Windbg调试器单步异常,直接gn不处理。
DTrace
DTrace on Windows - Windows drivers
使用D语言编写监控
效果发现其检测内核调试器的存在。
使用Dtrace进行追踪
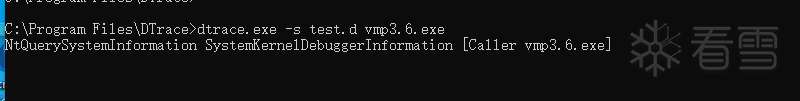
使用WinArk做inline hook。
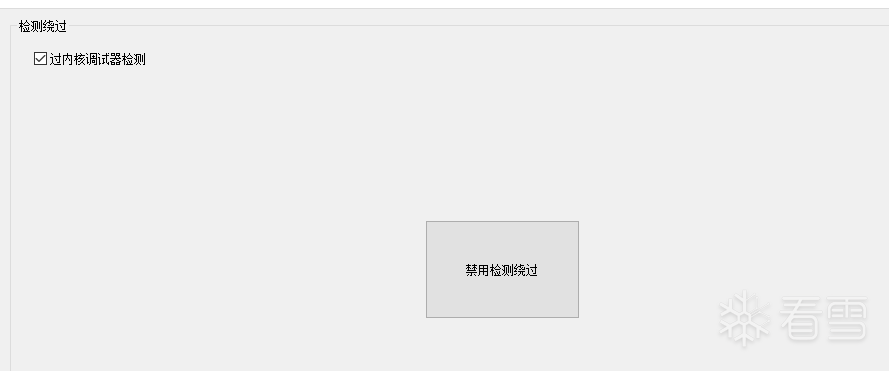
成功绕过vmp3.6 反内核调试器。
32.0: kd:x86> gn
The context is partially valid. Only x86 user-mode context is available.
WOW64 single step exception - code 4000001e (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
vmp3_6+0x4fa074:
00000000`008fa074 90 nop
32.0: kd:x86> ub
vmp3_6+0x4fa063:
00000000`008fa063 33d3 xor edx,ebx
00000000`008fa065 ffca dec edx
00000000`008fa067 41 inc ecx
00000000`008fa068 84d9 test cl,bl
00000000`008fa06a f7da neg edx
00000000`008fa06c e91832f0ff jmp vmp3_6+0x3fd289 (007fd289)
00000000`008fa071 9d popfd
00000000`008fa072 0f31 rdtsc
32.0: kd:x86> gn
32.0: kd:x86> gn
The context is partially valid. Only x86 user-mode context is available.
WOW64 single step exception - code 4000001e (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
vmp3_6+0x4fa074:
00000000`008fa074 90 nop
32.0: kd:x86> ub
vmp3_6+0x4fa063:
00000000`008fa063 33d3 xor edx,ebx
00000000`008fa065 ffca dec edx
00000000`008fa067 41 inc ecx
00000000`008fa068 84d9 test cl,bl
00000000`008fa06a f7da neg edx
00000000`008fa06c e91832f0ff jmp vmp3_6+0x3fd289 (007fd289)
00000000`008fa071 9d popfd
00000000`008fa072 0f31 rdtsc
32.0: kd:x86> gn
syscall::Nt*:entry
/ execname == $1 /
{
/*printf("%s [Caller %s]\n",probefunc, execname);*/
if(probefunc == "NtQuerySystemInformation") {
if(arg0 == 35){
printf("Detect Kernel Debugger\n");
}
}
if(probefunc == "NtQueryInformationProcess") {
if(arg1 == 0x7){
printf("Detect ProcessDebutPort\n");
}
if(arg1 == 0x1E){
printf("Detect ProcessDebugObjectHandle\n");
}
if(arg1 == 0x1F){
printf("Detect DebugFlags");
}
}
if(probefunc == "NtSetInformationThread"){
if(arg1 == 0x11){
printf("HideFromDebugger\n");
}
}
if(probefunc == "NtQueryInformationProcess"){
if(arg1 == 0){
printf("Query Process Basic Information \n");
}
}
if(probefunc == "NtQueryObject"){
if(arg1 == 2) {
printf("Query Object Type Information\n");
}
if(arg1 == 3) {
printf("Query Object Types Information\n");
}
}
if(probefunc == "NtClose") {
printf("Close Handle : 0x%x\n",arg0);
}
if(probefunc == "NtSetInformationObject") {
if(arg1 == 4){
printf("Set Handle Flag\n");
}
}
if(probefunc == "NtGetContextThread"){
printf("Get thread by thread handle : 0x%x",arg0);
}
if(probefunc == "NtYieldExecution") {
printf("NtYieldExecution\n");
}
if(probefunc == "DbgSetDebugFilterState") {
printf("DbgSetDebugFilterState\n");
}
}
syscall::Nt*:entry
/ execname == $1 /
{
/*printf("%s [Caller %s]\n",probefunc, execname);*/
if(probefunc == "NtQuerySystemInformation") {
if(arg0 == 35){
printf("Detect Kernel Debugger\n");
}
}
if(probefunc == "NtQueryInformationProcess") {
if(arg1 == 0x7){
printf("Detect ProcessDebutPort\n");
}
if(arg1 == 0x1E){
printf("Detect ProcessDebugObjectHandle\n");
}
if(arg1 == 0x1F){
printf("Detect DebugFlags");
}
}
if(probefunc == "NtSetInformationThread"){
if(arg1 == 0x11){
printf("HideFromDebugger\n");
}
}
if(probefunc == "NtQueryInformationProcess"){
if(arg1 == 0){
printf("Query Process Basic Information \n");
}
}
if(probefunc == "NtQueryObject"){
if(arg1 == 2) {
printf("Query Object Type Information\n");
}
[注意]传递专业知识、拓宽行业人脉——看雪讲师团队等你加入!