笔者在这先来聊聊某手的一些安全sdk相关的信息,毕竟知己知彼,百战不殆.
搞过某手业务的朋友都知道,某手有以下常见的算法防线,分别为
此外搞过看广告爆金币撸毛业务的以及设备注册朋友也应该知道某手还有以下算法防线
总体来说涉及的sdk有以下:
在libkwsgmain.so中有一个比较中心的方法:
此方法用于调度sdk的算法生成参数.
根据第一个参数去走不同的分支进行生成对应的参数.
以下是常见的命令:
我们只需要知道这四个即可
sig: 是标准的加盐md5 盐值:772867c19925/382700b563f4 签名(params+data(需字典排序转字符串) + salt) 这个盐是固定的,在某手和某手极速版不同,只要搞清楚签名的内容问题不大
__NStokensig: 加盐sha256 签名sig值+salt 这个盐在不同的设备上是不一样的 估计与设备注册相关联,搞清楚签名的内容 问题也不大
__NS_sig3/sig3: 签名UrlPath+sig值 主要涉及的算法CRC32 + AES-ecb-128-pkcs7 + HmacSha256
Kas: 签名UrlPath + sig3的值 + kaw的值 目测是魔改的black2s算法(哈希算法)+xor运算
__NS_xfalcon/sig4: 加密UrlPath+(Params+data) 目测是魔改的chacha20算法(对称算法)
Kaw: base64+xor运算 加密内容为设备反作弊信息.
本篇文章我们对kaw算法进行分析.
首先定位可以通过hook NewStringUtf打印调用堆栈快速回溯,可以看我之前写的文章,kaw所在的so不同寻常,他是通过网络请求而来的,解包apk是无法在lib文件夹下找到这个so的.他的存储位置位于
下
方法入口:
经过测试不存在初始化sdk操作.
我用的是969版本的so进行算法分析,附件里面会提供.
App版本13.10.20.45160,可以自行豌豆荚下载.
模拟执行代码:
补环境没什么好说的,看过我文章的问题不大,唯一需要注意的是,需要加上这个
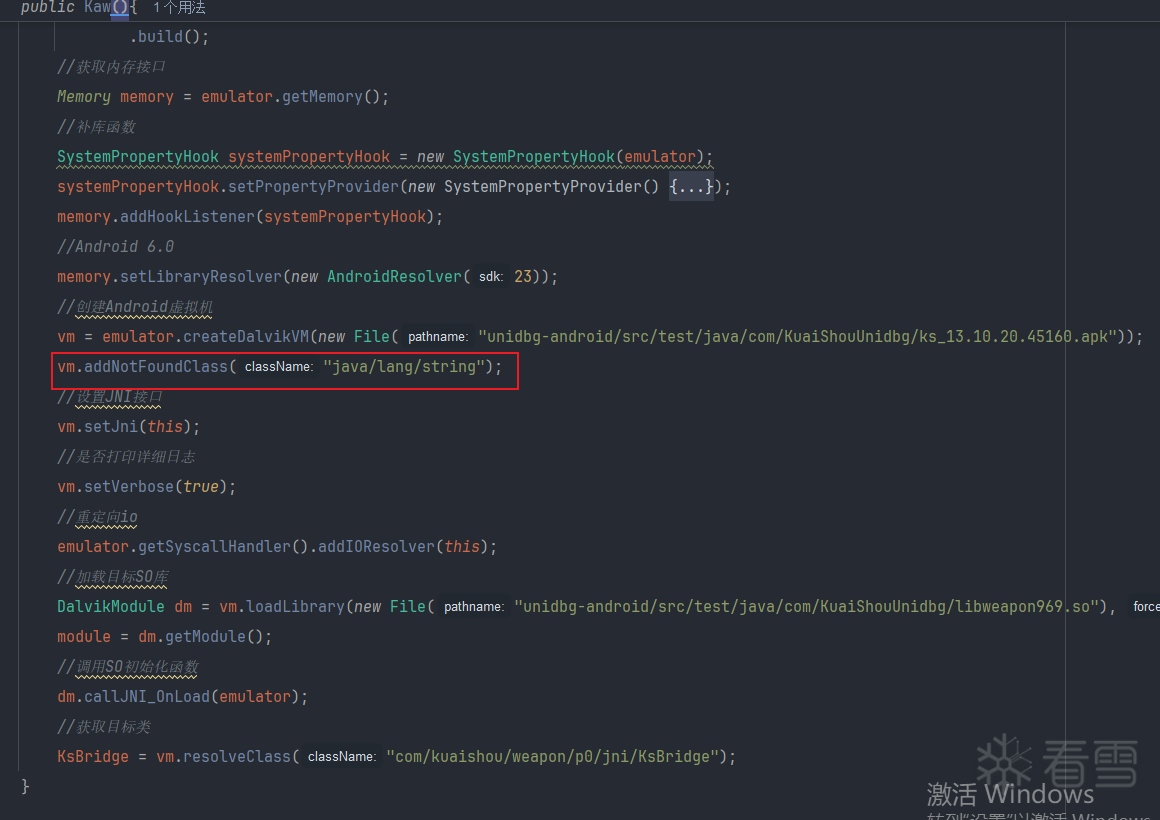
因为样本访问了一个压根就不存在的类,Unidbg没有判断类是否存在的能力,故这会成为一个检测点,这个问题,我也在我的上一篇文章某东的样本里面有讲过,只不过那篇文章侵权删除了.
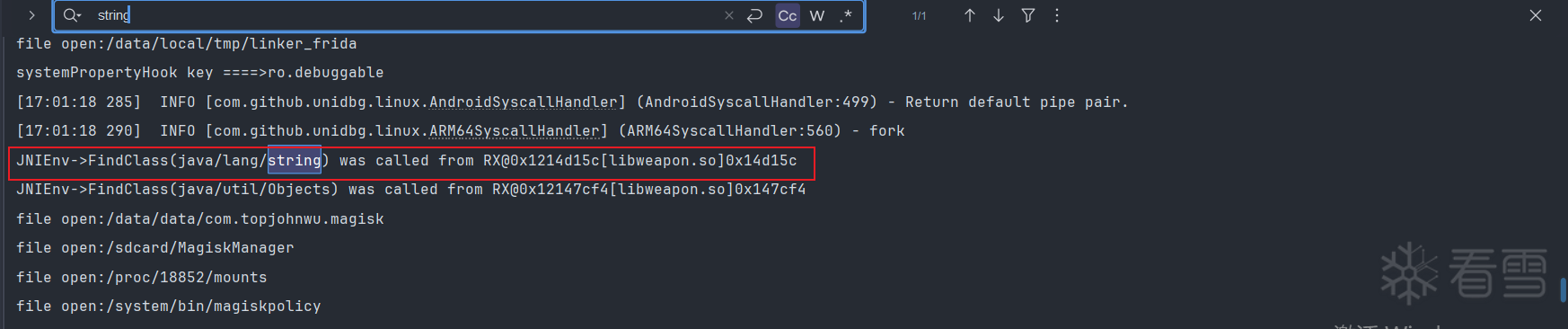
运行发现每次的结果都有些出入,结果是变化的,这对于算法还原来说,是一个干扰,我们需要固定随机因子,常见的随机因子有时间戳随机数这些,而这个demo中,我们只需要固定时间戳即可.
在unidbg项目这个路径下
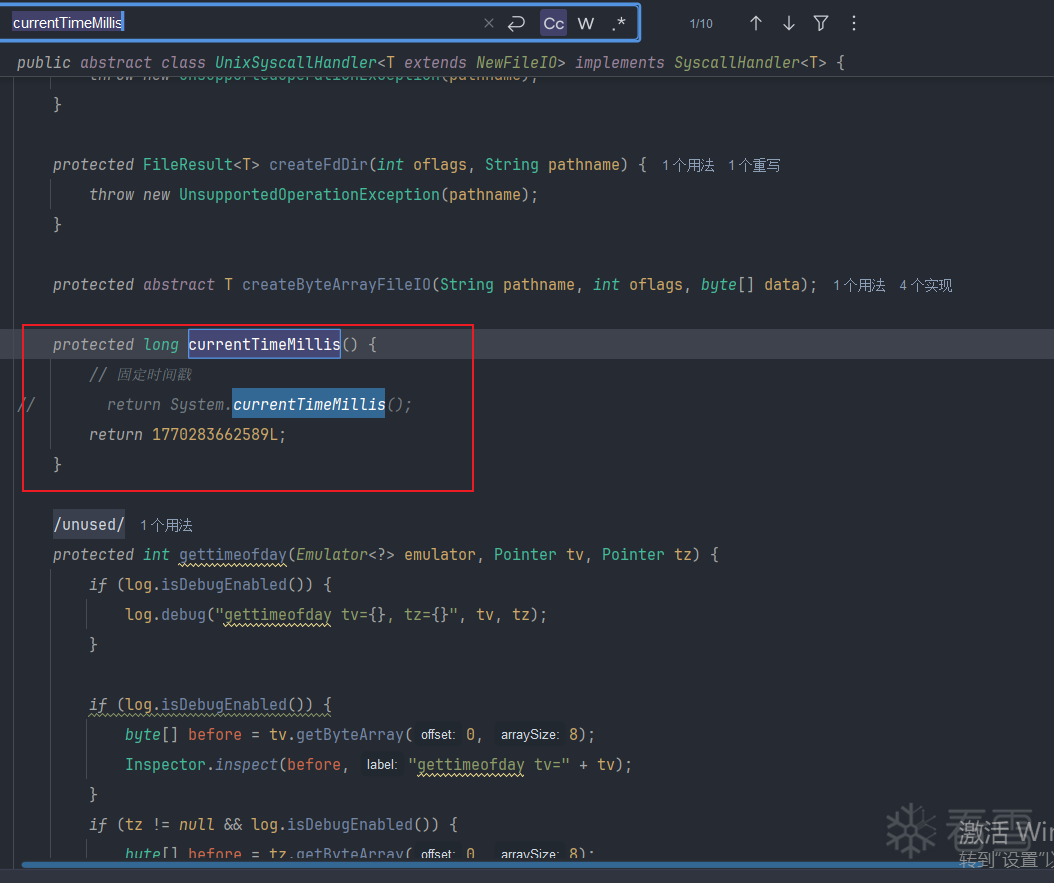
改成一个固定的时间戳即可.
接下来的话,我们就trace一份日志,方便我们后续分析
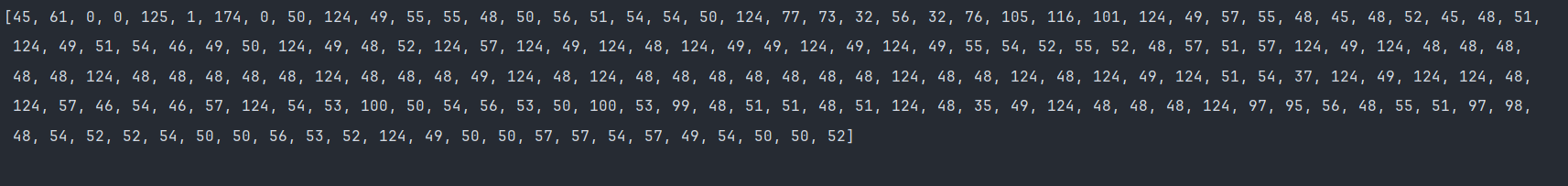
对密文结构进行分析,发现有着base64特殊的指纹痕迹,出现+/=这些字符,而base64的码表中恰好包含了这些字符,我们可以猜测他是经过base64编码过的某段数据.
