D 33C0 XOR EAX,EAX
0040BF6F E9 C8030000 JMP KD.0040C33C
0040BF74 68 04010000 PUSH 104
0040BF79 68 704A4100 PUSH KD.00414A70
0040BF7E 8B45 08 MOV EAX,DWORD PTR SS:[EBP+8]
0040BF81 50 PUSH EAX
0040BF82 FF15 AC534100 CALL DWORD PTR DS:[<&KERNEL32.GetModuleF>; kernel32.GetModuleFileNameA
0040BF88 85C0 TEST EAX,EAX
0040BF8A 0F85 07000000 JNZ KD.0040BF97
0040BF90 33C0 XOR EAX,EAX
0040BF92 E9 A5030000 JMP KD.0040C33C
0040BF97 8B55 14 MOV EDX,DWORD PTR SS:[EBP+14]
0040BF9A 8B4D 08 MOV ECX,DWORD PTR SS:[EBP+8]
0040BF9D E8 9E0E0000 CALL KD.0040CE40
0040BFA2 85C0 TEST EAX,EAX
0040BFA4 0F85 1B000000 JNZ KD.0040BFC5
0040BFAA 6A 00 PUSH 0
0040BFAC 68 B8104100 PUSH KD.004110B8
0040BFB1 68 14124100 PUSH KD.00411214 ; ASCII "InitInstance FALSE"
0040BFB6 6A 00 PUSH 0
0040BFB8 FF15 48544100 CALL DWORD PTR DS:[<&USER32.MessageBoxA>>; USER32.MessageBoxA
0040BFBE 33C0 XOR EAX,EAX
0040BFC0 E9 77030000 JMP KD.0040C33C
0040BFC5 C745 B0 0100000>MOV DWORD PTR SS:[EBP-50],1
0040BFCC 8B45 10 MOV EAX,DWORD PTR SS:[EBP+10]
0040BFCF A3 D0494100 MOV DWORD PTR DS:[4149D0],EAX
0040BFD4 BA 504A4100 MOV EDX,KD.00414A50
0040BFD9 8D0D B1494100 LEA ECX,DWORD PTR DS:[4149B1]
0040BFDF E8 CC2B0000 CALL KD.0040EBB0
0040BFE4 E8 F72B0000 CALL KD.0040EBE0
0040BFE9 85C0 TEST EAX,EAX
0040BFEB 0F84 18000000 JE KD.0040C009
0040BFF1 66:C705 B811410>MOV WORD PTR DS:[4111B8],1
0040BFFA C705 68114100 0>MOV DWORD PTR DS:[411168],1
0040C004 E9 9A020000 JMP KD.0040C2A3
0040C009 B9 01000000 MOV ECX,1
0040C00E E8 7D2A0000 CALL KD.0040EA90
0040C013 33C0 XOR EAX,EAX
0040C015 66:A1 424C4100 MOV AX,WORD PTR DS:[414C42]
0040C01B F6C4 C0 TEST AH,0C0
0040C01E 0F85 2E000000 JNZ KD.0040C052
//修改它为NOP0040C024 33C0 XOR EAX,EAX
0040C026 66:A1 424C4100 MOV AX,WORD PTR DS:[414C42]
0040C02C F6C4 10 TEST AH,10
0040C02F 0F84 1D000000 JE KD.0040C052
//修改它为NOP
0040C035 6A 00 PUSH 0
0040C037 68 03800000 PUSH 8003
0040C03C 68 11010000 PUSH 111
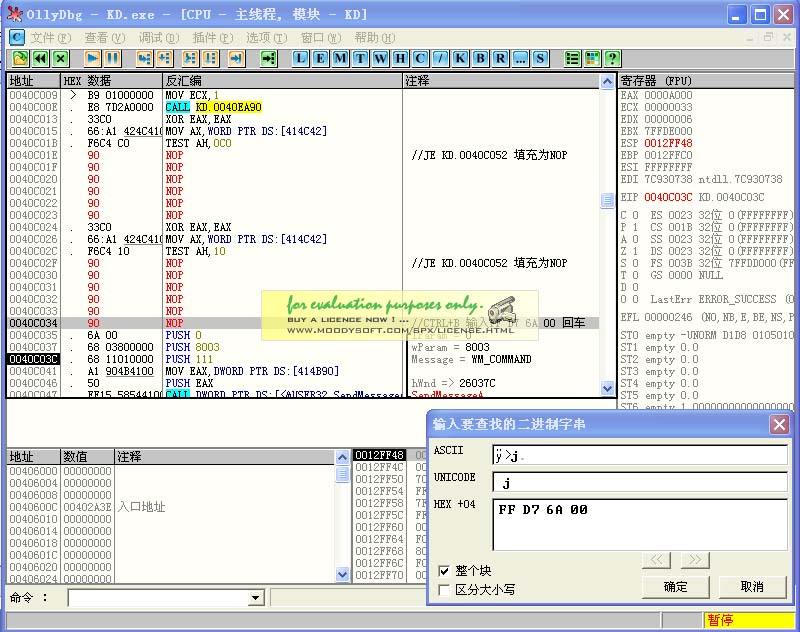
//CTRL+B 输入FF D7 6A 00 回车 跳转
0040C041 A1 904B4100 MOV EAX,DWORD PTR DS:[414B90]
0040C046 50 PUSH EAX
0040C047 FF15 58544100 CALL DWORD PTR DS:[<&USER32.SendMessageA>; USER32.SendMessageA
0040C04D E9 05000000 JMP KD.0040C057
0040C052 E8 19060000 CALL KD.0040C670
0040C057 833D 70114100 0>CMP DWORD PTR DS:[411170],0
0040C05E 0F84 16000000 JE KD.0040C07A
0040C064 8B4D B0 MOV ECX,DWORD PTR SS:[EBP-50]
0040C067 E8 442C0000 CALL KD.0040ECB0
0040C350 /$ 56 PUSH ESI
0040C351 |. 57 PUSH EDI
0040C352 |. 8BF2 MOV ESI,EDX
0040C354 |. 8B7C24 0C MOV EDI,DWORD PTR SS:[ESP+C]
0040C358 |. 8B51 02 MOV EDX,DWORD PTR DS:[ECX+2]
0040C35B |. 3351 06 XOR EDX,DWORD PTR DS:[ECX+6]
0040C35E |. 3351 0A XOR EDX,DWORD PTR DS:[ECX+A]
0040C361 |. 03FA ADD EDI,EDX
0040C363 |. 33D2 XOR EDX,EDX
0040C365 |> 8B41 06 /MOV EAX,DWORD PTR DS:[ECX+6]
0040C368 |. 42 |INC EDX
0040C369 |. 314497 FC |XOR DWORD PTR DS:[EDI+EDX*4-4],EAX
0040C36D |. 42 |INC EDX
0040C36E |. 8B41 0A |MOV EAX,DWORD PTR DS:[ECX+A]
0040C371 |. 314497 FC |XOR DWORD PTR DS:[EDI+EDX*4-4],EAX
0040C375 |. 83FA 14 |CMP EDX,14
0040C378 |.^ 7C EB \JL SHORT KD.0040C365
0040C37A |. 8B0E MOV ECX,DWORD PTR DS:[ESI]
0040C37C |. E8 5F320000 CALL KD.0040F5E0
0040C381 |. C706 00000000 MOV DWORD PTR DS:[ESI],0
0040C387 |. 66:833D B8114>CMP WORD PTR DS:[4111B8],0
0040C38F |. 74 0C JE SHORT KD.0040C39D
0040C391 |. 66:833D C0114>CMP WORD PTR DS:[4111C0],0
0040C399 |. 74 02 JE SHORT KD.0040C39D
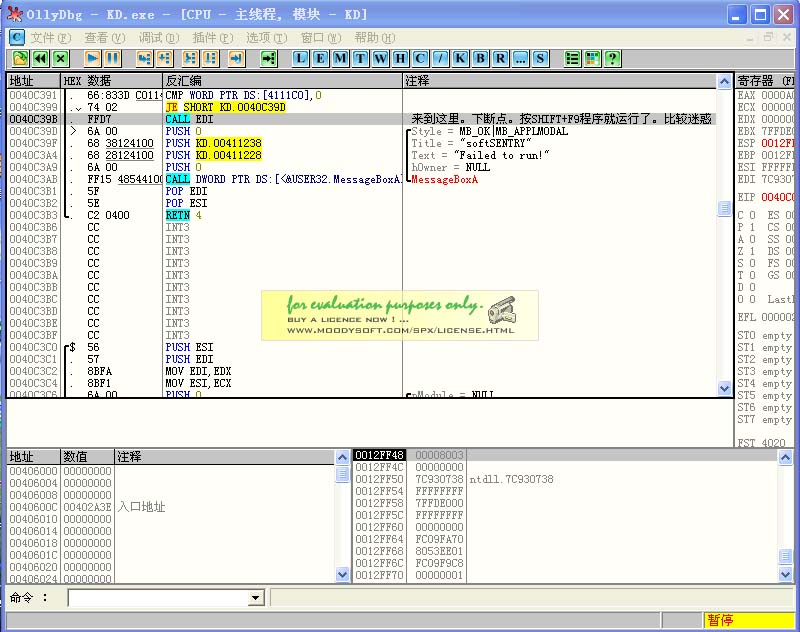
0040C39B |. FFD7 CALL EDI ;
来到这里。下断点。按SHIFT+F9程序就运行了。比较迷惑0040C39D |> 6A 00 PUSH 0 ; /Style = MB_OK|MB_APPLMODAL
0040C39F |. 68 38124100 PUSH KD.00411238 ; |Title = "softSENTRY"
0040C3A4 |. 68 28124100 PUSH KD.00411228 ; |Text = "Failed to run!"
0040C3A9 |. 6A 00 PUSH 0 ; |hOwner = NULL
0040C3AB |. FF15 48544100 CALL DWORD PTR DS:[<&USER32.MessageBoxA>>; \MessageBoxA
0040C3B1 |. 5F POP EDI
0040C3B2 |. 5E POP ESI
0040C3B3 \. C2 0400 RETN 4
0040C3B6 CC INT3
0040C3B7 CC INT3
到此就无法进行脱壳了。我那里出问题了
应该是跳到 CALL EDI 下断点。F9运行。取消断点。F7进入就可以脱壳了。可我一按下F9程序就运行了。
有人能帮帮我么
[注意]看雪招聘,专注安全领域的专业人才平台!