【文章使用unidbg以及代码下载】
654K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6H3j5h3&6Q4x3X3g2T1j5h3W2V1N6g2)9J5k6h3y4G2L8g2)9J5c8Y4y4Q4x3V1j5I4g2f1y4G2k6r3b7K6x3h3W2n7k6%4q4o6g2i4A6@1d9@1E0V1h3W2A6H3k6H3`.`.
提取码:5ifo
1.网上看了某帖子关于对sgmain的doCommandNative函数调用的复现,进一步了解了关于sgmain系列的安全措施,于是萌生了复现的想法,帖子链接:b9bK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6X3y4g2)9J5k6i4m8E0i4K6u0r3k6$3!0Q4x3X3b7I4x3U0V1J5y4e0k6Q4x3X3g2Z5N6r3#2D9
2.由于之前对某航app进行过研究,并且发现其对wToken参数加密时也使用了sgmain系列进行保护,所以想要针对次app进行unidbg复现sagmain.so的调用
3.关于在复现前,网查了很多关于sagmain的帖子,其中有汇编的大致分析逻辑和unidbg复现的相关逻辑,感谢前辈大佬的帖子
https://bbs.kanxue.com/thread-267741.htm#msg_header_h2_7
6a1K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6U0L8r3!0#2k6q4)9J5k6i4c8W2L8X3y4W2L8Y4c8Q4x3X3g2U0L8$3#2Q4x3V1k6V1k6i4k6W2L8r3!0H3k6i4u0Q4x3V1k6S2M7Y4c8A6j5$3I4W2i4K6u0r3x3e0V1J5x3K6p5@1z5l9`.`.
194K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8r3!0Y4i4K6u0W2j5%4y4V1L8W2)9J5k6h3&6W2N6q4)9J5c8V1A6G2K9r3&6Q4y4h3k6x3k6h3&6G2L8W2)9J5c8X3q4J5N6r3W2U0L8r3g2Q4x3V1k6V1k6i4c8S2K9h3I4K6i4K6u0r3x3e0t1&6y4e0M7J5x3U0p5%4
97fK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8r3!0Y4i4K6u0W2j5%4y4V1L8W2)9J5k6h3&6W2N6q4)9J5c8Y4q4I4i4K6g2X3x3K6t1&6y4e0f1J5x3U0y4Q4x3V1k6S2M7Y4c8A6j5$3I4W2i4K6u0r3k6r3g2@1j5h3W2D9M7#2)9J5c8U0p5J5x3o6f1H3x3o6x3#2x3b7`.`.
https://bbs.kanxue.com/thread-265017.htm
4.关于doCommandNative调用前,还需要进行初始化的操作,可以从启动app开始对次函数调用进行hook,打印参数的内容和返回值,然后unidbg模拟一步步的执行
5.最终目的时调用参数60902参数的doCommandNative方法对请求内容进行加密获得wToken值,思路明确后准备unidbg进行如下的调用:(这里借用:7b3K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6X3y4g2)9J5k6i4m8E0i4K6u0r3k6$3!0Q4x3X3b7I4x3U0V1J5y4e0k6Q4x3X3g2Z5N6r3#2D9 帖子大佬分析的执行流程图)
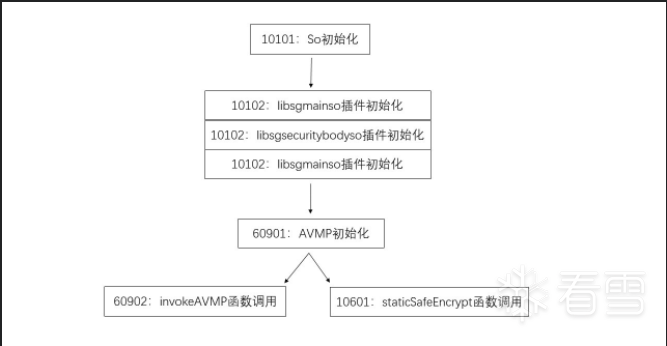
6.在unidbg复现过程中,在第一个10101的调用时候,返回值一直是null,而不是hook的0,经过多方测试,最终在unidbg低版本并且对32位so进行模拟执行时,会返回0(猜测:新版本unidbg应该是帮我们补了一些环境,而旧版本则没有,所以旧版本运行会提示补环境,照补即可,这里补充环境参考了以下两个链接的帖子:8f4K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8r3!0Y4i4K6u0W2j5%4y4V1L8W2)9J5k6h3&6W2N6q4)9J5c8V1A6G2K9r3&6Q4y4h3k6x3k6h3&6G2L8W2)9J5c8X3q4J5N6r3W2U0L8r3g2Q4x3V1k6V1k6i4c8S2K9h3I4K6i4K6u0r3x3e0t1&6y4e0M7J5x3U0p5%4 和 2ceK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8r3!0Y4i4K6u0W2j5%4y4V1L8W2)9J5k6h3&6W2N6q4)9J5c8Y4q4I4i4K6g2X3x3K6t1&6y4e0f1J5x3U0y4Q4x3V1k6S2M7Y4c8A6j5$3I4W2i4K6u0r3k6r3g2@1j5h3W2D9M7#2)9J5c8U0p5J5x3o6f1H3x3o6x3#2x3g2!0q4c8W2!0n7b7#2)9^5z5b7`.`.
7.unidbg代码如下:
8.以上代码虽然能够正确的执行一些逻辑,但是在最后的60902调用时,返回值出错了,并且提示SecException(1910),通过如下链接查找,399K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Z5k6h3I4H3i4K6u0W2j5h3I4A6P5i4g2F1i4K6u0W2j5$3!0E0i4K6u0r3k6r3!0U0N6h3#2W2L8Y4c8Q4y4h3k6V1k6i4c8S2K9h3I4Q4x3V1j5I4y4U0l9#2y4K6S2Q4x3X3g2Z5N6r3#2D9 该错误的原来可能是:非法的avmpInstance实例
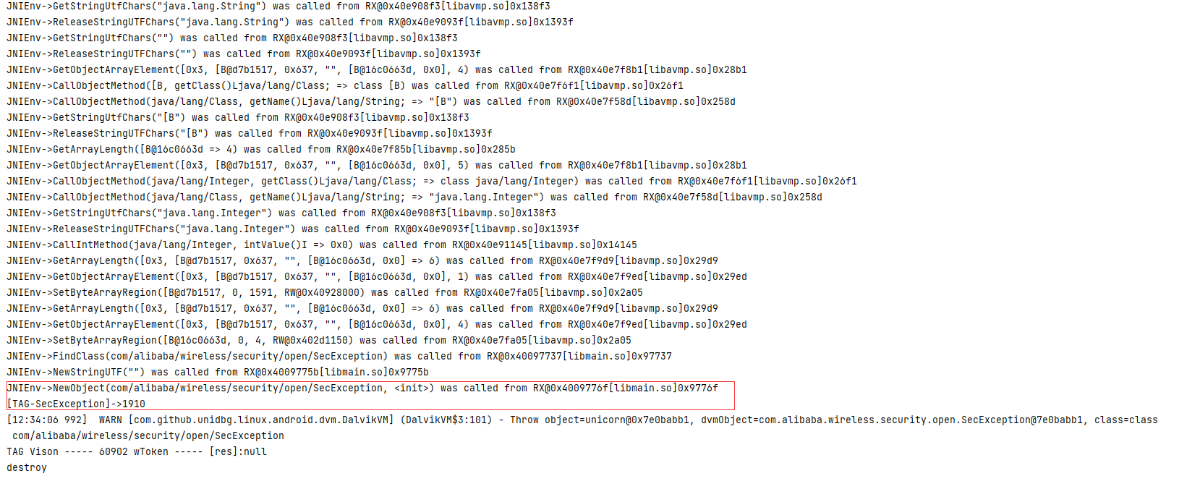
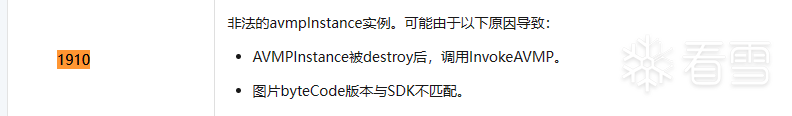
10.补充说明:使用unidbg 080版本进行复现
【注】文章中如有任何侵权,请联系说明修改!!
