样本libbaiduprotect.so
解密操作在initarray的前2个函数,第二个函数存在一些反调试且被混淆了,但是简单动调就能明白只是做了一些解密操作
选择合适时机 直接内存dump出data段和text段的解密数据然后写入原来的so即可简单脱壳
存在很多不同的字符串解密函数,hook几个看了看,要写一个IDA脚本批量解密方便静态分析
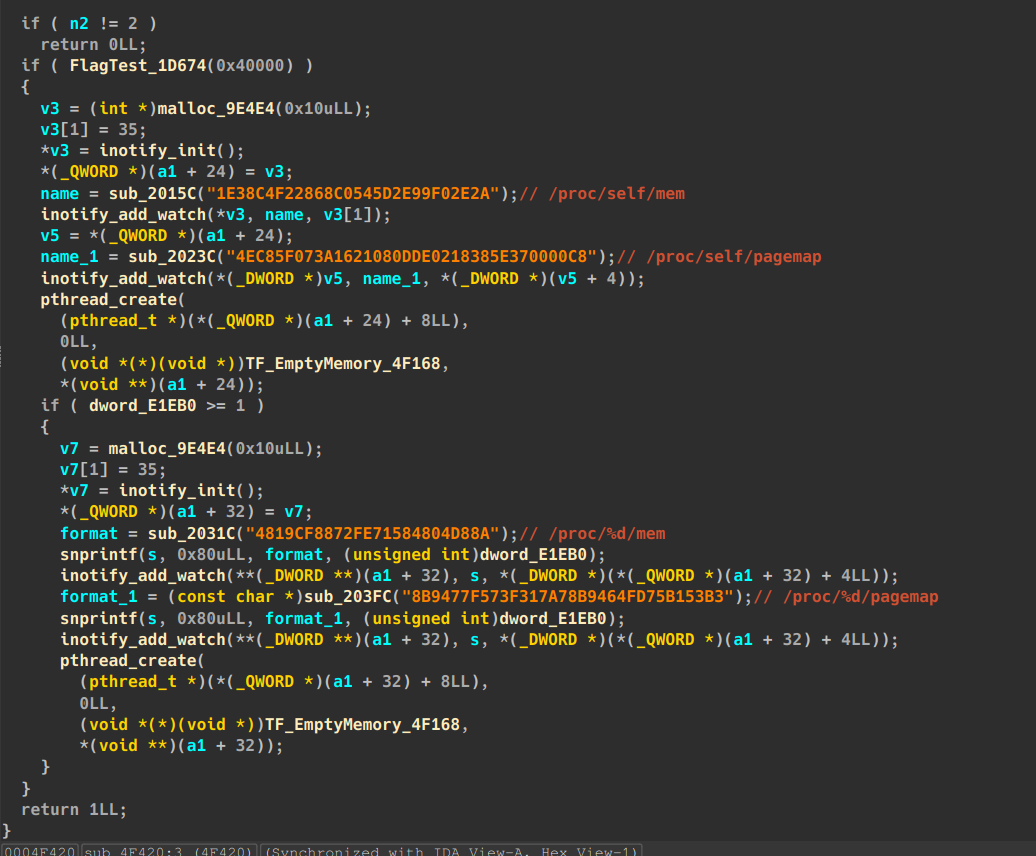
初始化 inotify 监控(自身进程) :
inotify 事件的处理逻辑( TF_EmptyMemory_4F168 线程的核心处理函数),主要逻辑如下:
循环读取事件:通过 read(*a1, s, 0xAA0uLL) 从 inotify 文件描述符(*a1)循环读取事件(a1 为监控相关数据,包含 inotify 实例的文件描述符)。
事件解析与处理:
对读取到的事件数据(存储在 s 中)进行循环解析,每次处理一个事件结构。
检查事件类型(v4 = *((_DWORD *)s_1 + 1)),若为 32、2、1 中的任意一种(对应 inotify 特定事件,如访问、修改、删除等),则:
但似乎我进行内存dump的时候并没有闪退?
核心功能: 监控进程内存相关文件的访问 / 修改行为(可能是调试器或恶意程序的操作),一旦检测到则主动退出以防止被分析或篡改
DoLibcProtection_166D8
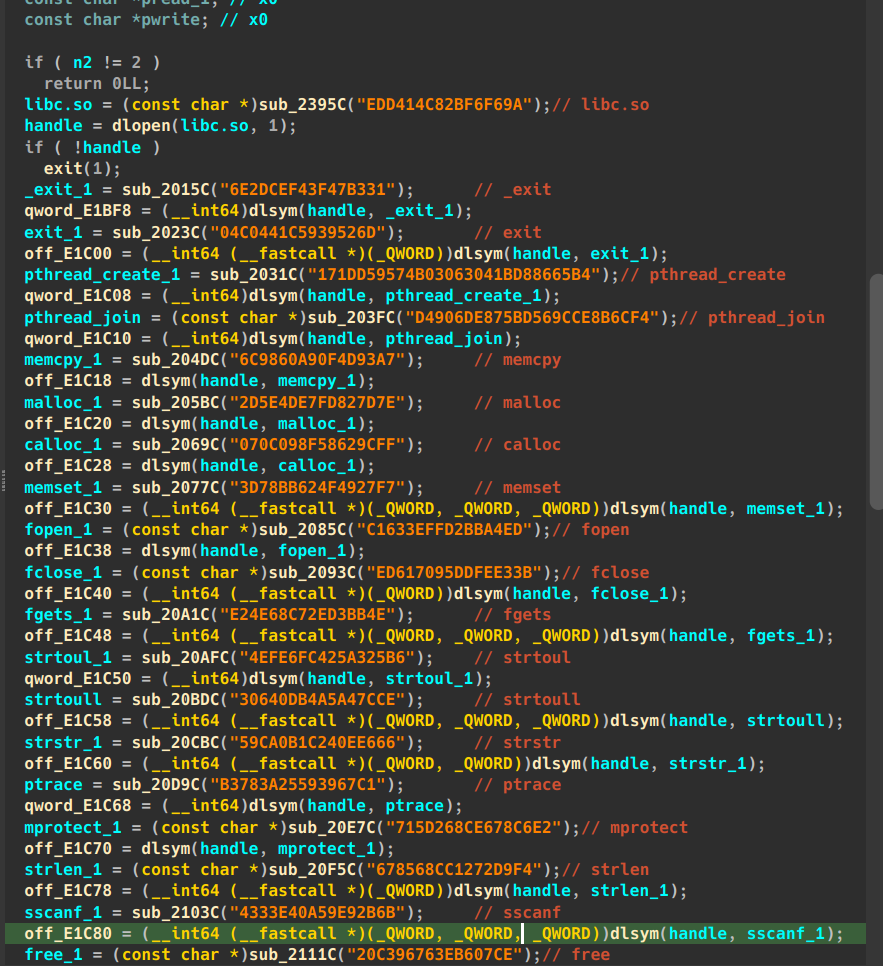
调用dlsym拿libc常用函数的地址 存到全局变量中进行调用
sub_350EC
检测脱壳工具核心类
检测脱壳工具相关文件
检测风险方法注册
二、当 n2 == 2 时:注册原生方法并校验环境
sub_2E2E0
检测 Frida 相关线程与内存特征
检测 linjector 注入工具遍历/proc/self/fd目录,分析文件描述符的链接信息,检查是否包含linjector(动态注入工具的特征)。
结果处理
sub_2E8DC
初始化与前置检查
定位关键方法与内存保护调整
关键方法完整性校验
再次获取_ZN3art9ArtMethod12PrettyMethodEb方法的内存地址,记录其原始内存数据(qword_E23B8)和方法地址(qword_E23C8),并标记初始化完成(byte_E23C0[0] = 1)。
后续调用时,校验当前_ZN3art9ArtMethod12PrettyMethodEb方法的内存数据与原始记录是否一致:
sub_34F88
执行 Hook 操作
结果返回
核心函数 sub_4D3D0 的作用:
准备模拟器特征字符串列表:通过一系列解密函数(sub_20BDC 等)生成一组字符串,这些字符串是常见的模拟器标识,包括:sdk、google_sdk、Andy、ttVM_Hdragon(天天龙模拟器)、Droid4X(海马玩模拟器)、nox(夜神模拟器)、sdk_x86、sdk_google、vbox86p(VirtualBox 模拟器)、emu64x(64 位模拟器)。
获取系统 PRODUCT 属性值:调用 sub_1F1D0 函数,获取 Android 系统中 android.os.Build.PRODUCT 属性的字符串值(该属性通常标识设备的产品名称,模拟器会有特定值)。
匹配模拟器特征:检查获取到的 PRODUCT 属性值中是否包含上述列表中的任何一个模拟器标识。
sub_4D550
准备模拟器制造商特征列表通过一系列解密函数(sub_2165C等)生成一组字符串,这些字符串是常见模拟器的制造商标识,包括:unknown、Genymotion(知名模拟器)、Andy(安迪模拟器)、MIT(可能关联特定模拟器)、nox(夜神模拟器)、TiantianVM(天天模拟器)、iToolsAVM(iTools 模拟器)、Netease(网易模拟器)。
获取系统MANUFACTURER属性值调用辅助函数sub_1F1D0(之前分析过的 JNI 工具函数),获取 Android 系统中android.os.Build.MANUFACTURER属性的字符串值(该属性通常标识设备的制造商名称,模拟器会有特定的制造商标识)。
匹配模拟器特征检查获取到的MANUFACTURER属性值中是否包含上述列表中的任何一个模拟器制造商标识:
sub_4D6B0
准备模拟器特征标识列表通过解密函数(sub_21F1C等)生成一组模拟器相关特征字符串,包括:generic、generic_x86(通用 x86 架构标识,常见于模拟器)、Andy(安迪模拟器)、TTVM(天天模拟器相关)。
获取系统BRAND属性值调用辅助函数sub_1F1D0(JNI 工具函数),获取 Android 系统android.os.Build.BRAND属性的字符串值。该属性标识设备品牌,模拟器通常会使用通用品牌名或专属品牌标识。
特征匹配判断检查获取到的BRAND属性值是否包含上述特征列表中的任意一个标识:
sub_4D7D0
生成模拟器特征标识列表通过一系列解密函数(sub_2245C等)生成 11 个模拟器相关特征字符串,包括:generic、generic_x86、generic_x86_64(通用架构标识,模拟器常用)、Andy(安迪模拟器)、ttVM_Hdragon(天天模拟器)、Droid4X(海马玩模拟器)、nox(夜神模拟器)、vbox86p(VirtualBox 模拟器)、iToolsAVM(iTools 模拟器)、emu64x(64 位模拟器)、emulator(直接模拟器标识)。
获取系统DEVICE属性值调用辅助函数sub_1F1D0(JNI 工具函数),获取 Android 系统android.os.Build.DEVICE属性的字符串值。该属性标识设备的具体型号或设备代号,模拟器会带有专属标识。
特征匹配与结果返回检查获取到的DEVICE属性值是否包含上述特征列表中的任意一个标识:
sub_4D960
生成模拟器特征标识列表通过解密函数(sub_22FBC等)生成 10 个模拟器相关特征字符串,覆盖主流模拟器及 SDK 测试设备标识:sdk、google_sdk、Droid4X(海马玩模拟器)、TiantianVM(天天模拟器)、Andy(安迪模拟器)、Android SDK built for x86_64(x86_64 架构 SDK 模拟器)、Android SDK built for x86(x86 架构 SDK 模拟器)、iToolsAVM(iTools 模拟器)、MuMu(沐沐模拟器)、sdk_gphone64(64 位 SDK 测试设备,常见于模拟器)。
获取系统MODEL属性值调用辅助函数sub_1F1D0(JNI 工具函数),获取 Android 系统android.os.Build.MODEL属性的字符串值。该属性标识设备的型号名称,模拟器通常会显示 SDK 相关名称或专属型号标识。
特征匹配与结果返回检查获取到的MODEL属性值是否包含上述特征列表中的任意一个标识:
sub_4DAE0
生成模拟器硬件特征列表通过解密函数(sub_23A3C等)生成 4 个模拟器专属的硬件特征字符串:goldfish(Android 官方模拟器的硬件标识)、vbox86(VirtualBox 模拟器相关硬件标识)、nox(夜神模拟器)、ttVM_x86(天天模拟器 x86 架构版本)。
获取系统HARDWARE属性值调用辅助函数sub_1F1D0(JNI 工具函数),获取 Android 系统android.os.Build.HARDWARE属性的字符串值。该属性标识设备的硬件型号,模拟器的硬件标识通常是固定的专属名称,与真实设备差异明显。
特征匹配与结果返回检查获取到的HARDWARE属性值是否包含上述特征列表中的任意一个标识:
sub_4DC00
生成模拟器指纹特征列表通过解密函数(sub_23F7C等)生成 10 个模拟器相关的FINGERPRINT特征字符串,涵盖通用模拟器、架构专属模拟器及知名第三方模拟器标识:
获取系统FINGERPRINT属性值调用辅助函数sub_1F1D0(JNI 工具函数),获取 Android 系统android.os.Build.FINGERPRINT属性的字符串值。该属性是设备的唯一指纹标识,由厂商、设备型号、系统版本等信息组合而成,模拟器的指纹标识具有明显的专属特征,且不易篡改。
特征匹配与结果返回检查获取到的FINGERPRINT属性值是否包含上述特征列表中的任意一个标识:
sub_4DD80
准备 MuMu 模拟器专属文件列表函数中涉及的文件包括:
文件存在性检查函数首先尝试访问 /etc/mumu-configs/device-prop-configs/mumu.config 文件,若该文件存在,则直接返回 1(判定为 MuMu 模拟器)。若该文件不存在,会依次检查上述 /data/local/cfg-* 系列文件和共享文件夹路径,只要其中任意一个文件 / 路径存在,就返回 1;若所有文件 / 路径都不存在,则返回 0。
sub_4DE00
准备模拟器专属系统属性列表函数中涉及的系统属性包括:
