-
-
[求助]ASProtect2.4文件脱壳失败,求教大神,感激不尽!
-
发表于: 2026-1-14 15:50 1216
-
求大神指教一下,脱壳原文件链接
通过网盘分享的文件:ForexTester5.exe
链接: c62K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6H3j5h3&6Q4x3X3g2T1j5h3W2V1N6g2)9J5k6h3y4G2L8g2)9J5c8Y4y4Q4x3V1j5I4j5g2)9J5k6o6g2x3d9V1&6E0z5g2u0u0e0i4c8C8j5U0N6G2e0%4W2d9N6W2m8%4i4K6y4r3M7s2N6V1i4K6y4p5z5o6y4^5K9R3`.`. 提取码: 83xj
脱壳后文件
通过网盘分享的文件:de_ForexTester5_.exe
链接: c0cK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6H3j5h3&6Q4x3X3g2T1j5h3W2V1N6g2)9J5k6h3y4G2L8g2)9J5c8Y4y4Q4x3V1j5I4e0o6c8Q4y4h3k6t1g2V1q4F1h3f1c8*7x3V1I4U0i4K6g2X3h3h3k6n7L8U0W2I4K9p5q4Q4x3@1k6H3N6$3c8Q4x3@1b7K6L8h3j5J5 提取码: 3mf2
脚本脱壳提示有偷窃代码,文件脱壳后查壳显示yoda壳,原文件应该是ASPr+VMP双重壳,脱壳后用importREC 修复,运行修复文件报错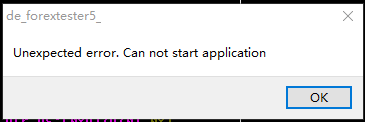
脚本脱壳日志如下:
Script Log Window
Address Message
2469008 dllimgbase: 02469000
2469008 freeloc: 02600000
4302777 freeloc: 04240000
433579E AsprAPIloc: 0434269C
433579E Aspr1stthunk: 00D19D20
432600C SDK 偷代码区段 = 00000013
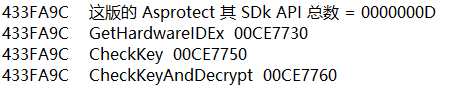
433FA9C EmuAddr: 00CE7730
433FA9C 这版的 Asprotect 其 SDk API 总数 = 0000000D
433FA9C GetHardwareIDEx 00CE7730
433FA9C CheckKey 00CE7750
433FA9C CheckKeyAndDecrypt 00CE7760
CEEB1C SDK 偷窃代码区段地址 = 05350000
CEEB1C SDK 偷窃代码区段地址 = 05360000
CEEB1C SDK 偷窃代码区段地址 = 05370000
CEEB1C SDK 偷窃代码区段地址 = 05380000
CEEB1C SDK 偷窃代码区段地址 = 05390000
CEEB1C SDK 偷窃代码区段地址 = 053A0000
CEEB1C SDK 偷窃代码区段地址 = 053B0000
CEEB1C SDK 偷窃代码区段地址 = 053C0000
CEEB1C SDK 偷窃代码区段地址 = 053D0000
CEEB1C SDK 偷窃代码区段地址 = 053E0000
CEEB1C SDK 偷窃代码区段地址 = 053F0000
CEEB1C SDK 偷窃代码区段地址 = 05400000
CEEB1C SDK 偷窃代码区段地址 = 05410000
CEEB1C SDK 偷窃代码区段地址 = 05420000
CEEB1C SDK 偷窃代码区段地址 = 05430000
CEEB1C SDK 偷窃代码区段地址 = 05440000
CEEB1C SDK 偷窃代码区段地址 = 05450000
CEEB1C SDK 偷窃代码区段地址 = 05460000
CEEB1C SDK 偷窃代码区段地址 = 05470000
CEEB1C IAT 的地址 = 00D18FD8
CEEB1C IAT 的相对地址 = 00918FD8
CEEB1C IAT 的大小 = 00000D58
CEEB1C OEP 的地址 = 00CEEB1C
CEEB1C OEP 的相对地址 = 008EEB1C
请教一下大神,是什么原因导致修复失败?是下面这三个函数的原因吗?得怎么修复呢?
[培训]Windows内核深度攻防:从Hook技术到Rootkit实战!