【注】本文仅用于学习讨论,不做任何商务用途!!
AOSP on blueline::com.rytong.ceair ]-> libDexHelper.so detect: 0x9ec5c
libDexHelper.so detect: 0xaa97c
libDexHelper.so detect: 0x9d73c
libDexHelper.so detect: 0xe3fd0
0x6fbe7e40ac
【2023-θ4-19 22:25:00:983】 目标app正在加载so文件:/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libdexjni.so
【2023-θ4-19 22:25:02:925】 目标app正在加载so文件:/vendor/lib64/hw/gralloc.sdm845.so
【2023-θ4-19 22:25:02:938】 目标app正在加载so文件:/vendor/lib64/hw/android.hardware.graphics.mapper@2.0-impl-qti-display.so
【2023-θ4-19 22:25:35:687】 目标app正在加载so文件:/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libsgmainso-5.4.193.so
【2023-θ4-19 22:25:35:687】 目标so已经加载,正在寻找目标类....
my_log->com.taobao.wireless.security.adapter.JNICLibrary,doCommandNative,,,,true,true
doCommandNative hooking....
【2023-θ4-19 22:25:35:699】 已找到目标类:com.taobao.wireless.security.adapter.JNICLibrary,正在切换classLoader....
--------------【2023-θ4-19 22:25:35:715】-------------
com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative is called
参数长度:2
参数0:【类型:number】
10101
参数1:【类型:object】
com.rytong.ceair.CeairApp@407804a,3,,/data/user/0/com.rytong.ceair/app_SGLib,
返回结果:【类型:object】 【类名:class java.lang.Integer】
0
调用栈:
java.lang.Throwable
at com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative(Native Method)
at com.alibaba.wireless.security.mainplugin.a.doCommand(Unknown Source:0)
at com.alibaba.wireless.security.mainplugin.SecurityGuardMainPlugin.onPluginLoaded(Unknown Source:147)
at com.alibaba.wireless.security.framework.d.a(Unknown Source:1134)
at com.alibaba.wireless.security.framework.d.d(Unknown Source:67)
at com.alibaba.wireless.security.framework.d.getPluginInfo(Unknown Source:3)
at com.alibaba.wireless.security.open.initialize.b.a(Unknown Source:38)
at com.alibaba.wireless.security.open.initialize.a.loadLibrarySync(Unknown Source:5)
at com.alibaba.wireless.security.open.initialize.a.initialize(Unknown Source:0)
at com.alibaba.wireless.security.open.SecurityGuardManager.getInstance(Unknown Source:20)
at com.alibaba.wireless.security.open.SecurityGuardManager.getInstance(Unknown Source:1)
at aej.a(AliPreWorm.java:54)
at com.rytong.ceair.CeairApp.agreeConcealPrivacyToInit(CeairApp.java:86)
at com.rytong.ceair.main.SplashActivity$l.onClick(SplashActivity.kt:477)
at zm.onClick(ClickProxy.java:55)
at android.view.View.performClick(View.java:7259)
at android.view.View.performClickInternal(View.java:7236)
at android.view.View.access$3600(View.java:801)
at android.view.View$PerformClick.run(View.java:27892)
at android.os.Handler.handleCallback(Handler.java:883)
at android.os.Handler.dispatchMessage(Handler.java:100)
at android.os.Looper.loop(Looper.java:214)
at android.app.ActivityThread.main(ActivityThread.java:7699)
at java.lang.reflect.Method.invoke(Native Method)
at com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)
--------------【2023-θ4-19 22:25:36:173】-------------
com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative is called
参数长度:2
参数0:【类型:number】
10102
参数1:【类型:object】
main,5.4.193,/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libsgmainso-5.4.193.so
返回结果:【类型:object】 【类名:class java.lang.Integer】
0
调用栈:
java.lang.Throwable
at com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative(Native Method)
at com.alibaba.wireless.security.mainplugin.a.doCommand(Unknown Source:0)
at com.alibaba.wireless.security.framework.d.a(Unknown Source:1207)
at com.alibaba.wireless.security.framework.d.d(Unknown Source:67)
at com.alibaba.wireless.security.framework.d.getPluginInfo(Unknown Source:3)
at com.alibaba.wireless.security.open.initialize.b.a(Unknown Source:38)
at com.alibaba.wireless.security.open.initialize.a.loadLibrarySync(Unknown Source:5)
at com.alibaba.wireless.security.open.initialize.a.initialize(Unknown Source:0)
at com.alibaba.wireless.security.open.SecurityGuardManager.getInstance(Unknown Source:20)
at com.alibaba.wireless.security.open.SecurityGuardManager.getInstance(Unknown Source:1)
at aej.a(AliPreWorm.java:54)
at com.rytong.ceair.CeairApp.agreeConcealPrivacyToInit(CeairApp.java:86)
at com.rytong.ceair.main.SplashActivity$l.onClick(SplashActivity.kt:477)
at zm.onClick(ClickProxy.java:55)
at android.view.View.performClick(View.java:7259)
at android.view.View.performClickInternal(View.java:7236)
at android.view.View.access$3600(View.java:801)
at android.view.View$PerformClick.run(View.java:27892)
at android.os.Handler.handleCallback(Handler.java:883)
at android.os.Handler.dispatchMessage(Handler.java:100)
at android.os.Looper.loop(Looper.java:214)
at android.app.ActivityThread.main(ActivityThread.java:7699)
at java.lang.reflect.Method.invoke(Native Method)
at com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)
【2023-θ4-19 22:25:36:236】 目标app正在加载so文件:/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libsgsecuritybodyso-5.4.112.so
--------------【2023-θ4-19 22:25:36:240】-------------
com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative is called
参数长度:2
参数0:【类型:number】
10102
参数1:【类型:object】
securitybody,5.4.112,/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libsgsecuritybodyso-5.4.112.so
返回结果:【类型:object】 【类名:class java.lang.Integer】
0
调用栈:
java.lang.Throwable
at com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative(Native Method)
at com.alibaba.wireless.security.mainplugin.a.doCommand(Unknown Source:0)
at com.alibaba.wireless.security.framework.d.a(Unknown Source:1207)
at com.alibaba.wireless.security.framework.d.d(Unknown Source:67)
at com.alibaba.wireless.security.framework.d.a(Unknown Source:301)
at com.alibaba.wireless.security.framework.d.a(Unknown Source:340)
at com.alibaba.wireless.security.framework.d.d(Unknown Source:67)
at com.alibaba.wireless.security.framework.d.getPluginInfo(Unknown Source:3)
at com.alibaba.wireless.security.framework.d.getInterface(Unknown Source:64)
at com.alibaba.wireless.security.open.SecurityGuardManager.getInterface(Unknown Source:2)
at aej.a(AliPreWorm.java:54)
at com.rytong.ceair.CeairApp.agreeConcealPrivacyToInit(CeairApp.java:86)
at com.rytong.ceair.main.SplashActivity$l.onClick(SplashActivity.kt:477)
at zm.onClick(ClickProxy.java:55)
at android.view.View.performClick(View.java:7259)
at android.view.View.performClickInternal(View.java:7236)
at android.view.View.access$3600(View.java:801)
at android.view.View$PerformClick.run(View.java:27892)
at android.os.Handler.handleCallback(Handler.java:883)
at android.os.Handler.dispatchMessage(Handler.java:100)
at android.os.Looper.loop(Looper.java:214)
at android.app.ActivityThread.main(ActivityThread.java:7699)
at java.lang.reflect.Method.invoke(Native Method)
at com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)
【2023-θ4-19 22:25:36:268】 目标app正在加载so文件:/data/user/0/com.rytong.ceair/app_SGLib/app_1681789435/main/libsgavmpso-5.4.1002.so
--------------【2023-θ4-19 22:25:36:270】-------------
com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative is called
参数长度:2
参数0:【类型:number】