系统属性存在性检查函数通过_system_property_get_E1DC0函数依次检查上述系统属性是否存在。只要其中任意一个系统属性能被成功获取(返回值大于等于 1),则返回1(判定为目标模拟器);若所有属性都不存在,则返回0。
一、Magisk 相关核心文件
二、通用 Root 工具文件
三、挂载与系统配置文件
sub_487F4
其核心目的是通过检查进程属性历史,判断当前进程是否与 zygote 进程存在关联。
sub_48674
第一步:检查进程与 zygote 的关联调用chckRoot1_487F4()函数,若返回 1(即进程属性历史中存在:zygote:),则直接返回 1(判定为 Root 相关状态)。
第二步:检查 Magisk 工具文件是否存在
第三步:检查挂载信息中的 Magisk 痕迹若前两步未检测到痕迹,则读取/proc/self/mounts(进程挂载信息文件),并在内容中搜索一组与 Magisk 相关的路径字符串(如/sbin/.magisk/、/sbin/.core/mirror等,由初始化函数定义)。
sub_48908
JNI检测是否存在特定类 android/bde/BdeEngineManager
sub_48230
popen(which,su) 检测返回结果
sub_483DC
检测su 文件
access遍历 可能的su文件
sub_47AC4
一、核心检测的系统属性与目标值
二、分版本检测逻辑(以 Android SDK 34 为分界)
SDK 版本 < 34(低版本 Android 系统)
按优先级依次检测,满足任一条件即返回1(风险状态):
SDK 版本 ≥ 34(高版本 Android 系统)
检测逻辑与低版本一致,但去掉了优先级顺序,直接并列检测 4 个条件,满足任一即返回1(风险状态):
三、关键补充说明
sub_47DF0
popen(getprop) 检测返回结果
执行系统命令获取属性信息
检测关键不安全特征逐行匹配缓冲区内容,若包含以下任一特征字符串,立即记录状态码、打印日志并终止进程:
sub_4837C
access检测/system/app/Superuser.apk
sub_47714
读取挂载信息文件打开 /proc/mounts 文件(系统挂载信息的核心文件,记录所有分区的挂载路径、类型、权限等),以只读模式逐行读取内容。
解析挂载项并检测可写权限对每一行挂载信息,通过 sscanf 解析出挂载路径、挂载点、文件系统类型和挂载权限等字段,重点检查挂载权限中是否包含 rw(可写标识):
结果返回函数最终返回 v6 & 1,即 1 表示存在系统分区可写挂载(风险状态),0 表示所有检测的系统分区均为只读挂载(正常状态)。
sub_4E3A4
一、Xposed 框架检测
二、虚拟环境检测
VirtualApp 标识检测分析栈信息中是否包含com.lody.virtual(VirtualApp 的包名特征),若存在则判定为运行在 VirtualApp 虚拟环境中。
XposedHelpers 类补充验证尝试查找de.robv.android.xposed.XposedHelpers类,进一步确认 Xposed 框架的存在。
进程与路径特征检测
三、结果返回
若上述任一检测条件满足(存在 Xposed 框架、VirtualApp 或 Exposed 环境),函数返回true;否则返回false。
sub_48458
assess检测以下文件
sub_484D4
读取进程内存映射文件
检测 Xposed/EdXposed 特征检查内存映射内容中是否包含以下任一特征:
结果返回若检测到上述任一特征,返回1(判定存在 Xposed/EdXposed 框架);若读取完毕未检测到特征,返回0(判定无风险)。
sub_4ED18
定位关键类与字段
检测动态代理特征
查找java.lang.reflect.Proxy类(Java 动态代理的核心类)。
检查ActivityThread.sPackageManager是否是Proxy的实例:
该函数通过检测IPackageManager是否被动态代理,判断应用的包管理功能是否被恶意篡改(常见于 Hook 工具对应用安装、卸载等行为的拦截场景)。一旦检测到风险,立即终止应用,防止恶意操作(如静默安装恶意应用、篡改包信息等),保障应用的包管理安全性。
检测MT管理器
sub_50DAC
sub_50E7C
遍历所有 FD,用 open 打开并读取 FD 对应的目标路径(或通过 readlink 获取链接指向)。检测是否打开了指定前缀路径的文件
509C8
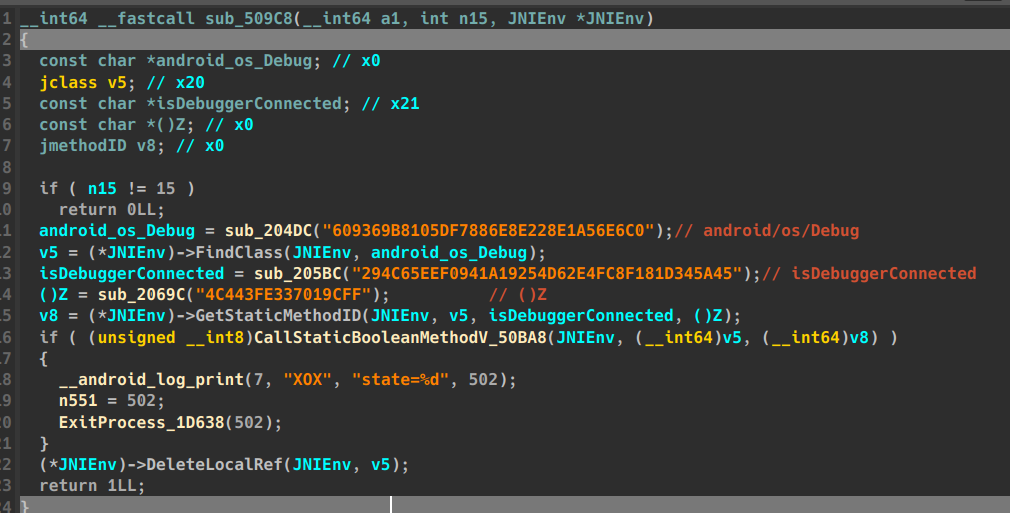
JNI调用
android.os.Debug.isDebuggerConnected() 静态方法,该方法返回 boolean 类型,true 表示进程已被调试器连接,false 表示未被调试。
4F8A0
遍历进程的所有线程目录代码首先通过 snprintf 生成路径 /proc/%d/task(%d 为目标进程 PID),然后用 opendir 打开该目录。/proc/[pid]/task 目录包含进程所有线程(TID)的子目录,代码通过 readdir 遍历这些线程目录。
筛选有效的线程 ID(TID) 对每个目录项(线程名)进行检查,确保其为纯数字(线程 ID 是数字),过滤掉非数字命名的目录(如 . 和 ..)。
读取线程的 status 文件对每个有效的线程,生成路径 /proc/%d/task/%s/status(%s 为线程 TID),通过 openat 打开该文件,读取内容到缓冲区 s2。
检查 TracerPid 字段在 status 文件内容中搜索 TracerPid: 关键字,找到后解析其值:
若 TracerPid 为非 0 值,说明进程被调试器跟踪;
定位并解析 Uid: 字段循环读取文件内容,通过 strncmp 匹配 Uid: 关键字(长度 4)。找到后从字段后解析数字形式的 UID 值,利用 atol 转换为整数。
资源清理与结果返回关闭文件描述符,返回解析得到的 UID 值。主逻辑会将该 UID 与进程预期 UID 对比,若不一致则判定为被调试。
4F6B8
生成进程 maps 文件路径通过 snprintf 拼接路径 /proc/%d/task/%d/maps(两个 %d 均为目标进程 PID)。/proc/[pid]/task/[tid]/maps 文件记录了进程(线程)的内存映射信息,包含加载的动态库路径。
打开并读取 maps 文件用 syscall_B232C 调用 SYS_openat 打开 maps 文件,若打开成功(返回值非负),通过 read_C76C 读取文件内容到缓冲区 s_1(每次读取 1024 字节)。
筛选动态库路径循环读取 maps 文件内容,通过 sscanf 提取每行中的动态库路径(maps 文件每行末尾记录映射文件路径,动态库以 .so 结尾)。
动态库合法性校验基于提取的动态库路径(haystack)执行多层校验,全部通过则判定为 “合法”(返回 0),否则判定为 “违规”(返回 1):
4FD70
读取/proc/self/cmdline
部分代码逻辑由AI分析并没有写代码验证,可能存在不准确的地方
import os
import struct
from elftools.elf.elffile import ELFFile
SOURCE_ELF_PATH = r"dump2_libbaiduprotect.so"
TARGET_ELF_PATH = r"libbaiduprotect.so"
PATCH_VA_START = 0xc6f4
PATCH_VA_END = 0x88ce4
TARGET_VA_START = 0xc6f4
PATCH_SIZE = PATCH_VA_END - PATCH_VA_START
def va_to_fa(elf_path: str, va: int) -> int:
with open(elf_path, 'rb') as f:
elf_file = ELFFile(f)
for segment in elf_file.iter_segments():
if segment['p_type'] == 'PT_LOAD':
seg_va_start = segment['p_vaddr']
seg_va_end = seg_va_start + segment['p_memsz']
if seg_va_start <= va < seg_va_end:
offset_in_segment = va - seg_va_start
file_offset = segment['p_offset'] + offset_in_segment
if offset_in_segment < segment['p_filesz']:
return file_offset
else:
raise ValueError(
f"VA {hex(va)} falls into BSS/uninitialized part of segment in {elf_path}. Cannot patch."
