-
-
[原创]内核中获取DNS解析的源头发起方进程方案
-
发表于:
2025-12-17 15:20
5879
-
论坛里好多朋友一直在询问如何在内核中比较准确的获取DNS实际发起方的进程,这里给大家抛砖引玉介绍一下我自己的方案,这个方案也有失败几率但是与成功率相比那就忽略了。整个方案的核心思路是在WFP层获取发送的DNS包(目标端口是53,且是UDP协议,基本认为是DNS请求包,然后在做自己的包解析确认是不是),明确了是发送的DNS包之后,接下来就是重点了:借助ALPC线程枚举,找到在等待ALPC应答的线程,通过线程反推PID,获取目标进程。在这个WFP层获取的发包PID不是我们想要的进程pid,这个PID一般都是svchost的进程,就是下面这个:
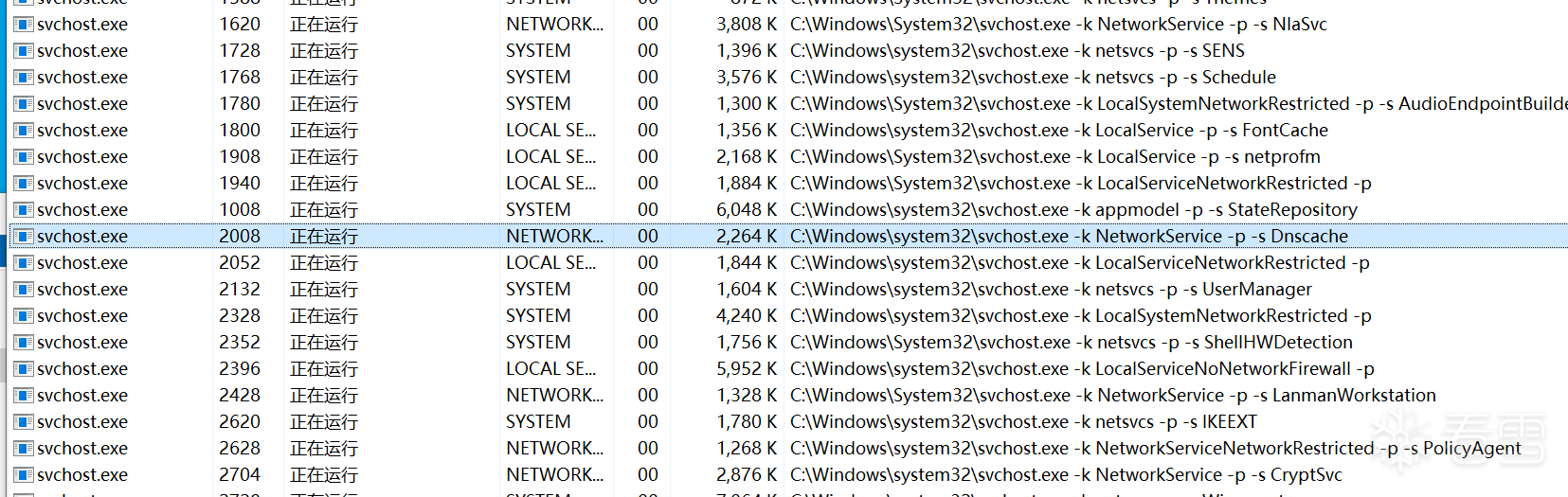