10102
参数1:【类型:object】
avmp,5.4.1002,/data/user/0/com.rytong.ceair/app_SGLib/app_1681789435/main/libsgavmpso-5.4.1002.so
返回结果:【类型:object】 【类名:class java.lang.Integer】
0
调用栈:
java.lang.Throwable
at com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative(Native Method)
at com.alibaba.wireless.security.mainplugin.a.doCommand(Unknown Source:0)
at com.alibaba.wireless.security.framework.d.a(Unknown Source:1207)
at com.alibaba.wireless.security.framework.d.d(Unknown Source:67)
at com.alibaba.wireless.security.framework.d.getPluginInfo(Unknown Source:3)
at com.alibaba.wireless.security.framework.d.getInterface(Unknown Source:64)
at com.alibaba.wireless.security.open.SecurityGuardManager.getInterface(Unknown Source:2)
at aej.a(AliPreWorm.java:54)
at com.rytong.ceair.CeairApp.agreeConcealPrivacyToInit(CeairApp.java:86)
at com.rytong.ceair.main.SplashActivity$l.onClick(SplashActivity.kt:477)
at zm.onClick(ClickProxy.java:55)
at android.view.View.performClick(View.java:7259)
at android.view.View.performClickInternal(View.java:7236)
at android.view.View.access$3600(View.java:801)
at android.view.View$PerformClick.run(View.java:27892)
at android.os.Handler.handleCallback(Handler.java:883)
at android.os.Handler.dispatchMessage(Handler.java:100)
at android.os.Looper.loop(Looper.java:214)
at android.app.ActivityThread.main(ActivityThread.java:7699)
at java.lang.reflect.Method.invoke(Native Method)
at com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)
--------------【2023-θ4-19 22:25:36:281】-------------
com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative is called
参数长度:2
参数0:【类型:number】
60901
参数1:【类型:object】
0335_mwua,sgcipher
返回结果:【类型:object】 【类名:class java.lang.Long】
475517112478
调用栈:
java.lang.Throwable
at com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative(Native Method)
at com.alibaba.wireless.security.mainplugin.a.doCommand(Unknown Source:0)
at com.alibaba.wireless.security.avmpplugin.b.b.a(Unknown Source:18)
at com.alibaba.wireless.security.avmpplugin.b.a.createAVMPInstance(Unknown Source:7)
at com.alibaba.wireless.security.avmpplugin.a.a.initialize(Unknown Source:14)
at aej.a(AliPreWorm.java:55)
at com.rytong.ceair.CeairApp.agreeConcealPrivacyToInit(CeairApp.java:86)
at com.rytong.ceair.main.SplashActivity$l.onClick(SplashActivity.kt:477)
at zm.onClick(ClickProxy.java:55)
at android.view.View.performClick(View.java:7259)
at android.view.View.performClickInternal(View.java:7236)
at android.view.View.access$3600(View.java:801)
at android.view.View$PerformClick.run(View.java:27892)
at android.os.Handler.handleCallback(Handler.java:883)
at android.os.Handler.dispatchMessage(Handler.java:100)
at android.os.Looper.loop(Looper.java:214)
at android.app.ActivityThread.main(ActivityThread.java:7699)
at java.lang.reflect.Method.invoke(Native Method)
at com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)
【2023-θ4-19 22:25:36:449】 目标app正在加载so文件:/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libdeviceid_1.0.so
【2023-θ4-19 22:25:37:564】 目标app正在加载so文件:/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libencrypt.so
【2023-θ4-19 22:25:37:619】 目标app正在加载so文件:/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libentryexpro.so
【2023-θ4-19 22:25:40:819】 目标app正在加载so文件:/data/dalvik-cache/arm64/product@app@webview@webview.apk@classes.dex
【2023-θ4-19 22:25:40:839】 目标app正在加载so文件:libwebviewchromium.so
【2023-θ4-19 22:25:40:927】 目标app正在加载so文件:/product/app/webview/webview.apk!/lib/arm64-v8a/libwebviewchromium.so
【2023-θ4-19 22:25:40:934】 目标app正在加载so文件:/system/lib64/libwebviewchromium_plat_support.so
【2023-θ4-19 22:25:42:838】 目标app正在加载so文件:/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libwbsk_crypto_tool.so
--------------【2023-θ4-19 22:25:42:894】-------------
com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative is called
参数长度:2
参数0:【类型:number】
60902
参数1:【类型:object】
475517112478,sign,class [B,[Ljava.lang.Object;@8058bb
返回结果:【类型:object】 【类名:class [B】
"QllUUl9yUncwbkFVNFNpWTg5WnlnVldBcnZ2bmZuYXhVZnY4WHE4WDREcGhvNmNYSkdzM2dMMjZ5YUV6dndoRUorSjF5V1ZRVHNxZnBndk1PdVdQc1ZMdktGcHloZ256WXorNHAyWWJJWlhCbW5zNVdyMzg3cFM2VTJiakFPZTExZ1NzakNSRWplcEJ0NmVYU2w0eHNtWll2UFV0MmYxVTM5TEFyN01ZbzVoZDMzS0gzKzQ1aXd4aDY0TGdVaVVicUlBR3VNQnBKalQxc2lhMENTcTJEbGxHQlBPaXRTRjExTmNoRnpjcHlyOFE3Q2NZPSZBV0VSX2EwMDEzOTIzNzc5M2I1YWE5YjJiYWVkZWI4NWYwOWM1ZDAwYWYxZDU3ZTE4NQ=="
调用栈:
java.lang.Throwable
at com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative(Native Method)
at com.alibaba.wireless.security.mainplugin.a.doCommand(Unknown Source:0)
at com.alibaba.wireless.security.avmpplugin.b.b.invokeAVMP(Unknown Source:30)
at com.alibaba.wireless.security.avmpplugin.a.a.avmpSign(Unknown Source:63)
at aej.a(AliPreWorm.java:86)
at acc.intercept(EncodeRequestInterceptor.kt:92)
at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:142)
at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:117)
at aco.intercept(TransactionIdInterceptor.kt:59)
at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:142)
at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:117)
at ack.intercept(IntervalRequestInterceptor.java:34)
at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:142)
at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:117)
at acd.intercept(HeaderInterceptor.kt:77)
at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:142)
at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:117)
at okhttp3.RealCall.getResponseWithInterceptorChain(RealCall.java:229)
at okhttp3.RealCall.execute(RealCall.java:81)
at retrofit2.OkHttpCall.execute(OkHttpCall.java:190)
at gya.a(CallObservable.java:41)
at hxb.f(Observable.java:12284)
at gxz.a(BodyObservable.java:34)
at hxb.f(Observable.java:12284)
at iqa$b.run(ObservableSubscribeOn.java:96)
at hxj$a.run(Scheduler.java:578)
at io.reactivex.internal.schedulers.ScheduledRunnable.run(ScheduledRunnable.java:66)
at io.reactivex.internal.schedulers.ScheduledRunnable.call(ScheduledRunnable.java:57)
at java.util.concurrent.FutureTask.run(FutureTask.java:266)
at java.util.concurrent.ScheduledThreadPoolExecutor$ScheduledFutureTask.run(ScheduledThreadPoolExecutor.java:301)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1167)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:641)
at java.lang.Thread.run(Thread.java:919)
AOSP on blueline::com.rytong.ceair ]-> libDexHelper.so detect: 0x9ec5c
libDexHelper.so detect: 0xaa97c
libDexHelper.so detect: 0x9d73c
libDexHelper.so detect: 0xe3fd0
0x6fbe7e40ac
【2023-θ4-19 22:25:00:983】 目标app正在加载so文件:/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libdexjni.so
【2023-θ4-19 22:25:02:925】 目标app正在加载so文件:/vendor/lib64/hw/gralloc.sdm845.so
【2023-θ4-19 22:25:02:938】 目标app正在加载so文件:/vendor/lib64/hw/android.hardware.graphics.mapper@2.0-impl-qti-display.so
【2023-θ4-19 22:25:35:687】 目标app正在加载so文件:/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libsgmainso-5.4.193.so
【2023-θ4-19 22:25:35:687】 目标so已经加载,正在寻找目标类....