)
raise ValueError(f"VA {hex(va)} not found in any loadable segment of {elf_path}.")
def patch_elf(source_path: str, target_path: str, src_va: int, tgt_va: int, size: int):
print(f"--- ???? 开始补丁操作 ---")
print(f"源 ELF: {source_path}")
print(f"目标 ELF: {target_path}")
print(f"源 VA 范围: {hex(src_va)} - {hex(src_va + size)}")
print(f"目标 VA 范围: {hex(tgt_va)} - {hex(tgt_va + size)}")
print(f"补丁大小: {size} 字节")
try:
src_fa_start = va_to_fa(source_path, src_va)
src_fa_end = va_to_fa(source_path, src_va + size - 1)
if src_fa_end != src_fa_start + size - 1:
raise ValueError("Source VA range conversion resulted in non-contiguous FA range. Check ELF structure.")
tgt_fa_start = va_to_fa(target_path, tgt_va)
tgt_fa_end = va_to_fa(target_path, tgt_va + size - 1)
if tgt_fa_end != tgt_fa_start + size - 1:
raise ValueError("Target VA range conversion resulted in non-contiguous FA range. Check ELF structure.")
except ValueError as e:
print(f"❌ 地址转换失败: {e}")
return
print(f"✅ 地址转换成功:")
print(f"源 FA 范围: {hex(src_fa_start)} - {hex(src_fa_start + size)}")
print(f"目标 FA 范围: {hex(tgt_fa_start)} - {hex(tgt_fa_start + size)}")
patch_data = b''
try:
with open(source_path, 'rb') as f_src:
f_src.seek(src_fa_start)
patch_data = f_src.read(size)
if len(patch_data) != size:
raise IOError(f"Failed to read {size} bytes from source FA {hex(src_fa_start)}. Read {len(patch_data)} bytes.")
except Exception as e:
print(f"❌ 读取源文件失败: {e}")
return
try:
with open(target_path, 'r+b') as f_tgt:
f_tgt.seek(tgt_fa_start)
f_tgt.write(patch_data)
except Exception as e:
print(f"❌ 写入目标文件失败: {e}")
return
print(f"✨ 补丁成功!{size} 字节的数据已从源VA {hex(src_va)} 拷贝到目标VA {hex(tgt_va)}。")
print(f"请检查文件 {target_path}。")
if __name__ == '__main__':
patch_elf(
SOURCE_ELF_PATH,
TARGET_ELF_PATH,
PATCH_VA_START,
TARGET_VA_START,
PATCH_SIZE
)
import os
import struct
from elftools.elf.elffile import ELFFile
SOURCE_ELF_PATH = r"dump2_libbaiduprotect.so"
TARGET_ELF_PATH = r"libbaiduprotect.so"
PATCH_VA_START = 0xc6f4
PATCH_VA_END = 0x88ce4
TARGET_VA_START = 0xc6f4
PATCH_SIZE = PATCH_VA_END - PATCH_VA_START
def va_to_fa(elf_path: str, va: int) -> int:
with open(elf_path, 'rb') as f:
elf_file = ELFFile(f)
for segment in elf_file.iter_segments():
if segment['p_type'] == 'PT_LOAD':
seg_va_start = segment['p_vaddr']
seg_va_end = seg_va_start + segment['p_memsz']
if seg_va_start <= va < seg_va_end:
offset_in_segment = va - seg_va_start
file_offset = segment['p_offset'] + offset_in_segment
if offset_in_segment < segment['p_filesz']:
return file_offset
else:
raise ValueError(
f"VA {hex(va)} falls into BSS/uninitialized part of segment in {elf_path}. Cannot patch."
)
raise ValueError(f"VA {hex(va)} not found in any loadable segment of {elf_path}.")
def patch_elf(source_path: str, target_path: str, src_va: int, tgt_va: int, size: int):
print(f"--- ???? 开始补丁操作 ---")
print(f"源 ELF: {source_path}")
print(f"目标 ELF: {target_path}")
print(f"源 VA 范围: {hex(src_va)} - {hex(src_va + size)}")
print(f"目标 VA 范围: {hex(tgt_va)} - {hex(tgt_va + size)}")
print(f"补丁大小: {size} 字节")
try:
src_fa_start = va_to_fa(source_path, src_va)
src_fa_end = va_to_fa(source_path, src_va + size - 1)
if src_fa_end != src_fa_start + size - 1:
raise ValueError("Source VA range conversion resulted in non-contiguous FA range. Check ELF structure.")
tgt_fa_start = va_to_fa(target_path, tgt_va)
tgt_fa_end = va_to_fa(target_path, tgt_va + size - 1)
if tgt_fa_end != tgt_fa_start + size - 1:
raise ValueError("Target VA range conversion resulted in non-contiguous FA range. Check ELF structure.")
except ValueError as e:
print(f"❌ 地址转换失败: {e}")
return
print(f"✅ 地址转换成功:")
print(f"源 FA 范围: {hex(src_fa_start)} - {hex(src_fa_start + size)}")
print(f"目标 FA 范围: {hex(tgt_fa_start)} - {hex(tgt_fa_start + size)}")
patch_data = b''
try:
with open(source_path, 'rb') as f_src:
f_src.seek(src_fa_start)
patch_data = f_src.read(size)
if len(patch_data) != size:
raise IOError(f"Failed to read {size} bytes from source FA {hex(src_fa_start)}. Read {len(patch_data)} bytes.")
except Exception as e:
print(f"❌ 读取源文件失败: {e}")
return
try:
with open(target_path, 'r+b') as f_tgt:
f_tgt.seek(tgt_fa_start)
f_tgt.write(patch_data)
except Exception as e:
print(f"❌ 写入目标文件失败: {e}")
return
print(f"✨ 补丁成功!{size} 字节的数据已从源VA {hex(src_va)} 拷贝到目标VA {hex(tgt_va)}。")
print(f"请检查文件 {target_path}。")
if __name__ == '__main__':
patch_elf(
SOURCE_ELF_PATH,
TARGET_ELF_PATH,
PATCH_VA_START,
TARGET_VA_START,
PATCH_SIZE
)
2025-11-01 02:29:58.320 9182-9182 HOOK pid-9182 I [BaiduProtect::0xa4390]flush cache: start:0xb23c0 end:0xba738
2025-11-01 02:29:58.380 9182-9182 HOOK pid-9182 I [BaiduProtect::0xad3e0]flush cache: start:0xc6f4 end:0x88ce4
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec2_23A3C::0xa8e0]: FeatureLibcProtection
2025-11-01 02:29:58.388 9182-9273 HOOK pid-9182 I [dec3_203FC::0x52e8c]: /proc/%d/cmdline
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec1_2015c::0xab8c]: unknown
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec1_2015c::0xacd8]: bdp.
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec5_2023C::0xacf4]: stamp-cert-sha256
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec1_2015c::0xada0]: FeatureMetaData
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec4_2031C::0xaff8]: FeatLogProtection
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec1_2015c::0xb4b4]: /sbin/.magisk/
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec5_2023C::0xb4d0]: /sbin/.core/mirror
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec4_2031C::0xb4e0]: /sbin/.core/img
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec3_203FC::0xb4f0]: /sbin/.core/db-0/magisk.db
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec6_204DC::0xb500]: /dev/.magisk.unblock
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec7_205BC::0xb51c]: /sbin/magiskinit
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec8_2069C::0xb52c]: /sbin/magisk
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec9_2077C::0xb53c]: /sbin/.magisk
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec1_2015c::0xb8b4]: ro.build.version.release
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec5_2023C::0xb8c8]: ro.build.version.incremental
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec4_2031C::0xb8dc]: ro.build.version.codename
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec3_203FC::0xb8f0]: ro.build.version.sdk
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec6_204DC::0xb904]: ro.product.model
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec7_205BC::0xb918]: ro.product.manufacturer
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec8_2069C::0xb92c]: ro.product.board
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec9_2077C::0xb940]: ro.product.brand
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec1_2015c::0xbad0]: FeatCheckRoot
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec1_2015c::0xbb70]: /etc/mumu-configs/device-prop-configs/mumu.config
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec5_2023C::0xbb8c]: /data/local/cfg-gdaeg
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec4_2031C::0xbb9c]: /data/local/cfg-yzi
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec3_203FC::0xbbac]: /data/local/cfg-hzg
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec6_204DC::0xbbbc]: /data/local/cfg-znz
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec7_205BC::0xbbcc]: /data/local/cfg-ndi
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec8_2069C::0xbbdc]: /data/local/cfg-zhz
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec9_2077C::0xbbec]: /mnt/windows/BstSharedFolder
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec6_204DC::0xbd78]: FeatCheckPmsHook
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec6_204DC::0xbe14]: FeatureMemoryChecker
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec3_203FC::0xbf44]: FeatureNativeAntiDebug
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec9_2077C::0xbfe4]: FeatureJavaAntiDebug
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec1_2015c::0xc080]: FeatureAntiMthook
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec1_2015c::0xc198]: b0f957fc8d26239fe1d7d0fd0851ef3dcf86b8c2
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec1_2015c::0xc3b4]: FeatureSharedPrefEncryption
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec5_2023C::0xc414]: FeatureFileEncryption
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec4_2031C::0xc46c]: FeatureSQLiteEncryption
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec1_2015c::0xc4f0]: <?xml
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec1_2015c::0x16728]: _exit
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec5_2023C::0x16748]: exit
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec4_2031C::0x16768]: pthread_create
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec3_203FC::0x16788]: pthread_join
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec6_204DC::0x167a8]: memcpy
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec7_205BC::0x167c8]: malloc
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec8_2069C::0x167e8]: calloc
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec9_2077C::0x16808]: memset
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec5_2023C::0x50ddc]: bin/mt/apksignaturekillerplus/HookApplication
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec4_2031C::0x50e48]: libmthook.so
2025-11-01 02:29:58.394 9182-9280 HOOK pid-9182 I [dec1_2015c::0x4fdf4]: gdbserver
2025-11-01 02:29:58.394 9182-9280 HOOK pid-9182 I [dec5_2023C::0x4fe04]: gdb
2025-11-01 02:29:58.394 9182-9280 HOOK pid-9182 I [dec4_2031C::0x4fe14]: android_server
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec7_205BC::0x513e0]: android/app/ActivityThread
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec8_2069C::0x51408]: currentActivityThread
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec9_2077C::0x51418]: ()Landroid/app/ActivityThread;
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec5_2023C::0x1440c]: n1
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec4_2031C::0x14420]: (Landroid/content/Context;Ljava/lang/String;Ljava/lang/String;Ljava/lang/String;I)V
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec3_203FC::0x1443c]: n2
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec6_204DC::0x14450]: (Landroid/content/Context;)V
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec7_205BC::0x1446c]: n3
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec8_2069C::0x14480]: (Landroid/content/Context;)V
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec1_2015c::0x14660]: %s/.bdlock
2025-11-01 02:29:58.395 9272-9182 HOOK pid-9272 I [BaiduProtect::0x53320]flush cache: start:0xae54a01c end:0xae54a03c
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec9_2077C::0x1de7c]: assets/%s.md
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec1_2015c::0x26fa0]: %s/.1
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec5_2023C::0x27004]: %s
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec4_2031C::0x27048]: %s/1
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.437 9182-9182 HOOK pid-9182 I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.474 9182-9182 HOOK pid-9182 I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.507 9182-9182 HOOK pid-9182 I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.534 9182-9182 HOOK pid-9182 I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.594 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.657 9182-9280 HOOK com.mi.car.mobile I [dec6_204DC::0x50a04]: android/os/Debug
2025-11-01 02:29:58.657 9182-9280 HOOK com.mi.car.mobile I [dec7_205BC::0x50a28]: isDebuggerConnected
2025-11-01 02:29:58.657 9182-9280 HOOK com.mi.car.mobile I [dec8_2069C::0x50a38]: ()Z
2025-11-01 02:29:58.657 9182-9280 [Hook] com.mi.car.mobile D 拦截IsDebuggerConnected!
2025-11-01 02:29:58.663 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.725 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.784 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.830 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.868 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.894 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.907 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.919 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.999 9182-9539 HOOK com.mi.car.mobile I [dec8_2069C::0x1dd18]: assets/%s-sec.dex
2025-11-01 02:29:59.152 9182-9539 HOOK com.mi.car.mobile I [dec3_203FC::0x50eb0]: /data/data/
2025-11-01 02:29:59.152 9182-9539 HOOK com.mi.car.mobile I [dec6_204DC::0x50fc4]: /data/user/0
2025-11-01 02:29:59.152 9182-9539 HOOK com.mi.car.mobile I [dec1_2015c::0x50cc0]: /proc/self/fd/%d
2025-11-01 02:30:00.024 9752-9752 [Hook] pid-9752 D 拦截IsDebuggerConnected!
2025-11-01 02:30:00.448 9752-9910 [Hook] com.mi.car.mobile D 拦截IsDebuggerConnected!
2025-11-01 02:29:58.320 9182-9182 HOOK pid-9182 I [BaiduProtect::0xa4390]flush cache: start:0xb23c0 end:0xba738
2025-11-01 02:29:58.380 9182-9182 HOOK pid-9182 I [BaiduProtect::0xad3e0]flush cache: start:0xc6f4 end:0x88ce4
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec2_23A3C::0xa8e0]: FeatureLibcProtection
2025-11-01 02:29:58.388 9182-9273 HOOK pid-9182 I [dec3_203FC::0x52e8c]: /proc/%d/cmdline
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec1_2015c::0xab8c]: unknown
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec1_2015c::0xacd8]: bdp.