可以通过hookMemcpy查看数据的流向:
MemCpy日志:
对这部分日志进行分析,离我们结果最近的一条日志中.
有一条182字节数据发生数据流向改变的日志
这会是编码的数据吗,大胆猜测,小心求证.
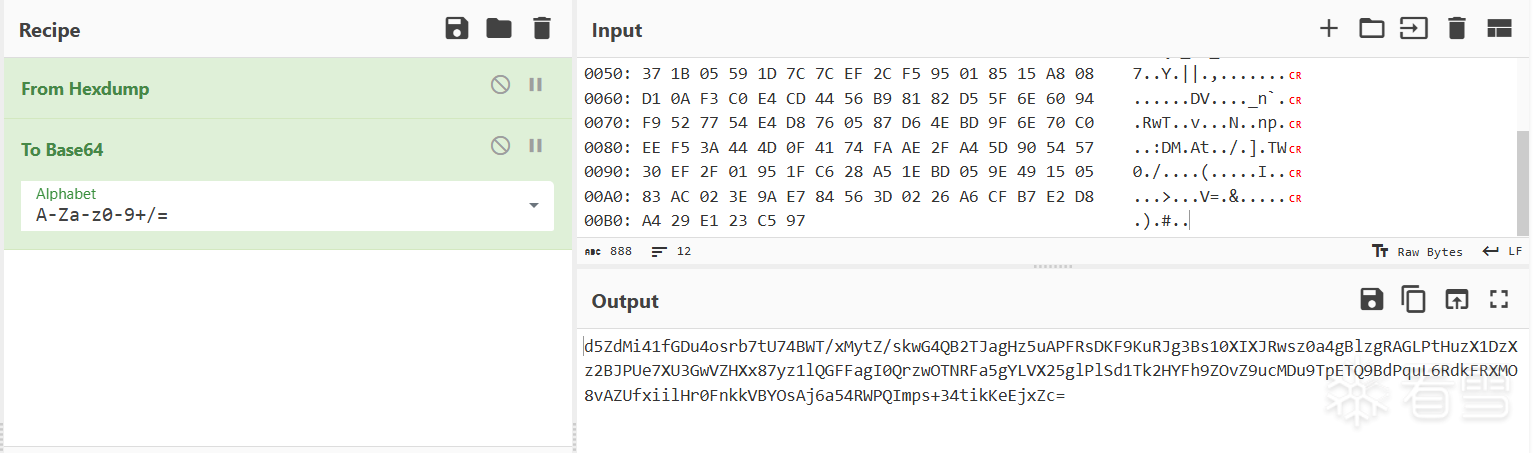
显然不一致,但是通过观察我们的结果是248长度,而此编码结果长度是244,根据base64编码原则3变4,可以算出原始编码字节长度185,也就是说少了三个字节.
对结果进行base64解码:
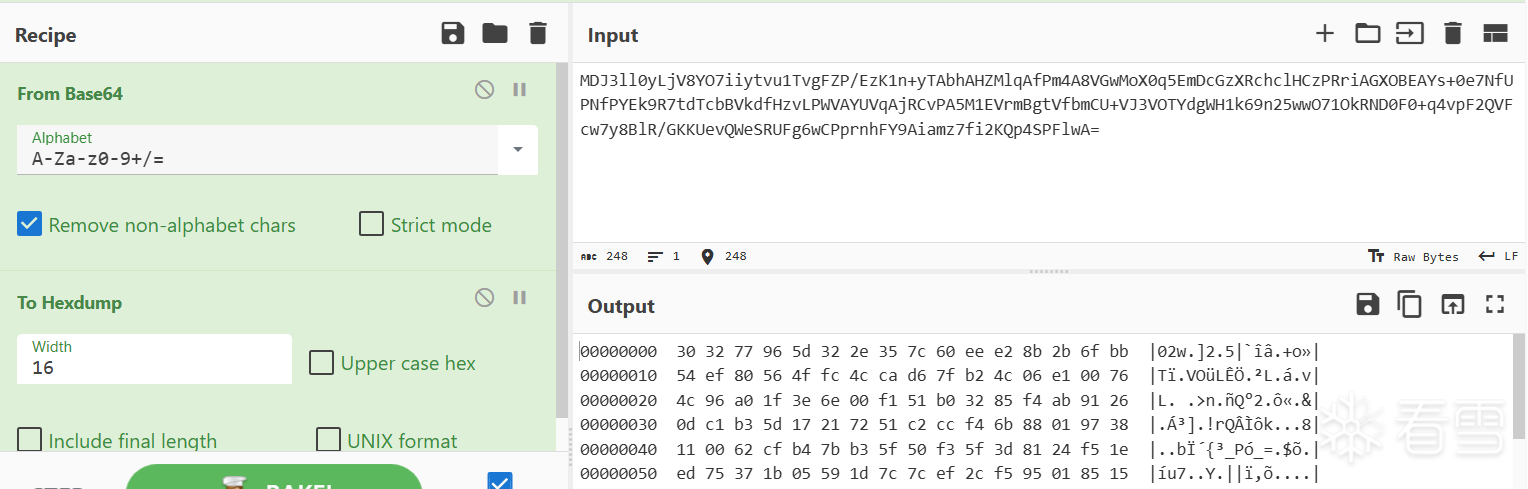
发现前2字节与最后一字节是差异点,掐头去尾之后与那182字节编码结果一致.
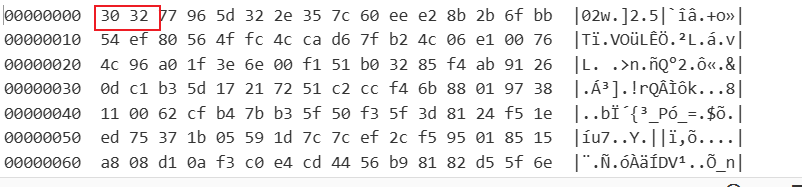
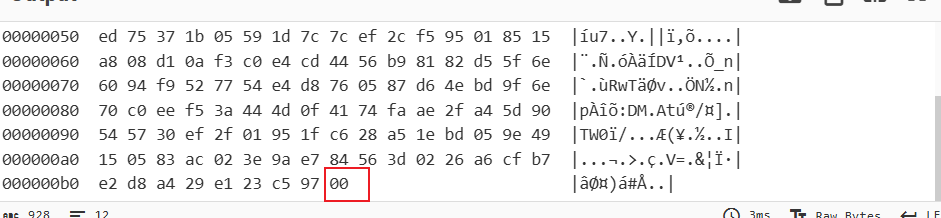
那么我们就可以断定使用了标准的base64编码.
关于前2字节后后一字节,多次抓包解码发现是固定的,这里我们不对此进行探讨,我们主要对那182字节数据来源进行分析.
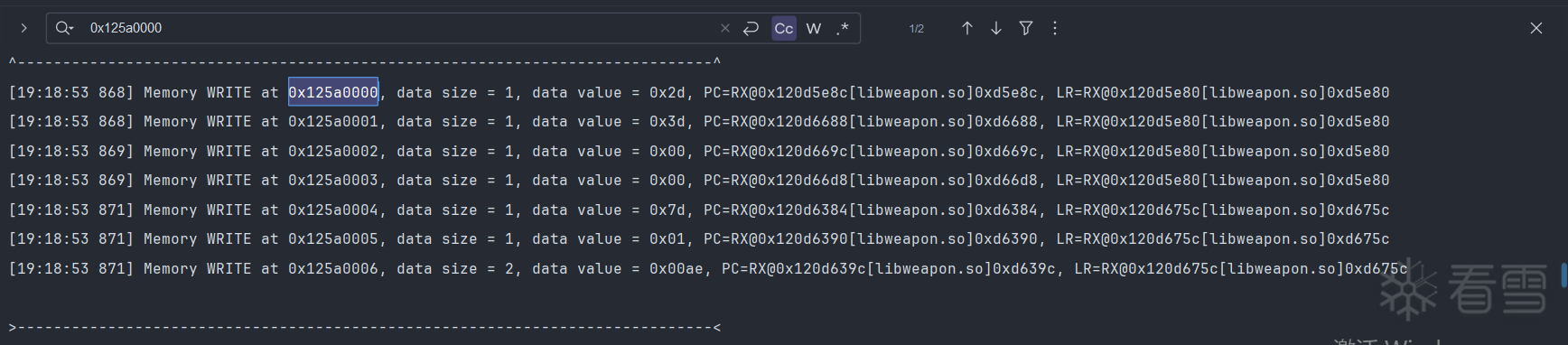
根据memcpy日志此数据来源与此地址1259a000进行拷贝,那就对这个地址进行内存写入追踪
将hookMemcpy与traceMemoryWrite一同开启
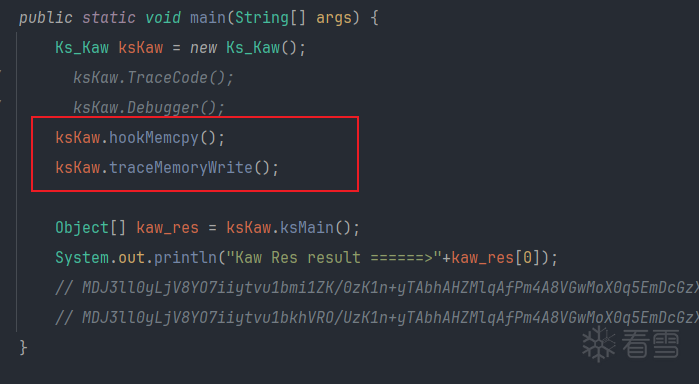
在trace日志里搜索此偏移
前面加一个0
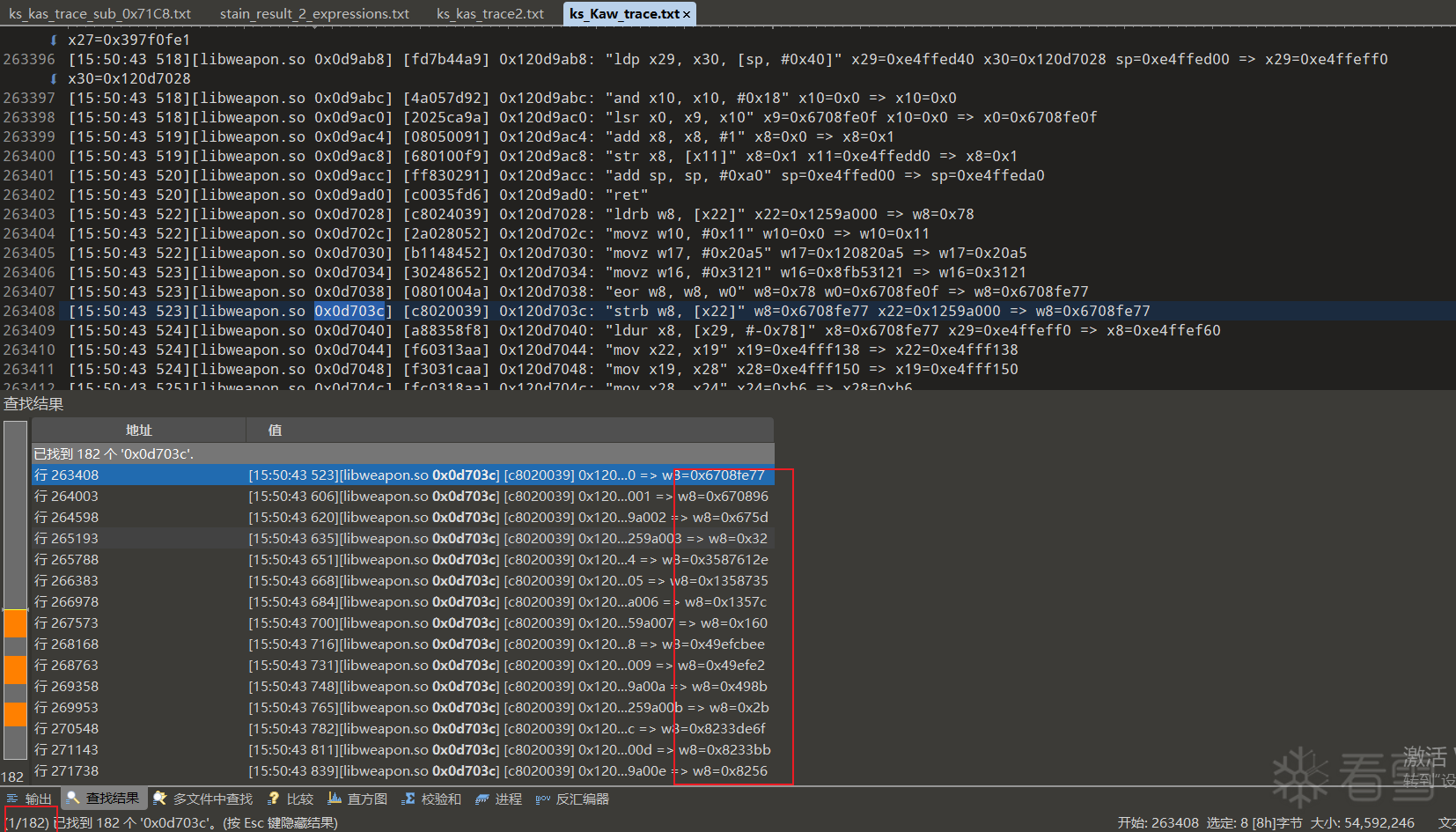
搜索结果恰好182个,结果也对应的上.
