赞赏记录
参与人
雪币
留言
时间
butterfly_n
+1
这个讨论对我很有帮助,谢谢!
2025-2-10 19:20
风兮木晓
你的分享对大家帮助很大,非常感谢!
2025-1-10 15:42
Ram98
非常支持你的观点!
2024-12-30 09:54
Yangser
你的分享对大家帮助很大,非常感谢!
2024-12-10 15:21
Ive_406746
谢谢你的细致分析,受益匪浅!
2024-10-11 10:57
touful
感谢你的贡献,论坛因你而更加精彩!
2024-9-18 11:27
ngiokweng
感谢你的贡献,论坛因你而更加精彩!
2024-7-31 13:37
养只猫不好么
为你点赞~
2024-7-30 16:52
Aar0n
非常支持你的观点!
2024-7-30 10:54
你瞒我瞒
你的分享对大家帮助很大,非常感谢!
2024-7-29 16:08
|
|
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|

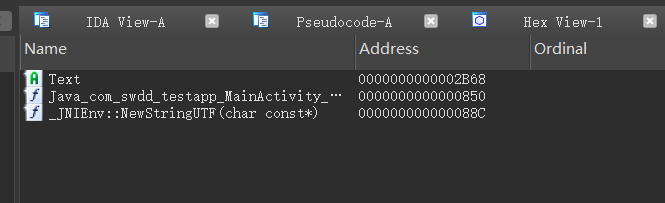
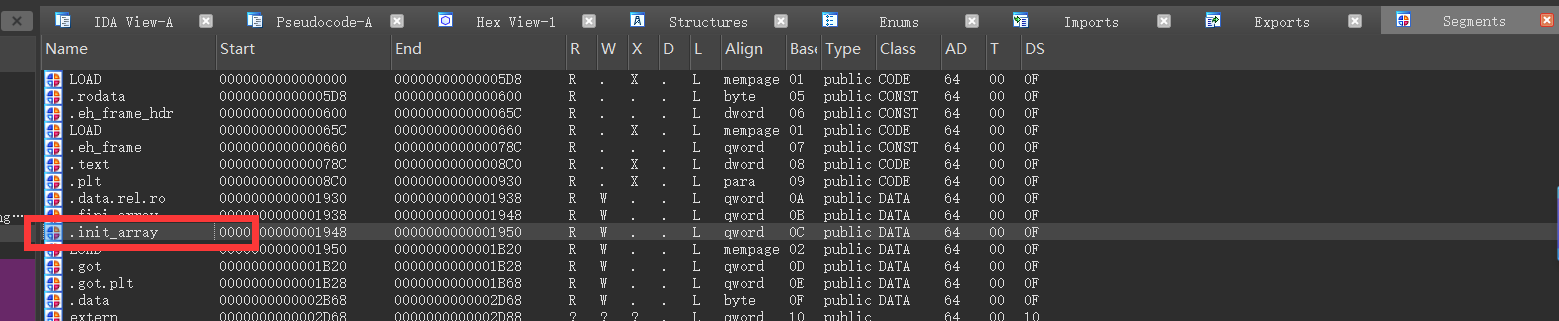
