基本是参照这个写的:etw_HOOK
这个是用C++写的,对C++不是很精通的人可能看着很难读懂,所以我用纯C代码复刻了一下。
1.什么是ETWHOOK?
简单的说就是在有PatchGurad的windows系统上SSDT hook的一种替代方案
2.ETWHOOK实现步骤
(1).替换HalpPrivatDispatchTable(可以通过MmGetSystemRoutineAddress函数获取)表中的的HalColleePmcCounts函数指针为自己的代理函数,代理函数的功能是在堆栈中寻找系统调用的目标内核函数指针并且在找到的时候替换它;
(2).开启Windows的ETW功能,并且经过一系列的设置使得系统调用时能进入HalColleePmcCounts函数(经过第一步的操作之后HalColleePmcCounts已经被替换成自己的代理函数了);
3.代码
(1).HalColleePmcCounts代理函数的实现:
(2).最麻烦的是开启ETW功能
(3).开启ETW功能分支功能PerformatsCounts计数功能
4.具体原理
WINDOWS的.data节一般是存放可以变的全局变量的,所谓的偷指针就是修改.data节区的指针。
而在这里,最好玩的是HalPrivateDispatchTable,这个是windows 的ntoskenl.exe为了方便使用HAL的导出函数,把他们存放在统一的地方。而HAL,用到的地方肯定很多,ETW 正是如此。
看一下系统调用ETW的调用路径。
这里其实可以看到,call rax 其实就是正常的系统调用,而再进入ETW系统调用之前,他把原始的系统调用存放在了栈上,这就导致我们拦截到ETW的时候,可以修改栈上的位置,来进行HOOK Syscall。
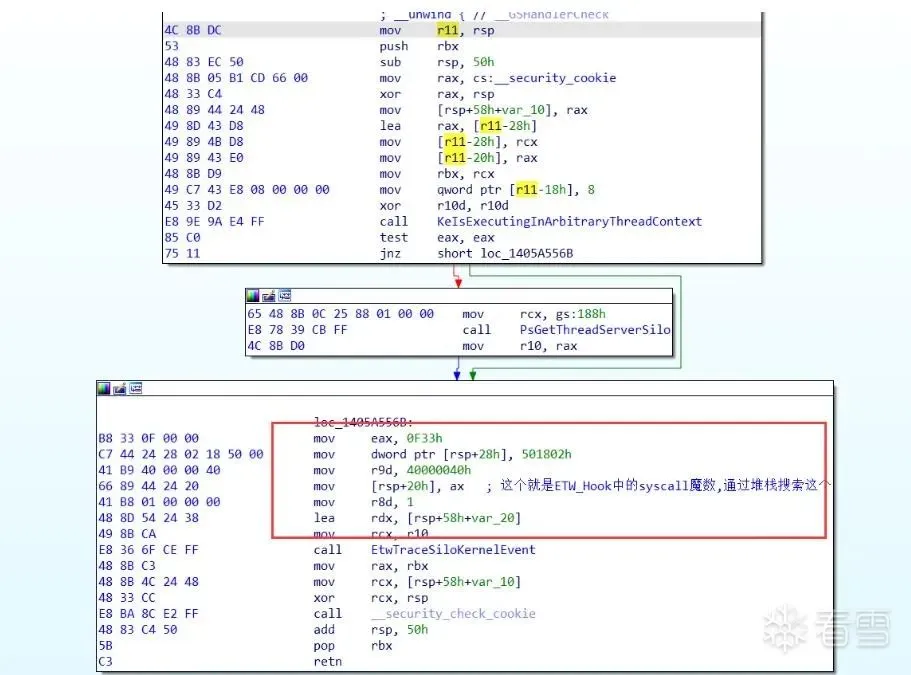
如果说之前无法定位,现在可以通过这个栈上面的magic number来定位系统调用的目标函数的地址,从而替换了。
继续跟到EtwTraceSiloKernelEvent里面,可以发现,无论参数怎么样,这个函数调用了EtwpLogKernelEvent。继续跟踪EtwpLogKernelEvent会发现EtwpLogKernelEvent会调用EtwpReserveWithPmcCounters。
而EtwpReserveWithPmcCounters就是这次事件的主角,关键部分代码为:
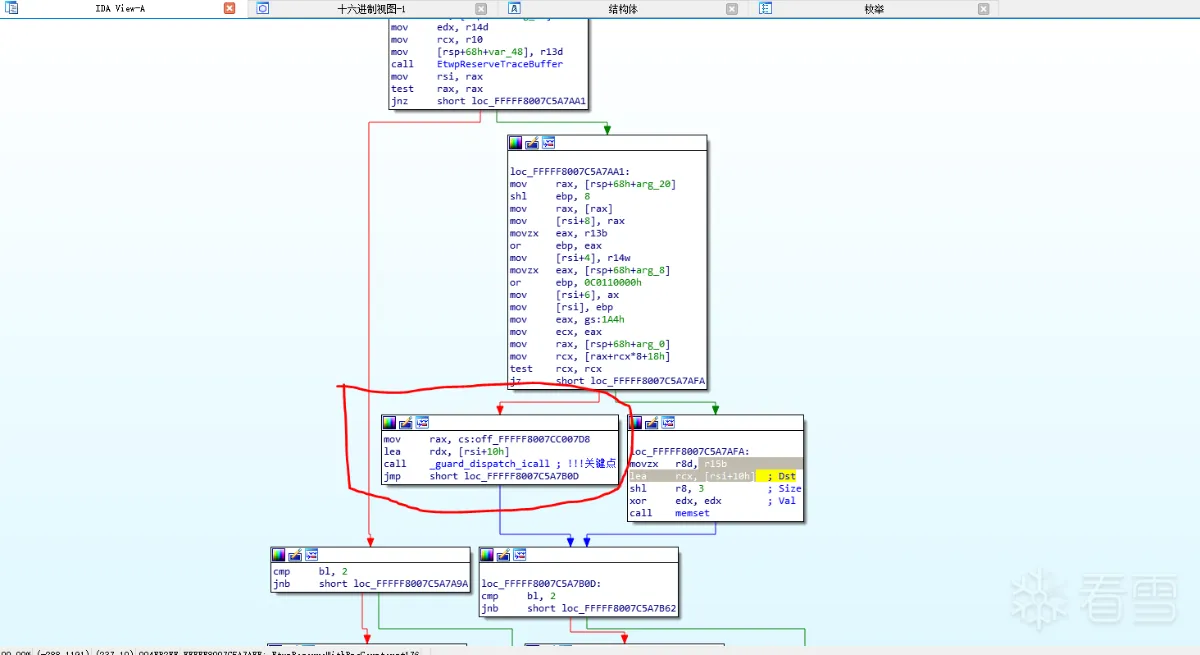