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec5_2023C::0xacf4]: stamp-cert-sha256
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec1_2015c::0xada0]: FeatureMetaData
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec4_2031C::0xaff8]: FeatLogProtection
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec1_2015c::0xb4b4]: /sbin/.magisk/
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec5_2023C::0xb4d0]: /sbin/.core/mirror
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec4_2031C::0xb4e0]: /sbin/.core/img
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec3_203FC::0xb4f0]: /sbin/.core/db-0/magisk.db
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec6_204DC::0xb500]: /dev/.magisk.unblock
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec7_205BC::0xb51c]: /sbin/magiskinit
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec8_2069C::0xb52c]: /sbin/magisk
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec9_2077C::0xb53c]: /sbin/.magisk
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec1_2015c::0xb8b4]: ro.build.version.release
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec5_2023C::0xb8c8]: ro.build.version.incremental
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec4_2031C::0xb8dc]: ro.build.version.codename
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec3_203FC::0xb8f0]: ro.build.version.sdk
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec6_204DC::0xb904]: ro.product.model
2025-11-01 02:29:58.388 9182-9182 HOOK pid-9182 I [dec7_205BC::0xb918]: ro.product.manufacturer
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec8_2069C::0xb92c]: ro.product.board
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec9_2077C::0xb940]: ro.product.brand
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec1_2015c::0xbad0]: FeatCheckRoot
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec1_2015c::0xbb70]: /etc/mumu-configs/device-prop-configs/mumu.config
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec5_2023C::0xbb8c]: /data/local/cfg-gdaeg
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec4_2031C::0xbb9c]: /data/local/cfg-yzi
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec3_203FC::0xbbac]: /data/local/cfg-hzg
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec6_204DC::0xbbbc]: /data/local/cfg-znz
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec7_205BC::0xbbcc]: /data/local/cfg-ndi
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec8_2069C::0xbbdc]: /data/local/cfg-zhz
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec9_2077C::0xbbec]: /mnt/windows/BstSharedFolder
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec6_204DC::0xbd78]: FeatCheckPmsHook
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec6_204DC::0xbe14]: FeatureMemoryChecker
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec3_203FC::0xbf44]: FeatureNativeAntiDebug
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec9_2077C::0xbfe4]: FeatureJavaAntiDebug
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec1_2015c::0xc080]: FeatureAntiMthook
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec1_2015c::0xc198]: b0f957fc8d26239fe1d7d0fd0851ef3dcf86b8c2
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec1_2015c::0xc3b4]: FeatureSharedPrefEncryption
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec5_2023C::0xc414]: FeatureFileEncryption
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec4_2031C::0xc46c]: FeatureSQLiteEncryption
2025-11-01 02:29:58.389 9182-9182 HOOK pid-9182 I [dec1_2015c::0xc4f0]: <?xml
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec1_2015c::0x16728]: _exit
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec5_2023C::0x16748]: exit
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec4_2031C::0x16768]: pthread_create
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec3_203FC::0x16788]: pthread_join
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec6_204DC::0x167a8]: memcpy
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec7_205BC::0x167c8]: malloc
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec8_2069C::0x167e8]: calloc
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec9_2077C::0x16808]: memset
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec5_2023C::0x50ddc]: bin/mt/apksignaturekillerplus/HookApplication
2025-11-01 02:29:58.393 9182-9182 HOOK pid-9182 I [dec4_2031C::0x50e48]: libmthook.so
2025-11-01 02:29:58.394 9182-9280 HOOK pid-9182 I [dec1_2015c::0x4fdf4]: gdbserver
2025-11-01 02:29:58.394 9182-9280 HOOK pid-9182 I [dec5_2023C::0x4fe04]: gdb
2025-11-01 02:29:58.394 9182-9280 HOOK pid-9182 I [dec4_2031C::0x4fe14]: android_server
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec7_205BC::0x513e0]: android/app/ActivityThread
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec8_2069C::0x51408]: currentActivityThread
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec9_2077C::0x51418]: ()Landroid/app/ActivityThread;
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec5_2023C::0x1440c]: n1
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec4_2031C::0x14420]: (Landroid/content/Context;Ljava/lang/String;Ljava/lang/String;Ljava/lang/String;I)V
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec3_203FC::0x1443c]: n2
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec6_204DC::0x14450]: (Landroid/content/Context;)V
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec7_205BC::0x1446c]: n3
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec8_2069C::0x14480]: (Landroid/content/Context;)V
2025-11-01 02:29:58.394 9182-9182 HOOK pid-9182 I [dec1_2015c::0x14660]: %s/.bdlock
2025-11-01 02:29:58.395 9272-9182 HOOK pid-9272 I [BaiduProtect::0x53320]flush cache: start:0xae54a01c end:0xae54a03c
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec9_2077C::0x1de7c]: assets/%s.md
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec1_2015c::0x26fa0]: %s/.1
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec5_2023C::0x27004]: %s
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec4_2031C::0x27048]: %s/1
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.395 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec3_203FC::0x2714c]: /%d.jar
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec6_204DC::0x271b4]: /%d.odex
2025-11-01 02:29:58.396 9182-9182 HOOK pid-9182 I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.437 9182-9182 HOOK pid-9182 I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.474 9182-9182 HOOK pid-9182 I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.507 9182-9182 HOOK pid-9182 I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.534 9182-9182 HOOK pid-9182 I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.594 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.657 9182-9280 HOOK com.mi.car.mobile I [dec6_204DC::0x50a04]: android/os/Debug
2025-11-01 02:29:58.657 9182-9280 HOOK com.mi.car.mobile I [dec7_205BC::0x50a28]: isDebuggerConnected
2025-11-01 02:29:58.657 9182-9280 HOOK com.mi.car.mobile I [dec8_2069C::0x50a38]: ()Z
2025-11-01 02:29:58.657 9182-9280 [Hook] com.mi.car.mobile D 拦截IsDebuggerConnected!
2025-11-01 02:29:58.663 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.725 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.784 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.830 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.868 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.894 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.907 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.919 9182-9182 HOOK com.mi.car.mobile I [dec4_2031C::0x1d8f0]: assets/%s%d.jar
2025-11-01 02:29:58.999 9182-9539 HOOK com.mi.car.mobile I [dec8_2069C::0x1dd18]: assets/%s-sec.dex
2025-11-01 02:29:59.152 9182-9539 HOOK com.mi.car.mobile I [dec3_203FC::0x50eb0]: /data/data/
2025-11-01 02:29:59.152 9182-9539 HOOK com.mi.car.mobile I [dec6_204DC::0x50fc4]: /data/user/0
2025-11-01 02:29:59.152 9182-9539 HOOK com.mi.car.mobile I [dec1_2015c::0x50cc0]: /proc/self/fd/%d
2025-11-01 02:30:00.024 9752-9752 [Hook] pid-9752 D 拦截IsDebuggerConnected!
2025-11-01 02:30:00.448 9752-9910 [Hook] com.mi.car.mobile D 拦截IsDebuggerConnected!
import idaapi
import idautils
import idc
def decrypt(cipher, keybox):
v4 = len(cipher) // 2
result = [0] * (v4 + 1)
result[v4] = 0
if not cipher:
return bytes(result[:v4])
n0x3A = cipher[0]
n8 = 0
v8_idx = 2
v9_idx = 0
while n0x3A != 0:
n0x3A_1 = cipher[v8_idx - 1]
if n0x3A >= 0x3A:
v11 = -112
else:
v11 = 0
if n0x3A_1 >= 0x3A:
v12 = -55
else:
v12 = -48
if n8 == 8:
n8 = 0
decoded_byte = keybox[n8] ^ (v11 + 16 * n0x3A + v12 + n0x3A_1)
result[v9_idx] = decoded_byte & 0xFF
v9_idx += 1
n0x3A = cipher[v8_idx] if v8_idx < len(cipher) else 0
n8 += 1
v8_idx += 2
return bytes(result[:v9_idx])
def find_all_decfunc(start_ea, end_ea):
print(f"--- 正在查找范围 {hex(start_ea)} 到 {hex(end_ea)} 内的数据引用 ---")
decfunc=[]
ea = start_ea
while ea < end_ea:
for xref in idautils.XrefsTo(ea):
ref_from_ea = xref.frm
func_ea = idc.get_func_attr(ref_from_ea, idc.FUNCATTR_START)
decfunc.append(func_ea)
ea +=8
print("--- 查找结束 ---")
return decfunc
def get_aarch64_first_arg(call_ea):
ARG_REG = "X0"
ea = idc.prev_head(call_ea)
func_start = idc.get_func_attr(call_ea, idc.FUNCATTR_START)
max_lookback = 10
for i in range(max_lookback):
if ea == idc.BADADDR or ea < func_start:
print(f"[-] 追溯到函数开始或无法继续,未找到 {ARG_REG} 的设置指令。")
return None
mnem = idc.print_insn_mnem(ea)
op_type0 = idc.get_operand_type(ea, 0)
op_text0 = idc.print_operand(ea, 0)
if op_type0 == idc.o_reg and op_text0 == ARG_REG:
op_type1 = idc.get_operand_type(ea, 1)
if op_type1 == idc.o_imm or op_type1 == idc.o_near:
arg_value = idc.get_operand_value(ea, 1)
string_content = idc.get_strlit_contents(arg_value, -1, idc.STRTYPE_C)
value_name = idc.get_name(arg_value, idaapi.GN_DEMANGLED)
return string_content
elif mnem == "LDR" and op_type1 == idc.o_displ:
print(f"指令: {hex(ea)} ({idc.generate_disasm_line(ea,0)}) => 复杂内存加载 (LDR),需要数据流分析")
return
else:
print(f"指令: {hex(ea)} ({idc.generate_disasm_line(ea,0)}) => 复杂寄存器/内存操作")
return
ea = idc.prev_head(ea)
return None
KEYBOX_START_EA = 0xB3671
KEYBOX_END_EA = 0xB3989
decfuncs=find_all_decfunc(KEYBOX_START_EA, KEYBOX_END_EA)
for idx,func_start in enumerate(decfuncs):
for xref in idautils.XrefsTo(func_start):
ref_from_ea = xref.frm
cipher=get_aarch64_first_arg(ref_from_ea)
if not cipher:
print(f"需要手动解密 : {hex(ref_from_ea)}")
continue
keybox=list(idc.get_bytes(START_EA+idx*8,8))
plain=decrypt(cipher,keybox)
print(f"[{hex(ref_from_ea)}]: {plain}")
idc.set_cmt(ref_from_ea, f"{plain.decode('utf-8', errors='ignore')}", True)
import idaapi
import idautils
import idc
def decrypt(cipher, keybox):
v4 = len(cipher) // 2
result = [0] * (v4 + 1)
result[v4] = 0
if not cipher:
return bytes(result[:v4])
n0x3A = cipher[0]
n8 = 0
v8_idx = 2
v9_idx = 0
while n0x3A != 0:
n0x3A_1 = cipher[v8_idx - 1]
if n0x3A >= 0x3A:
v11 = -112
else:
v11 = 0
if n0x3A_1 >= 0x3A:
v12 = -55
else:
v12 = -48
if n8 == 8:
n8 = 0
decoded_byte = keybox[n8] ^ (v11 + 16 * n0x3A + v12 + n0x3A_1)
result[v9_idx] = decoded_byte & 0xFF
v9_idx += 1
n0x3A = cipher[v8_idx] if v8_idx < len(cipher) else 0
n8 += 1
v8_idx += 2
return bytes(result[:v9_idx])
def find_all_decfunc(start_ea, end_ea):
print(f"--- 正在查找范围 {hex(start_ea)} 到 {hex(end_ea)} 内的数据引用 ---")
decfunc=[]
ea = start_ea
while ea < end_ea:
for xref in idautils.XrefsTo(ea):
ref_from_ea = xref.frm
func_ea = idc.get_func_attr(ref_from_ea, idc.FUNCATTR_START)
decfunc.append(func_ea)
ea +=8
print("--- 查找结束 ---")
return decfunc
def get_aarch64_first_arg(call_ea):
ARG_REG = "X0"
ea = idc.prev_head(call_ea)
func_start = idc.get_func_attr(call_ea, idc.FUNCATTR_START)
max_lookback = 10
for i in range(max_lookback):
if ea == idc.BADADDR or ea < func_start:
print(f"[-] 追溯到函数开始或无法继续,未找到 {ARG_REG} 的设置指令。")
return None
mnem = idc.print_insn_mnem(ea)
op_type0 = idc.get_operand_type(ea, 0)
op_text0 = idc.print_operand(ea, 0)
if op_type0 == idc.o_reg and op_text0 == ARG_REG:
op_type1 = idc.get_operand_type(ea, 1)
if op_type1 == idc.o_imm or op_type1 == idc.o_near:
arg_value = idc.get_operand_value(ea, 1)
string_content = idc.get_strlit_contents(arg_value, -1, idc.STRTYPE_C)
value_name = idc.get_name(arg_value, idaapi.GN_DEMANGLED)
return string_content
elif mnem == "LDR" and op_type1 == idc.o_displ:
print(f"指令: {hex(ea)} ({idc.generate_disasm_line(ea,0)}) => 复杂内存加载 (LDR),需要数据流分析")
return
else:
print(f"指令: {hex(ea)} ({idc.generate_disasm_line(ea,0)}) => 复杂寄存器/内存操作")
return
ea = idc.prev_head(ea)
return None
KEYBOX_START_EA = 0xB3671
KEYBOX_END_EA = 0xB3989
decfuncs=find_all_decfunc(KEYBOX_START_EA, KEYBOX_END_EA)
for idx,func_start in enumerate(decfuncs):
for xref in idautils.XrefsTo(func_start):
ref_from_ea = xref.frm
cipher=get_aarch64_first_arg(ref_from_ea)
if not cipher:
print(f"需要手动解密 : {hex(ref_from_ea)}")
continue
keybox=list(idc.get_bytes(START_EA+idx*8,8))
plain=decrypt(cipher,keybox)
print(f"[{hex(ref_from_ea)}]: {plain}")
idc.set_cmt(ref_from_ea, f"{plain.decode('utf-8', errors='ignore')}", True)
--- 正在查找范围 0xb3671 到 0xb3989 内的数据引用 ---
--- 查找结束 ---
[0xab88]: b'unknown\x00'
[0xacd4]: b'bdp.\x00\x00\x00\x00'
[0xad9c]: b'FeatureMetaData'
[0xb4b0]: b'/sbin/.magisk/'
[0xb8b0]: b'ro.build.version.release'
[0xbacc]: b'FeatCheckRoot'
[0xbb6c]: b'/etc/mumu-configs/device-prop-configs/mumu.config'
[0xc07c]: b'FeatureAntiMthook'
[0xc194]: b'b0f957fc8d26239fe1d7d0fd0851ef3dcf86b8c2'
[0xc3b0]: b'FeatureSharedPrefEncryption'
[0xc4ec]: b'<?xml\x00\x00\x00'
[0xcfd4]: b'\x00\x00\x00\x00\x00\x00\x00\x00'
[0x11a30]: b'%s %*s %*s %*s %*s %*s'
指令: 0x14654 (ADD X0, X8,
需要手动解密 : 0x1465c -> b'%s/.bdlock'
[0x16724]: b'_exit\x00\x00\x00'
[0x1ea4c]: b'\x00\x00\x00\x00\x00\x00\x00\x00'
[0x26f9c]: b'%s/.1\x00\x00\x00'
[0x2dbb0]: b'/proc/self/maps'
指令: 0x34fa4 (ADD X0, X9,
需要手动解密 : 0x34fac libandroid_runtime.so
指令: 0x47834 (MOV X0, X28) => 复杂寄存器/内存操作
需要手动解密 : 0x47838 %n%*s%n %n%*s%n %n%*s%n %n%*s%n %d %d
[0x47a30]: b' %n%*s%n %n%*s%n %n%*s%n %n%*s%n %d %d'
[0x4e450]: b'java/lang/Throwable'
指令: 0x4ed4c (ADD X0, X8,
需要手动解密 : 0x4ed50 android/app/ActivityThread
[0x4f488]: b'/proc/self/mem'
[0x4fdf0]: b'gdbserver'
[0x50cbc]: b'/proc/self/fd/%d'
[0x78364]: b'.db\x00\x00\x00\x00\x00'
[0x7c850]: b'/\x00\x00\x00\x00\x00\x00\x00'
[0xacf0]: b'stamp-cert-sha256'
[0xb4cc]: b'/sbin/.core/mirror'
[0xb8c4]: b'ro.build.version.incremental'
[0xbb88]: b'/data/local/cfg-gdaeg'
[0xc410]: b'FeatureFileEncryption'
[0xd044]: b'\x00\x00\x00\x00\x00\x00\x00\x00'
[0x11a4c]: b'/proc/self/maps'
指令: 0x14404 (MOV X0, X8) => 复杂寄存器/内存操作
需要手动解密 : 0x14408 n1\x00\x00\x00\x00\x00\x00
[0x16744]: b'exit\x00\x00\x00\x00'
[0x1d864]: b'assets/%s%d.i.dex'
[0x27000]: b'%s\x00\x00\x00\x00\x00\x00'
[0x2dbc0]: b'r\x00\x00\x00\x00\x00\x00\x00'
指令: 0x34fdc (ADD X0, X8,
需要手动解密 : 0x34fe0 __android_log_buf_write
[0x4774c]: b'/proc/mounts'
[0x4e474]: b'getStackTrace'
指令: 0x4eda8 (ADD X0, X8,
需要手动解密 : 0x4edac sPackageManager
[0x4f4a8]: b'/proc/self/pagemap'
[0x4fe00]: b'gdb\x00\x00\x00\x00\x00'
[0x50dd8]: b'bin/mt/apksignaturekillerplus/HookApplication'
[0x784b0]: b'-journal'
[0x79f38]: b'/proc/self/fd/%d'
[0x7c9a8]: b'/%s/%s/%s'
[0xaff4]: b'FeatLogProtection'
[0xb4dc]: b'/sbin/.core/img'
[0xb8d8]: b'ro.build.version.codename'
[0xbb98]: b'/data/local/cfg-yzi'
[0xc468]: b'FeatureSQLiteEncryption'
[0xd0b4]: b'\x00\x00\x00\x00\x00\x00\x00\x00'
[0x11a5c]: b'r\x00\x00\x00\x00\x00\x00\x00'
指令: 0x14418 (MOV X0, X8) => 复杂寄存器/内存操作
需要手动解密 : 0x1441cb'(Landroid/content/Context;Ljava/lang/String;Ljava/lang/String;Ljava/lang/String;I)V
[0x16764]: b'pthread_create'
[0x1d8ec]: b'assets/%s%d.jar'
[0x27044]: b'%s/1\x00\x00\x00\x00'
[0x2a3d0]: b'classes\x00'
[0x2dbfc]: b'r--p\x00\x00\x00\x00'
[0x4775c]: b'r\x00\x00\x00\x00\x00\x00\x00'
[0x4e484]: b'()[Ljava/lang/StackTraceElement;'
指令: 0x4edb8 (ADD X0, X8,
需要手动解密 : 0x4edbc Landroid/content/pm/IPackageManager;
[0x4f50c]: b'/proc/%d/mem'
[0x4fe10]: b'android_server'
[0x50e44]: b'libmthook.so'
[0x78244]: b'libsqlite.so'
[0x78728]: b'libsqlite.so'
[0x7a060]: b'/shared_prefs/'
[0x7cdbc]: b'/proc/self/fd/%d'
[0xb4ec]: b'/sbin/.core/db-0/magisk.db'
[0xb8ec]: b'ro.build.version.sdk'
[0xbba8]: b'/data/local/cfg-hzg'
[0xbf40]: b'FeatureNativeAntiDebug'
[0xd124]: b'\x00\x00\x00\x00\x00\x00\x00\x00'
指令: 0x14434 (MOV X0, X8) => 复杂寄存器/内存操作
需要手动解密 : 0x14438 b'n2\x00\x00\x00\x00\x00\x00'
[0x16784]: b'pthread_join'
[0x1d974]: b'assets/%s%d.d.jar'
[0x1ed80]: b'.\x00\x00\x00\x00\x00\x00\x00'
指令: 0x1ef7c (MOV X0, X22) => 复杂寄存器/内存操作
需要手动解密 : 0x1ef80 b'.\x00\x00\x00\x00\x00\x00\x00'
[0x27148]: b'/%d.jar\x00'
[0x2a3ec]: b'.dex\x00\x00\x00\x00'
[0x2dc0c]: b'%s %s %*s %*s %*s %s'
[0x478f0]: b'rw\x00\x00\x00\x00\x00\x00'
[0x4e4e4]: b'java/lang/StackTraceElement'
指令: 0x4ee60 (ADD X0, X8,
需要手动解密 : 0x4ee64 java/lang/reflect/Proxy
[0x4f540]: b'/proc/%d/pagemap'
[0x50eac]: b'/data/data/'
[0x52e88]: b'/proc/%d/cmdline'
[0x79a20]: b'SQLite\x00\x00'
[0x7a15c]: b'.\x00\x00\x00\x00\x00\x00\x00'
[0x7cee8]: b'android/os/Environment'
[0xb4fc]: b'/dev/.magisk.unblock'
[0xb900]: b'ro.product.model'
[0xbbb8]: b'/data/local/cfg-znz'
[0xbd74]: b'FeatCheckPmsHook'
[0xbe10]: b'FeatureMemoryChecker'
指令: 0x14448 (MOV X0, X8) => 复杂寄存器/内存操作
需要手动解密 : 0x1444c b'(Landroid/content/Context;)V'
[0x167a4]: b'memcpy\x00\x00'
[0x1da4c]: b'%s/lib\x00\x00'
[0x1ed9c]: b'..\x00\x00\x00\x00\x00\x00'
指令: 0x1ef94 (MOV X0, X23) => 复杂寄存器/内存操作
需要手动解密 : 0x1ef98 b'..\x00\x00\x00\x00\x00\x00'
指令: 0x271ac (MOV X0, X28) => 复杂寄存器/内存操作
需要手动解密 : 0x271b0 b'/%d.odex'
指令: 0x29ae0 (MOV X0, X24) => 复杂寄存器/内存操作
需要手动解密 : 0x29ae4 b'META-INF/'
[0x2dc1c]: b'r-xp\x00\x00\x00\x00'
[0x47af4]: b'1\x00\x00\x00\x00\x00\x00\x00'
[0x4e50c]: b'toString'
[0x50a00]: b'android/os/Debug'
[0x50fc0]: b'/data/user/0'
[0x78260]: b'\x00\x00\x00\x00\x00\x00\x00\x00'
[0x7876c]: b'\x00\x00\x00\x00\x00\x00\x00\x00'
[0x7a224]: b'.xml\x00\x00\x00\x00'
[0x7cf10]: b'getExternalStorageDirectory'
[0xb518]: b'/sbin/magiskinit'
[0xb914]: b'ro.product.manufacturer'
[0xbbc8]: b'/data/local/cfg-ndi'
指令: 0x14464 (MOV X0, X8) => 复杂寄存器/内存操作
需要手动解密 : 0x14468 b'n3\x00\x00\x00\x00\x00\x00'
[0x167c4]: b'malloc\x00\x00'
[0x1dbb0]: b'/.%s/lib'
[0x1ee3c]: b'/\x00\x00\x00\x00\x00\x00\x00'
指令: 0x1ef5c (MOV X0, X24) => 复杂寄存器/内存操作
需要手动解密 : 0x1ef60 b'/\x00\x00\x00\x00\x00\x00\x00'
[0x27530]: b'android/os/Build'
[0x29b00]: b'.MF\x00\x00\x00\x00\x00'
[0x47b04]: b'0\x00\x00\x00\x00\x00\x00\x00'
[0x4e51c]: b'()Ljava/lang/String;'
[0x50a24]: b'isDebuggerConnected'
[0x513dc]: b'android/app/ActivityThread'
[0x7b014]: b'open\x00\x00\x00\x00'
[0x7cf20]: b'()Ljava/io/File;'
[0xb528]: b'/sbin/magisk'
[0xb928]: b'ro.product.board'
[0xbbd8]: b'/data/local/cfg-zhz'
指令: 0x14478 (MOV X0, X8) => 复杂寄存器/内存操作
需要手动解密 : 0x1447c b'(Landroid/content/Context;)V'
[0x167e4]: b'calloc\x00\x00'
[0x1dd14]: b'assets/%s-sec.dex'
[0x1f0e4]: b'android/os/Build'
[0x27554]: b'FINGERPRINT'
[0x29b1c]: b'.SF\x00\x00\x00\x00\x00'
[0x47b14]: b'1\x00\x00\x00\x00\x00\x00\x00'
[0x4e3e0]: b'de/robv/android/xposed/XposedBridge'
[0x50a34]: b'()Z\x00\x00\x00\x00\x00'
[0x51404]: b'currentActivityThread'
[0x7b048]: b'close\x00\x00\x00'
[0x7cf68]: b'java/io/File'
[0xb538]: b'/sbin/.magisk'
[0xb93c]: b'ro.product.brand'
[0xbbe8]: b'/mnt/windows/BstSharedFolder'
[0xbfe0]: b'FeatureJavaAntiDebug'
[0x16804]: b'memset\x00\x00'
[0x1de78]: b'assets/%s.md'
[0x1f0f4]: b'MODEL\x00\x00\x00'
[0x27564]: b'Ljava/lang/String;'
[0x29b38]: b'.RSA\x00\x00\x00\x00'
[0x47b24]: b'1\x00\x00\x00\x00\x00\x00\x00'
指令: 0x4e810 (MOV X0, X21) => 复杂寄存器/内存操作
需要手动解密 : 0x4e814 b'com.lody.virtual'
[0x51414]: b'()Landroid/app/ActivityThread;'
[0x7b070]: b'read\x00\x00\x00\x00'
[0x7cf90]: b'getAbsolutePath'
[0xad00]: b'FeatureIntegrityCheck'
[0xb548]: b'/data/adb/magisk.img'
[0xb950]: b'ro.product.device'
[0xbbf8]: b'nemud.player_package'
[0x16824]: b'fopen\x00\x00\x00'
[0x1dfe0]: b'assets/%s/d0'
[0x1f3c4]: b'android/content/pm/Signature'
[0x26cdc]: b'%s/.config'
[0x26da0]: b'%s/.config'
[0x276a8]: b'%s/.config'
[0x277a8]: b'%s/.config'
[0x278a8]: b'%s/.config'
[0x47e28]: b'getprop\x00'
[0x4ea0c]: b'de/robv/android/xposed/XposedHelpers'
[0x5145c]: b'getApplication'
[0x7b098]: b'write\x00\x00\x00'
[0x7cfa0]: b'()Ljava/lang/String;'
[0xb558]: b'/data/adb/magisk.db'
[0xb964]: b'ro.product.name'
[0xbc08]: b'microvirt.dlhost'
[0x16844]: b'fclose\x00\x00'
[0x1e554]: b'/proc/self/maps'
[0x1f3e8]: b'android/content/pm/PackageInfo'
[0x27960]: b'/.%s/1/%d.jar'
[0x47e38]: b'r\x00\x00\x00\x00\x00\x00\x00'
[0x4ea64]: b'io.va.exposed64'
[0x5146c]: b'()Landroid/app/Application;'
[0x7b18c]: b'esp showHookInfo, hooked lib: '
[0x7d2b8]: b'/files/\x00'
[0xb568]: b'/data/adb/.boot_count'
[0xb978]: b'ro.hardware'
[0xbc18]: b'microvirt.memu_version'
[0x16864]: b'fgets\x00\x00\x00'
[0x1e564]: b'r\x00\x00\x00\x00\x00\x00\x00'
[0x1f40c]: b'android/content/pm/PackageManager'
[0x27a18]: b'/.%s/1/%d.'
指令: 0x47ea8 (MOV X0, X21) => 复杂寄存器/内存操作
需要手动解密 : 0x47eac b'[Android/aosp'
[0x4ea84]: b'/io.va.exposed64/virtual/'
[0x51638]: b'getPackageResourcePath'
[0x7b220]: b'[\x00\x00\x00\x00\x00\x00\x00'
[0x7d3c0]: b'/databases/'
[0xb578]: b'/data/adb/magisk_simple'
[0xb98c]: b'ro.product.cpu.abi'
[0xbc28]: b'persist.nox.model'
[0xbcd8]: b'FeatCheckHook'
[0x16884]: b'strtoul\x00'
指令: 0x1e5c8 (MOV X0, X21) => 复杂寄存器/内存操作
需要手动解密 : 0x1e5cc b'libart.so'
[0x1f430]: b'android/app/ActivityThread'
[0x27a58]: b'.jar\x00\x00\x00\x00'
指令: 0x47ec0 (MOV X0, X22) => 复杂寄存器/内存操作
需要手动解密 : 0x47ec4 b'[userdebug]'
[0x51648]: b'()Ljava/lang/String;'
[0x787b4]: b'open\x00\x00\x00\x00'
[0x7b24c]: b' ESP_HOOK_LIBJAVACORE'
[0x7d4c0]: b'.db\x00\x00\x00\x00\x00'
[0xac38]: b'FeatureProtectEnvironment'
[0xb588]: b'/data/adb/magisk'
[0xb9a0]: b'ro.product.cpu.abi2'
[0x168a4]: b'strtoull'
[0x1e65c]: b'libart.so'
[0x1f454]: b'android/app/ContextImpl'
指令: 0x47ed8 (MOV X0, X23) => 复杂寄存器/内存操作
需要手动解密 : 0x47edc b'[unlocked]'
[0x4d408]: b'sdk\x00\x00\x00\x00\x00'
[0x51924]: b'/data/app/'
[0x787d8]: b'close\x00\x00\x00'
[0x7b274]: b' (\x00\x00\x00\x00\x00\x00'
[0x7d744]: b'/shared_prefs/'
[0xb598]: b'/cache/.disable_magisk'
[0xb9b4]: b'ro.build.display.id'
[0x168c4]: b'strstr\x00\x00'
指令: 0x1e5e0 (MOV X0, X22) => 复杂寄存器/内存操作
需要手动解密 : 0x1e5e4 b'libdvm.so'
[0x1f478]: b'getSystemContext'
指令: 0x47ef0 (MOV X0, X24) => 复杂寄存器/内存操作
需要手动解密 : 0x47ef4 b'.flash.locked]: [0]'
[0x4d41c]: b'google_sdk'
[0x519c4]: b'-1/base.apk'
[0x787fc]: b'read\x00\x00\x00\x00'
[0x7b2a0]: b' JAVACORE_HOOK_OPEN'
[0x7d854]: b'.xml\x00\x00\x00\x00'
[0xb5a8]: b'/cache/magisk.log'
[0xb9c8]: b'ro.build.host'
[0x168e4]: b'ptrace\x00\x00'
[0x1e6c8]: b'libdvm.so'
[0x1f488]: b'()Landroid/app/ContextImpl;'
指令: 0x47f08 (MOV X0, X25) => 复杂寄存器/内存操作
需要手动解密 : 0x47f0c
[0x4d42c]: b'Andy\x00\x00\x00\x00'
[0x51a34]: b'/data/app/'
[0x78820]: b'write\x00\x00\x00'
[0x7b2cc]: b' JAVACORE_HOOK_CLOSE'
[0x7d980]: b'android/os/Environment'
[0xb5b8]: b'/init.magisk.rc'
[0xb9dc]: b'ro.build.user'
[0x16904]: b'mprotect'
指令: 0x1e5f8 (MOV X0, X23) => 复杂寄存器/内存操作
需要手动解密 : 0x1e5fc b'[ro.debuggable]: [1]'
[0x1f4b4]: b'currentActivityThread'
[0x4817c]: b'0\x00\x00\x00\x00\x00\x00\x00'
[0x4d43c]: b'ttVM_Hdragon'
[0x51b74]: b'-2/base.apk'
[0x78844]: b'pread\x00\x00\x00'
[0x7b2f8]: b' JAVACORE_HOOK_READ'
[0x7d9a8]: b'getExternalStorageState'
[0xb5c8]: b'/data/local/su'
[0xb9f0]: b'ro.build.id'
[0x16924]: b'strlen\x00\x00'
[0x1e734]: b'libvmkid_lemur.so'
[0x1f4c4]: b'()Landroid/app/ActivityThread;'
[0x48264]: b'which su'
[0x4d44c]: b'Droid4X\x00'
[0x51d6c]: b'/proc/%d/cmdline'
[0x78868]: b'pwrite\x00\x00'
[0x7b324]: b' JAVACORE_HOOK_WRITE'
[0x7d9b8]: b'()Ljava/lang/String;'
[0xb5e4]: b'/data/local/bin/su'
[0xba04]: b'ro.build.type'
[0x16944]: b'sscanf\x00\x00'
指令: 0x1e610 (MOV X0, X24) => 复杂寄存器/内存操作
需要手动解密 : 0x1e614 b'libaoc.so'
[0x1f51c]: b'getPackageManager'
[0x48274]: b'r\x00\x00\x00\x00\x00\x00\x00'
[0x4d45c]: b'nox\x00\x00\x00\x00\x00'
[0x51dac]: b'r\x00\x00\x00\x00\x00\x00\x00'
[0x7888c]: b'pread64\x00'
[0x7b350]: b' JAVACORE_HOOK_READ__CHK'
[0x7da20]: b'MEDIA_MOUNTED'
[0xb5f4]: b'/data/local/xbin/su'
[0xba18]: b'ro.build.tags'
[0x16964]: b'free\x00\x00\x00\x00'
[0x1e7a0]: b'libaoc.so'
[0x1f52c]: b'()Landroid/content/pm/PackageManager;'
[0x483a4]: b'/system/app/Superuser.apk'
[0x4d46c]: b'sdk_x86\x00'
[0x51f0c]: b'getPackageName'
[0x788b0]: b'pwrite64'
[0x7b37c]: b' JAVACORE_HOOK_WRITE__CHK'
[0x7da30]: b'Ljava/lang/String;'
[0xb604]: b'/sbin/su'
[0xba2c]: b'ro.build.fingerprint'
[0x16984]: b'strdup\x00\x00'
[0x1f56c]: b'getPackageInfo'
[0x48508]: b'/proc/%d/maps'
[0x4d47c]: b'sdk_google'
[0x51f1c]: b'()Ljava/lang/String;'
[0x788d4]: b'mmap\x00\x00\x00\x00'
[0x7b3a0]: b' )\x00\x00\x00\x00\x00\x00'
[0x7dd9c]: b'/tmp000000001'
[0xb614]: b'/system/bin/su'
[0xba40]: b'ro.secure'
[0x169a4]: b'strcmp\x00\x00'
[0x1f57c]: b'(Ljava/lang/String;I)Landroid/content/pm/PackageInfo;'
[0x48558]: b'com.saurik.substrate'
[0x4d48c]: b'vbox86p\x00'
[0x52138]: b'counter\x00'
[0x788f8]: b'munmap\x00\x00'
[0x7b3cc]: b' ESP_HOOK_LIBNATIVEHELPER'
[0x7e0c4]: b'/data/user/1'
[0xb624]: b'/system/bin/.ext/su'
[0xba54]: b'ro.debuggable'
[0x169c4]: b'strcasecmp'
[0x1f5dc]: b'signatures'
[0x48568]: b'XposedBridge.jar'
[0x4d49c]: b'emu64x\x00\x00'
[0x52148]: b'I\x00\x00\x00\x00\x00\x00\x00'
[0x7891c]: b'fopen\x00\x00\x00'
[0x7b3f4]: b' (\x00\x00\x00\x00\x00\x00'
[0x7e150]: b'/data/user/2'
[0xb634]: b'/system/bin/failsafe/su'
[0xba68]: b'sys.initd'
[0x169e4]: b'utime\x00\x00\x00'
指令: 0x1e284 (MOV X0, X8) => 复杂寄存器/内存操作
需要手动解密 : 0x1e288 b'arm64-v8a'
[0x1f5ec]: b'[Landroid/content/pm/Signature;'
[0x48578]: b'edxp.jar'
[0x4d4ac]: b'android/os/Build'
[0x52174]: b'version\x00'
[0x7b420]: b' NATIVEHELPER_HOOK_OPEN'
[0x7e1dc]: b'/data/user/3'
[0xb644]: b'/system/sd/xbin/su'
[0xba7c]: b'ro.build.selinux'
[0x16a04]: b'mkdir\x00\x00\x00'
[0x1f64c]: b'toByteArray'
[0x486b4]: b'/data/magisk/resetprop'
[0x4d4bc]: b'PRODUCT\x00'
[0x52184]: b'Ljava/lang/String;'
[0x7b44c]: b' NATIVEHELPER_HOOK_CLOSE'
[0x7e270]: b'/data/user/4'
[0xb654]: b'/su/xbin/su'
[0xba90]: b'service.adb.root'
[0x16a24]: b'open\x00\x00\x00\x00'
[0x1f660]: b'()[B\x00\x00\x00\x00'
指令: 0x48818 (ADD X0, X9,
需要手动解密 : 0x48824 b'/proc/self/attr/prev'
[0x4d588]: b'unknown\x00'
[0x7b478]: b' NATIVEHELPER_HOOK_READ'
[0x7e304]: b'/data/user/5'
[0xb664]: b'/su/bin/su'
[0x16a44]: b'close\x00\x00\x00'
指令: 0x1e464 (MOV X0, X8) => 复杂寄存器/内存操作
需要手动解密 : 0x1e468 b'%s/.%s\x00\x00'
[0x1f99c]: b'ro.build.version.sdk'
指令: 0x4887c (ADD X0, X8,
需要手动解密 : 0x48884 b':zygote:'
[0x4d59c]: b'Genymotion'
[0x7b4a4]: b' NATIVEHELPER_HOOK_WRITE'
[0x7e398]: b'/data/user/6'
[0xab9c]: b'FeatureGlobalInfo'
[0xb674]: b'/magisk/.core/bin/su'
[0x16a64]: b'unlink\x00\x00'
[0x1f9d0]: b'ro.build.version.preview_sdk'
[0x486f0]: b'/proc/self/mounts'
[0x4d5ac]: b'Andy\x00\x00\x00\x00'
[0x7b4c8]: b' )\x00\x00\x00\x00\x00\x00'
[0x7e42c]: b'/data/user/7'
[0xb684]: b'/system/usr/we-need-root/su'
[0x16a84]: b'stat\x00\x00\x00\x00'
[0x1f2b8]: b'%s\x00\x00\x00\x00\x00\x00'
[0x1fa84]: b'%s\x00\x00\x00\x00\x00\x00'
[0x48700]: b'r\x00\x00\x00\x00\x00\x00\x00'
[0x4d5bc]: b'MIT\x00\x00\x00\x00\x00'
[0x7b4f4]: b' ESP_HOOK_LIBOPENJDK'