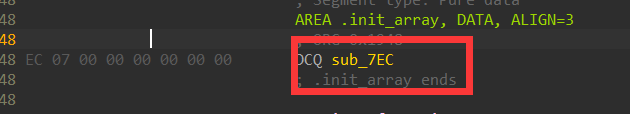
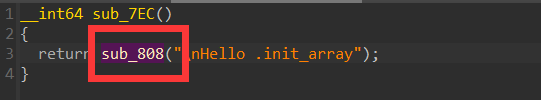
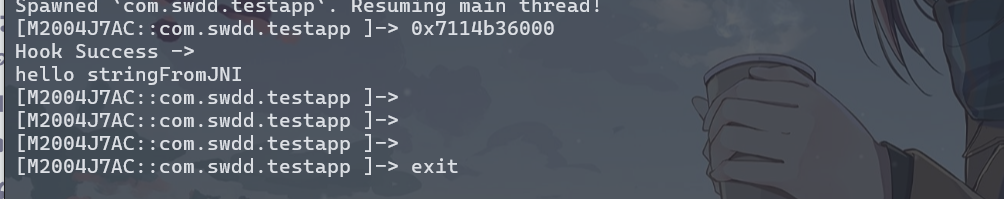
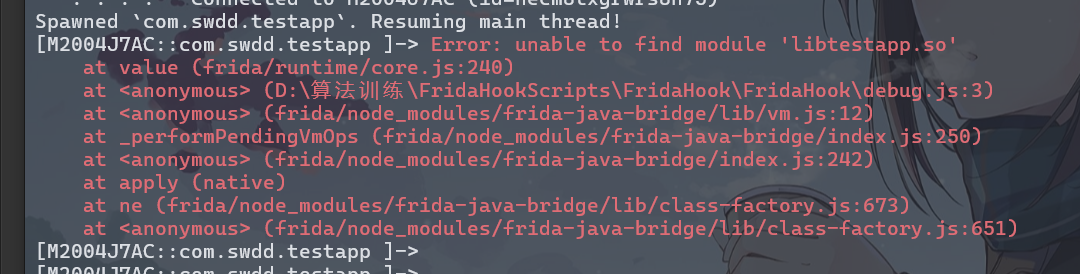
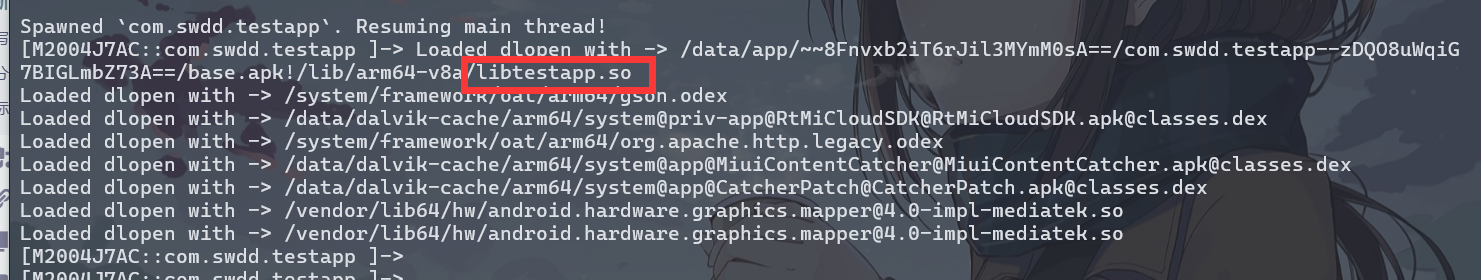
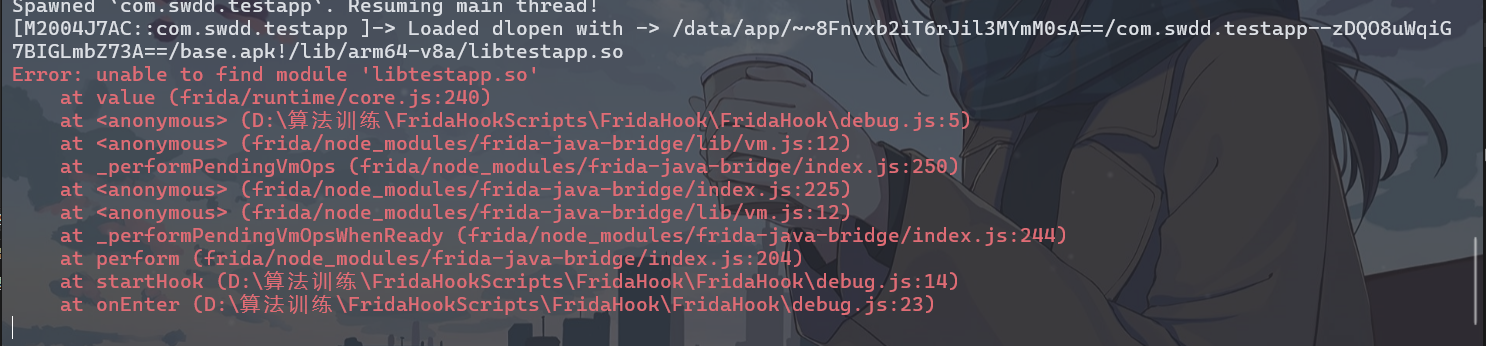
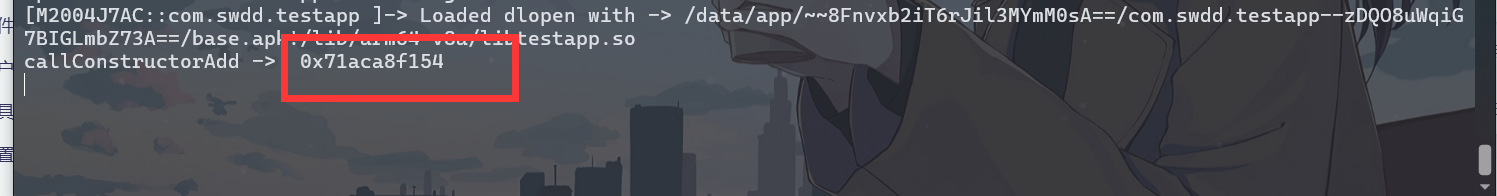
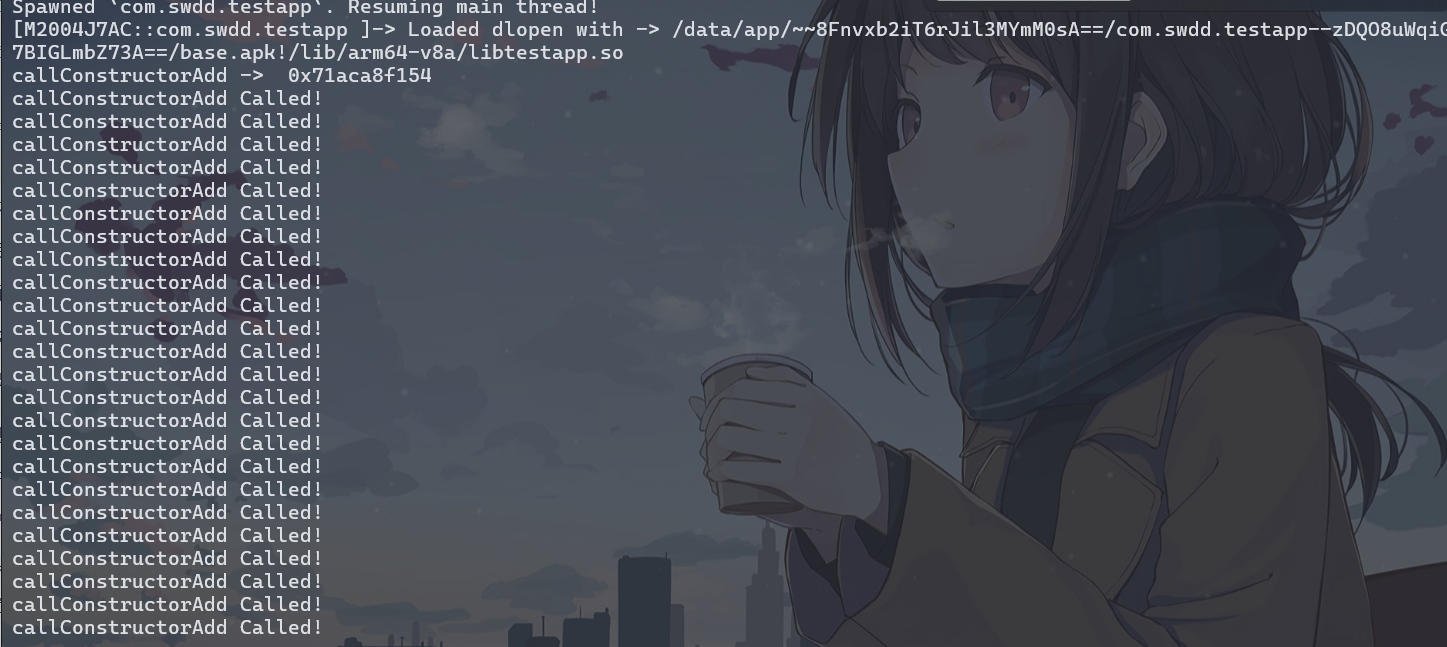
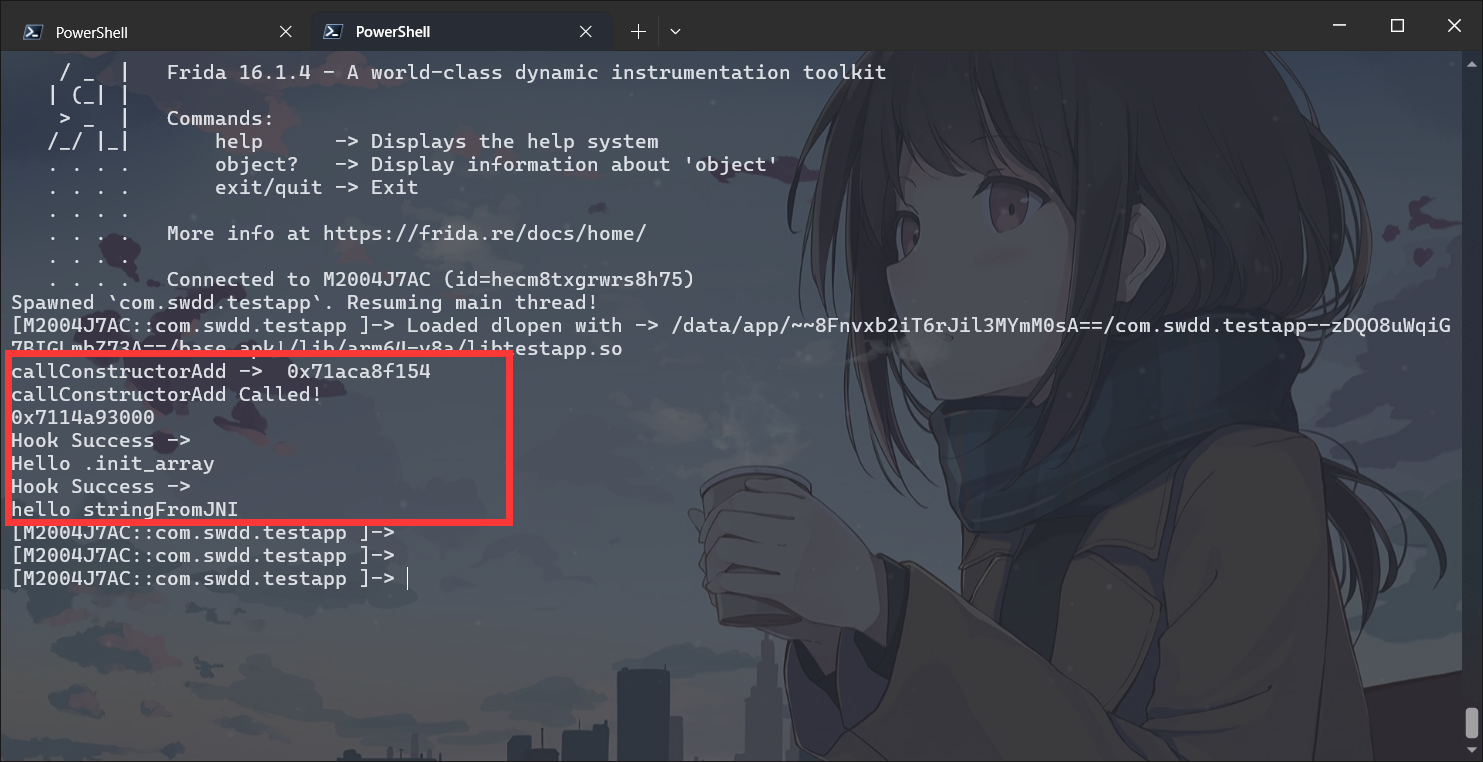

 ,大佬有个问题请教一下,如果是init_proc里的方法呢,方式和这个一样嘛。init_proc和init_array有什么区别,哪个对抗的难度更高?
,大佬有个问题请教一下,如果是init_proc里的方法呢,方式和这个一样嘛。init_proc和init_array有什么区别,哪个对抗的难度更高?