my_log->com.taobao.wireless.security.adapter.JNICLibrary,doCommandNative,,,,true,true
doCommandNative hooking....
【2023-θ4-19 22:25:35:699】 已找到目标类:com.taobao.wireless.security.adapter.JNICLibrary,正在切换classLoader....
--------------【2023-θ4-19 22:25:35:715】-------------
com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative is called
参数长度:2
参数0:【类型:number】
10101
参数1:【类型:object】
com.rytong.ceair.CeairApp@407804a,3,,/data/user/0/com.rytong.ceair/app_SGLib,
返回结果:【类型:object】 【类名:class java.lang.Integer】
0
调用栈:
java.lang.Throwable
at com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative(Native Method)
at com.alibaba.wireless.security.mainplugin.a.doCommand(Unknown Source:0)
at com.alibaba.wireless.security.mainplugin.SecurityGuardMainPlugin.onPluginLoaded(Unknown Source:147)
at com.alibaba.wireless.security.framework.d.a(Unknown Source:1134)
at com.alibaba.wireless.security.framework.d.d(Unknown Source:67)
at com.alibaba.wireless.security.framework.d.getPluginInfo(Unknown Source:3)
at com.alibaba.wireless.security.open.initialize.b.a(Unknown Source:38)
at com.alibaba.wireless.security.open.initialize.a.loadLibrarySync(Unknown Source:5)
at com.alibaba.wireless.security.open.initialize.a.initialize(Unknown Source:0)
at com.alibaba.wireless.security.open.SecurityGuardManager.getInstance(Unknown Source:20)
at com.alibaba.wireless.security.open.SecurityGuardManager.getInstance(Unknown Source:1)
at aej.a(AliPreWorm.java:54)
at com.rytong.ceair.CeairApp.agreeConcealPrivacyToInit(CeairApp.java:86)
at com.rytong.ceair.main.SplashActivity$l.onClick(SplashActivity.kt:477)
at zm.onClick(ClickProxy.java:55)
at android.view.View.performClick(View.java:7259)
at android.view.View.performClickInternal(View.java:7236)
at android.view.View.access$3600(View.java:801)
at android.view.View$PerformClick.run(View.java:27892)
at android.os.Handler.handleCallback(Handler.java:883)
at android.os.Handler.dispatchMessage(Handler.java:100)
at android.os.Looper.loop(Looper.java:214)
at android.app.ActivityThread.main(ActivityThread.java:7699)
at java.lang.reflect.Method.invoke(Native Method)
at com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)
--------------【2023-θ4-19 22:25:36:173】-------------
com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative is called
参数长度:2
参数0:【类型:number】
10102
参数1:【类型:object】
main,5.4.193,/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libsgmainso-5.4.193.so
返回结果:【类型:object】 【类名:class java.lang.Integer】
0
调用栈:
java.lang.Throwable
at com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative(Native Method)
at com.alibaba.wireless.security.mainplugin.a.doCommand(Unknown Source:0)
at com.alibaba.wireless.security.framework.d.a(Unknown Source:1207)
at com.alibaba.wireless.security.framework.d.d(Unknown Source:67)
at com.alibaba.wireless.security.framework.d.getPluginInfo(Unknown Source:3)
at com.alibaba.wireless.security.open.initialize.b.a(Unknown Source:38)
at com.alibaba.wireless.security.open.initialize.a.loadLibrarySync(Unknown Source:5)
at com.alibaba.wireless.security.open.initialize.a.initialize(Unknown Source:0)
at com.alibaba.wireless.security.open.SecurityGuardManager.getInstance(Unknown Source:20)
at com.alibaba.wireless.security.open.SecurityGuardManager.getInstance(Unknown Source:1)
at aej.a(AliPreWorm.java:54)
at com.rytong.ceair.CeairApp.agreeConcealPrivacyToInit(CeairApp.java:86)
at com.rytong.ceair.main.SplashActivity$l.onClick(SplashActivity.kt:477)
at zm.onClick(ClickProxy.java:55)
at android.view.View.performClick(View.java:7259)
at android.view.View.performClickInternal(View.java:7236)
at android.view.View.access$3600(View.java:801)
at android.view.View$PerformClick.run(View.java:27892)
at android.os.Handler.handleCallback(Handler.java:883)
at android.os.Handler.dispatchMessage(Handler.java:100)
at android.os.Looper.loop(Looper.java:214)
at android.app.ActivityThread.main(ActivityThread.java:7699)
at java.lang.reflect.Method.invoke(Native Method)
at com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)
【2023-θ4-19 22:25:36:236】 目标app正在加载so文件:/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libsgsecuritybodyso-5.4.112.so
--------------【2023-θ4-19 22:25:36:240】-------------
com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative is called
参数长度:2
参数0:【类型:number】
10102
参数1:【类型:object】
securitybody,5.4.112,/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libsgsecuritybodyso-5.4.112.so
返回结果:【类型:object】 【类名:class java.lang.Integer】
0
调用栈:
java.lang.Throwable
at com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative(Native Method)
at com.alibaba.wireless.security.mainplugin.a.doCommand(Unknown Source:0)
at com.alibaba.wireless.security.framework.d.a(Unknown Source:1207)
at com.alibaba.wireless.security.framework.d.d(Unknown Source:67)
at com.alibaba.wireless.security.framework.d.a(Unknown Source:301)
at com.alibaba.wireless.security.framework.d.a(Unknown Source:340)
at com.alibaba.wireless.security.framework.d.d(Unknown Source:67)
at com.alibaba.wireless.security.framework.d.getPluginInfo(Unknown Source:3)
at com.alibaba.wireless.security.framework.d.getInterface(Unknown Source:64)
at com.alibaba.wireless.security.open.SecurityGuardManager.getInterface(Unknown Source:2)
at aej.a(AliPreWorm.java:54)
at com.rytong.ceair.CeairApp.agreeConcealPrivacyToInit(CeairApp.java:86)
at com.rytong.ceair.main.SplashActivity$l.onClick(SplashActivity.kt:477)
at zm.onClick(ClickProxy.java:55)
at android.view.View.performClick(View.java:7259)
at android.view.View.performClickInternal(View.java:7236)
at android.view.View.access$3600(View.java:801)
at android.view.View$PerformClick.run(View.java:27892)
at android.os.Handler.handleCallback(Handler.java:883)
at android.os.Handler.dispatchMessage(Handler.java:100)
at android.os.Looper.loop(Looper.java:214)
at android.app.ActivityThread.main(ActivityThread.java:7699)
at java.lang.reflect.Method.invoke(Native Method)
at com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)
【2023-θ4-19 22:25:36:268】 目标app正在加载so文件:/data/user/0/com.rytong.ceair/app_SGLib/app_1681789435/main/libsgavmpso-5.4.1002.so
--------------【2023-θ4-19 22:25:36:270】-------------
com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative is called
参数长度:2
参数0:【类型:number】
10102
参数1:【类型:object】
avmp,5.4.1002,/data/user/0/com.rytong.ceair/app_SGLib/app_1681789435/main/libsgavmpso-5.4.1002.so
返回结果:【类型:object】 【类名:class java.lang.Integer】
0
调用栈:
java.lang.Throwable
at com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative(Native Method)
at com.alibaba.wireless.security.mainplugin.a.doCommand(Unknown Source:0)
at com.alibaba.wireless.security.framework.d.a(Unknown Source:1207)
at com.alibaba.wireless.security.framework.d.d(Unknown Source:67)
at com.alibaba.wireless.security.framework.d.getPluginInfo(Unknown Source:3)
at com.alibaba.wireless.security.framework.d.getInterface(Unknown Source:64)
at com.alibaba.wireless.security.open.SecurityGuardManager.getInterface(Unknown Source:2)
at aej.a(AliPreWorm.java:54)
at com.rytong.ceair.CeairApp.agreeConcealPrivacyToInit(CeairApp.java:86)
at com.rytong.ceair.main.SplashActivity$l.onClick(SplashActivity.kt:477)
at zm.onClick(ClickProxy.java:55)
at android.view.View.performClick(View.java:7259)
at android.view.View.performClickInternal(View.java:7236)
at android.view.View.access$3600(View.java:801)
at android.view.View$PerformClick.run(View.java:27892)
at android.os.Handler.handleCallback(Handler.java:883)
at android.os.Handler.dispatchMessage(Handler.java:100)
at android.os.Looper.loop(Looper.java:214)
at android.app.ActivityThread.main(ActivityThread.java:7699)
at java.lang.reflect.Method.invoke(Native Method)
at com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)
--------------【2023-θ4-19 22:25:36:281】-------------
com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative is called
参数长度:2
参数0:【类型:number】
60901
参数1:【类型:object】
0335_mwua,sgcipher
返回结果:【类型:object】 【类名:class java.lang.Long】
475517112478
调用栈:
java.lang.Throwable
at com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative(Native Method)
at com.alibaba.wireless.security.mainplugin.a.doCommand(Unknown Source:0)
at com.alibaba.wireless.security.avmpplugin.b.b.a(Unknown Source:18)
at com.alibaba.wireless.security.avmpplugin.b.a.createAVMPInstance(Unknown Source:7)
at com.alibaba.wireless.security.avmpplugin.a.a.initialize(Unknown Source:14)
at aej.a(AliPreWorm.java:55)
at com.rytong.ceair.CeairApp.agreeConcealPrivacyToInit(CeairApp.java:86)
at com.rytong.ceair.main.SplashActivity$l.onClick(SplashActivity.kt:477)
at zm.onClick(ClickProxy.java:55)
at android.view.View.performClick(View.java:7259)
at android.view.View.performClickInternal(View.java:7236)
at android.view.View.access$3600(View.java:801)
at android.view.View$PerformClick.run(View.java:27892)
at android.os.Handler.handleCallback(Handler.java:883)
at android.os.Handler.dispatchMessage(Handler.java:100)
at android.os.Looper.loop(Looper.java:214)
at android.app.ActivityThread.main(ActivityThread.java:7699)
at java.lang.reflect.Method.invoke(Native Method)
at com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)
【2023-θ4-19 22:25:36:449】 目标app正在加载so文件:/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libdeviceid_1.0.so
【2023-θ4-19 22:25:37:564】 目标app正在加载so文件:/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libencrypt.so
【2023-θ4-19 22:25:37:619】 目标app正在加载so文件:/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libentryexpro.so
【2023-θ4-19 22:25:40:819】 目标app正在加载so文件:/data/dalvik-cache/arm64/product@app@webview@webview.apk@classes.dex
【2023-θ4-19 22:25:40:839】 目标app正在加载so文件:libwebviewchromium.so
【2023-θ4-19 22:25:40:927】 目标app正在加载so文件:/product/app/webview/webview.apk!/lib/arm64-v8a/libwebviewchromium.so
【2023-θ4-19 22:25:40:934】 目标app正在加载so文件:/system/lib64/libwebviewchromium_plat_support.so
【2023-θ4-19 22:25:42:838】 目标app正在加载so文件:/data/app/com.rytong.ceair-2joxiTDNb8xd68-9jbFtkA==/lib/arm64/libwbsk_crypto_tool.so
--------------【2023-θ4-19 22:25:42:894】-------------
com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative is called
参数长度:2
参数0:【类型:number】
60902
参数1:【类型:object】
475517112478,sign,class [B,[Ljava.lang.Object;@8058bb
返回结果:【类型:object】 【类名:class [B】
"QllUUl9yUncwbkFVNFNpWTg5WnlnVldBcnZ2bmZuYXhVZnY4WHE4WDREcGhvNmNYSkdzM2dMMjZ5YUV6dndoRUorSjF5V1ZRVHNxZnBndk1PdVdQc1ZMdktGcHloZ256WXorNHAyWWJJWlhCbW5zNVdyMzg3cFM2VTJiakFPZTExZ1NzakNSRWplcEJ0NmVYU2w0eHNtWll2UFV0MmYxVTM5TEFyN01ZbzVoZDMzS0gzKzQ1aXd4aDY0TGdVaVVicUlBR3VNQnBKalQxc2lhMENTcTJEbGxHQlBPaXRTRjExTmNoRnpjcHlyOFE3Q2NZPSZBV0VSX2EwMDEzOTIzNzc5M2I1YWE5YjJiYWVkZWI4NWYwOWM1ZDAwYWYxZDU3ZTE4NQ=="
调用栈:
java.lang.Throwable
at com.taobao.wireless.security.adapter.JNICLibrary.doCommandNative(Native Method)
at com.alibaba.wireless.security.mainplugin.a.doCommand(Unknown Source:0)
at com.alibaba.wireless.security.avmpplugin.b.b.invokeAVMP(Unknown Source:30)
at com.alibaba.wireless.security.avmpplugin.a.a.avmpSign(Unknown Source:63)
at aej.a(AliPreWorm.java:86)
at acc.intercept(EncodeRequestInterceptor.kt:92)
at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:142)
at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:117)
at aco.intercept(TransactionIdInterceptor.kt:59)
at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:142)
at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:117)
at ack.intercept(IntervalRequestInterceptor.java:34)
at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:142)
at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:117)
at acd.intercept(HeaderInterceptor.kt:77)
at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:142)
at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:117)
at okhttp3.RealCall.getResponseWithInterceptorChain(RealCall.java:229)
at okhttp3.RealCall.execute(RealCall.java:81)
at retrofit2.OkHttpCall.execute(OkHttpCall.java:190)
at gya.a(CallObservable.java:41)
at hxb.f(Observable.java:12284)
at gxz.a(BodyObservable.java:34)
at hxb.f(Observable.java:12284)
at iqa$b.run(ObservableSubscribeOn.java:96)
at hxj$a.run(Scheduler.java:578)
at io.reactivex.internal.schedulers.ScheduledRunnable.run(ScheduledRunnable.java:66)
at io.reactivex.internal.schedulers.ScheduledRunnable.call(ScheduledRunnable.java:57)
at java.util.concurrent.FutureTask.run(FutureTask.java:266)
at java.util.concurrent.ScheduledThreadPoolExecutor$ScheduledFutureTask.run(ScheduledThreadPoolExecutor.java:301)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1167)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:641)
at java.lang.Thread.run(Thread.java:919)
package com.taobao.wireless.security.adapter.JNICLibrary;
import com.alibaba.fastjson.util.IOUtils;
import com.github.unidbg.AndroidEmulator;
import com.github.unidbg.Module;
import com.github.unidbg.Emulator;
import com.github.unidbg.file.FileResult;
import com.github.unidbg.file.IOResolver;
import com.github.unidbg.file.linux.AndroidFileIO;
import com.github.unidbg.linux.android.AndroidARMEmulator;
import com.github.unidbg.linux.android.AndroidResolver;
import com.github.unidbg.linux.android.dvm.*;
import com.github.unidbg.linux.android.dvm.array.ArrayObject;
import com.github.unidbg.linux.android.dvm.array.ByteArray;
import com.github.unidbg.linux.android.dvm.wrapper.DvmInteger;
import com.github.unidbg.linux.android.dvm.wrapper.DvmLong;
import com.github.unidbg.memory.Memory;
import java.io.File;
import java.util.HashMap;
import java.util.Set;
public class MyAli extends AbstractJni implements IOResolver<AndroidFileIO> {
private final AndroidEmulator emulator;
private final VM vm;
Module module;
DalvikModule dm;
static public long slot;
private final DvmClass MYJNICLibrary;
private final boolean logging;
@Override
public FileResult<AndroidFileIO> resolve(Emulator<AndroidFileIO> emulator, String pathname, int oflags){
System.out.println("[files open]->"+pathname);
switch (pathname){
case "/data/app/com.rytong.ceair.apk":
return FileResult.success(emulator.getFileSystem().createSimpleFileIO(
new File("unidbg-android/src/test/java/com/taobao/wireless/security/adapter/JNICLibrary/rootfs", pathname), oflags, pathname));
}
return null;
}
public MyAli(boolean logging) {
this.logging = logging;
emulator=new AndroidARMEmulator("com.rytong.ceair");
final Memory memory = emulator.getMemory(); // 模拟器的内存操作接口
emulator.getSyscallHandler().addIOResolver(this);
memory.setLibraryResolver(new AndroidResolver(23)); // 设置系统类库解析
vm = emulator.createDalvikVM(new File("unidbg-android/src/test/java/com/taobao/wireless/security/adapter/JNICLibrary/donghang9.3.0.apk"));
vm.setVerbose(logging); // 设置是否打印Jni调用细节
vm.setJni(this);
MYJNICLibrary = vm.resolveClass("com/taobao/wireless/security/adapter/JNICLibrary");
}
void destroy() {
IOUtils.close(emulator);
if (logging) {
System.out.println("destroy");
}
}
public static void main(String[] args) throws Exception {
MyAli test = new MyAli(true);
test.Call_doCommandNative();
test.destroy();
}
void Call_doCommandNative(){
dm = vm.loadLibrary(new File("unidbg-android/src/test/java/com/taobao/wireless/security/adapter/JNICLibrary/libsgmainso-5.4.193.so"), true); // 加载libttEncrypt.so到unicorn虚拟内存,加载成功以后会默认调用init_array等函数
dm.callJNI_OnLoad(emulator); // 手动执行JNI_OnLoad函数
module = dm.getModule();
System.out.println("TAG Vison ------------------- [1] -------------------");
//【1】-10101 So初始化
ArrayObject initSo_arg=new ArrayObject(
vm.resolveClass("android/content/Context").newObject(null),
DvmInteger.valueOf(vm,3),
new StringObject(vm,""),
new StringObject(vm,"/data/user/0/com.rytong.ceair/app_SGLib"),
new StringObject(vm,"")
);
DvmObject<?> dvmObject_initSo = MYJNICLibrary.callStaticJniMethodObject(emulator, "doCommandNative(I[Ljava/lang/Object;)Ljava/lang/Object;", 10101,initSo_arg);
System.out.println("TAG Vison ----- 10101 initSo ----- [res]:"+dvmObject_initSo.getValue());
System.out.println("TAG Vison ------------------- [2] -------------------");
//【2】-10102 libsgmainso插件初始化
ArrayObject initSosgmain_arg=new ArrayObject(
new StringObject(vm,"main"),
new StringObject(vm,"5.4.193"),
new StringObject(vm,"/data/app/com.rytong.ceair-yoTJTWpoydDKBU49a55E_A==/lib/arm/libsgmainso-5.4.193.so")
);
DvmObject<?> dvmObject_initSosgmain = MYJNICLibrary.callStaticJniMethodObject(emulator, "doCommandNative(I[Ljava/lang/Object;)Ljava/lang/Object;", 10102,initSosgmain_arg);
System.out.println("TAG Vison ----- 10102 initSosgmain ----- [res]:"+dvmObject_initSosgmain.getValue());
System.out.println("TAG Vison ------------------- [2-3 load-so] -------------------");
DalvikModule dm1 = vm.loadLibrary(new File("unidbg-android/src/test/java/com/taobao/wireless/security/adapter/JNICLibrary/libsgsecuritybodyso-5.4.112.so"), true); // 加载libttEncrypt.so到unicorn虚拟内存,加载成功以后会默认调用init_array等函数
dm1.callJNI_OnLoad(emulator);
System.out.println("TAG Vison ------------------- [3] -------------------");
//【3】-10102 libsgsecuritybodyso插件初始化
ArrayObject initSosgsecuritybody_arg=new ArrayObject(
new StringObject(vm,"securitybody"),
new StringObject(vm,"5.4.112"),
new StringObject(vm,"/data/app/com.rytong.ceair-yoTJTWpoydDKBU49a55E_A==/lib/arm/libsgsecuritybodyso-5.4.112.so")
);
DvmObject<?> dvmObject_initSosgsecuritybody = MYJNICLibrary.callStaticJniMethodObject(emulator, "doCommandNative(I[Ljava/lang/Object;)Ljava/lang/Object;", 10102,initSosgsecuritybody_arg);
System.out.println("TAG Vison ----- 10102 initSosgsecuritybody ----- [res]:"+dvmObject_initSosgsecuritybody.getValue());
System.out.println("TAG Vison ------------------- [3-4 load-so] -------------------");
DalvikModule dm2 = vm.loadLibrary(new File("unidbg-android/src/test/java/com/taobao/wireless/security/adapter/JNICLibrary/libsgavmpso-5.4.1002.so"), true); // 加载libttEncrypt.so到unicorn虚拟内存,加载成功以后会默认调用init_array等函数
dm2.callJNI_OnLoad(emulator);
System.out.println("TAG Vison ------------------- [4] -------------------");
//【4】-10102 libsgavmpso插件初始化
ArrayObject initSosgavmp_arg=new ArrayObject(
new StringObject(vm,"avmp"),
new StringObject(vm,"5.4.1002"),
new StringObject(vm,"/data/user/0/com.rytong.ceair/app_SGLib/app_1682143210/main/libsgavmpso-5.4.1002.so")
);
DvmObject<?> dvmObject_initSosgavmp = MYJNICLibrary.callStaticJniMethodObject(emulator, "doCommandNative(I[Ljava/lang/Object;)Ljava/lang/Object;", 10102,initSosgavmp_arg);
System.out.println("TAG Vison ----- 10102 initSosgavmp ----- [res]:"+dvmObject_initSosgavmp.getValue());
System.out.println("TAG Vison ------------------- [5] -------------------");
//【5】-60901 AVMP初始化
ArrayObject initVmp_arg=new ArrayObject(
new StringObject(vm,"0335_mwua"),
new StringObject(vm,"sgcipher")
);
DvmObject<?> dvmObject_initVmp = MYJNICLibrary.callStaticJniMethodObject(emulator, "doCommandNative(I[Ljava/lang/Object;)Ljava/lang/Object;", 60901,initVmp_arg);
long createAVMPInstance = Long.valueOf(dvmObject_initVmp.getValue().toString());
createAVMPInstance=createAVMPInstance& 0xffffffffL;
System.out.println("TAG Vison ----- 60901 initVmp ----- [res]:"+createAVMPInstance);
//long createAVMPInstance=2242459650L;
System.out.println("TAG Vison ------------------- [6] -------------------");
//【6】-60902 wToken加密调用
String strbody = "{\"req\":\"S6TVWfiiBE2ZEXY9ldOr4oz9JB6+/EaSHqY1/vILbUs/6L2Eqv3e8m2QToNujniIPYeDZRK4Gr6fVX+hRS4f9aWHsJaevbhzM+qiHoS2nsFagR+T3pTsKJmkNRObOuYk0POOaSRogMRZ+1tkiG7RuzxfZ8fVZ47CKz6dGB1jsC2z4KGQDRp8iGkKlhzP65+DqgbazzCBhv3nFhKXFL/GtBnmJnoVktVmCGVp/tCMLmybMF+EniB7nejy3nlCoJ512ZOeuYNCWnYgz2KjnYr913ksgfGfewxGXJtLr8A3KjbGHAEAs/IOohWkoR8k+2X1+q4myAypJ+jh5cRj8ghYuz149+lGJan68aaZgeMOBYL1jdtAL71E8zPHCJ66Ap33flyIfK/D2SxzIaGvVjWttsMvCBTsd5xkqUiGgDOXCHb0MPez3c+fzBtg+LTsFbdNWBWdEKV+uVw/xJByHUncxmT/cT7cgQHt55qNvdULzpCYOFxh5tqQgFAs3lM27Y1Z6WYm5noXLO24gUoehhxCC2Rw/duiowt+yw2iHhi3UpLbjvGSudkDUyDIYb7ij7xpkIt6HD2O5avNJIBh2aYuRmcpcHPUQItbf/PoQwlB8BEy+tce6Pp7ZeOFUudo3yBOuWo2yP5KyKjL8nkstRDwKwjcplZPZfKwJQJvz+osen1oGdfyhseJEuBLGzHcc1g3pJbf9OqIoQ3iniQcne3IY7IB0Y5hWfMfgvCv5BbZjYD8Ofw5OkuvBOY7WKS0TuahsnucIVKtqhcy/C9NzAM9Zx1Ge2q+aK4zKjQJckgs6R4EXB4V+6ZlJx4rwFMXRs/WeJFE2TtIX83XND+KilCLvnI3BUfbDLAyvZk3e6EXaSDZtTxWGAr+sRrlk66dRZydCVe8Eu00bHTP7fV3MBcldb5RXoW3JAg0DyXJaPRUh7VL7w091OoUoW/9Kb0pbXjlent4Tvg/VKb5HBQ/BmV+HUcScDLm4ra7aPmYFR1v5SmXxRw1snKXgoM6Cu/pd1Z2epLsm2dqiaHO99B5bq853tKdtYDwXcXLh8Fr9MtyftqGy25cxVGK4sfzwvEAt9wzGX1xHKFROq4bJXEcFSDB2zifdx9QUjDIezIBiMNzg2nSYeAMsf/aymk8HnEAwPL7DjrvmzooFKI0IbVF+wT8mjsbAXmFyRLeuBQyKm9HSvNuoz7E9Z6xN8ZSnZyYpJ0KAovs59k9/HpHWMvXxK+7mjVDeUhk/LErE1d36LAxK0rAp10iwHqeXCPdwZr3+y/0/YKNgkXGV0IYrljD8X2ue13+cu3bMtDgaxACee0l57qzGr/bTcbW6RDzlwtZf/R8kNrvjTybLs+gwFl6wFHZbNxwJ3ED8k0Nxt/RO0ZBXdFtGJSQ+uppc5yh2OJJKXB3aYy7IsmCY8f02jI1qM/UfkGy3WGbToWtV0bEVV1SHIApX1+G10+9Lqc84JABPbwB26Zd+TljMcBCIzB2ltL/68kiId7EGlcUK3Y0C02XjVFGxqCz1+6Z/P+2IhpxzJCRfRWIXWImq76MfAIu3Xacmw9lLscd/pR9Saaj1/DMPSTU=\"}";
ArrayObject aryobj1=new ArrayObject(
DvmInteger.valueOf(vm,3),
new ByteArray(vm,strbody.getBytes()),
DvmInteger.valueOf(vm,strbody.length()),
new StringObject(vm,""),
new ByteArray(vm,new byte[4]),
DvmInteger.valueOf(vm,0)
);
ArrayObject aryobj2=new ArrayObject(
DvmLong.valueOf(vm,createAVMPInstance),
new StringObject(vm,"sign"),
vm.resolveClass("[B"),
aryobj1
);
DvmObject<?> dvmObject_entry = MYJNICLibrary.callStaticJniMethodObject(emulator, "doCommandNative(I[Ljava/lang/Object;)Ljava/lang/Object;", 60902,aryobj2); // 执行Jni方法
System.out.println("TAG Vison ----- 60902 wToken ----- [res]:"+dvmObject_entry);
}
@Override
public DvmObject<?> callObjectMethod(BaseVM vm, DvmObject<?> dvmObject, String signature, VarArg varArg) {
switch (signature){
case "android/content/Context->getPackageCodePath()Ljava/lang/String;":{
return new StringObject(vm, "/data/app/com.rytong.ceair.apk");
}
case "android/content/Context->getFilesDir()Ljava/io/File;":{
return vm.resolveClass("java/io/File").newObject(new File("/data/data/com.rytong.ceair/files"));
}
// 固定写法
case "java/io/File->getAbsolutePath()Ljava/lang/String;": {
return new StringObject(vm, ((File) dvmObject.getValue()).getAbsolutePath());
}
case "[B->getClass()Ljava/lang/Class;":{
return vm.resolveClass("[B");
}
case "android/app/ActivityThread->getSystemContext()Landroid/app/ContextImpl;":{
return vm.resolveClass("android/app/ContextImpl").newObject(null);
}
case "android/app/ContextImpl->getPackageManager()Landroid/content/pm/PackageManager;":{
return vm.resolveClass("android/content/pm/PackageManager").newObject(null);
}
case "android/app/ContextImpl->getSystemService(Ljava/lang/String;)Ljava/lang/Object;":{
String str1= (String) varArg.getObject(0).getValue();
System.out.println("[getSystemService str1]->"+str1);
return vm.resolveClass("android/net/wifi/WifiManager").newObject(null);
}
case "android/net/wifi/WifiManager->getConnectionInfo()Landroid/net/wifi/WifiInfo;":{
return vm.resolveClass("android/net/wifi/WifiInfo").newObject(null);
}
case "android/net/wifi/WifiInfo->getMacAddress()Ljava/lang/String;":{
return new StringObject(vm,"02:00:00:00:00:00");
}
case "java/util/HashMap->keySet()Ljava/util/Set;":{
HashMap<?,?> map = (HashMap<?, ?>) dvmObject.getValue();
return vm.resolveClass("java/util/Set").newObject(map.keySet());
}
case "java/util/Set->toArray()[Ljava/lang/Object;":{
Set<?> set= (Set<?>) dvmObject.getValue();
Object[] array=set.toArray();
DvmObject<?>[] objects=new DvmObject[array.length];
for(int i=0;i<array.length;i++){
if(array[i] instanceof String){
objects[i]=new StringObject(vm, (String) array[i]);
}else{
//throw new IllegalAccessException("array="+array[i]);
}
}
return new ArrayObject(objects);
}
case "java/util/HashMap->get(Ljava/lang/Object;)Ljava/lang/Object;":{
HashMap<?,?> map = (HashMap<?, ?>) dvmObject.getValue();
Object key = varArg.getObject(0).getValue();
Object obj = map.get(key);
if(obj instanceof String){
return new StringObject(vm, (String) obj);
}else{
//throw new IllegalAccessException("array="+obj);
}
}
}
return super.callObjectMethod(vm, dvmObject, signature, varArg);
}
@Override
public DvmObject<?> getObjectField(BaseVM vm, DvmObject<?> dvmObject, String signature) {
switch (signature){
case "android/content/pm/ApplicationInfo->nativeLibraryDir:Ljava/lang/String;": {
return new StringObject(vm, "/data/app/com.rytong.ceair-yoTJTWpoydDKBU49a55E_A==/lib/arm");
}
}
return super.getObjectField(vm, dvmObject, signature);
}
@Override
public void callStaticVoidMethod(BaseVM vm, DvmClass dvmClass, String signature, VarArg varArg) {
switch (signature){
case "com/alibaba/wireless/security/open/edgecomputing/ECMiscInfo->registerAppLifeCyCleCallBack()V": {
return;
}
}
super.callStaticVoidMethod(vm, dvmClass, signature, varArg);
}
@Override
public int callStaticIntMethod(BaseVM vm, DvmClass dvmClass, String signature, VarArg varArg) {
switch (signature){
case "com/alibaba/wireless/security/framework/utils/UserTrackMethodJniBridge->utAvaiable()I": {
return 1;
}
}
return super.callStaticIntMethod(vm, dvmClass, signature, varArg);
}
@Override
public DvmObject<?> newObject(BaseVM vm, DvmClass dvmClass, String signature, VarArg varArg) {
switch (signature){
// 固定写法
case "java/lang/Integer-><init>(I)V": {
int value = varArg.getInt(0);
return vm.resolveClass("java/lang/Integer").newObject(value);
}
case "java/lang/Long-><init>(J)V": {
int value = varArg.getInt(0);
return vm.resolveClass("java/lang/Long").newObject(value);
}
case "com/alibaba/wireless/security/open/SecException-><init>(Ljava/lang/String;I)V": {
int value = varArg.getInt(1);
System.out.println("[TAG-SecException]->"+value);
return vm.resolveClass("com/alibaba/wireless/security/open/SecException").newObject(value);
}
}
return super.newObject(vm, dvmClass, signature, varArg);
}
@Override
public long getStaticLongField(BaseVM vm, DvmClass dvmClass, String signature) {
switch (signature) {
case "com/alibaba/wireless/security/framework/SGPluginExtras->slot:J": {
return slot;
}
}
return super.getStaticLongField(vm, dvmClass, signature);
}
@Override
public void setStaticLongField(BaseVM vm, DvmClass dvmClass, String signature, long value) {
switch (signature) {
case "com/alibaba/wireless/security/framework/SGPluginExtras->slot:J": {
slot = value;
return;
}
}
super.setStaticLongField(vm, dvmClass, signature, value);
}
@Override
public int getStaticIntField(BaseVM vm, DvmClass dvmClass, String signature) {
switch (signature){
case"android/os/Build$VERSION->SDK_INT:I":{
return 23;
}
}
return super.getStaticIntField(vm, dvmClass, signature);
}
@Override
public DvmObject<?> callStaticObjectMethod(BaseVM vm, DvmClass dvmClass, String signature, VarArg varArg) {
switch (signature){
case"android/app/ActivityThread->currentPackageName()Ljava/lang/String;":{
return new StringObject(vm,"com.rytong.ceair");
}
case "android/app/ActivityThread->currentActivityThread()Landroid/app/ActivityThread;":{
return dvmClass.newObject(null);
}
case "android/os/SystemProperties->get(Ljava/lang/String;Ljava/lang/String;)Ljava/lang/String;":{
String str1= (String) varArg.getObject(0).getValue();
String res="";
System.out.println("[SystemProperties str1]->"+str1);
System.out.println("[SystemProperties str2]->"+varArg.getObject(1).getValue());
if(str1.indexOf("ro.serialno")!=-1){
res="94CX1Z56A";
}
return new StringObject(vm,res);
}
}
return super.callStaticObjectMethod(vm, dvmClass, signature, varArg);
}
@Override
public DvmObject<?> getStaticObjectField(BaseVM vm, DvmClass dvmClass, String signature) {
switch (signature){
case "android/os/Build->BRAND:Ljava/lang/String;":
return new StringObject(vm,"Ljava/lang/String;");
case "android/os/Build->MODEL:Ljava/lang/String;":
return new StringObject(vm,"Ljava/lang/String;");
case "android/os/Build$VERSION->RELEASE:Ljava/lang/String;":
return new StringObject(vm,"Ljava/lang/String;");
case "android/os/Build->DEVICE:Ljava/lang/String;":
return new StringObject(vm,"Ljava/lang/String;");
}
return super.getStaticObjectField(vm,dvmClass,signature);
}
}
package com.taobao.wireless.security.adapter.JNICLibrary;
import com.alibaba.fastjson.util.IOUtils;
import com.github.unidbg.AndroidEmulator;
import com.github.unidbg.Module;
import com.github.unidbg.Emulator;
import com.github.unidbg.file.FileResult;
import com.github.unidbg.file.IOResolver;
import com.github.unidbg.file.linux.AndroidFileIO;
import com.github.unidbg.linux.android.AndroidARMEmulator;
import com.github.unidbg.linux.android.AndroidResolver;
import com.github.unidbg.linux.android.dvm.*;
import com.github.unidbg.linux.android.dvm.array.ArrayObject;
import com.github.unidbg.linux.android.dvm.array.ByteArray;
import com.github.unidbg.linux.android.dvm.wrapper.DvmInteger;
import com.github.unidbg.linux.android.dvm.wrapper.DvmLong;
import com.github.unidbg.memory.Memory;
import java.io.File;
import java.util.HashMap;
import java.util.Set;
public class MyAli extends AbstractJni implements IOResolver<AndroidFileIO> {
private final AndroidEmulator emulator;
private final VM vm;
Module module;
DalvikModule dm;
static public long slot;
private final DvmClass MYJNICLibrary;
private final boolean logging;
@Override
public FileResult<AndroidFileIO> resolve(Emulator<AndroidFileIO> emulator, String pathname, int oflags){
System.out.println("[files open]->"+pathname);
switch (pathname){
case "/data/app/com.rytong.ceair.apk":
return FileResult.success(emulator.getFileSystem().createSimpleFileIO(
new File("unidbg-android/src/test/java/com/taobao/wireless/security/adapter/JNICLibrary/rootfs", pathname), oflags, pathname));
}
return null;
}
public MyAli(boolean logging) {
this.logging = logging;
emulator=new AndroidARMEmulator("com.rytong.ceair");
final Memory memory = emulator.getMemory(); // 模拟器的内存操作接口
emulator.getSyscallHandler().addIOResolver(this);
memory.setLibraryResolver(new AndroidResolver(23)); // 设置系统类库解析
[培训]Windows内核深度攻防:从Hook技术到Rootkit实战!
最后于 2023-4-26 12:35
被shmilyaxy编辑
,原因: 添加附件及说明