-
-
[原创]amateursCTF[pwn/Injection]
-
发表于: 2025-11-22 00:46 6504
-
someone would say why? its the shellcode again. because I am beginnerrr for pwn just for a month and a half. And in fact, It should also be the weekend of the same week, I played RCTF, Then I got stuck by the SIGIN shellcode. Of course, the knowledge I learned was not solid enough. Dramatic events is that in my interview, I can make two heaps, but I can't get a flag from the stack, i mean that time shellcode came too.
so, let u and m begin!
the Injection is belong to HARD at that CTF with only 3 men sols it. I will do a check. Gooddd luckkk to m.
Its very typical in foreign CTF competitions because they provide the source code.
accepts an uploaded ELF binary from the player, saves it to /tmp/solve, and runs it inside a strict seccomp sandbox that only allows a few system calls.
to rum this binary i should first to run the command to "elfpatch"
and we will use this command gcc -static -nostdlib -fno-builtin -o solve 1.c
as we can see
The error occurs because you used -nostdlib; the linker does not automatically link libc, so the syscall() function is not provided, resulting in an undefined reference.
and then we have to think about how to escape it what can i sayyyy. yup
Make system calls directly with inline assembly without calling syscall()
we can see it and
then we will get it
and we use remote!!!
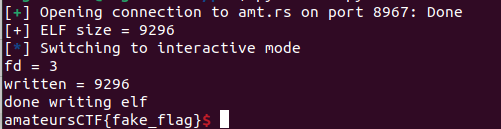
however it can find the true flag, i used to think there's a fake flag in the remote environment, it is a joke arl?
let us think it moreeeeeeeeee :(((
yuppp it was me who didnt read the code...
wowww why he let you to have execute it is because it needdddd
before that we should think something why he give us so many files
nsjail.cfg and hook.sh
and
and
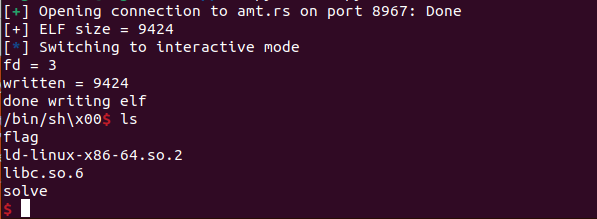
we know that here has the libc and in our program we can see the sleep, so we maybe need to hook it
opens /tmp/libc.so.6 in read–write mode and overwrites the bytes at the fixed offset SLEEP_OFFSET with custom shellcode.the code advances the file offset by repeatedly calling read(). Each read() call automatically moves the file pointer forward. It keeps reading in chunks (1024 bytes each time) until the current offset reaches SLEEP_OFFSET.Once the offset equals SLEEP_OFFSET, the code performs a write() to overwrite the data at that position with the shellcode buffer. Finally, it exits. And we also need ''volatile'' to write in the inline.
赞赏
- [原创]安卓FRIDA2 1665
- [原创]安卓FRIDA 4815
- [原创]amateursCTF[pwn/Injection] 6505
- [原创]amateursCTF[pwn/Easy Shellcoding] 5981