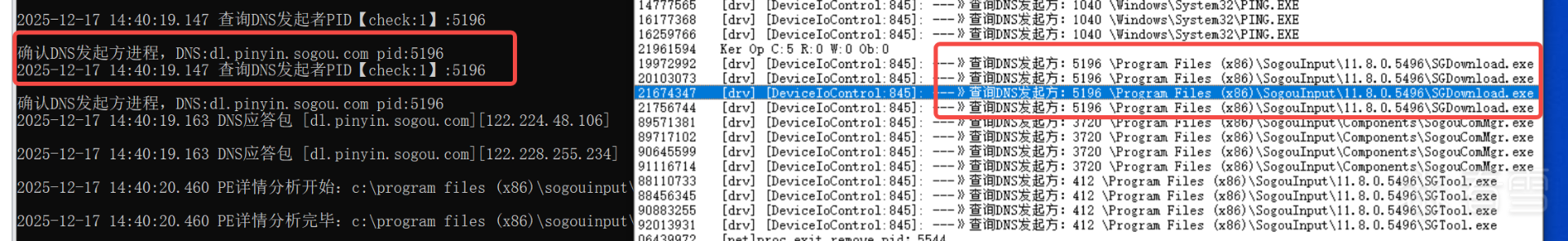
实际上应用程序在发起DNS解析时,是通过本地ALPC将相关信息发送给了这个DNS解析与缓存服务,随后统一由这个进程进行解析,如果缓存里有了,就发送新的请求了,如果缓存里没有就执行一下UDP请求。在我们的实际业务场景中(网络检测与拦截)我们需要获得的是真正发起这个DNS请求的进程,而不是这个svchost的代理进程。先看下效果,再贴代码:
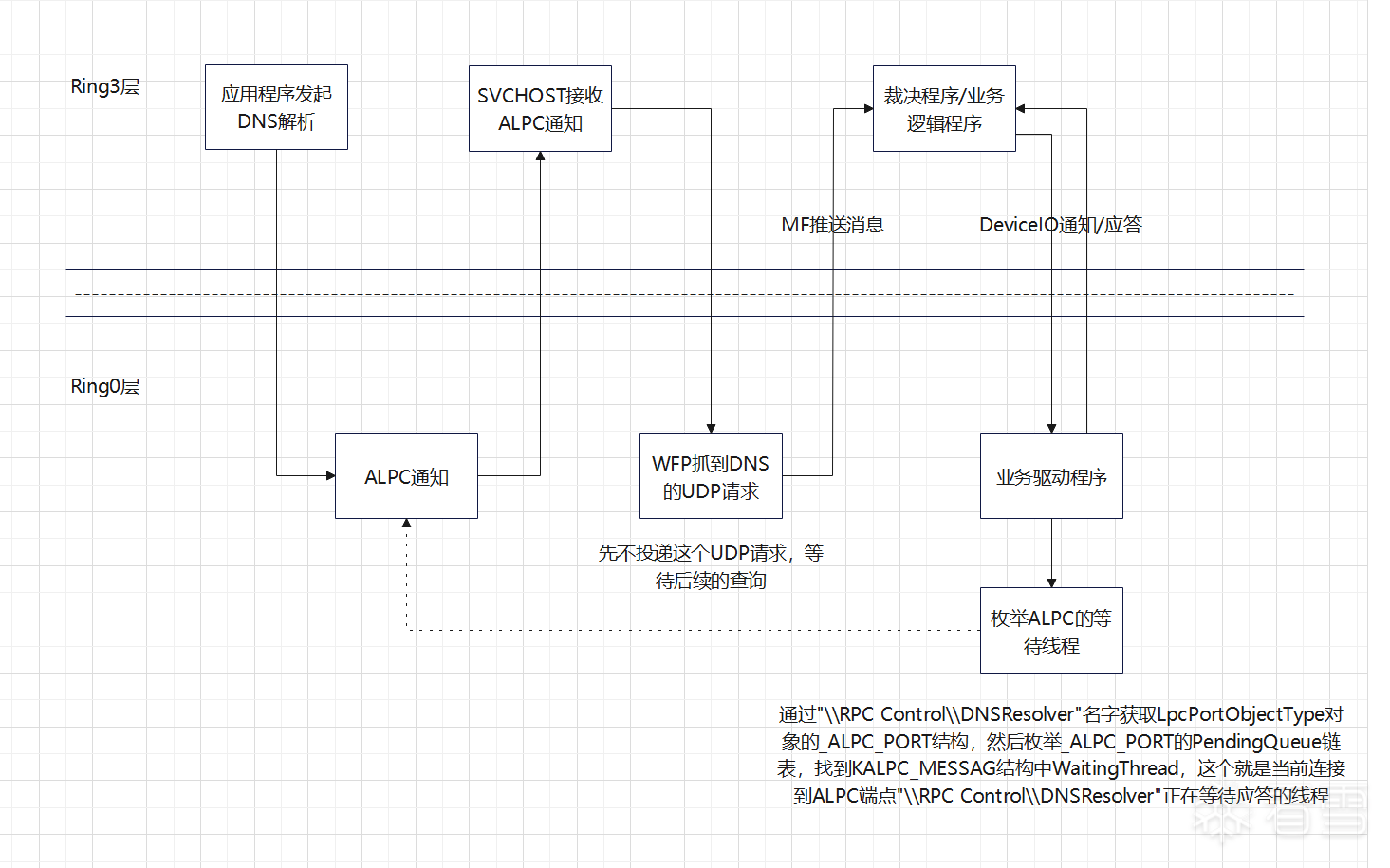
逻辑图如下所示(逻辑图描述了整个方案的实现思路):
传播安全知识、拓宽行业人脉——看雪讲师团队等你加入!
最后于 2025-12-17 15:36
被沧海浮萍_编辑
,原因: