网址:aHR0cHM6Ly95cC4xMjBhc2suY29tL3NlYXJjaC81LTI4My5odG1s
视频教程:视频
打开F12抓包观察
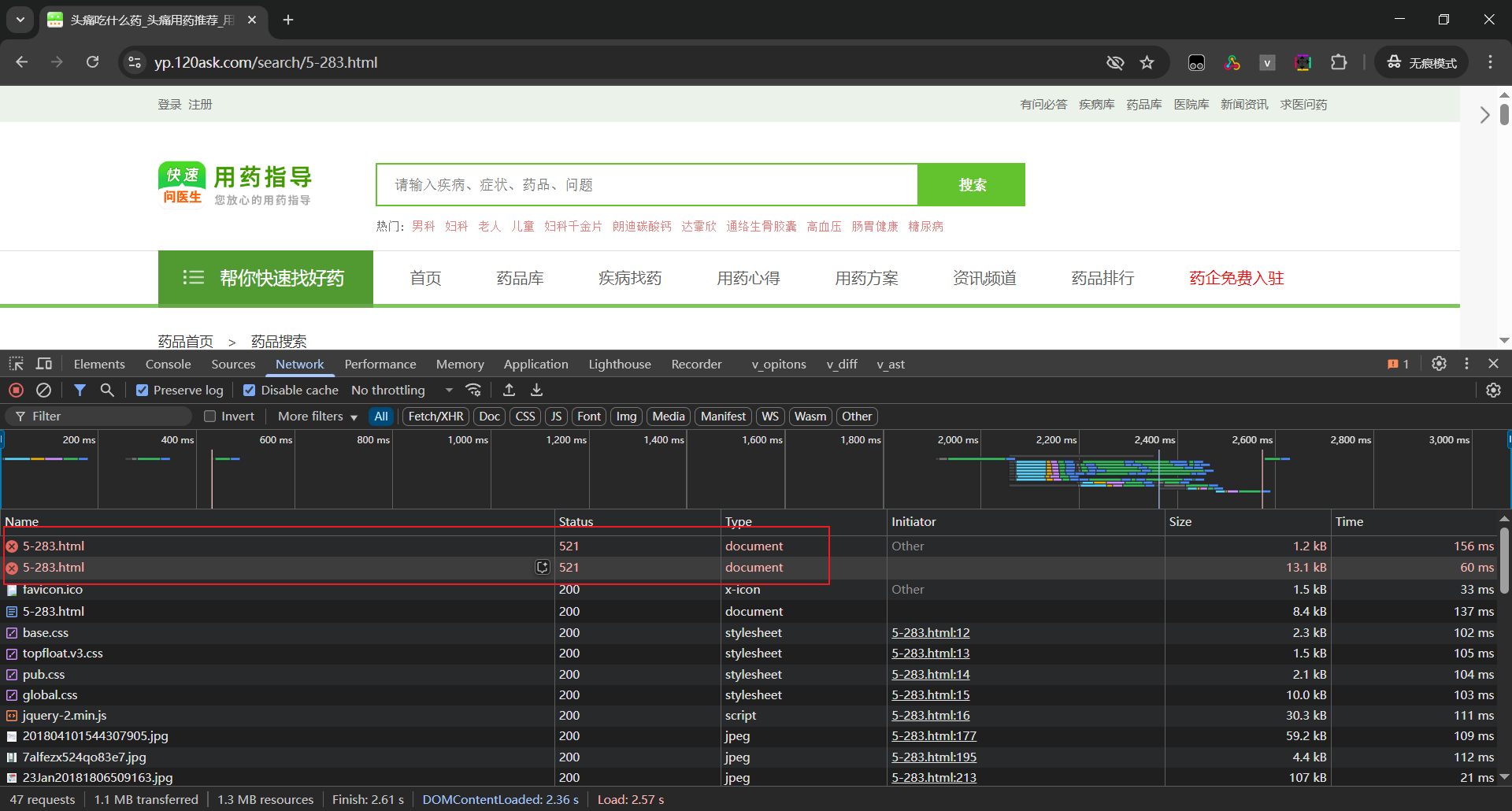
加速乐经典两次521,由于页面已经加载成功,两次521的请求响应看不到,清除cookie再下个script断点继续观察。
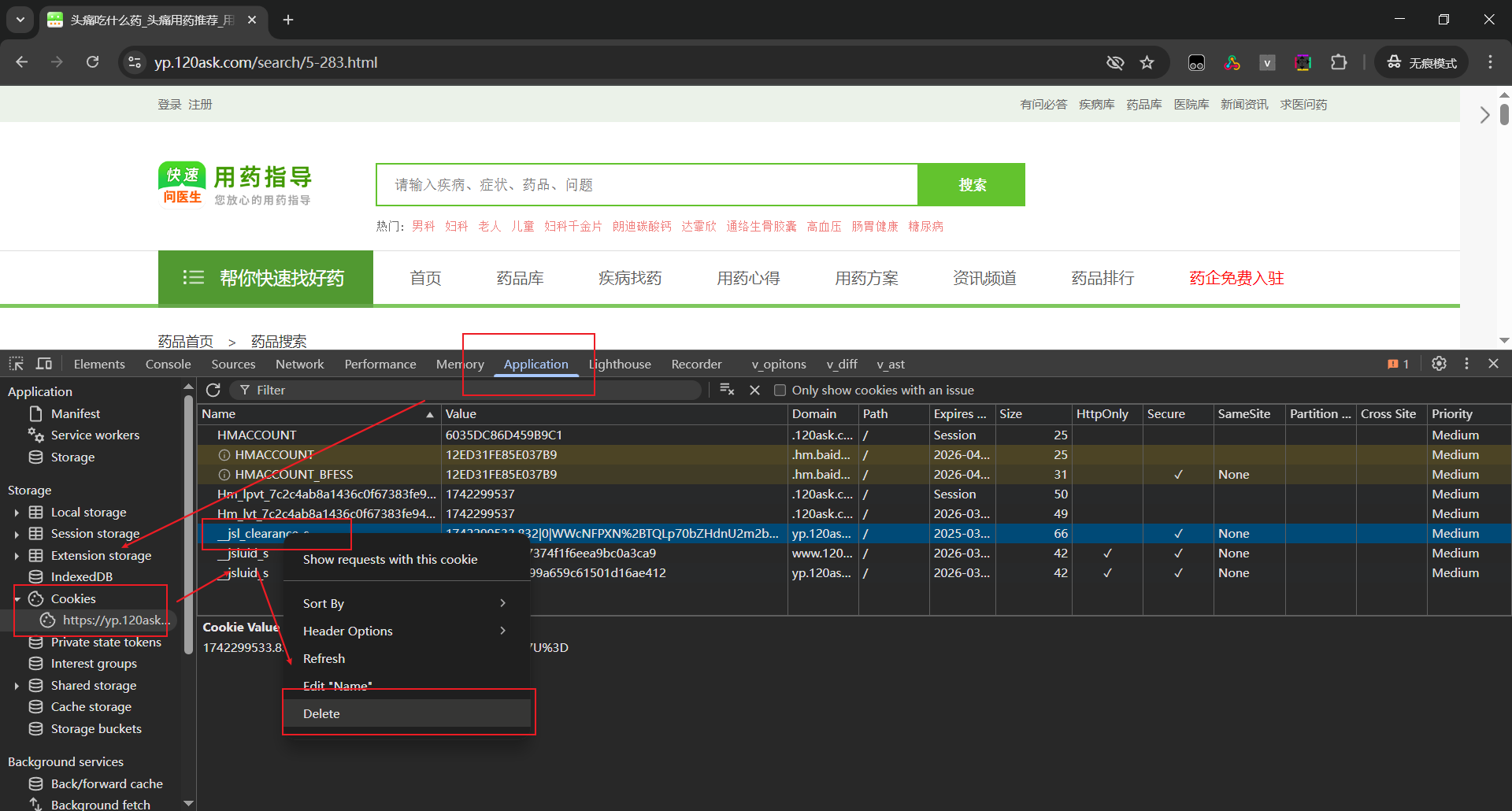
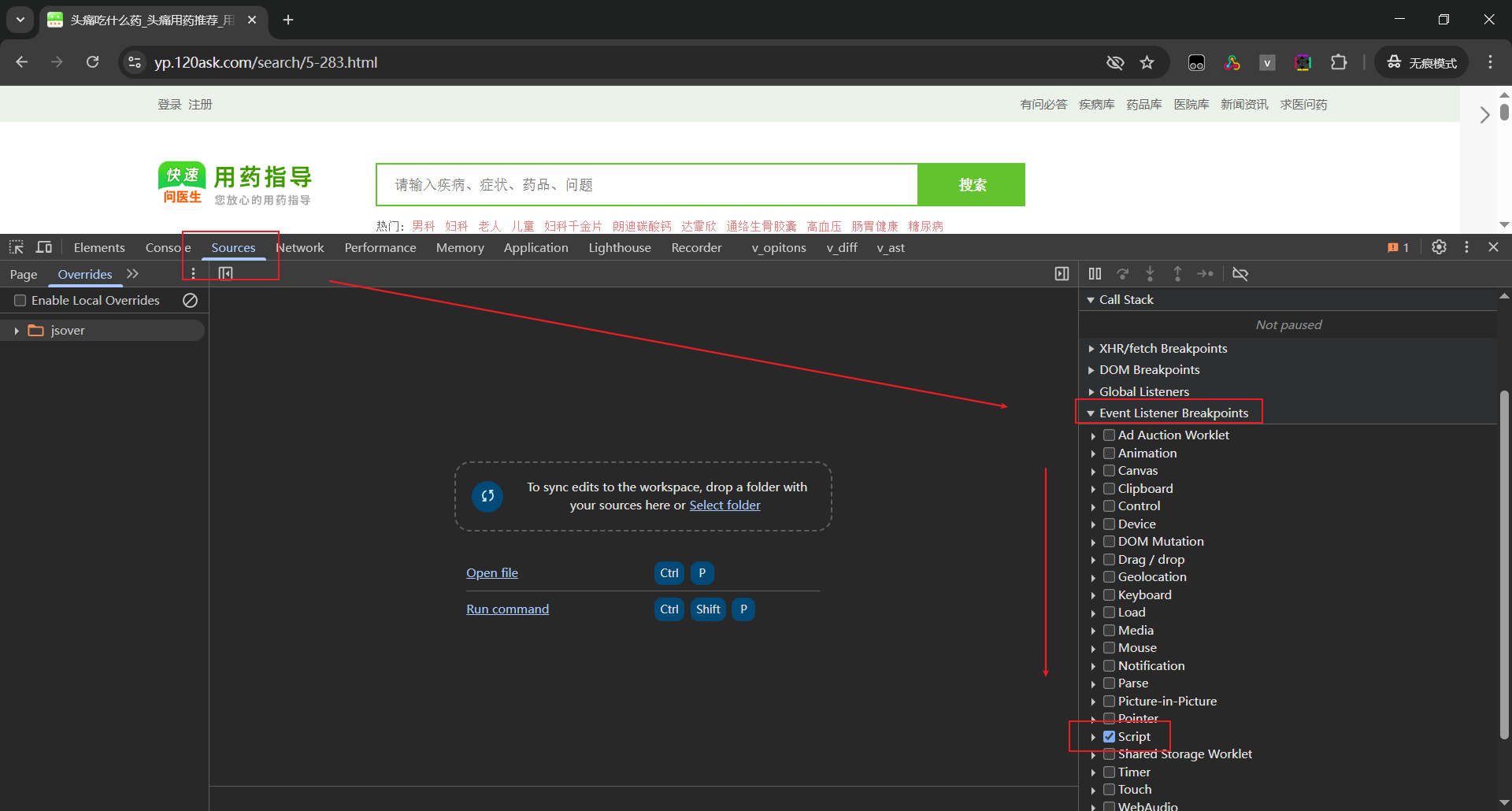
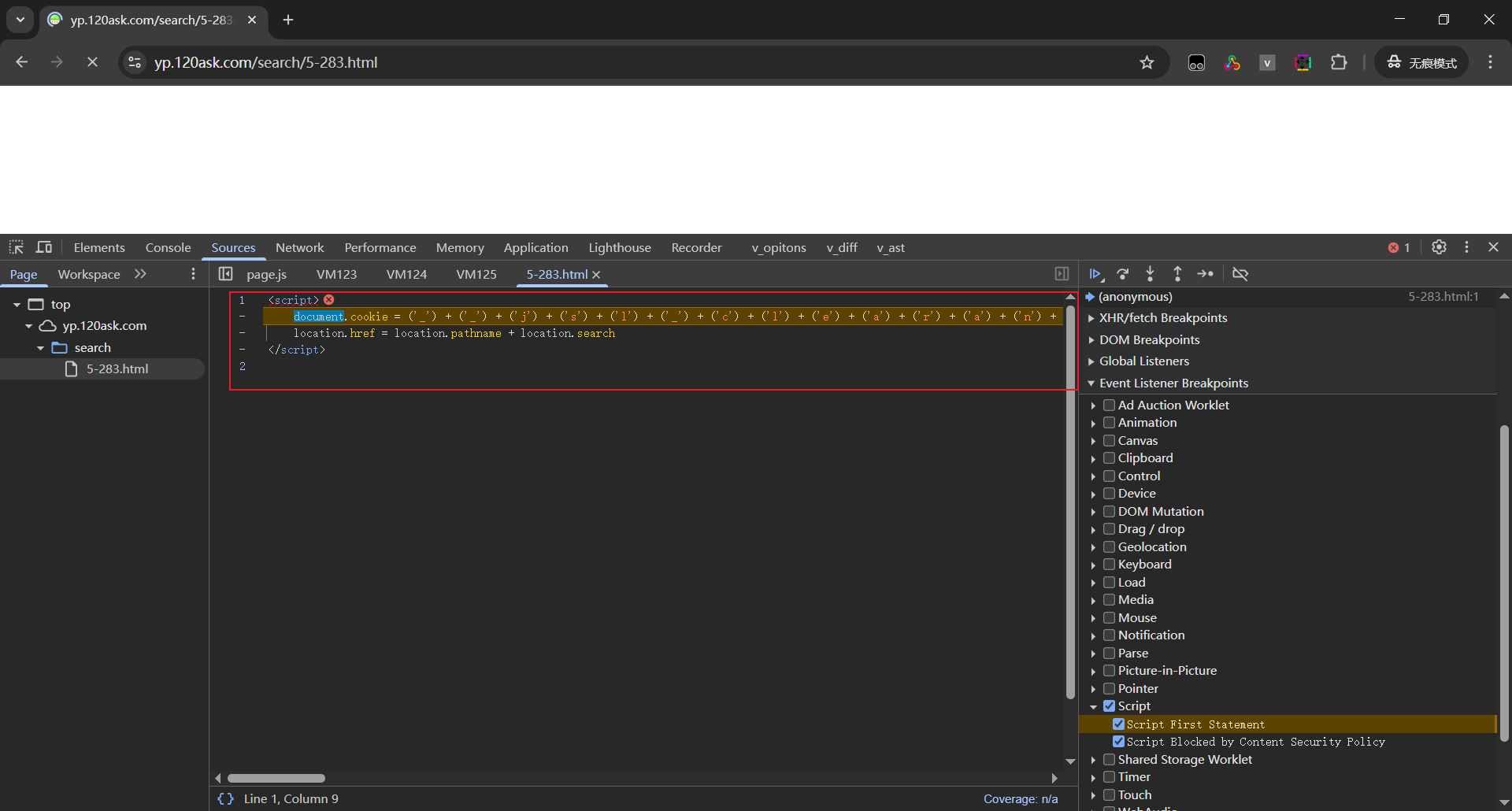
拿出来看看。
简单,直接执行即可拿到第一次的cookie。
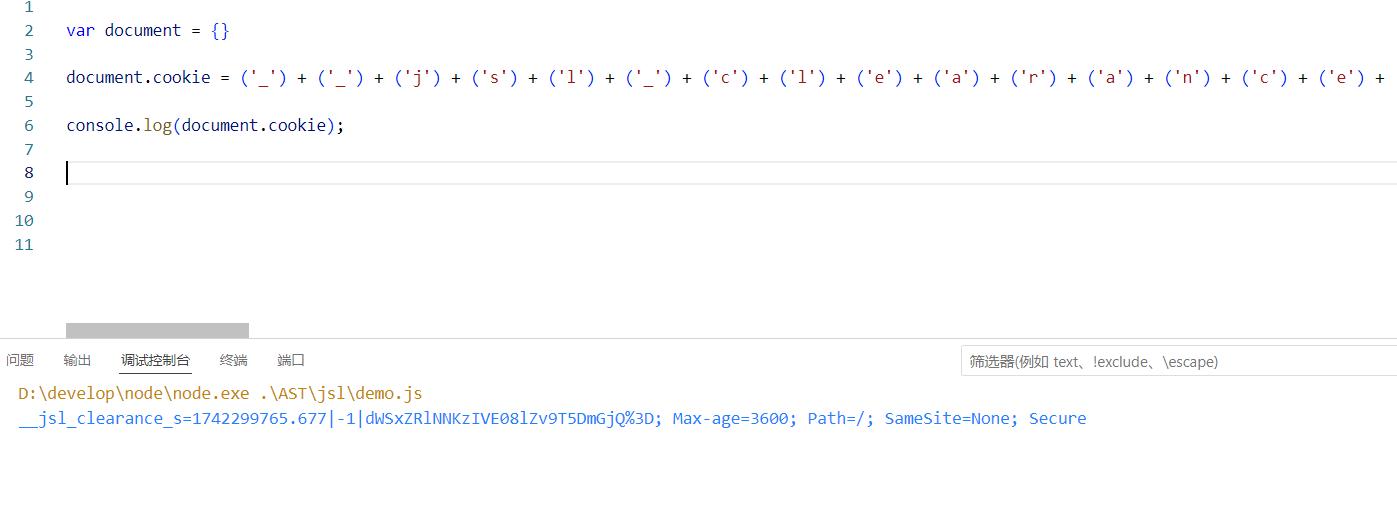
继续放行,直到断住第二次521
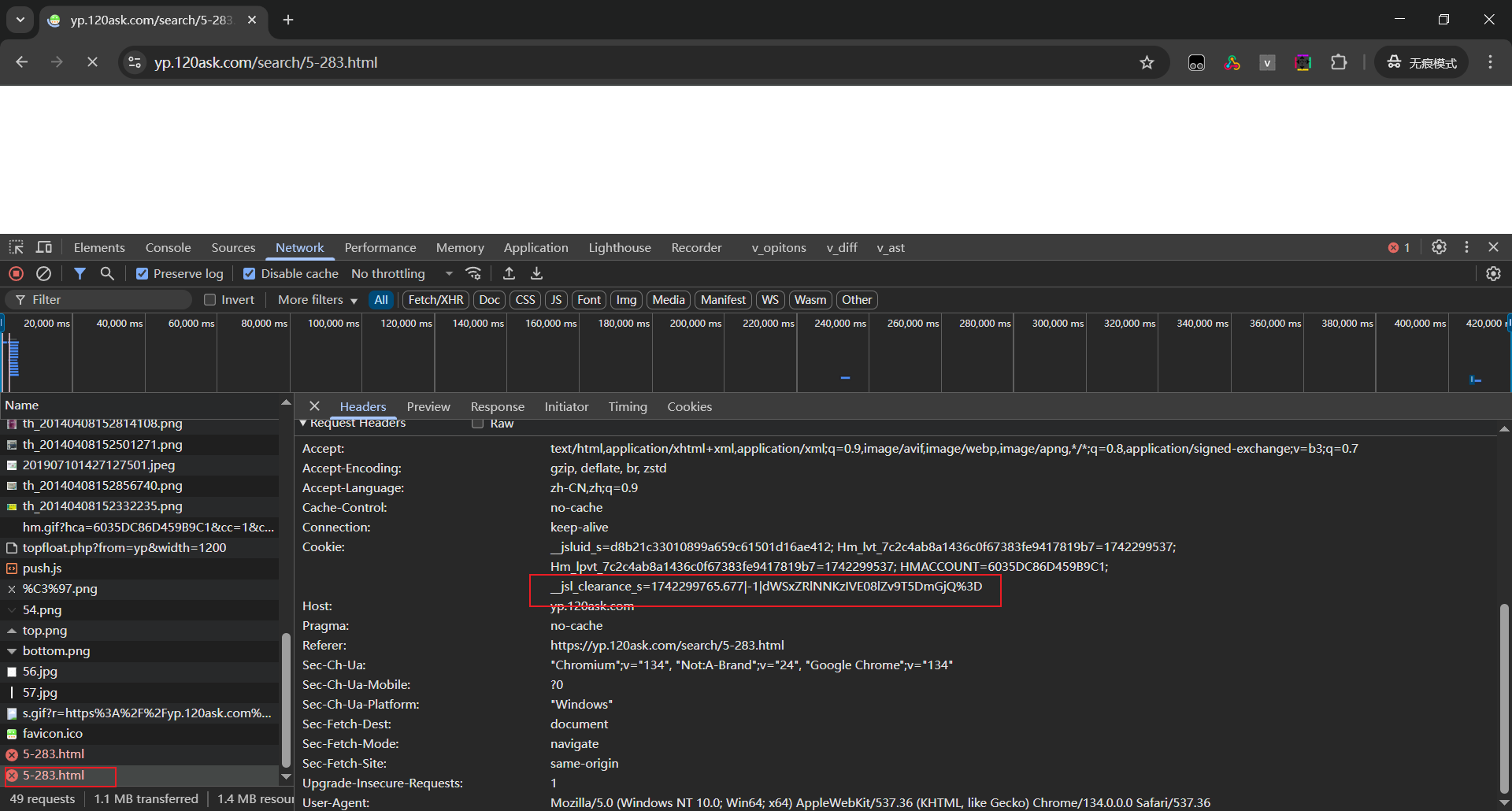
再观察本次请求头特征,携带的cookie正是第一次521生成的cookie
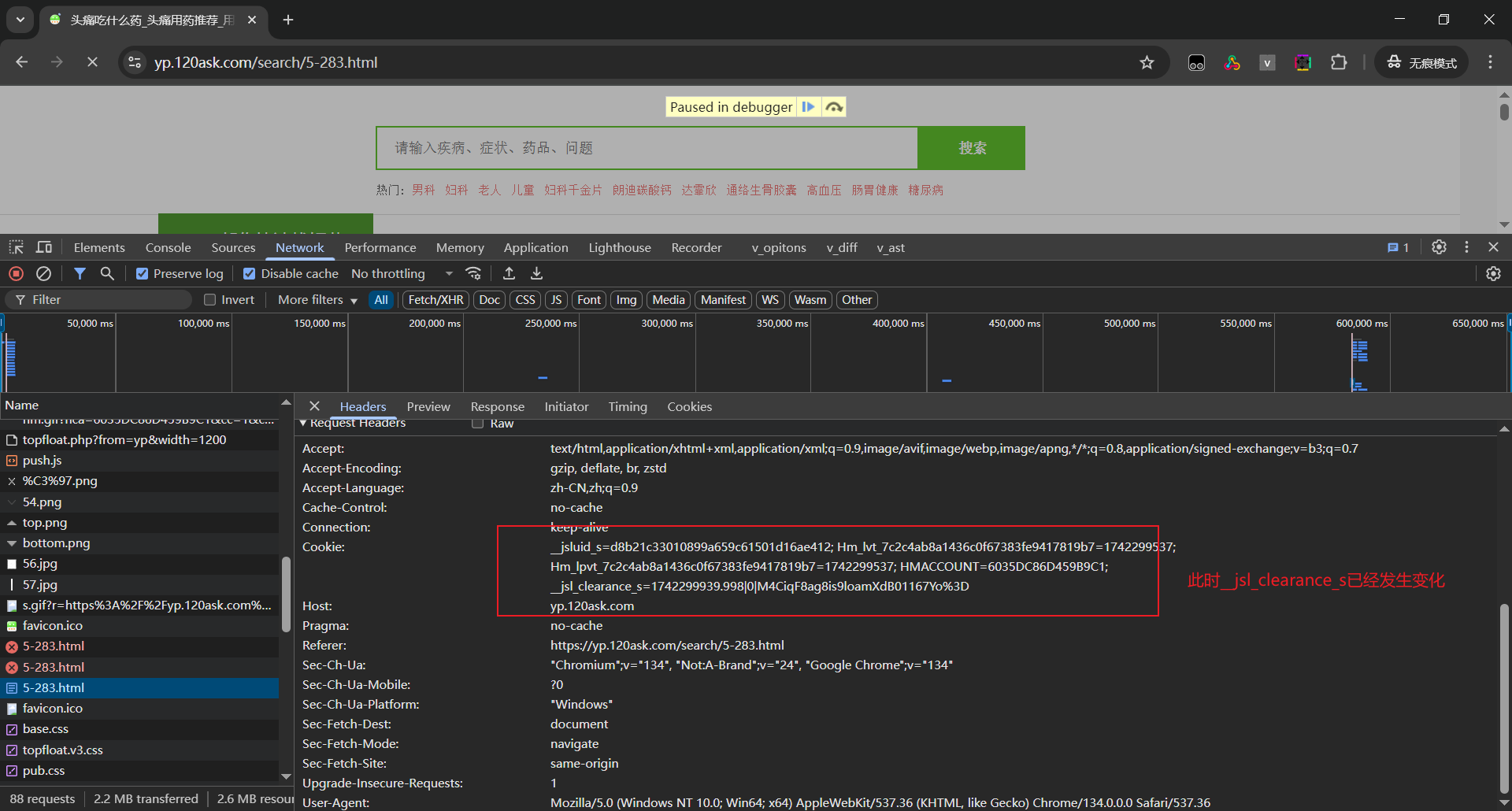
继续放行,页面加载成功,发现__jsl_clearance_s值已经发生变化
整体流程如下:
第一次521的cookie值很容易获取,执行js即可。
第二次521的js需要逆向分析
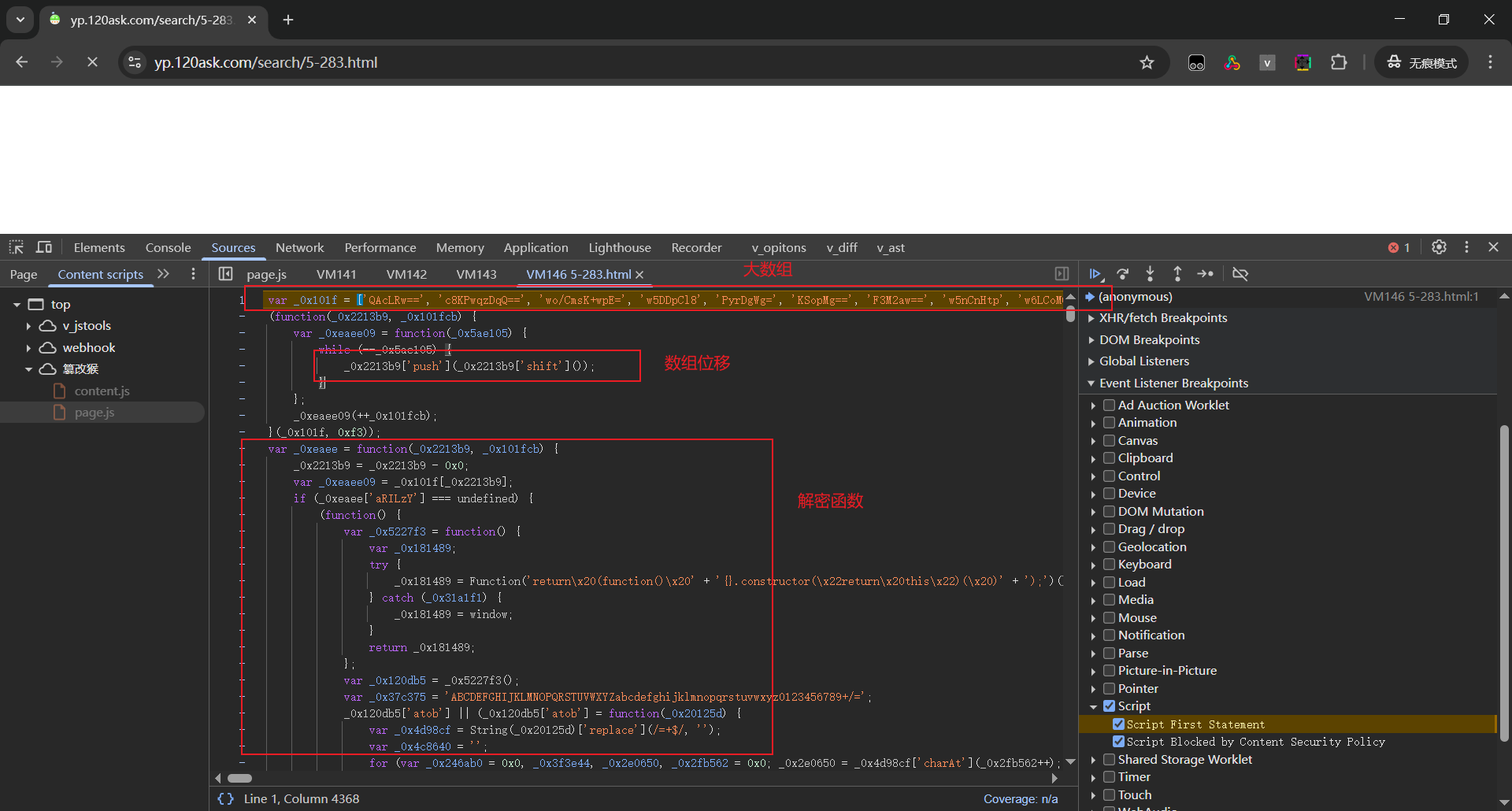
观察代码发现OB混淆三个特征(大数组、数组位移、解密函数)。
看到一个OB混淆,正好最近在学习AST,拿来还原练手。完整解混淆流程在:视频
解混淆后观察代码结构:

2个大方法,调用了go方法,传入了一个对象,继续分析go方法

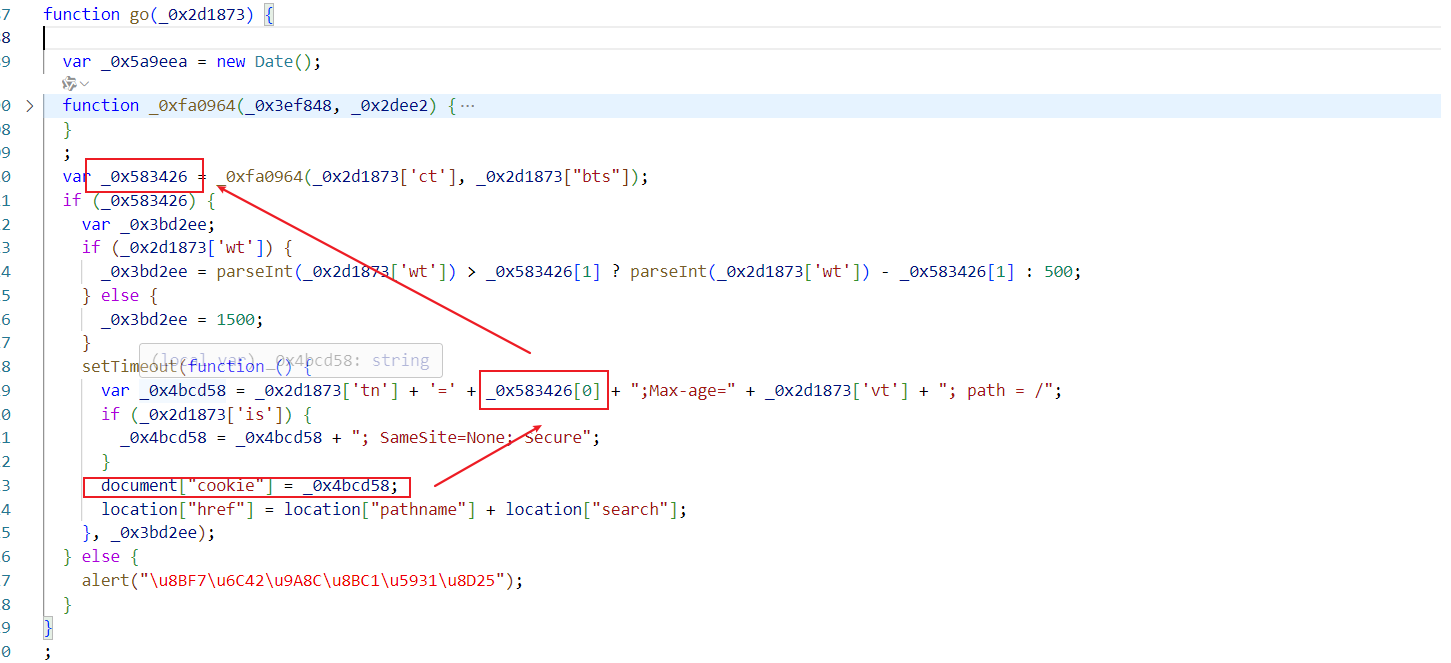
cookie来自于_0x4bcd58,_0x4bcd58来自于 _0x583426[0],_0x583426[0]来自于_0x583426,所以下面代码可以全部干掉
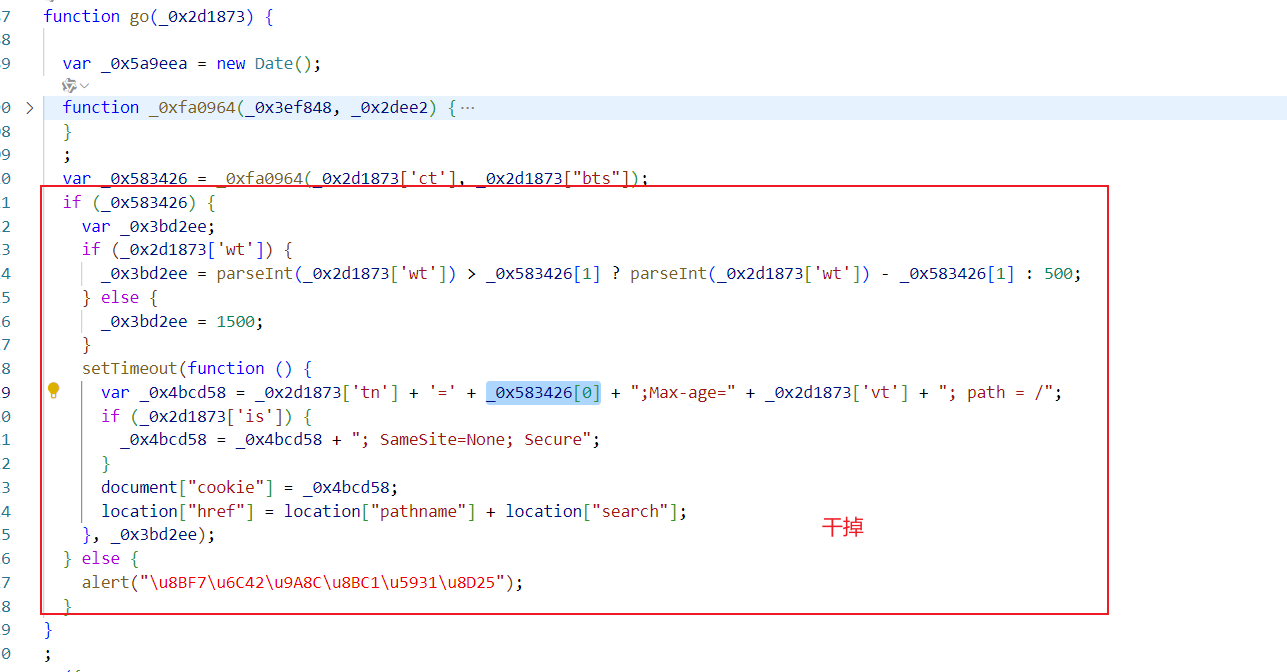
此时目标就是看_0x583426的逻辑了,精简后的go方法代码如下。
debug看看。

大致分析如上,最终代码如下:
注意这里去掉了hash方法,因为每次返回的js不一样,其本质算法就是拿出当前这次js的参数里面的ha值,代表对应的哈希算法,经过运算比对处理后生成新的__jsl_clearance_s,至此流程全部结束。
没毛病,完成
document.cookie = ('_') + ('_') + ('j') + ('s') + ('l') + ('_') + ('c') + ('l') + ('e') + ('a') + ('r') + ('a') + ('n') + ('c') + ('e') + ('_') + ('s') + ('=') + ((+true) + '') + (1 + 6 + '') + (1 + 3 + '') + (-~1 + '') + (0 + 1 + 0 + 1 + '') + (1 + [0] - (1) + '') + ([3] * (3) + '') + (9 - 1 * 2 + '') + ((1 + [2]) / [2] + '') + (([2] + 0 >> 2) + '') + ('.') + (-~[5] + '') + (-~[6] + '') + (7 + '') + ('|') + ('-') + ((+true) + '') + ('|') + ('d') + ('W') + ('S') + ('x') + ('Z') + ('R') + ('l') + ('N') + ('N') + ('K') + ('z') + ('I') + ('V') + ('E') + (~~[] + '') + ((2 << 2) + '') + ('l') + ('Z') + ('v') + (1 + 8 + '') + ('T') + (5 + '') + ('D') + ('m') + ('G') + ('j') + ('Q') + ('%') + ((1 + [2] >> 2) + '') + ('D') + (';') + (' ') + ('M') + ('a') + ('x') + ('-') + ('a') + ('g') + ('e') + ('=') + (1 + 2 + '') + ([2] * (3) + '') + ((+[]) + '') + (~~[] + '') + (';') + (' ') + ('P') + ('a') + ('t') + ('h') + ('=') + ('/') + (';') + (' ') + ('S') + ('a') + ('m') + ('e') + ('S') + ('i') + ('t') + ('e') + ('=') + ('N') + ('o') + ('n') + ('e') + (';') + (' ') + ('S') + ('e') + ('c') + ('u') + ('r') + ('e');
location.href = location.pathname + location.search
document.cookie = ('_') + ('_') + ('j') + ('s') + ('l') + ('_') + ('c') + ('l') + ('e') + ('a') + ('r') + ('a') + ('n') + ('c') + ('e') + ('_') + ('s') + ('=') + ((+true) + '') + (1 + 6 + '') + (1 + 3 + '') + (-~1 + '') + (0 + 1 + 0 + 1 + '') + (1 + [0] - (1) + '') + ([3] * (3) + '') + (9 - 1 * 2 + '') + ((1 + [2]) / [2] + '') + (([2] + 0 >> 2) + '') + ('.') + (-~[5] + '') + (-~[6] + '') + (7 + '') + ('|') + ('-') + ((+true) + '') + ('|') + ('d') + ('W') + ('S') + ('x') + ('Z') + ('R') + ('l') + ('N') + ('N') + ('K') + ('z') + ('I') + ('V') + ('E') + (~~[] + '') + ((2 << 2) + '') + ('l') + ('Z') + ('v') + (1 + 8 + '') + ('T') + (5 + '') + ('D') + ('m') + ('G') + ('j') + ('Q') + ('%') + ((1 + [2] >> 2) + '') + ('D') + (';') + (' ') + ('M') + ('a') + ('x') + ('-') + ('a') + ('g') + ('e') + ('=') + (1 + 2 + '') + ([2] * (3) + '') + ((+[]) + '') + (~~[] + '') + (';') + (' ') + ('P') + ('a') + ('t') + ('h') + ('=') + ('/') + (';') + (' ') + ('S') + ('a') + ('m') + ('e') + ('S') + ('i') + ('t') + ('e') + ('=') + ('N') + ('o') + ('n') + ('e') + (';') + (' ') + ('S') + ('e') + ('c') + ('u') + ('r') + ('e');
location.href = location.pathname + location.search
function go(_0x2d1873) {
var _0x5a9eea = new Date();
function _0xfa0964(_0x3ef848, _0x2dee2) {
var _0x1ed308 = _0x2d1873["chars"]["length"];
for (var _0x56d891 = 0; _0x56d891 < _0x1ed308; _0x56d891++) {
for (var _0x479e66 = 0; _0x479e66 < _0x1ed308; _0x479e66++) {
if ("VhzfI" !== "FDcqf") {
var _0xeeecec = _0x2dee2[0] + _0x2d1873["chars"]["substr"](_0x56d891, 1) + _0x2d1873["chars"]["substr"](_0x479e66, 1) + _0x2dee2[1];
if (hash(_0xeeecec) == _0x3ef848) {
if ("NaMJk" === "NaMJk") {
return [_0xeeecec, new Date() - _0x5a9eea];
} else {
blks[_0x56d891] = 0;
}
}
} else {
return !![];
}
}
}
}
;
var _0x583426 = _0xfa0964(_0x2d1873['ct'], _0x2d1873["bts"]);
console.log(_0x583426);
}
function go(_0x2d1873) {
var _0x5a9eea = new Date();
function _0xfa0964(_0x3ef848, _0x2dee2) {
var _0x1ed308 = _0x2d1873["chars"]["length"];
for (var _0x56d891 = 0; _0x56d891 < _0x1ed308; _0x56d891++) {
for (var _0x479e66 = 0; _0x479e66 < _0x1ed308; _0x479e66++) {
if ("VhzfI" !== "FDcqf") {
var _0xeeecec = _0x2dee2[0] + _0x2d1873["chars"]["substr"](_0x56d891, 1) + _0x2d1873["chars"]["substr"](_0x479e66, 1) + _0x2dee2[1];
if (hash(_0xeeecec) == _0x3ef848) {
if ("NaMJk" === "NaMJk") {
return [_0xeeecec, new Date() - _0x5a9eea];
} else {
blks[_0x56d891] = 0;
}
}
} else {
return !![];
}
}
}
}
;
var _0x583426 = _0xfa0964(_0x2d1873['ct'], _0x2d1873["bts"]);
console.log(_0x583426);
}
var CryptoJS = require('crypto-js')
function dynamicHash(algorithm, data) {
try {
// 根据算法名称选择对应的哈希函数
const hashFunctions = {
'md5': CryptoJS.MD5,
'sha1': CryptoJS.SHA1,
'sha224': CryptoJS.SHA224,
'sha256': CryptoJS.SHA256,
'sha384': CryptoJS.SHA384,
'sha512': CryptoJS.SHA512,
'sha3': CryptoJS.SHA3
};
if (!hashFunctions[algorithm]) {
throw new Error(`Unsupported algorithm: ${algorithm}`);
}
// 计算哈希值
const hash = hashFunctions[algorithm](data);
return hash.toString(CryptoJS.enc.Hex); // 返回十六进制字符串
} catch (error) {
return `Error: ${error.message}`;
}
}
function getCookie(_0x52e87e) {
_0x52e87e = JSON.parse(_0x52e87e);
console.log(_0x52e87e);
var _0x171118 = new Date();
function _0x18b9db(_0x3a9f8b, _0x28ec7f) {
var _0x15f5ed = _0x52e87e["chars"]["length"];
for (var _0x4184d5 = 0; _0x4184d5 < _0x15f5ed; _0x4184d5++) {
for (var _0x19da6b = 0; _0x19da6b < _0x15f5ed; _0x19da6b++) {
var _0x44455a = _0x28ec7f[0] + _0x52e87e["chars"]["substr"](_0x4184d5, 1) + _0x52e87e["chars"]["substr"](_0x19da6b, 1) + _0x28ec7f[1];
if (dynamicHash(_0x52e87e['ha'],_0x44455a) == _0x3a9f8b) {
return [_0x44455a, new Date() - _0x171118];
}
}
}
}
var _0x41c42e = _0x18b9db(_0x52e87e['ct'], _0x52e87e["bts"]);
console.log(_0x41c42e[0]);
return _0x41c42e[0];
}
param = {
"bts": ["1741572280.105|0|muv", "sjo3nn%2FimqQAhNp9X1aCuY%3D"],
"chars": "TqPahdOXDzvVxEzQfGHK5v",
"ct": "d38f1d26d274ebfb77ae39fda3893f0611b8256716fa6ce1a11a1bba7feaedcf",
"ha": "sha256",
"is": true,
"tn": "__jsl_clearance_s",
"vt": "3600",
"wt": "1500"
}
param1 = {"bts":["1741586083.055|0|8CI","B7T2GJJz%2FcUdeHFkRe6pg3bg%3D"],"chars":"YSmMypDsqQ2ohC%jibqXLT","ct":"460ea567c075a1ae6961688fdfb94b90ad348834","ha":"sha1","is":true,"tn":"__jsl_clearance_s","vt":"3600","wt":"1500"}
// getCookie(param1)
getCookie('{"bts":["1741586083.055|0|8CI","B7T2GJJz%2FcUdeHFkRe6pg3bg%3D"],"chars":"YSmMypDsqQ2ohC%jibqXLT","ct":"460ea567c075a1ae6961688fdfb94b90ad348834","ha":"sha1","is":true,"tn":"__jsl_clearance_s","vt":"3600","wt":"1500"}')
var CryptoJS = require('crypto-js')
function dynamicHash(algorithm, data) {
[培训]Windows内核深度攻防:从Hook技术到Rootkit实战!