图中红圈中的地方就是EtwpReserveWithPmcCounters通过CFG保护的方式调用HalPrivateDispatchTable表中的HalCollectPmcCounters。
我们替换HalPrivateDispatchTable表中的HalCollectPmcCounters函数指针为我们自己的函数,在我们自己的函数里就可以在栈上查找并替换系统调用的目标函数从而达到HOOk的目的。
最后一点疑问:PG只要监控HalPrivateDispatchTable表就能修复这个漏洞,但貌似知道现在这个漏洞仍然可用。
VOID ProxyHalPrivateDispatchTable(PVOID Context, ULONGLONG TraceBuff)
{
USHORT Magic = 0xf33;\\系统调用在栈上的关键字1
ULONG Signate = 0x501802;\\系统调用在栈上的关键字2
PULONG RspPos = _AddressOfReturnAddress();
PULONG RspLimit = __readgsqword(0x1a8);
ULONG64 KiSystemServiceRepeat = HookInfo->KiSystemServiceRepeat;
if (KeGetCurrentIrql() <= DISPATCH_LEVEL)
{
if (ExGetPreviousMode() == KernelMode)return;
if (!KiSystemServiceRepeat)
{
DbgPrint("failed to find KiSystemServiceRepeat\r\n");
return;
}
while (RspPos <= RspLimit)
{
if (*((PUSHORT)(RspPos)) == Magic)
{
if (RspPos[2] == Signate)
{
for (; (ULONG64)RspPos <= (ULONG64)RspLimit; ++RspPos)
{
if ((*((PULONG64)(RspPos)) >= (KiSystemServiceRepeat & 0XFFFFFFFFFFFFF000)) &&
(*((PULONG64)(RspPos)) <= ((KiSystemServiceRepeat & 0XFFFFFFFFFFFFF000) + 0x2000)))
{
//TargetFind!
if (((PULONG64)RspPos)[9] == HookInfo->OrgFunc)
{
HookInfo->Lock = FALSE;
_disable();
((PULONG64)RspPos)[9] = HookInfo->HookFunc;
_enable();
}
goto sub_1;
}
}
}
}
++RspPos;
}
}
sub_1:
return HookInfo->OrigeHalCollectPmcCounters(Context, TraceBuff);
}
VOID ProxyHalPrivateDispatchTable(PVOID Context, ULONGLONG TraceBuff)
{
USHORT Magic = 0xf33;\\系统调用在栈上的关键字1
ULONG Signate = 0x501802;\\系统调用在栈上的关键字2
PULONG RspPos = _AddressOfReturnAddress();
PULONG RspLimit = __readgsqword(0x1a8);
ULONG64 KiSystemServiceRepeat = HookInfo->KiSystemServiceRepeat;
if (KeGetCurrentIrql() <= DISPATCH_LEVEL)
{
if (ExGetPreviousMode() == KernelMode)return;
if (!KiSystemServiceRepeat)
{
DbgPrint("failed to find KiSystemServiceRepeat\r\n");
return;
}
while (RspPos <= RspLimit)
{
if (*((PUSHORT)(RspPos)) == Magic)
{
if (RspPos[2] == Signate)
{
for (; (ULONG64)RspPos <= (ULONG64)RspLimit; ++RspPos)
{
if ((*((PULONG64)(RspPos)) >= (KiSystemServiceRepeat & 0XFFFFFFFFFFFFF000)) &&
(*((PULONG64)(RspPos)) <= ((KiSystemServiceRepeat & 0XFFFFFFFFFFFFF000) + 0x2000)))
{
//TargetFind!
if (((PULONG64)RspPos)[9] == HookInfo->OrgFunc)
{
HookInfo->Lock = FALSE;
_disable();
((PULONG64)RspPos)[9] = HookInfo->HookFunc;
_enable();
}
goto sub_1;
}
}
}
}
++RspPos;
}
}
sub_1:
return HookInfo->OrigeHalCollectPmcCounters(Context, TraceBuff);
}
NTSTATUS EndEventTraceWork()
{
NTSTATUS state = STATUS_UNSUCCESSFUL;
ULONG LenthRetVaul=0;
EVENT_TRACE_PROPERTIES* EtwInfo = ExAllocatePool(PagedPool, 0x1000);
if (!EtwInfo)
{
DbgPrint("2_AllocateMemFial!\n");
}
memset(EtwInfo, 0, 0x1000);
EtwInfo->Wnode.BufferSize = 0x1000;
EtwInfo->Wnode.Flags = WNODE_FLAG_TRACED_GUID;
RtlInitUnicodeString(&(EtwInfo->ProviderName), L"Circular Kernel Context Logger");
EtwInfo->Wnode.Guid = CkclSessionGuid;
EtwInfo->Wnode.ClientContext = 1;
EtwInfo->BufferSize = sizeof(ULONG);
EtwInfo->MinimumBuffers = 2;
EtwInfo->MaximumBuffers = 2;
EtwInfo->LogFileMode = EVENT_TRACE_BUFFERING_MODE;
state = ZwTraceControl(EtwpStopTrace, EtwInfo, 0x1000, EtwInfo, 0x1000, &LenthRetVaul);
if (!NT_SUCCESS(state))
{
DbgPrint("stop event trace fail!-state=%x\n", state);
}
if (EtwInfo)ExFreePool(EtwInfo);
HookInfo->EtwOffNo = FALSE;
return state;
}
NTSTATUS StartEventTraceWork()
{
NTSTATUS state=STATUS_UNSUCCESSFUL;
ULONG LenthRetVaul=0;
EVENT_TRACE_PROPERTIES* EtwInfo = ExAllocatePool(PagedPool, 0x1000);
if (!EtwInfo)
{
DbgPrint("1_AllocateMemFial!\n");
}
memset(EtwInfo, 0, 0x1000);
EtwInfo->Wnode.BufferSize = 0x1000;
EtwInfo->Wnode.Flags = WNODE_FLAG_TRACED_GUID;
RtlInitUnicodeString(&(EtwInfo->ProviderName), L"Circular Kernel Context Logger");
EtwInfo->Wnode.Guid = CkclSessionGuid;
EtwInfo->Wnode.ClientContext = 1;
EtwInfo->BufferSize = sizeof(ULONG);
EtwInfo->MinimumBuffers = 2;
EtwInfo->MaximumBuffers = 2;
EtwInfo->LogFileMode = EVENT_TRACE_BUFFERING_MODE;
state = ZwTraceControl(EtwpStartTrace, EtwInfo, 0X1000, EtwInfo,0x1000, &LenthRetVaul);
if (!NT_SUCCESS(state) && state != STATUS_OBJECT_NAME_COLLISION)
{
DbgPrint("EventTrace Start Fail-state=%x\n",state);
}
EtwInfo->EnableFlags = EVENT_TRACE_FLAG_SYSTEMCALL;
state = ZwTraceControl(EtwpUpdateTrace, EtwInfo, 0x1000, EtwInfo, 0x1000, &LenthRetVaul);
if (!NT_SUCCESS(state))
{
DbgPrint("failed to enable syscall etw-state=%x\n", state);
}
if (EtwInfo)
{
ExFreePool(EtwInfo);
}
return state;
}
NTSTATUS EndEventTraceWork()
{
NTSTATUS state = STATUS_UNSUCCESSFUL;
ULONG LenthRetVaul=0;
EVENT_TRACE_PROPERTIES* EtwInfo = ExAllocatePool(PagedPool, 0x1000);
if (!EtwInfo)
{
DbgPrint("2_AllocateMemFial!\n");
}
memset(EtwInfo, 0, 0x1000);
EtwInfo->Wnode.BufferSize = 0x1000;
EtwInfo->Wnode.Flags = WNODE_FLAG_TRACED_GUID;
RtlInitUnicodeString(&(EtwInfo->ProviderName), L"Circular Kernel Context Logger");
EtwInfo->Wnode.Guid = CkclSessionGuid;
EtwInfo->Wnode.ClientContext = 1;
EtwInfo->BufferSize = sizeof(ULONG);
EtwInfo->MinimumBuffers = 2;
EtwInfo->MaximumBuffers = 2;
EtwInfo->LogFileMode = EVENT_TRACE_BUFFERING_MODE;
state = ZwTraceControl(EtwpStopTrace, EtwInfo, 0x1000, EtwInfo, 0x1000, &LenthRetVaul);
if (!NT_SUCCESS(state))
{
DbgPrint("stop event trace fail!-state=%x\n", state);
}
if (EtwInfo)ExFreePool(EtwInfo);
HookInfo->EtwOffNo = FALSE;
return state;
}
NTSTATUS StartEventTraceWork()
{
NTSTATUS state=STATUS_UNSUCCESSFUL;
ULONG LenthRetVaul=0;
EVENT_TRACE_PROPERTIES* EtwInfo = ExAllocatePool(PagedPool, 0x1000);
if (!EtwInfo)
{
DbgPrint("1_AllocateMemFial!\n");
}
memset(EtwInfo, 0, 0x1000);
EtwInfo->Wnode.BufferSize = 0x1000;
EtwInfo->Wnode.Flags = WNODE_FLAG_TRACED_GUID;
RtlInitUnicodeString(&(EtwInfo->ProviderName), L"Circular Kernel Context Logger");
EtwInfo->Wnode.Guid = CkclSessionGuid;
EtwInfo->Wnode.ClientContext = 1;
EtwInfo->BufferSize = sizeof(ULONG);
EtwInfo->MinimumBuffers = 2;
EtwInfo->MaximumBuffers = 2;
EtwInfo->LogFileMode = EVENT_TRACE_BUFFERING_MODE;
传播安全知识、拓宽行业人脉——看雪讲师团队等你加入!
最后于 2024-9-18 13:15
被Mr.hack编辑
,原因: 上传源代码