分析日志,strb是一条写入数据指令将0x6708fe77数据按一个字节写入到0x1259a000此地址
0x6708fe77来源于上面一条指令
这是一个异或运算
那么现在问题就转换成0x78和0x6708fe0f的来源了.
而0x78又来源于一条读取地址数据的指令
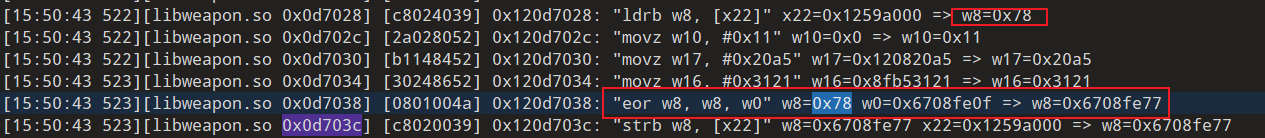
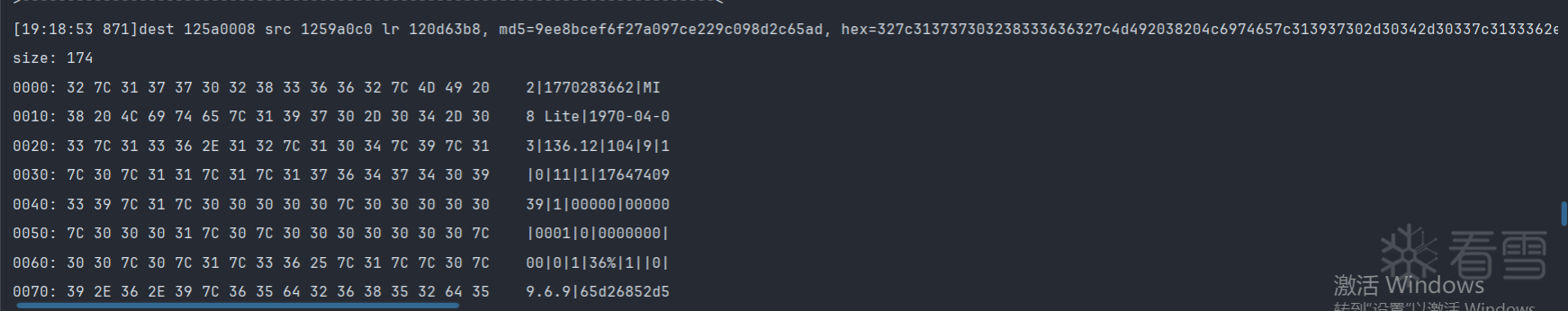
那么直接对这个地址进行追踪,这个地址与我们之前追踪的地址一致,在输出日志中进行搜索这个地址0x1259a000.
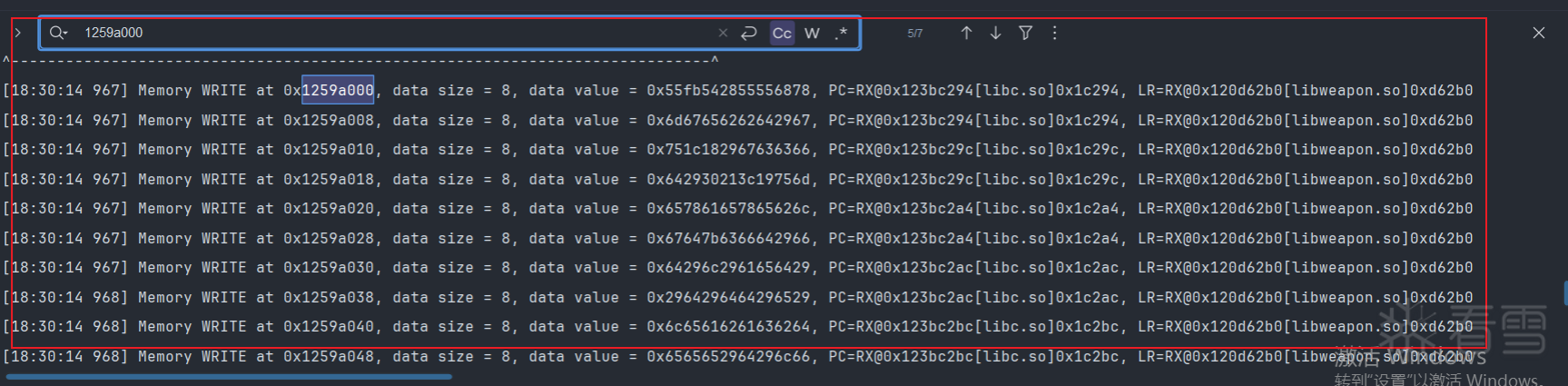
发现他是以8字节进行写入的,并且pc寄存器偏移在libc.so这个so,说明可能是调用memcpy来的在memcpy日志中搜索0x1259a000
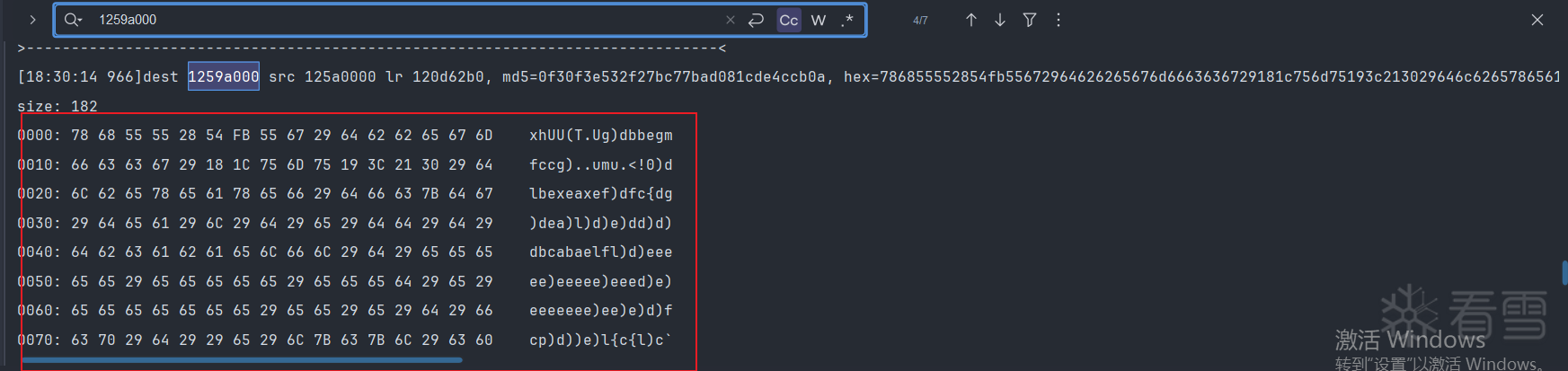
从125a0000拷贝到1259a000
我们继续对这个地址125a0000进行内存写入追踪
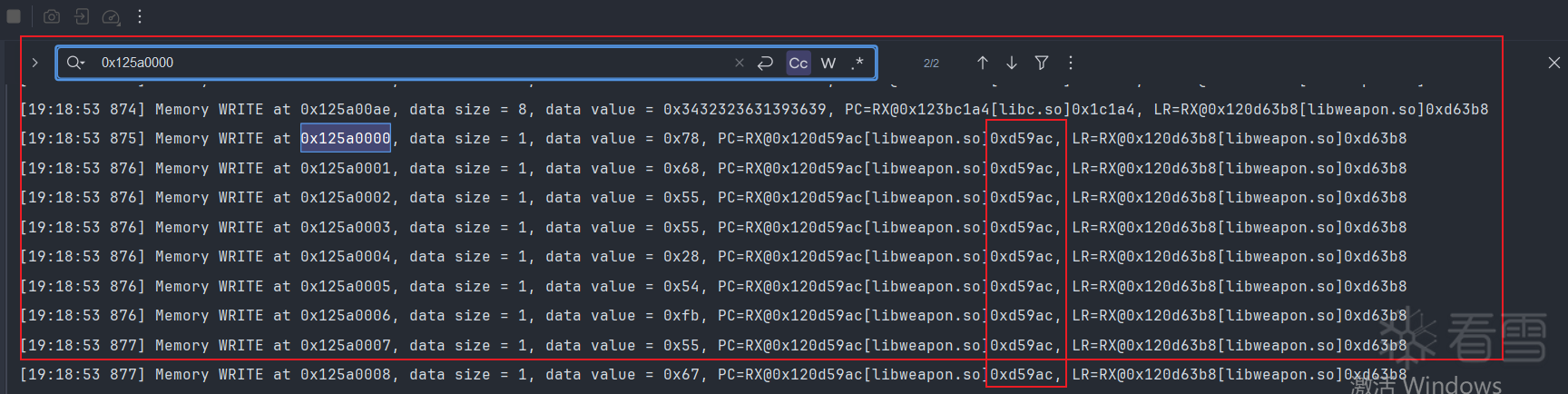
在trace中搜索此偏移,记得在前面加个0
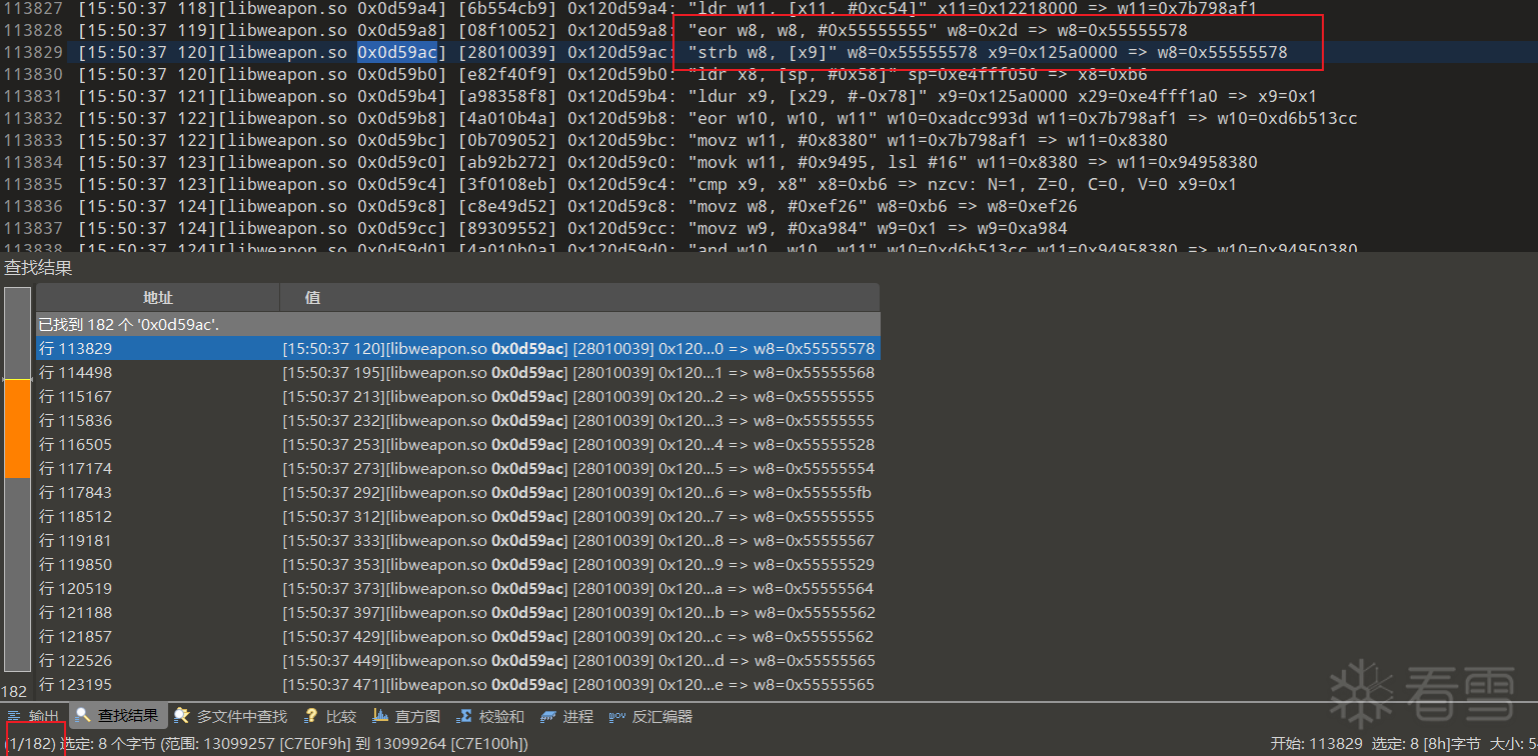
搜索结果有182个也对应的上.
主要涉及汇编指令:
0x55555578 = 0x2d ^ 0x55555555
而现在就要确定0x2d的来源了,0x55555555是个常量.
向上追溯0x2d的来源,发现他是内存读取的
这个地址与我们上面那个是一样的,直接在输出日志中搜索即可,前面10个字节经过测试是固定的,后面的字节就是某手收集的反作弊的数据了.
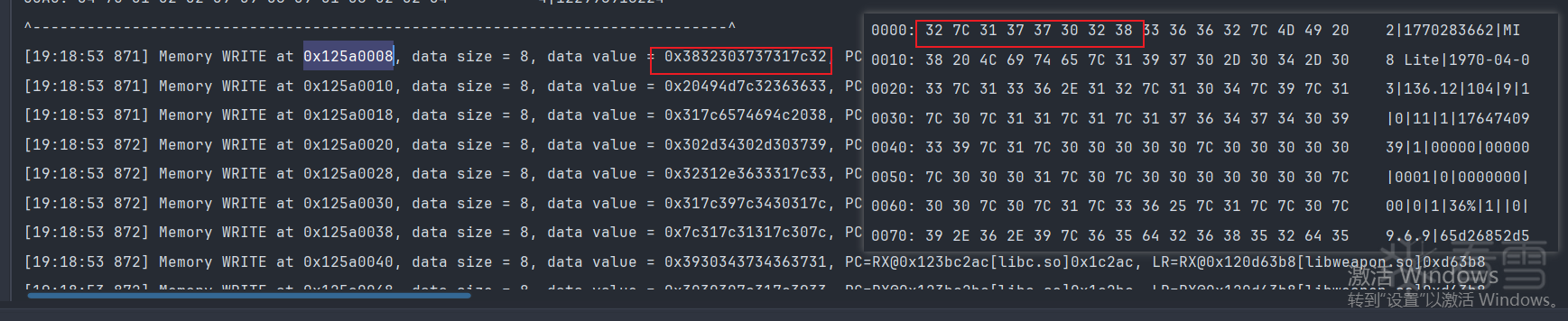
也就是这段数据与0x55555555进行异或操作得到的0x78,....的数据.
现在就差0x6708fe0f这个数据的来源了.
继续在trace日志里进行搜索0x6708fe0f
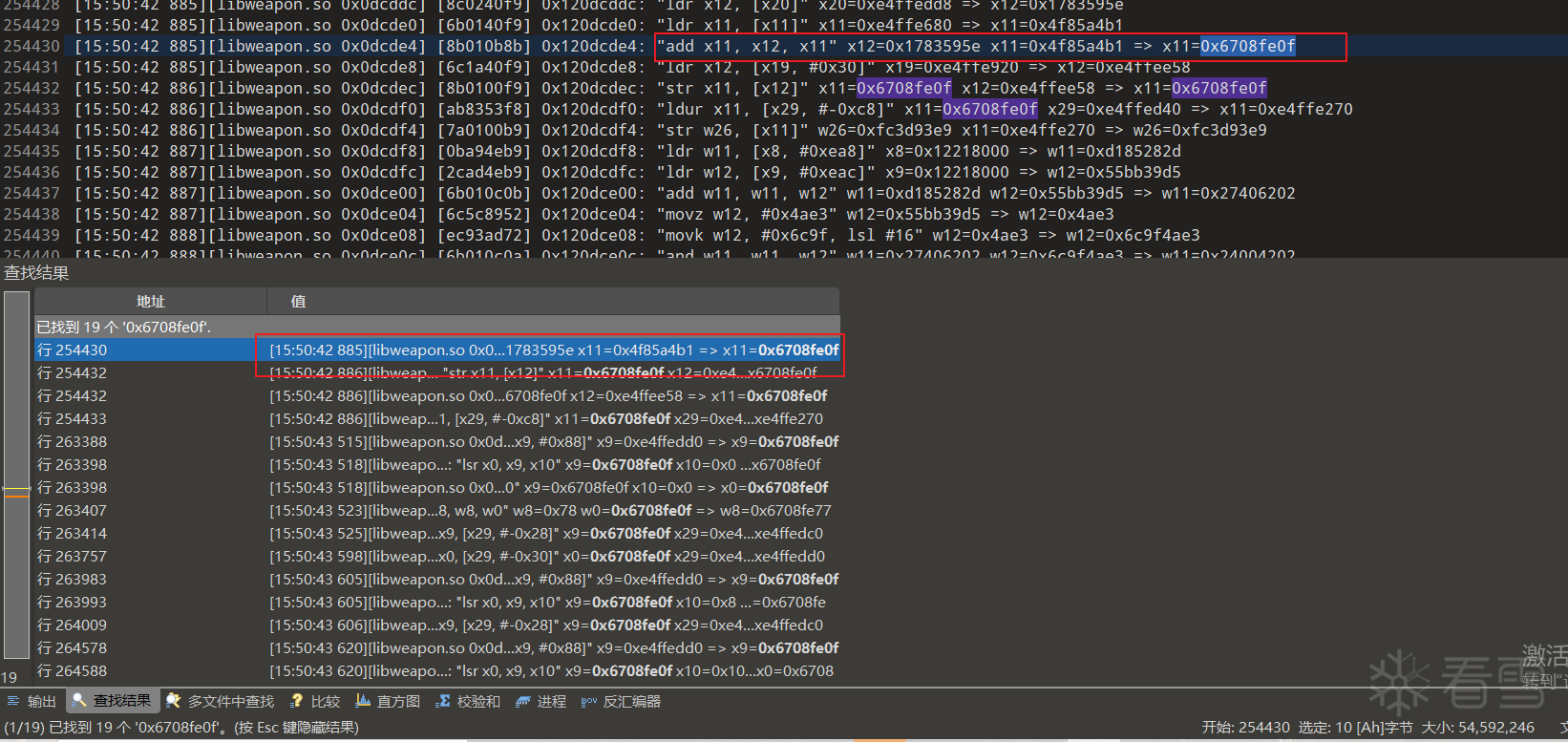
跳转到第一个结果,发现他是加法计算而来的.
继续追溯这两个值.
追溯到最后是在内存中读取的,找不到写入的指令了,猜测是固定的值,改变明文测试一下,发现没有变化,可以暂时固定.
基于我们的分析我们可以写一个解密算法,抓包一个k
aw,尝试进行解密,如果能解密,那就说明我们的算法没有问题.
贴一下自己写的解密算法
最终也是成功解密.
由于工作原因,文章写的比较潦草,还请读者朋友多多海涵.
如果觉得文章写的不错或者对你有帮助的,不妨给笔者点个关注+点赞,笔者在此谢谢大家了.
也欢迎各位搞某手业务的朋友一起交流学习.
Sig
__NStokensig
__NS_sig3/sig3
__NS_xfalcon/sig4
Kas
Kaw
Sig
__NStokensig
__NS_sig3/sig3
__NS_xfalcon/sig4
Kas
Kaw
sign ===> 与sig3类似
deviceInfo
encdata
data
......
sign ===> 与sig3类似
deviceInfo
encdata
data
......
libcore.so ===> sig
libw.so ===> Kas
libweapon969.so ===> Kaw
libkwsgmain.so ===> sig3 sign deviceInfo encdata data等
libksxgs.so ===> sig4
libcore.so ===> sig
libw.so ===> Kas
libweapon969.so ===> Kaw
libkwsgmain.so ===> sig3 sign deviceInfo encdata data等
libksxgs.so ===> sig4
com.kuaishou.android.security.internal.dispatch.JNICLibrary.doCommandNative
doCommandNative(int,Object;)
com.kuaishou.android.security.internal.dispatch.JNICLibrary.doCommandNative
doCommandNative(int,Object;)
int决定不同的功能:
10400 -加密
10405 -旧版本签名
10406 -解密
10411 -未知
10412 -初始化sdk
10413 -未知
10414 -旧版本加密
10416 -未知
10417 -未知
10418 -签名
10419 -未知
int决定不同的功能:
10400 -加密
10405 -旧版本签名
10406 -解密
10411 -未知
10412 -初始化sdk
10413 -未知
10414 -旧版本加密
10416 -未知
10417 -未知
10418 -签名
10419 -未知
10400 -加密 deviceInfo encdata data
10406 -解密
10412 -初始化sdk
10418 -签名 sig3 sign
10400 -加密 deviceInfo encdata data
10406 -解密
10412 -初始化sdk
10418 -签名 sig3 sign
/data/user/0/com.smile.gifmaker/files/.0/lib/9.7.5/1530048325/arm64-v8a/
/data/user/0/com.smile.gifmaker/files/.0/lib/9.7.5/1530048325/arm64-v8a/
Lcom/kuaishou/weapon/p0/jni/KsBridge;->ksMain(I[Ljava/lang/Object;)[Ljava/lang/Object;
Lcom/kuaishou/weapon/p0/jni/KsBridge;->ksMain(I[Ljava/lang/Object;)[Ljava/lang/Object;
package com.KuaiShouUnidbg;
import com.github.unidbg.AndroidEmulator;
import com.github.unidbg.Emulator;
import com.github.unidbg.Module;
import com.github.unidbg.file.FileResult;
import com.github.unidbg.file.IOResolver;
import com.github.unidbg.file.linux.AndroidFileIO;
import com.github.unidbg.linux.android.AndroidEmulatorBuilder;
import com.github.unidbg.linux.android.AndroidResolver;
import com.github.unidbg.linux.android.SystemPropertyHook;
import com.github.unidbg.linux.android.SystemPropertyProvider;
import com.github.unidbg.linux.android.dvm.*;
import com.github.unidbg.linux.android.dvm.array.ArrayObject;
import com.github.unidbg.linux.android.dvm.wrapper.DvmBoolean;
import com.github.unidbg.memory.Memory;
import com.github.unidbg.unix.UnixEmulator;
import java.io.File;
public class Kaw extends AbstractJni implements IOResolver<AndroidFileIO> {
private final AndroidEmulator emulator;
private final VM vm;
private final Module module;
private final DvmClass KsBridge;
@Override
public FileResult<AndroidFileIO> resolve(Emulator<AndroidFileIO> emulator, String pathname, int oflags) {
System.out.println("file open:"+pathname);
switch (pathname){
case "/sbin/su":
case "/su/bin/su":
case "/system/bin/su":
case "/system/xbin/su":
case "/system/sd/xbin/su":
case "/system/bin/failsafe/su":
case "/data/local/xbin/su":
case "/data/local/bin/su":
case "/data/local/su":
case "/vendor/bin/su":
case "/system/sbin/su":
case "/system/bin/.ext/su":
case "/system/usr/we-need-root/su":
case "/cache/su":
case "/data/su":
case "/dev/su":
case "/system/lib/libxposed_art.so":
case "/system/lib64/libxposed_art.so":
case "/storage/emulated/0/gadget":
case "/data/local/tmp/linker_frida":
case "/data/data/com.topjohnwu.magisk":
case "/sdcard/MagiskManager":
case "/system/bin/magiskpolicy":
case "/system/bin/magisk":
case "/data/adb/magisk":
case "/system/lib/libhoudini.so":
return FileResult.failed(UnixEmulator.EACCES);
case "/proc/10720/mounts":
case "/proc/cpuinfo":
case "/proc/meminfo":
}
return null;
}
public Kaw(){
//创建模拟器实例 (ARM32架构)
emulator = AndroidEmulatorBuilder.for64Bit()
.setProcessName("com.smile.gifmaker")
.build();
//获取内存接口
Memory memory = emulator.getMemory();
//补库函数
SystemPropertyHook systemPropertyHook = new SystemPropertyHook(emulator);
systemPropertyHook.setPropertyProvider(new SystemPropertyProvider() {
@Override
public String getProperty(String key) {
System.out.println("systemPropertyHook key ====>"+key);
switch(key){
case "ro.product.device":
return "platina";
case "ro.product.cpu.abilist32":
return "armeabi-v7a,armeabi";
case "ro.product.cpu.abilist":
return "arm64-v8a,armeabi-v7a,armeabi";
case "ro.product.cpu.abi":
return "arm64-v8a";
case "ro.dalvik.vm.isa.arm":
return "";
case "ro.build.product":
return "platina";
case "ro.arch":
return "";
case "nemud.player_architecture":
return "";
case "dalvik.vm.isa.x86.variant":
return "";
case "ro.debuggable":
return "0";
case "ro.product.model":
return "MI 8 Lite";
case "ro.adb.secure":
return "1";
case "ro.secure":
return "1";
}
return null;
}
});
memory.addHookListener(systemPropertyHook);
//Android 6.0
memory.setLibraryResolver(new AndroidResolver(23));
//创建Android虚拟机
vm = emulator.createDalvikVM(new File("unidbg-android/src/test/java/com/KuaiShouUnidbg/ks_13.10.20.45160.apk"));
vm.addNotFoundClass("java/lang/string");
//设置JNI接口
vm.setJni(this);
//是否打印详细日志
vm.setVerbose(true);
//重定向io
emulator.getSyscallHandler().addIOResolver(this);
//加载目标SO库
DalvikModule dm = vm.loadLibrary(new File("unidbg-android/src/test/java/com/KuaiShouUnidbg/libweapon969.so"), true);
module = dm.getModule();
//调用SO初始化函数
dm.callJNI_OnLoad(emulator);
//获取目标类
KsBridge = vm.resolveClass("com/kuaishou/weapon/p0/jni/KsBridge");
}
@Override
public int getStaticIntField(BaseVM vm, DvmClass dvmClass, String signature) {
switch (signature){
case "com/kuaishou/weapon/p0/jni/Engine->jPid:I":
return -0x1;
}
return super.getStaticIntField(vm,dvmClass,signature);
}
@Override
public DvmObject<?> callObjectMethodV(BaseVM vm, DvmObject<?> dvmObject, String signature, VaList vaList) {
switch (signature) {
case "android/app/ActivityThread->getApplication()Landroid/app/Application;":
return vm.resolveClass("android/app/Application").newObject(null);
}
return super.callObjectMethodV(vm,dvmObject,signature,vaList);
}
@Override
public boolean callBooleanMethodV(BaseVM vm, DvmObject<?> dvmObject, String signature, VaList vaList) {
switch (signature) {
case "java/lang/Boolean->booleanValue()Z":
Boolean bool = (Boolean) (dvmObject.getValue());
return bool.booleanValue();
}
return super.callBooleanMethodV(vm,dvmObject,signature,vaList);
}
@Override
public DvmObject<?> callStaticObjectMethodV(BaseVM vm, DvmClass dvmClass, String signature, VaList vaList) {
switch (signature) {
case "com/kuaishou/weapon/p0/jni/KsBridge->ksMain2(I[Ljava/lang/Object;)Ljava/lang/Object;":
int int_arg = vaList.getIntArg(0);
Object obj_arg = vaList.getObjectArg(0);
System.out.println("int arg =====>"+ int_arg + ", Object arg =====>"+obj_arg);
switch (int_arg){
case 73629481:
return DvmBoolean.valueOf(vm,true);
case 45782319:
return new StringObject(vm,"[]");
}
}
return super.callStaticObjectMethodV(vm,dvmClass,signature,vaList);
}
public Object[] ksMain(){
//调用静态native方法
DvmObject<?> result = KsBridge.callStaticJniMethodObject(
emulator,
"ksMain(I[Ljava/lang/Object;)[Ljava/lang/Object;",
26329714,
new ArrayObject(
new StringObject(
vm,
"1|1764741174|CPH2491|1970-04-03|136.12|104|9|1|0|11|1|1764740939|1|00100|00000|0000|0|1100000|00|00|1|36%|1||0|9.6.9|65d26852d5c03303|0#1|000|a_8073ab0644622854|122996916224"
)
)
);
//获取并返回结果
return (Object[]) result.getValue();
}
public static void main(String[] args) {
Kaw ksKaw = new Kaw();
Object[] kaw_res = ksKaw.ksMain();
System.out.println("Kaw Res result ======>"+kaw_res[0]);
}
}
package com.KuaiShouUnidbg;
import com.github.unidbg.AndroidEmulator;
import com.github.unidbg.Emulator;
import com.github.unidbg.Module;
import com.github.unidbg.file.FileResult;
import com.github.unidbg.file.IOResolver;
import com.github.unidbg.file.linux.AndroidFileIO;
import com.github.unidbg.linux.android.AndroidEmulatorBuilder;
import com.github.unidbg.linux.android.AndroidResolver;
import com.github.unidbg.linux.android.SystemPropertyHook;
import com.github.unidbg.linux.android.SystemPropertyProvider;
import com.github.unidbg.linux.android.dvm.*;
import com.github.unidbg.linux.android.dvm.array.ArrayObject;
import com.github.unidbg.linux.android.dvm.wrapper.DvmBoolean;
import com.github.unidbg.memory.Memory;
import com.github.unidbg.unix.UnixEmulator;
import java.io.File;
public class Kaw extends AbstractJni implements IOResolver<AndroidFileIO> {
private final AndroidEmulator emulator;
private final VM vm;
private final Module module;
private final DvmClass KsBridge;
@Override
public FileResult<AndroidFileIO> resolve(Emulator<AndroidFileIO> emulator, String pathname, int oflags) {
System.out.println("file open:"+pathname);
switch (pathname){
case "/sbin/su":
case "/su/bin/su":
case "/system/bin/su":
case "/system/xbin/su":
case "/system/sd/xbin/su":
case "/system/bin/failsafe/su":
case "/data/local/xbin/su":
case "/data/local/bin/su":
case "/data/local/su":
case "/vendor/bin/su":
case "/system/sbin/su":
case "/system/bin/.ext/su":
case "/system/usr/we-need-root/su":
case "/cache/su":
case "/data/su":
case "/dev/su":
case "/system/lib/libxposed_art.so":
case "/system/lib64/libxposed_art.so":
case "/storage/emulated/0/gadget":
case "/data/local/tmp/linker_frida":
case "/data/data/com.topjohnwu.magisk":
case "/sdcard/MagiskManager":
case "/system/bin/magiskpolicy":
case "/system/bin/magisk":
case "/data/adb/magisk":
case "/system/lib/libhoudini.so":
return FileResult.failed(UnixEmulator.EACCES);
case "/proc/10720/mounts":
case "/proc/cpuinfo":
case "/proc/meminfo":
}
return null;
}
public Kaw(){
//创建模拟器实例 (ARM32架构)
emulator = AndroidEmulatorBuilder.for64Bit()
.setProcessName("com.smile.gifmaker")
.build();
//获取内存接口
Memory memory = emulator.getMemory();
//补库函数
SystemPropertyHook systemPropertyHook = new SystemPropertyHook(emulator);
systemPropertyHook.setPropertyProvider(new SystemPropertyProvider() {
@Override
public String getProperty(String key) {
System.out.println("systemPropertyHook key ====>"+key);
switch(key){
case "ro.product.device":
return "platina";
case "ro.product.cpu.abilist32":
return "armeabi-v7a,armeabi";
case "ro.product.cpu.abilist":
return "arm64-v8a,armeabi-v7a,armeabi";
case "ro.product.cpu.abi":
return "arm64-v8a";
case "ro.dalvik.vm.isa.arm":
return "";
case "ro.build.product":
return "platina";
case "ro.arch":
return "";
case "nemud.player_architecture":
return "";
case "dalvik.vm.isa.x86.variant":
return "";
case "ro.debuggable":
return "0";
case "ro.product.model":
return "MI 8 Lite";
case "ro.adb.secure":
return "1";
case "ro.secure":
return "1";
}
return null;
}
});
memory.addHookListener(systemPropertyHook);
//Android 6.0
memory.setLibraryResolver(new AndroidResolver(23));
//创建Android虚拟机
vm = emulator.createDalvikVM(new File("unidbg-android/src/test/java/com/KuaiShouUnidbg/ks_13.10.20.45160.apk"));
vm.addNotFoundClass("java/lang/string");
//设置JNI接口
vm.setJni(this);
//是否打印详细日志
vm.setVerbose(true);
//重定向io
emulator.getSyscallHandler().addIOResolver(this);
//加载目标SO库
DalvikModule dm = vm.loadLibrary(new File("unidbg-android/src/test/java/com/KuaiShouUnidbg/libweapon969.so"), true);
module = dm.getModule();
//调用SO初始化函数
dm.callJNI_OnLoad(emulator);
//获取目标类
KsBridge = vm.resolveClass("com/kuaishou/weapon/p0/jni/KsBridge");
}
@Override
public int getStaticIntField(BaseVM vm, DvmClass dvmClass, String signature) {
switch (signature){
case "com/kuaishou/weapon/p0/jni/Engine->jPid:I":
return -0x1;
}
return super.getStaticIntField(vm,dvmClass,signature);
}
@Override
public DvmObject<?> callObjectMethodV(BaseVM vm, DvmObject<?> dvmObject, String signature, VaList vaList) {
switch (signature) {
case "android/app/ActivityThread->getApplication()Landroid/app/Application;":
return vm.resolveClass("android/app/Application").newObject(null);
}
return super.callObjectMethodV(vm,dvmObject,signature,vaList);
}
@Override
public boolean callBooleanMethodV(BaseVM vm, DvmObject<?> dvmObject, String signature, VaList vaList) {
switch (signature) {
case "java/lang/Boolean->booleanValue()Z":
Boolean bool = (Boolean) (dvmObject.getValue());
return bool.booleanValue();
}
return super.callBooleanMethodV(vm,dvmObject,signature,vaList);
}
@Override
public DvmObject<?> callStaticObjectMethodV(BaseVM vm, DvmClass dvmClass, String signature, VaList vaList) {
switch (signature) {
case "com/kuaishou/weapon/p0/jni/KsBridge->ksMain2(I[Ljava/lang/Object;)Ljava/lang/Object;":
int int_arg = vaList.getIntArg(0);
Object obj_arg = vaList.getObjectArg(0);
System.out.println("int arg =====>"+ int_arg + ", Object arg =====>"+obj_arg);
switch (int_arg){
case 73629481:
return DvmBoolean.valueOf(vm,true);
case 45782319:
return new StringObject(vm,"[]");
}
}
return super.callStaticObjectMethodV(vm,dvmClass,signature,vaList);
}
public Object[] ksMain(){
//调用静态native方法
DvmObject<?> result = KsBridge.callStaticJniMethodObject(
emulator,
"ksMain(I[Ljava/lang/Object;)[Ljava/lang/Object;",
26329714,
new ArrayObject(
new StringObject(
vm,
"1|1764741174|CPH2491|1970-04-03|136.12|104|9|1|0|11|1|1764740939|1|00100|00000|0000|0|1100000|00|00|1|36%|1||0|9.6.9|65d26852d5c03303|0#1|000|a_8073ab0644622854|122996916224"
)
)
);
//获取并返回结果
return (Object[]) result.getValue();
}
public static void main(String[] args) {
Kaw ksKaw = new Kaw();
Object[] kaw_res = ksKaw.ksMain();
System.out.println("Kaw Res result ======>"+kaw_res[0]);
}
}
JNIEnv->FindClass(java/lang/string) was called from RX@0x1214d15c[libweapon.so]0x14d15c
JNIEnv->FindClass(java/lang/string) was called from RX@0x1214d15c[libweapon.so]0x14d15c
unidbg-master\unidbg-api\src\main\java\com\github\unidbg\unix\UnixSyscallHandler.java
unidbg-master\unidbg-api\src\main\java\com\github\unidbg\unix\UnixSyscallHandler.java
void TraceCode(){
String traceFile = "unidbg-android/src/test/java/com/kuaishou/ks_Kaw_trace.txt";
PrintStream traceStream = null;
try{
traceStream = new PrintStream(new FileOutputStream(traceFile), true);
} catch (FileNotFoundException e) {
e.printStackTrace();
}
emulator.traceCode(module.base,module.base+module.size).setRedirect(traceStream);
}
void TraceCode(){
String traceFile = "unidbg-android/src/test/java/com/kuaishou/ks_Kaw_trace.txt";
PrintStream traceStream = null;
try{
traceStream = new PrintStream(new FileOutputStream(traceFile), true);
} catch (FileNotFoundException e) {
e.printStackTrace();
}
emulator.traceCode(module.base,module.base+module.size).setRedirect(traceStream);
}
MDJ3ll0yLjV8YO7iiytvu1TvgFZP/EzK1n+yTAbhAHZMlqAfPm4A8VGwMoX0q5EmDcGzXRchclHCzPRriAGXOBEAYs+0e7NfUPNfPYEk9R7tdTcbBVkdfHzvLPWVAYUVqAjRCvPA5M1EVrmBgtVfbmCU+VJ3VOTYdgWH1k69n25wwO71OkRND0F0+q4vpF2QVFcw7y8BlR/GKKUevQWeSRUFg6wCPprnhFY9Aiamz7fi2KQp4SPFlwA=
MDJ3ll0yLjV8YO7iiytvu1TvgFZP/EzK1n+yTAbhAHZMlqAfPm4A8VGwMoX0q5EmDcGzXRchclHCzPRriAGXOBEAYs+0e7NfUPNfPYEk9R7tdTcbBVkdfHzvLPWVAYUVqAjRCvPA5M1EVrmBgtVfbmCU+VJ3VOTYdgWH1k69n25wwO71OkRND0F0+q4vpF2QVFcw7y8BlR/GKKUevQWeSRUFg6wCPprnhFY9Aiamz7fi2KQp4SPFlwA=
void hookMemcpy() {
emulator.attach().addBreakPoint(module.findSymbolByName("memcpy").getAddress(), new BreakPointCallback() {
@Override
public boolean onHit(Emulator<?> emulator, long address) {
RegisterContext context = emulator.getContext();
int len = context.getIntArg(2);
UnidbgPointer pointer1 = context.getPointerArg(0);
UnidbgPointer pointer2 = context.getPointerArg(1);
UnidbgPointer pointer3 = context.getLRPointer();
Inspector.inspect(pointer2.getByteArray(0, len), "dest " + Long.toHexString(pointer1.peer) + " src " + Long.toHexString(pointer2.peer) + " lr " + Long.toHexString(pointer3.peer));
return true;
}
});
}
void hookMemcpy() {
emulator.attach().addBreakPoint(module.findSymbolByName("memcpy").getAddress(), new BreakPointCallback() {
@Override
public boolean onHit(Emulator<?> emulator, long address) {
RegisterContext context = emulator.getContext();
int len = context.getIntArg(2);
UnidbgPointer pointer1 = context.getPointerArg(0);
UnidbgPointer pointer2 = context.getPointerArg(1);
UnidbgPointer pointer3 = context.getLRPointer();
Inspector.inspect(pointer2.getByteArray(0, len), "dest " + Long.toHexString(pointer1.peer) + " src " + Long.toHexString(pointer2.peer) + " lr " + Long.toHexString(pointer3.peer));
return true;
}
});
}
>-----------------------------------------------------------------------------<
[17:28:11 869]dest 1259a0c0 src 1259a180 lr 12406ecc, md5=05d2981ffb38a02ec96e41fad770b371, hex=327c313737303238333636327c4d492038204c6974657c313937302d30342d30337c3133362e31327c3130347c397c317c307c31317c317c313736343734303933397c317c30303030307c30303030307c303030317c307c303030303030307c30307c307c317c3336257c317c7c307c392e362e397c363564323638353264356330333330337c3023317c3030307c615f383037336162303634343632323835347c31323239393639313632323400
size: 175
0000: 32 7C 31 37 37 30 32 38 33 36 36 32 7C 4D 49 20 2|1770283662|MI
0010: 38 20 4C 69 74 65 7C 31 39 37 30 2D 30 34 2D 30 8 Lite|1970-04-0
0020: 33 7C 31 33 36 2E 31 32 7C 31 30 34 7C 39 7C 31 3|136.12|104|9|1
0030: 7C 30 7C 31 31 7C 31 7C 31 37 36 34 37 34 30 39 |0|11|1|17647409
0040: 33 39 7C 31 7C 30 30 30 30 30 7C 30 30 30 30 30 39|1|00000|00000
0050: 7C 30 30 30 31 7C 30 7C 30 30 30 30 30 30 30 7C |0001|0|0000000|
0060: 30 30 7C 30 7C 31 7C 33 36 25 7C 31 7C 7C 30 7C 00|0|1|36%|1||0|
0070: 39 2E 36 2E 39 7C 36 35 64 32 36 38 35 32 64 35 9.6.9|65d26852d5
0080: 63 30 33 33 30 33 7C 30 23 31 7C 30 30 30 7C 61 c03303|0
0090: 5F 38 30 37 33 61 62 30 36 34 34 36 32 32 38 35 _8073ab064462285
00A0: 34 7C 31 32 32 39 39 36 39 31 36 32 32 34 00 4|122996916224.
^-----------------------------------------------------------------------------^
>-----------------------------------------------------------------------------<
[17:28:11 881]dest 125a0008 src 1259a0c0 lr 120d63b8, md5=9ee8bcef6f27a097ce229c098d2c65ad, hex=327c313737303238333636327c4d492038204c6974657c313937302d30342d30337c3133362e31327c3130347c397c317c307c31317c317c313736343734303933397c317c30303030307c30303030307c303030317c307c303030303030307c30307c307c317c3336257c317c7c307c392e362e397c363564323638353264356330333330337c3023317c3030307c615f383037336162303634343632323835347c313232393936393136323234
size: 174
0000: 32 7C 31 37 37 30 32 38 33 36 36 32 7C 4D 49 20 2|1770283662|MI
0010: 38 20 4C 69 74 65 7C 31 39 37 30 2D 30 34 2D 30 8 Lite|1970-04-0
0020: 33 7C 31 33 36 2E 31 32 7C 31 30 34 7C 39 7C 31 3|136.12|104|9|1
0030: 7C 30 7C 31 31 7C 31 7C 31 37 36 34 37 34 30 39 |0|11|1|17647409
0040: 33 39 7C 31 7C 30 30 30 30 30 7C 30 30 30 30 30 39|1|00000|00000
0050: 7C 30 30 30 31 7C 30 7C 30 30 30 30 30 30 30 7C |0001|0|0000000|
0060: 30 30 7C 30 7C 31 7C 33 36 25 7C 31 7C 7C 30 7C 00|0|1|36%|1||0|
0070: 39 2E 36 2E 39 7C 36 35 64 32 36 38 35 32 64 35 9.6.9|65d26852d5
0080: 63 30 33 33 30 33 7C 30 23 31 7C 30 30 30 7C 61 c03303|0
0090: 5F 38 30 37 33 61 62 30 36 34 34 36 32 32 38 35 _8073ab064462285
00A0: 34 7C 31 32 32 39 39 36 39 31 36 32 32 34 4|122996916224
^-----------------------------------------------------------------------------^
>-----------------------------------------------------------------------------<
[17:28:11 888]dest 1259a000 src 125a0000 lr 120d62b0, md5=0f30f3e532f27bc77bad081cde4ccb0a, hex=786855552854fb55672964626265676d6663636729181c756d75193c213029646c6265786561786566296466637b646729646561296c29642965296464296429646263616261656c666c296429656565656529656565656529656565642965296565656565656529656529652964296663702964292965296c7b637b6c2963603167636d60673160366566666566296576642965656529340a6d6562663437656361616367676d6061296467676c6c636c6463676761
size: 182
0000: 78 68 55 55 28 54 FB 55 67 29 64 62 62 65 67 6D xhUU(T.Ug)dbbegm
0010: 66 63 63 67 29 18 1C 75 6D 75 19 3C 21 30 29 64 fccg)..umu.<!0)d
0020: 6C 62 65 78 65 61 78 65 66 29 64 66 63 7B 64 67 lbexeaxef)dfc{dg
0030: 29 64 65 61 29 6C 29 64 29 65 29 64 64 29 64 29 )dea)l)d)e)dd)d)
0040: 64 62 63 61 62 61 65 6C 66 6C 29 64 29 65 65 65 dbcabaelfl)d)eee
0050: 65 65 29 65 65 65 65 65 29 65 65 65 64 29 65 29 ee)eeeee)eeed)e)
0060: 65 65 65 65 65 65 65 29 65 65 29 65 29 64 29 66 eeeeeee)ee)e)d)f
0070: 63 70 29 64 29 29 65 29 6C 7B 63 7B 6C 29 63 60 cp)d))e)l{c{l)c`
0080: 31 67 63 6D 60 67 31 60 36 65 66 66 65 66 29 65 1gcm`g1`6effef)e
0090: 76 64 29 65 65 65 29 34 0A 6D 65 62 66 34 37 65 vd)eee)4.mebf47e
00A0: 63 61 61 63 67 67 6D 60 61 29 64 67 67 6C 6C 63 caacggm`a)dggllc
00B0: 6C 64 63 67 67 61 ldcgga
^-----------------------------------------------------------------------------^
>-----------------------------------------------------------------------------<
[17:28:11 900]dest e4ffe280 src e4ffedd8 lr 120db238, md5=0a1cd535cc56952ffe44358d5554ecf2, hex=5e59831700000000786ac28d000000004e18992500000000d381977200000000f4f3de9a0000000016ef769800000000cdcb2a740000000012de039100000000786ac29800000000f44fa2a900000000fdd33891000000004e1899ab0000000001000000000000004fd3be2a00000000f65721a900000000f39321f400000000
size: 128
0000: 5E 59 83 17 00 00 00 00 78 6A C2 8D 00 00 00 00 ^Y......xj......
0010: 4E 18 99 25 00 00 00 00 D3 81 97 72 00 00 00 00 N..%.......r....
0020: F4 F3 DE 9A 00 00 00 00 16 EF 76 98 00 00 00 00 ..........v.....
0030: CD CB 2A 74 00 00 00 00 12 DE 03 91 00 00 00 00 ..*t............
0040: 78 6A C2 98 00 00 00 00 F4 4F A2 A9 00 00 00 00 xj.......O......
0050: FD D3 38 91 00 00 00 00 4E 18 99 AB 00 00 00 00 ..8.....N.......
0060: 01 00 00 00 00 00 00 00 4F D3 BE 2A 00 00 00 00 ........O..*....
0070: F6 57 21 A9 00 00 00 00 F3 93 21 F4 00 00 00 00 .W!.......!.....
^-----------------------------------------------------------------------------^
>-----------------------------------------------------------------------------<
[17:28:11 924]dest e4ffe1e0 src e4ffedd8 lr 120db238, md5=c99335f5f1706fa64cbff772608ee64e, hex=5e59831700000000786ac28d000000004e18992500000000d381977200000000f4f3de9a0000000016ef769800000000cdcb2a740000000012de039100000000786ac29800000000f44fa2a900000000fdd33891000000004e1899ab0000000002000000000000004fd3be2a00000000f65721a900000000f39321f400000000
size: 128
0000: 5E 59 83 17 00 00 00 00 78 6A C2 8D 00 00 00 00 ^Y......xj......
0010: 4E 18 99 25 00 00 00 00 D3 81 97 72 00 00 00 00 N..%.......r....
0020: F4 F3 DE 9A 00 00 00 00 16 EF 76 98 00 00 00 00 ..........v.....
0030: CD CB 2A 74 00 00 00 00 12 DE 03 91 00 00 00 00 ..*t............
0040: 78 6A C2 98 00 00 00 00 F4 4F A2 A9 00 00 00 00 xj.......O......
0050: FD D3 38 91 00 00 00 00 4E 18 99 AB 00 00 00 00 ..8.....N.......
0060: 02 00 00 00 00 00 00 00 4F D3 BE 2A 00 00 00 00 ........O..*....
0070: F6 57 21 A9 00 00 00 00 F3 93 21 F4 00 00 00 00 .W!.......!.....
^-----------------------------------------------------------------------------^
>-----------------------------------------------------------------------------<
[17:28:11 927]dest e4ffe1e0 src e4ffedd8 lr 120db238, md5=92206d6ef441d658814c83c1d4ff8379, hex=5e59831700000000786ac28d000000004e18992500000000d381977200000000f4f3de9a0000000016ef769800000000cdcb2a740000000012de039100000000786ac29800000000f44fa2a900000000fdd33891000000004e1899ab0000000003000000000000004fd3be2a00000000f65721a900000000f39321f400000000
size: 128
0000: 5E 59 83 17 00 00 00 00 78 6A C2 8D 00 00 00 00 ^Y......xj......
0010: 4E 18 99 25 00 00 00 00 D3 81 97 72 00 00 00 00 N..%.......r....
0020: F4 F3 DE 9A 00 00 00 00 16 EF 76 98 00 00 00 00 ..........v.....
0030: CD CB 2A 74 00 00 00 00 12 DE 03 91 00 00 00 00 ..*t............
0040: 78 6A C2 98 00 00 00 00 F4 4F A2 A9 00 00 00 00 xj.......O......
0050: FD D3 38 91 00 00 00 00 4E 18 99 AB 00 00 00 00 ..8.....N.......
0060: 03 00 00 00 00 00 00 00 4F D3 BE 2A 00 00 00 00 ........O..*....
0070: F6 57 21 A9 00 00 00 00 F3 93 21 F4 00 00 00 00 .W!.......!.....
^-----------------------------------------------------------------------------^
>-----------------------------------------------------------------------------<
[17:28:11 930]dest 1259a182 src 1259a000 lr 120d60f8, md5=7712df1581044110c3d0c350bb77ed3d, hex=77965d322e357c60eee28b2b6fbb54ef80564ffc4ccad67fb24c06e100764c96a01f3e6e00f151b03285f4ab91260dc1b35d17217251c2ccf46b88019738110062cfb47bb35f50f35f3d8124f51eed75371b05591d7c7cef2cf595018515a808d10af3c0e4cd4456b98182d55f6e6094f9527754e4d8760587d64ebd9f6e70c0eef53a444d0f4174faae2fa45d90545730ef2f01951fc628a51ebd059e49150583ac023e9ae784563d0226a6cfb7e2d8a429e123c597
size: 182
0000: 77 96 5D 32 2E 35 7C 60 EE E2 8B 2B 6F BB 54 EF w.]2.5|`...+o.T.
0010: 80 56 4F FC 4C CA D6 7F B2 4C 06 E1 00 76 4C 96 .VO.L....L...vL.
0020: A0 1F 3E 6E 00 F1 51 B0 32 85 F4 AB 91 26 0D C1 ..>n..Q.2....&..
0030: B3 5D 17 21 72 51 C2 CC F4 6B 88 01 97 38 11 00 .].!rQ...k...8..
0040: 62 CF B4 7B B3 5F 50 F3 5F 3D 81 24 F5 1E ED 75 b..{._P._=.$...u
0050: 37 1B 05 59 1D 7C 7C EF 2C F5 95 01 85 15 A8 08 7..Y.||.,.......
0060: D1 0A F3 C0 E4 CD 44 56 B9 81 82 D5 5F 6E 60 94 ......DV...._n`.
0070: F9 52 77 54 E4 D8 76 05 87 D6 4E BD 9F 6E 70 C0 .RwT..v...N..np.
0080: EE F5 3A 44 4D 0F 41 74 FA AE 2F A4 5D 90 54 57 ..:DM.At../.].TW
0090: 30 EF 2F 01 95 1F C6 28 A5 1E BD 05 9E 49 15 05 0./....(.....I..
00A0: 83 AC 02 3E 9A E7 84 56 3D 02 26 A6 CF B7 E2 D8 ...>...V=.&.....
00B0: A4 29 E1 23 C5 97 .).
^-----------------------------------------------------------------------------^
>-----------------------------------------------------------------------------<
[17:28:11 950]dest 125a3100 src 125a3000 lr 120d5e04, md5=035760cba12ccc95d7b6ad9ffd54e296, hex=4d444a336c6c30794c6a5638594f3769697974767531547667465a502f457a4b316e2b795441626841485a4d6c714166506d3441385647774d6f58307135456d4463477a58526368636c48437a505272694147584f42454159732b3065374e6655504e665059456b395237746454636242566b6466487a764c5057564159555671416a5243765041354d314556726d4267745666626d43552b564a33564f545964675748316b36396e323577774f37314f6b524e443046302b7134767046325156466377377938426c522f474b4b55657651576553525546673677435070726e684659394169616d7a376669324b5170345350466c77413d
size: 248
0000: 4D 44 4A 33 6C 6C 30 79 4C 6A 56 38 59 4F 37 69 MDJ3ll0yLjV8YO7i
0010: 69 79 74 76 75 31 54 76 67 46 5A 50 2F 45 7A 4B iytvu1TvgFZP/EzK
0020: 31 6E 2B 79 54 41 62 68 41 48 5A 4D 6C 71 41 66 1n+yTAbhAHZMlqAf
0030: 50 6D 34 41 38 56 47 77 4D 6F 58 30 71 35 45 6D Pm4A8VGwMoX0q5Em
0040: 44 63 47 7A 58 52 63 68 63 6C 48 43 7A 50 52 72 DcGzXRchclHCzPRr
0050: 69 41 47 58 4F 42 45 41 59 73 2B 30 65 37 4E 66 iAGXOBEAYs+0e7Nf
0060: 55 50 4E 66 50 59 45 6B 39 52 37 74 64 54 63 62 UPNfPYEk9R7tdTcb
0070: 42 56 6B 64 66 48 7A 76 4C 50 57 56 41 59 55 56 BVkdfHzvLPWVAYUV
0080: 71 41 6A 52 43 76 50 41 35 4D 31 45 56 72 6D 42 qAjRCvPA5M1EVrmB
0090: 67 74 56 66 62 6D 43 55 2B 56 4A 33 56 4F 54 59 gtVfbmCU+VJ3VOTY
00A0: 64 67 57 48 31 6B 36 39 6E 32 35 77 77 4F 37 31 dgWH1k69n25wwO71
00B0: 4F 6B 52 4E 44 30 46 30 2B 71 34 76 70 46 32 51 OkRND0F0+q4vpF2Q
00C0: 56 46 63 77 37 79 38 42 6C 52 2F 47 4B 4B 55 65 VFcw7y8BlR/GKKUe
00D0: 76 51 57 65 53 52 55 46 67 36 77 43 50 70 72 6E vQWeSRUFg6wCPprn
00E0: 68 46 59 39 41 69 61 6D 7A 37 66 69 32 4B 51 70 hFY9Aiamz7fi2KQp
00F0: 34 53 50 46 6C 77 41 3D 4SPFlwA=
^-----------------------------------------------------------------------------^
>-----------------------------------------------------------------------------<
[17:28:11 955]dest 125a3000 src 125a3100 lr 120d4fbc, md5=035760cba12ccc95d7b6ad9ffd54e296, hex=4d444a336c6c30794c6a5638594f3769697974767531547667465a502f457a4b316e2b795441626841485a4d6c714166506d3441385647774d6f58307135456d4463477a58526368636c48437a505272694147584f42454159732b3065374e6655504e665059456b395237746454636242566b6466487a764c5057564159555671416a5243765041354d314556726d4267745666626d43552b564a33564f545964675748316b36396e323577774f37314f6b524e443046302b7134767046325156466377377938426c522f474b4b55657651576553525546673677435070726e684659394169616d7a376669324b5170345350466c77413d
size: 248
0000: 4D 44 4A 33 6C 6C 30 79 4C 6A 56 38 59 4F 37 69 MDJ3ll0yLjV8YO7i
0010: 69 79 74 76 75 31 54 76 67 46 5A 50 2F 45 7A 4B iytvu1TvgFZP/EzK
0020: 31 6E 2B 79 54 41 62 68 41 48 5A 4D 6C 71 41 66 1n+yTAbhAHZMlqAf
0030: 50 6D 34 41 38 56 47 77 4D 6F 58 30 71 35 45 6D Pm4A8VGwMoX0q5Em
0040: 44 63 47 7A 58 52 63 68 63 6C 48 43 7A 50 52 72 DcGzXRchclHCzPRr
0050: 69 41 47 58 4F 42 45 41 59 73 2B 30 65 37 4E 66 iAGXOBEAYs+0e7Nf
0060: 55 50 4E 66 50 59 45 6B 39 52 37 74 64 54 63 62 UPNfPYEk9R7tdTcb
0070: 42 56 6B 64 66 48 7A 76 4C 50 57 56 41 59 55 56 BVkdfHzvLPWVAYUV
0080: 71 41 6A 52 43 76 50 41 35 4D 31 45 56 72 6D 42 qAjRCvPA5M1EVrmB
0090: 67 74 56 66 62 6D 43 55 2B 56 4A 33 56 4F 54 59 gtVfbmCU+VJ3VOTY
00A0: 64 67 57 48 31 6B 36 39 6E 32 35 77 77 4F 37 31 dgWH1k69n25wwO71
00B0: 4F 6B 52 4E 44 30 46 30 2B 71 34 76 70 46 32 51 OkRND0F0+q4vpF2Q
00C0: 56 46 63 77 37 79 38 42 6C 52 2F 47 4B 4B 55 65 VFcw7y8BlR/GKKUe
00D0: 76 51 57 65 53 52 55 46 67 36 77 43 50 70 72 6E vQWeSRUFg6wCPprn
00E0: 68 46 59 39 41 69 61 6D 7A 37 66 69 32 4B 51 70 hFY9Aiamz7fi2KQp
00F0: 34 53 50 46 6C 77 41 3D 4SPFlwA=
^-----------------------------------------------------------------------------^
>-----------------------------------------------------------------------------<
[17:28:11 869]dest 1259a0c0 src 1259a180 lr 12406ecc, md5=05d2981ffb38a02ec96e41fad770b371, hex=327c313737303238333636327c4d492038204c6974657c313937302d30342d30337c3133362e31327c3130347c397c317c307c31317c317c313736343734303933397c317c30303030307c30303030307c303030317c307c303030303030307c30307c307c317c3336257c317c7c307c392e362e397c363564323638353264356330333330337c3023317c3030307c615f383037336162303634343632323835347c31323239393639313632323400
size: 175
0000: 32 7C 31 37 37 30 32 38 33 36 36 32 7C 4D 49 20 2|1770283662|MI
0010: 38 20 4C 69 74 65 7C 31 39 37 30 2D 30 34 2D 30 8 Lite|1970-04-0
0020: 33 7C 31 33 36 2E 31 32 7C 31 30 34 7C 39 7C 31 3|136.12|104|9|1
0030: 7C 30 7C 31 31 7C 31 7C 31 37 36 34 37 34 30 39 |0|11|1|17647409
0040: 33 39 7C 31 7C 30 30 30 30 30 7C 30 30 30 30 30 39|1|00000|00000
0050: 7C 30 30 30 31 7C 30 7C 30 30 30 30 30 30 30 7C |0001|0|0000000|
0060: 30 30 7C 30 7C 31 7C 33 36 25 7C 31 7C 7C 30 7C 00|0|1|36%|1||0|
0070: 39 2E 36 2E 39 7C 36 35 64 32 36 38 35 32 64 35 9.6.9|65d26852d5
0080: 63 30 33 33 30 33 7C 30 23 31 7C 30 30 30 7C 61 c03303|0
0090: 5F 38 30 37 33 61 62 30 36 34 34 36 32 32 38 35 _8073ab064462285
00A0: 34 7C 31 32 32 39 39 36 39 31 36 32 32 34 00 4|122996916224.
^-----------------------------------------------------------------------------^
>-----------------------------------------------------------------------------<
[17:28:11 881]dest 125a0008 src 1259a0c0 lr 120d63b8, md5=9ee8bcef6f27a097ce229c098d2c65ad, hex=327c313737303238333636327c4d492038204c6974657c313937302d30342d30337c3133362e31327c3130347c397c317c307c31317c317c313736343734303933397c317c30303030307c30303030307c303030317c307c303030303030307c30307c307c317c3336257c317c7c307c392e362e397c363564323638353264356330333330337c3023317c3030307c615f383037336162303634343632323835347c313232393936393136323234
size: 174
0000: 32 7C 31 37 37 30 32 38 33 36 36 32 7C 4D 49 20 2|1770283662|MI
0010: 38 20 4C 69 74 65 7C 31 39 37 30 2D 30 34 2D 30 8 Lite|1970-04-0
0020: 33 7C 31 33 36 2E 31 32 7C 31 30 34 7C 39 7C 31 3|136.12|104|9|1
0030: 7C 30 7C 31 31 7C 31 7C 31 37 36 34 37 34 30 39 |0|11|1|17647409
0040: 33 39 7C 31 7C 30 30 30 30 30 7C 30 30 30 30 30 39|1|00000|00000
0050: 7C 30 30 30 31 7C 30 7C 30 30 30 30 30 30 30 7C |0001|0|0000000|
0060: 30 30 7C 30 7C 31 7C 33 36 25 7C 31 7C 7C 30 7C 00|0|1|36%|1||0|
0070: 39 2E 36 2E 39 7C 36 35 64 32 36 38 35 32 64 35 9.6.9|65d26852d5
0080: 63 30 33 33 30 33 7C 30 23 31 7C 30 30 30 7C 61 c03303|0
0090: 5F 38 30 37 33 61 62 30 36 34 34 36 32 32 38 35 _8073ab064462285
00A0: 34 7C 31 32 32 39 39 36 39 31 36 32 32 34 4|122996916224
^-----------------------------------------------------------------------------^
>-----------------------------------------------------------------------------<
[17:28:11 888]dest 1259a000 src 125a0000 lr 120d62b0, md5=0f30f3e532f27bc77bad081cde4ccb0a, hex=786855552854fb55672964626265676d6663636729181c756d75193c213029646c6265786561786566296466637b646729646561296c29642965296464296429646263616261656c666c296429656565656529656565656529656565642965296565656565656529656529652964296663702964292965296c7b637b6c2963603167636d60673160366566666566296576642965656529340a6d6562663437656361616367676d6061296467676c6c636c6463676761
size: 182
0000: 78 68 55 55 28 54 FB 55 67 29 64 62 62 65 67 6D xhUU(T.Ug)dbbegm
0010: 66 63 63 67 29 18 1C 75 6D 75 19 3C 21 30 29 64 fccg)..umu.<!0)d
0020: 6C 62 65 78 65 61 78 65 66 29 64 66 63 7B 64 67 lbexeaxef)dfc{dg
0030: 29 64 65 61 29 6C 29 64 29 65 29 64 64 29 64 29 )dea)l)d)e)dd)d)
0040: 64 62 63 61 62 61 65 6C 66 6C 29 64 29 65 65 65 dbcabaelfl)d)eee
0050: 65 65 29 65 65 65 65 65 29 65 65 65 64 29 65 29 ee)eeeee)eeed)e)
0060: 65 65 65 65 65 65 65 29 65 65 29 65 29 64 29 66 eeeeeee)ee)e)d)f
0070: 63 70 29 64 29 29 65 29 6C 7B 63 7B 6C 29 63 60 cp)d))e)l{c{l)c`
0080: 31 67 63 6D 60 67 31 60 36 65 66 66 65 66 29 65 1gcm`g1`6effef)e
0090: 76 64 29 65 65 65 29 34 0A 6D 65 62 66 34 37 65 vd)eee)4.mebf47e
00A0: 63 61 61 63 67 67 6D 60 61 29 64 67 67 6C 6C 63 caacggm`a)dggllc
00B0: 6C 64 63 67 67 61 ldcgga
^-----------------------------------------------------------------------------^
>-----------------------------------------------------------------------------<
[17:28:11 900]dest e4ffe280 src e4ffedd8 lr 120db238, md5=0a1cd535cc56952ffe44358d5554ecf2, hex=5e59831700000000786ac28d000000004e18992500000000d381977200000000f4f3de9a0000000016ef769800000000cdcb2a740000000012de039100000000786ac29800000000f44fa2a900000000fdd33891000000004e1899ab0000000001000000000000004fd3be2a00000000f65721a900000000f39321f400000000
size: 128
0000: 5E 59 83 17 00 00 00 00 78 6A C2 8D 00 00 00 00 ^Y......xj......
0010: 4E 18 99 25 00 00 00 00 D3 81 97 72 00 00 00 00 N..%.......r....
0020: F4 F3 DE 9A 00 00 00 00 16 EF 76 98 00 00 00 00 ..........v.....
0030: CD CB 2A 74 00 00 00 00 12 DE 03 91 00 00 00 00 ..*t............
0040: 78 6A C2 98 00 00 00 00 F4 4F A2 A9 00 00 00 00 xj.......O......
0050: FD D3 38 91 00 00 00 00 4E 18 99 AB 00 00 00 00 ..8.....N.......
0060: 01 00 00 00 00 00 00 00 4F D3 BE 2A 00 00 00 00 ........O..*....
0070: F6 57 21 A9 00 00 00 00 F3 93 21 F4 00 00 00 00 .W!.......!.....
^-----------------------------------------------------------------------------^
>-----------------------------------------------------------------------------<
[17:28:11 924]dest e4ffe1e0 src e4ffedd8 lr 120db238, md5=c99335f5f1706fa64cbff772608ee64e, hex=5e59831700000000786ac28d000000004e18992500000000d381977200000000f4f3de9a0000000016ef769800000000cdcb2a740000000012de039100000000786ac29800000000f44fa2a900000000fdd33891000000004e1899ab0000000002000000000000004fd3be2a00000000f65721a900000000f39321f400000000
size: 128
0000: 5E 59 83 17 00 00 00 00 78 6A C2 8D 00 00 00 00 ^Y......xj......
0010: 4E 18 99 25 00 00 00 00 D3 81 97 72 00 00 00 00 N..%.......r....
[培训]Windows内核深度攻防:从Hook技术到Rootkit实战!
最后于 20小时前
被KanXue_NG编辑
,原因: 上传附加