[0x7e4c0]: b'/data/user/8'
[0xb694]: b'/system/xbin/su'
[0x16aa4]: b'time\x00\x00\x00\x00'
[0x1f224]: b'Ljava/lang/String;'
[0x48934]: b'android/bde/BdeEngineManager'
[0x4d5cc]: b'nox\x00\x00\x00\x00\x00'
[0x7b51c]: b' (\x00\x00\x00\x00\x00\x00'
[0x7e554]: b'/data/user/9'
[0xb6a4]: b'/system/etc/init.d/99SuperSUDaemon'
[0x16ac4]: b'snprintf'
[0x1fb34]: b'I\x00\x00\x00\x00\x00\x00\x00'
[0x4d5dc]: b'TiantianVM'
[0x7b548]: b' OPENJDK_HOOK_JVM_OPEN'
[0x7e5e8]: b'\x00\x00\x00\x00\x00\x00\x00\x00'
[0xb6b4]: b'/dev/com.koushikdutta.superuser.daemon'
[0x16ae4]: b'strchr\x00\x00'
[0x4d5ec]: b'iToolsAVM'
[0x7b574]: b' OPENJDK_HOOK_HANDLE_OPEN'
[0x7e684]: b'/\x00\x00\x00\x00\x00\x00\x00'
[0xb6c4]: b'/system/xbin/daemonsu'
[0x16b04]: b'strncmp\x00'
[0x1fdec]: b'/proc/self/maps'
[0x4d5fc]: b'Netease\x00'
[0x7b598]: b' )\x00\x00\x00\x00\x00\x00'
[0x7e72c]: b'/files/\x00'
[0xb6d4]: b'/system/lib/libxposed_art.so'
[0x16b24]: b'pthread_detach'
[0x1fe04]: b'/proc/%d/maps'
[0x4d60c]: b'android/os/Build'
[0x7b5bc]: b' ]\x00\x00\x00\x00\x00\x00'
[0x7e750]: b'/data/data'
[0xb6f0]: b'/system/lib64/libxposed_art.so'
[0x16b44]: b'pthread_self'
[0x1fe40]: b'r\x00\x00\x00\x00\x00\x00\x00'
[0x4d61c]: b'MANUFACTURER'
[0x7b740]: b'open\x00\x00\x00\x00'
[0x7f2ac]: b'/\x00\x00\x00\x00\x00\x00\x00'
[0xb700]: b'/system/xposed.prop'
[0x16b64]: b'opendir\x00'
指令: 0x1fe8c (MOV X0, X22) => 复杂寄存器/内存操作
需要手动解密 : 0x1fe90 b'r-xp\x00\x00\x00\x00'
[0x4d6e8]: b'generic\x00'
[0x7b7a0]: b'close\x00\x00\x00'
[0x7f354]: b'/databases/'
[0xb710]: b'/cache/recovery/xposed.zip'
[0x16b84]: b'readdir\x00'
指令: 0x1fea4 (MOV X0, X23) => 复杂寄存器/内存操作
需要手动解密 : 0x1fea8 r--p\x00\x00\x00\x00
[0x4d6fc]: b'generic_x86'
[0x7b7cc]: b'read\x00\x00\x00\x00'
[0x7f388]: b'/data/data'
[0xb720]: b'/system/framework/XposedBridge.jar'
[0x16ba4]: b'closedir'
[0x1ff68]: b'/proc/%d/cmdline'
[0x4d70c]: b'Andy\x00\x00\x00\x00'
[0x7b7f8]: b'write\x00\x00\x00'
[0x7fee4]: b'/\x00\x00\x00\x00\x00\x00\x00'
[0xb730]: b'/system/bin/app_process64_xposed'
[0x16bc4]: b'mmap\x00\x00\x00\x00'
[0x1ff8c]: b'r\x00\x00\x00\x00\x00\x00\x00'
[0x4d71c]: b'TTVM\x00\x00\x00\x00'
[0x7be70]: b'JVM_Open'
[0x7ff8c]: b'/shared_prefs/'
[0xb740]: b'/system/bin/app_process32_xposed'
[0x16be4]: b'munmap\x00\x00'
[0x200e4]: b'/proc/self/fd/%d'
[0x4d72c]: b'android/os/Build'
[0x7bed4]: b'__read_chk'
[0x7ffc0]: b'/data/data'
[0xb750]: b'/magisk/xposed/system/lib/libsigchain.so'
[0x16c04]: b'lseek\x00\x00\x00'
[0x4d73c]: b'BRAND\x00\x00\x00'
[0x7bf00]: b'__write_chk'
[0x80bb4]: b'/storage/emulated'
[0xb760]: b'/magisk/xposed/system/lib/libart.so'
[0x16c24]: b'fstat\x00\x00\x00'
[0x4d808]: b'generic\x00'
[0x7c174]: b'handleOpen'
[0x814ec]: b'/mnt/sdcard'
[0xb770]: b'/magisk/xposed/system/lib/libart-disassembler.so'
[0x16c44]: b'read\x00\x00\x00\x00'
[0x4d81c]: b'generic_x86'
[0x7c3e8]: b'__read_chk'
[0x815bc]: b'/storage/'
[0xb780]: b'/magisk/xposed/system/lib/libart-compiler.so'
[0x16c64]: b'select\x00\x00'
[0x4d82c]: b'Andy\x00\x00\x00\x00'
[0x7c414]: b'__write_chk'
[0x8168c]: b'/storage/emulated'
[0xb790]: b'/system/bin/app_process32_orig'
[0x16c84]: b'bsd_signal'
[0x4d83c]: b'ttVM_Hdragon'
[0x8181c]: b'/mnt/sdcard'
[0xb7a0]: b'/system/bin/app_process64_orig'
[0x16ca4]: b'fork\x00\x00\x00\x00'
[0x4d84c]: b'Droid4X\x00'
[0x818ec]: b'/storage/'
[0xb7b0]: b'/system/lib/libmemtrack_real.so'
[0x16cc4]: b'prctl\x00\x00\x00'
[0x4d85c]: b'nox\x00\x00\x00\x00\x00'
[0x80b58]: b'/storage/emulated'
[0xb7c0]: b'/system/lib64/libmemtrack_real.so'
[0x16ce4]: b'setrlimit'
[0x4d86c]: b'vbox86p\x00'
[0x80cf0]: b'/mnt/sdcard'
[0xb7d0]: b'/system/lib/libriru_edxp.so'
[0x16d04]: b'getppid\x00'
[0x4d87c]: b'generic_x86_64'
[0x80dc0]: b'/storage/'
[0xb7e0]: b'/system/lib64/libriru_edxp.so'
[0x16d24]: b'getpid\x00\x00'
[0x4d88c]: b'iToolsAVM'
[0x80e90]: b'/storage/emulated'
[0xb7f0]: b'/system/lib/libwhale.edxp.so'
[0x16d44]: b'waitpid\x00'
[0x4d89c]: b'emu64x\x00\x00'
[0x80fcc]: b'/mnt/sdcard'
[0xb800]: b'/system/lib64/libwhale.edxp.so'
[0x16d64]: b'kill\x00\x00\x00\x00'
[0x4d8ac]: b'emulator'
[0x81094]: b'/storage/'
[0xb810]: b'/system/framework/edxp.jar'
[0x16d84]: b'flock\x00\x00\x00'
[0x4d8bc]: b'android/os/Build'
[0x812d4]: b'/storage/sdcard1'
[0xb820]: b'/system\x00'
[0x16da4]: b'write\x00\x00\x00'
[0x4d8cc]: b'DEVICE\x00\x00'
[0x81348]: b'/storage/sdcard1'
[0xb83c]: b'/system/bin'
[0x16dc4]: b'execve\x00\x00'
[0x4d998]: b'sdk\x00\x00\x00\x00\x00'
[0x81bac]: b'/storage/sdcard1'
[0xb84c]: b'/system/sbin'
[0x16de4]: b'execv\x00\x00\x00'
[0x4d9ac]: b'google_sdk'
[0x82158]: b'.lock\x00\x00\x00'
[0xb85c]: b'/system/xbin'
[0x16e04]: b'execl\x00\x00\x00'
[0x4d9bc]: b'Droid4X\x00'
[0x82220]: b'.flock\x00\x00'
[0xb86c]: b'/vendor/bin'
[0x16e24]: b'sysconf\x00'
[0x4d9cc]: b'TiantianVM'
[0x822e8]: b'.so\x00\x00\x00\x00\x00'
[0xb87c]: b'/sbin\x00\x00\x00'
[0x16e44]: b'__system_property_get'
[0x4d9dc]: b'Andy\x00\x00\x00\x00'
[0x823b0]: b'.tmp\x00\x00\x00\x00'
[0xb88c]: b'/etc\x00\x00\x00\x00'
[0x16e64]: b'ftruncate'
[0x4d9ec]: b'Android SDK built for x86_64'
[0x82480]: b'.temp\x00\x00\x00'
[0x16e84]: b'gettid\x00\x00'
[0x4d9fc]: b'Android SDK built for x86'
[0x8255c]: b'.luac\x00\x00\x00'
[0x16ea4]: b'pread64\x00'
[0x4da0c]: b'iToolsAVM'
[0x8262c]: b'.lua\x00\x00\x00\x00'
[0x16ec4]: b'pwrite64'
[0x4da1c]: b'MuMu\x00\x00\x00\x00'
[0x826fc]: b'.png\x00\x00\x00\x00'
[0x16ee4]: b'pread\x00\x00\x00'
[0x4da2c]: b'sdk_gphone64'
[0x827cc]: b'.csb\x00\x00\x00\x00'
[0x16f04]: b'pwrite\x00\x00'
[0x4da3c]: b'android/os/Build'
[0x8289c]: b'.ttf\x00\x00\x00\x00'
[0x16708]: b'libc.so\x00'
[0x4da4c]: b'MODEL\x00\x00\x00'
[0x82964]: b'.jpg\x00\x00\x00\x00'
[0xa8dc]: b'FeatureLibcProtection'
[0x4db18]: b'goldfish'
[0x82a2c]: b'.manifest'
[0x4db2c]: b'vbox86\x00\x00'
[0x82af4]: b'.js\x00\x00\x00\x00\x00'
[0x4db3c]: b'nox\x00\x00\x00\x00\x00'
[0x82bbc]: b'.html\x00\x00\x00'
[0x4db4c]: b'ttVM_x86'
[0x82c84]: b'.css\x00\x00\x00\x00'
[0x4db5c]: b'android/os/Build'
[0x82d54]: b'-journal'
[0x4db6c]: b'HARDWARE'
[0x82e1c]: b'-shm\x00\x00\x00\x00'
[0x4dc38]: b'generic/sdk/generic'
[0x82ee4]: b'-wal\x00\x00\x00\x00'
[0x4dc4c]: b'generic_x86/sdk_x86/generic_x86'
[0x82fac]: b'bugle_db'
[0x4dc5c]: b'Andy\x00\x00\x00\x00'
[0x83b2c]: b'.xml\x00\x00\x00\x00'
[0x4dc6c]: b'ttVM_Hdragon'
[0x83b98]: b'.\x00\x00\x00\x00\x00\x00\x00'
[0x4dc7c]: b'generic_x86_64'
[0x83ca0]: b'.db\x00\x00\x00\x00\x00'
[0x4dc8c]: b'generic/google_sdk/generic'
[0x83d40]: b'.\x00\x00\x00\x00\x00\x00\x00'
[0x4dc9c]: b'vbox86p\x00'
[0x85f54]: b'libc.so\x00'
[0x4dcac]: b'generic/vbox86p/vbox86p'
[0x85f6c]: b'open\x00\x00\x00\x00'
[0x4dcbc]: b'google/sdk_gphone64'
[0x85f88]: b'close\x00\x00\x00'
[0x4dccc]: b'emulator'
[0x85fa4]: b'read\x00\x00\x00\x00'
[0x4dcdc]: b'android/os/Build'
[0x85fc0]: b'write\x00\x00\x00'
[0x4dcec]: b'FINGERPRINT'
[0x85fdc]: b'munmap\x00\x00'
[0xbc38]: b'FeatCheckEmulator'
[0x860ac]: b'pread64\x00'
[0x860c8]: b'pwrite64'
[0x860e4]: b'mmap64\x00\x00'
--- 正在查找范围 0xb3671 到 0xb3989 内的数据引用 ---
--- 查找结束 ---
[0xab88]: b'unknown\x00'
[0xacd4]: b'bdp.\x00\x00\x00\x00'
[0xad9c]: b'FeatureMetaData'
[0xb4b0]: b'/sbin/.magisk/'
[0xb8b0]: b'ro.build.version.release'
[0xbacc]: b'FeatCheckRoot'
[0xbb6c]: b'/etc/mumu-configs/device-prop-configs/mumu.config'
[0xc07c]: b'FeatureAntiMthook'
[0xc194]: b'b0f957fc8d26239fe1d7d0fd0851ef3dcf86b8c2'
[0xc3b0]: b'FeatureSharedPrefEncryption'
[0xc4ec]: b'<?xml\x00\x00\x00'
[0xcfd4]: b'\x00\x00\x00\x00\x00\x00\x00\x00'
[0x11a30]: b'%s %*s %*s %*s %*s %*s'
指令: 0x14654 (ADD X0, X8,
需要手动解密 : 0x1465c -> b'%s/.bdlock'
[0x16724]: b'_exit\x00\x00\x00'
[0x1ea4c]: b'\x00\x00\x00\x00\x00\x00\x00\x00'
[0x26f9c]: b'%s/.1\x00\x00\x00'
[0x2dbb0]: b'/proc/self/maps'
指令: 0x34fa4 (ADD X0, X9,
需要手动解密 : 0x34fac libandroid_runtime.so
指令: 0x47834 (MOV X0, X28) => 复杂寄存器/内存操作
需要手动解密 : 0x47838 %n%*s%n %n%*s%n %n%*s%n %n%*s%n %d %d
[0x47a30]: b' %n%*s%n %n%*s%n %n%*s%n %n%*s%n %d %d'
[0x4e450]: b'java/lang/Throwable'
指令: 0x4ed4c (ADD X0, X8,
需要手动解密 : 0x4ed50 android/app/ActivityThread
[0x4f488]: b'/proc/self/mem'
[0x4fdf0]: b'gdbserver'
[0x50cbc]: b'/proc/self/fd/%d'
[0x78364]: b'.db\x00\x00\x00\x00\x00'
[0x7c850]: b'/\x00\x00\x00\x00\x00\x00\x00'
[0xacf0]: b'stamp-cert-sha256'
[0xb4cc]: b'/sbin/.core/mirror'
[0xb8c4]: b'ro.build.version.incremental'
[0xbb88]: b'/data/local/cfg-gdaeg'
[0xc410]: b'FeatureFileEncryption'
[0xd044]: b'\x00\x00\x00\x00\x00\x00\x00\x00'
[0x11a4c]: b'/proc/self/maps'
指令: 0x14404 (MOV X0, X8) => 复杂寄存器/内存操作
需要手动解密 : 0x14408 n1\x00\x00\x00\x00\x00\x00
[0x16744]: b'exit\x00\x00\x00\x00'
[0x1d864]: b'assets/%s%d.i.dex'
[0x27000]: b'%s\x00\x00\x00\x00\x00\x00'
[0x2dbc0]: b'r\x00\x00\x00\x00\x00\x00\x00'
指令: 0x34fdc (ADD X0, X8,
需要手动解密 : 0x34fe0 __android_log_buf_write
[0x4774c]: b'/proc/mounts'
[0x4e474]: b'getStackTrace'
指令: 0x4eda8 (ADD X0, X8,
需要手动解密 : 0x4edac sPackageManager
[0x4f4a8]: b'/proc/self/pagemap'
[0x4fe00]: b'gdb\x00\x00\x00\x00\x00'
[0x50dd8]: b'bin/mt/apksignaturekillerplus/HookApplication'
[0x784b0]: b'-journal'
[0x79f38]: b'/proc/self/fd/%d'
[0x7c9a8]: b'/%s/%s/%s'
[0xaff4]: b'FeatLogProtection'
[0xb4dc]: b'/sbin/.core/img'
[0xb8d8]: b'ro.build.version.codename'
[0xbb98]: b'/data/local/cfg-yzi'
[0xc468]: b'FeatureSQLiteEncryption'
[0xd0b4]: b'\x00\x00\x00\x00\x00\x00\x00\x00'
[0x11a5c]: b'r\x00\x00\x00\x00\x00\x00\x00'
指令: 0x14418 (MOV X0, X8) => 复杂寄存器/内存操作
需要手动解密 : 0x1441cb'(Landroid/content/Context;Ljava/lang/String;Ljava/lang/String;Ljava/lang/String;I)V
[0x16764]: b'pthread_create'
[0x1d8ec]: b'assets/%s%d.jar'
[0x27044]: b'%s/1\x00\x00\x00\x00'
[0x2a3d0]: b'classes\x00'
[0x2dbfc]: b'r--p\x00\x00\x00\x00'
[0x4775c]: b'r\x00\x00\x00\x00\x00\x00\x00'
[0x4e484]: b'()[Ljava/lang/StackTraceElement;'
指令: 0x4edb8 (ADD X0, X8,
需要手动解密 : 0x4edbc Landroid/content/pm/IPackageManager;
[0x4f50c]: b'/proc/%d/mem'
[0x4fe10]: b'android_server'
[0x50e44]: b'libmthook.so'
[0x78244]: b'libsqlite.so'
[0x78728]: b'libsqlite.so'
[0x7a060]: b'/shared_prefs/'
[0x7cdbc]: b'/proc/self/fd/%d'
[0xb4ec]: b'/sbin/.core/db-0/magisk.db'
[0xb8ec]: b'ro.build.version.sdk'
[0xbba8]: b'/data/local/cfg-hzg'
[0xbf40]: b'FeatureNativeAntiDebug'
[0xd124]: b'\x00\x00\x00\x00\x00\x00\x00\x00'
指令: 0x14434 (MOV X0, X8) => 复杂寄存器/内存操作
需要手动解密 : 0x14438 b'n2\x00\x00\x00\x00\x00\x00'
[0x16784]: b'pthread_join'
[0x1d974]: b'assets/%s%d.d.jar'
[0x1ed80]: b'.\x00\x00\x00\x00\x00\x00\x00'
指令: 0x1ef7c (MOV X0, X22) => 复杂寄存器/内存操作
需要手动解密 : 0x1ef80 b'.\x00\x00\x00\x00\x00\x00\x00'
[0x27148]: b'/%d.jar\x00'
[0x2a3ec]: b'.dex\x00\x00\x00\x00'
[0x2dc0c]: b'%s %s %*s %*s %*s %s'
[0x478f0]: b'rw\x00\x00\x00\x00\x00\x00'
[0x4e4e4]: b'java/lang/StackTraceElement'
指令: 0x4ee60 (ADD X0, X8,
需要手动解密 : 0x4ee64 java/lang/reflect/Proxy
[0x4f540]: b'/proc/%d/pagemap'
[0x50eac]: b'/data/data/'
[0x52e88]: b'/proc/%d/cmdline'
[0x79a20]: b'SQLite\x00\x00'
[0x7a15c]: b'.\x00\x00\x00\x00\x00\x00\x00'
[0x7cee8]: b'android/os/Environment'
[0xb4fc]: b'/dev/.magisk.unblock'
[0xb900]: b'ro.product.model'
[0xbbb8]: b'/data/local/cfg-znz'
[0xbd74]: b'FeatCheckPmsHook'
[0xbe10]: b'FeatureMemoryChecker'
指令: 0x14448 (MOV X0, X8) => 复杂寄存器/内存操作
需要手动解密 : 0x1444c b'(Landroid/content/Context;)V'
[0x167a4]: b'memcpy\x00\x00'
[0x1da4c]: b'%s/lib\x00\x00'
[0x1ed9c]: b'..\x00\x00\x00\x00\x00\x00'
指令: 0x1ef94 (MOV X0, X23) => 复杂寄存器/内存操作
需要手动解密 : 0x1ef98 b'..\x00\x00\x00\x00\x00\x00'
指令: 0x271ac (MOV X0, X28) => 复杂寄存器/内存操作
需要手动解密 : 0x271b0 b'/%d.odex'
指令: 0x29ae0 (MOV X0, X24) => 复杂寄存器/内存操作
需要手动解密 : 0x29ae4 b'META-INF/'
[0x2dc1c]: b'r-xp\x00\x00\x00\x00'
[0x47af4]: b'1\x00\x00\x00\x00\x00\x00\x00'
[0x4e50c]: b'toString'
[0x50a00]: b'android/os/Debug'
[0x50fc0]: b'/data/user/0'
[0x78260]: b'\x00\x00\x00\x00\x00\x00\x00\x00'
[0x7876c]: b'\x00\x00\x00\x00\x00\x00\x00\x00'
[0x7a224]: b'.xml\x00\x00\x00\x00'
[0x7cf10]: b'getExternalStorageDirectory'
[0xb518]: b'/sbin/magiskinit'
[0xb914]: b'ro.product.manufacturer'
[0xbbc8]: b'/data/local/cfg-ndi'
指令: 0x14464 (MOV X0, X8) => 复杂寄存器/内存操作
需要手动解密 : 0x14468 b'n3\x00\x00\x00\x00\x00\x00'
[0x167c4]: b'malloc\x00\x00'
[0x1dbb0]: b'/.%s/lib'
[0x1ee3c]: b'/\x00\x00\x00\x00\x00\x00\x00'
指令: 0x1ef5c (MOV X0, X24) => 复杂寄存器/内存操作
需要手动解密 : 0x1ef60 b'/\x00\x00\x00\x00\x00\x00\x00'
[0x27530]: b'android/os/Build'
[0x29b00]: b'.MF\x00\x00\x00\x00\x00'
[0x47b04]: b'0\x00\x00\x00\x00\x00\x00\x00'
[0x4e51c]: b'()Ljava/lang/String;'
[0x50a24]: b'isDebuggerConnected'
[0x513dc]: b'android/app/ActivityThread'
[0x7b014]: b'open\x00\x00\x00\x00'
传播安全知识、拓宽行业人脉——看雪讲师团队等你加入!
最后于 2025-11-19 19:38
被npc0vo编辑
,原因: