-
-
[原创]某应用sign签名算法还原
-
发表于: 2022-1-7 17:26 33067
-
首先使用jadx对apk进行逆向
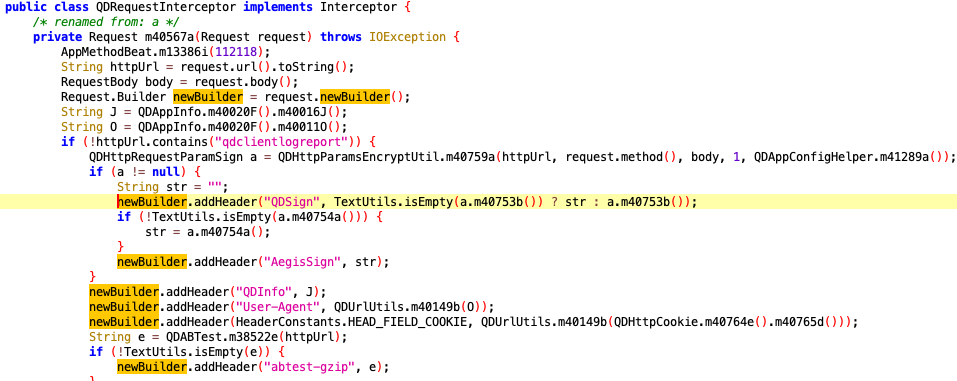
搜索关键字 QDSign,可以直接找到对应的类,可以看到参数经过加密得到
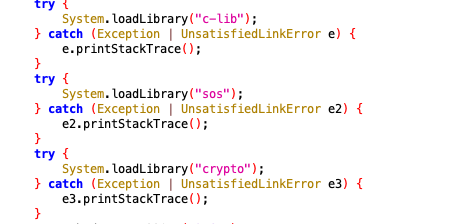
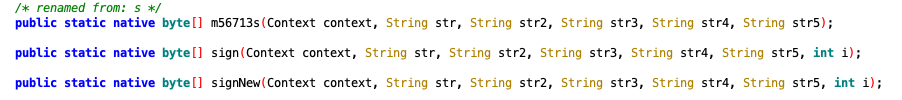
进一步跟踪,发现了c类中有如下三个so方法,还有3个loadlibrary,分别进行了hook,发现c-lib动态注册了sign,sos动态注册了s,没有发现crypto有动态注册,使用frida对3个so函数进行了hook,证实sign是QDSign的加密函数,s是AegisSign的加密函数,SignNew并没有调用,搜索java代码,也没有发现调用的地方,猜测可能该函数没有实现,暂时不管了。
先用frida进行hook看看返回结果
确认结果确实为QDSign的值
通过 jnitrace -l libsos.so 包名 -i RegisterNatives 可以看到是动态注册的函数
直接再执行 jnitrace -l libsos.so 包名 发现程序卡在了闪屏页,原因不明,这种方法在很多应用上都会这样,有大神知道原因吗?
换成程序启动后,进行attach的方式, jnitrace -l libc-lib.so 应用名 -m attach ,貌似没有结果,这个方法在自己的程序上可以正常获取trace,但是在最近逆向的应用上都没有任何输出,原因不明,有没有知道的大佬解答一下?
祭出unidbg大杀器试试,使用模拟23版本,会报错
报以上错误,猜想是不是用的applcationContext、看了下日志,替换为android/content/ContextWrapper后,继续执行,又报错
搜了一圈,没找到有用的信息。
最后想不到办法了,抱着侥幸心理、死马当活马医,换成19版本。。!!!居然成功了!!!
模拟执行sign方法,得到如下结果
观察在sign方法中获取了参数、版本号、签名,然后进行了两次md5,最后输出了一个128位的字节数组,经过测试,两个md5分别为对请求参加md5,对签名进行md5。
sign函数返回的是字节数组,看了下jadx解析出来的工具类的名字为Base64Util,遂想到先用android的Base64一下,看看结果如何。可以看出,应用的base64函数做过特殊处理,在中间插入了两个空格,看来需要直接使用它原来的方法比较好。
此时需要逆向 包名.core.util.e(这个类是Base64Util)下的public static String m39789a(byte[] bArr)函数,可以看出,该函数逻辑恢复不正确;
于是通过jadx的信息,定位该dex位于classes3.dex中,通过dex2jar,获得了对应的jar压缩包;
由于压缩包中其他的类,并不是本次关注对象,单独提取 包名.core.util.e.class,扔到在线反编译网站,选择Procyon引擎进行逆向后得到
通过该函数解析字节数组,得到了最终的加密参数。
下面该还原so中的具体加密细节了。
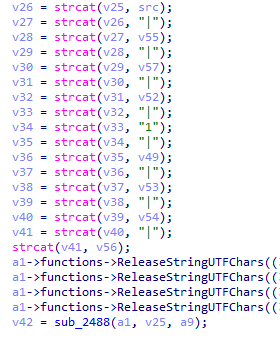
打开IDA查看函数,通过unidbg模拟可以看到动态注册函数位置位于0x25a9,查看伪代码,可以看到对参数进行了拼接
这些参数通过对比unidbg日志,除了src不知道是什么,其余都对应上了,那接下来,hook下strcat
可以得出src的值
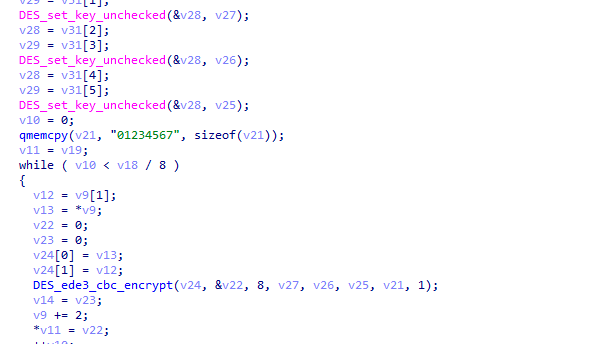
再往下分析,得出2488函数是最终进行加密的函数,继续跟进,看到如下代码
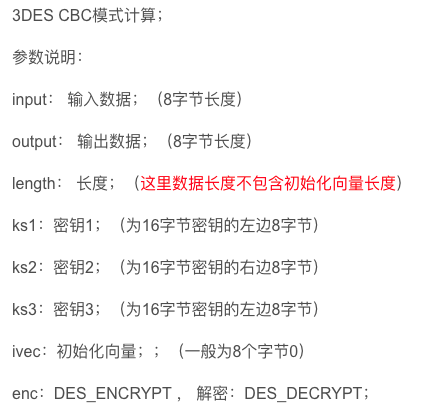
可以看到DES_ede3_cbc_encrypt关键字,搜索google,发现有一个openssl库一模一样的函数,参数个数也对应上了,
得出v24是输入参数,v27、v26、v25分别为秘钥1、2、3,v21为初始化向量。懒得找一个openssl库来实验了,我先想办法得到秘钥,向量已经在代码中看到了,既是01234567。
hook函数DES_ede3_cbc_encrypt
结果如下
看这个日志输出,三个秘钥都不相同,看不出是个啥,往回看秘钥来源于0xb88函数,hook这个函数
得到了一个字符串,搜索google找到DES_ede3_cbc_encrypt对应的java方法实验一下
然后把两个字节比较之后发现一模一样,说明秘钥正确。
到此算法分析结束。
C0025c.sign.implementation = function(v1,v2,v3,v4,v5,v6,v7) { var ret = this.sign(v1,v2,v3,v4,v5,v6,v7) console.log("sign params:", v1,v2,v3,v4,v5,v6,v7); console.log("sign:", Base64Util.a(ret)); return ret; }C0025c.sign.implementation = function(v1,v2,v3,v4,v5,v6,v7) { var ret = this.sign(v1,v2,v3,v4,v5,v6,v7) console.log("sign params:", v1,v2,v3,v4,v5,v6,v7); console.log("sign:", Base64Util.a(ret)); return ret; }JNIEnv->FindClass(android/content/ContextWrapper) was called from RX@0x40002629[libc-lib.so]0x2629JNIEnv->GetMethodID(android/content/ContextWrapper.getPackageManager()Landroid/content/pm/PackageManager;) => 0x53f2c391 was called from RX@0x4000263f[libc-lib.so]0x263f[14:16:09 117] WARN [com.github.unidbg.linux.ARM32SyscallHandler] (ARM32SyscallHandler:530) - handleInterrupt intno=2, NR=-1073744244, svcNumber=0x11f, PC=unidbg@0xfffe0284, LR=RX@0x40000af5[libc-lib.so]0xaf5, syscall=nullcom.github.unidbg.arm.backend.BackendException: dvmObject=android.content.Context@5f2050f6, dvmClass=class android/content/Context, jmethodID=unidbg@0x53f2c391JNIEnv->FindClass(android/content/ContextWrapper) was called from RX@0x40002629[libc-lib.so]0x2629JNIEnv->GetMethodID(android/content/ContextWrapper.getPackageManager()Landroid/content/pm/PackageManager;) => 0x53f2c391 was called from RX@0x4000263f[libc-lib.so]0x263f[14:16:09 117] WARN [com.github.unidbg.linux.ARM32SyscallHandler] (ARM32SyscallHandler:530) - handleInterrupt intno=2, NR=-1073744244, svcNumber=0x11f, PC=unidbg@0xfffe0284, LR=RX@0x40000af5[libc-lib.so]0xaf5, syscall=nullcom.github.unidbg.arm.backend.BackendException: dvmObject=android.content.Context@5f2050f6, dvmClass=class android/content/Context, jmethodID=unidbg@0x53f2c391Invalid address 0x40344000 passed to free: value not allocated[crash]A/libc: Invalid address 0x40344000 passed to free: value not allocatedException in thread "main" java.lang.NullPointerExceptionInvalid address 0x40344000 passed to free: value not allocated[crash]A/libc: Invalid address 0x40344000 passed to free: value not allocatedException in thread "main" java.lang.NullPointerExceptionJNIEnv->FindClass(a/c) was called from RX@0x40000b57[libc-lib.so]0xb57JNIEnv->RegisterNatives(a/c, RW@0x40007000[libc-lib.so]0x7000, 1) was called from RX@0x40000b6d[libc-lib.so]0xb6dRegisterNative(a/c, sign(Landroid/content/Context;Ljava/lang/String;Ljava/lang/String;Ljava/lang/String;Ljava/lang/String;Ljava/lang/String;I)[B, RX@0x400025a9[libc-lib.so]0x25a9)Find native function Java_a_c_sign => RX@0x400025a9[libc-lib.so]0x25a9JNIEnv->GetStringUtfChars("bookid=1021617576&isoutbook=0") was called from RX@0x40002519[libc-lib.so]0x2519JNIEnv->ReleaseStringUTFChars("bookid=1021617576&isoutbook=0") was called from RX@0x4000257f[libc-lib.so]0x257fJNIEnv->NewStringUTF("bf0fd95eb2cf2d1750cb5ff9364c5f49") was called from RX@0x4000258d[libc-lib.so]0x258dJNIEnv->GetStringUtfChars("bf0fd95eb2cf2d1750cb5ff9364c5f49") was called from RX@0x400025cf[libc-lib.so]0x25cfJNIEnv->GetStringUtfChars("1641450591209") was called from RX@0x400025df[libc-lib.so]0x25dfJNIEnv->GetStringUtfChars("0") was called from RX@0x400025fb[libc-lib.so]0x25fbJNIEnv->GetStringUtfChars("9e450ea5f3dd0b8a") was called from RX@0x4000260b[libc-lib.so]0x260bJNIEnv->GetStringUtfChars("0") was called from RX@0x4000261b[libc-lib.so]0x261bJNIEnv->FindClass(android/content/ContextWrapper) was called from RX@0x40002629[libc-lib.so]0x2629JNIEnv->GetMethodID(android/content/ContextWrapper.getPackageManager()Landroid/content/pm/PackageManager;) => 0x53f2c391 was called from RX@0x4000263f[libc-lib.so]0x263fJNIEnv->CallObjectMethodV(android.content.ContextWrapper@26ba2a48, getPackageManager() => android.content.pm.PackageManager@17550481) was called from RX@0x40000af5[libc-lib.so]0xaf5JNIEnv->GetMethodID(android/content/ContextWrapper.getPackageName()Ljava/lang/String;) => 0x8bcc2d71 was called from RX@0x40002665[libc-lib.so]0x2665JNIEnv->CallObjectMethodV(android.content.ContextWrapper@26ba2a48, getPackageName() => "com.xx") was called from RX@0x40000af5[libc-lib.so]0xaf5JNIEnv->GetMethodID(android/content/pm/PackageManager.getPackageInfo(Ljava/lang/String;I)Landroid/content/pm/PackageInfo;) => 0x3bca8377 was called from RX@0x4000268f[libc-lib.so]0x268fJNIEnv->CallObjectMethodV(android.content.pm.PackageManager@17550481, getPackageInfo("com.xx", 0x40) => android.content.pm.PackageInfo@180bc464) was called from RX@0x40000af5[libc-lib.so]0xaf5JNIEnv->GetFieldID(android/content/pm/PackageInfo.versionName Ljava/lang/String;) => 0xbcc0232a was called from RX@0x400026c5[libc-lib.so]0x26c5JNIEnv->GetObjectField(android.content.pm.PackageInfo@180bc464, versionName Ljava/lang/String; => "7.9.178") was called from RX@0x400026d3[libc-lib.so]0x26d3JNIEnv->GetStringUtfChars("7.9.178") was called from RX@0x400026e3[libc-lib.so]0x26e3JNIEnv->GetFieldID(android/content/pm/PackageInfo.signatures [Landroid/content/pm/Signature;) => 0x25f17218 was called from RX@0x400026fb[libc-lib.so]0x26fbJNIEnv->GetObjectField(android.content.pm.PackageInfo@180bc464, signatures [Landroid/content/pm/Signature; => [android.content.pm.Signature@3a82f6ef]) was called from RX@0x4000270b[libc-lib.so]0x270bJNIEnv->GetArrayLength([android.content.pm.Signature@3a82f6ef] => 1) was called from RX@0x40002719[libc-lib.so]0x2719JNIEnv->GetObjectArrayElement([android.content.pm.Signature@3a82f6ef], 0) => android.content.pm.Signature@3a82f6ef was called from RX@0x40002727[libc-lib.so]0x2727JNIEnv->GetMethodID(android/content/pm/Signature.toCharsString()Ljava/lang/String;) => 0x7a908191 was called from RX@0x40002745[libc-lib.so]0x2745JNIEnv->CallObjectMethodV(android.content.pm.Signature@3a82f6ef, toCharsString() => "308202253082018ea00302010202044e239460300d06092a864886f70d0101050500305731173015060355040a0c0ec386c3b0c2b5c3a3c396c390c38e311d301b060355040b0c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8311d301b06035504030c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8301e170d3131303731383032303331325a170d3431303731303032303331325a305731173015060355040a0c0ec386c3b0c2b5c3a3c396c390c38e311d301b060355040b0c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8311d301b06035504030c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b830819f300d06092a864886f70d010101050003818d0030818902818100a3d47f8bfd8d54de1dfbc40a9caa88a43845e287e8f40da2056be126b17233669806bfa60799b3d1364e79a78f355fd4f72278650b377e5acc317ff4b2b3821351bcc735543dab0796c716f769c3a28fedc3bca7780e5fff6c87779f3f3cdec6e888b4d21de27df9e7c21fc8a8d9164bfafac6df7d843e59b88ec740fc52a3c50203010001300d06092a864886f70d0101050500038181001f7946581b8812961a383b2d860b89c3f79002d46feb96f2a505bdae57097a070f3533c42fc3e329846886281a2fbd5c87685f59ab6dd71cc98af24256d2fbf980ded749e2c35eb0151ffde993193eace0b4681be4bcee5f663dd71dd06ab64958e02a60d6a69f21290cb496dd8784a4c31ebadb1b3cc5cb0feebdaa2f686ee2") was called from RX@0x40000af5[libc-lib.so]0xaf5JNIEnv->GetStringUtfChars("308202253082018ea00302010202044e239460300d06092a864886f70d0101050500305731173015060355040a0c0ec386c3b0c2b5c3a3c396c390c38e311d301b060355040b0c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8311d301b06035504030c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8301e170d3131303731383032303331325a170d3431303731303032303331325a305731173015060355040a0c0ec386c3b0c2b5c3a3c396c390c38e311d301b060355040b0c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8311d301b06035504030c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b830819f300d06092a864886f70d010101050003818d0030818902818100a3d47f8bfd8d54de1dfbc40a9caa88a43845e287e8f40da2056be126b17233669806bfa60799b3d1364e79a78f355fd4f72278650b377e5acc317ff4b2b3821351bcc735543dab0796c716f769c3a28fedc3bca7780e5fff6c87779f3f3cdec6e888b4d21de27df9e7c21fc8a8d9164bfafac6df7d843e59b88ec740fc52a3c50203010001300d06092a864886f70d0101050500038181001f7946581b8812961a383b2d860b89c3f79002d46feb96f2a505bdae57097a070f3533c42fc3e329846886281a2fbd5c87685f59ab6dd71cc98af24256d2fbf980ded749e2c35eb0151ffde993193eace0b4681be4bcee5f663dd71dd06ab64958e02a60d6a69f21290cb496dd8784a4c31ebadb1b3cc5cb0feebdaa2f686ee2") was called from RX@0x40002519[libc-lib.so]0x2519JNIEnv->ReleaseStringUTFChars("308202253082018ea00302010202044e239460300d06092a864886f70d0101050500305731173015060355040a0c0ec386c3b0c2b5c3a3c396c390c38e311d301b060355040b0c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8311d301b06035504030c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8301e170d3131303731383032303331325a170d3431303731303032303331325a305731173015060355040a0c0ec386c3b0c2b5c3a3c396c390c38e311d301b060355040b0c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8311d301b06035504030c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b830819f300d06092a864886f70d010101050003818d0030818902818100a3d47f8bfd8d54de1dfbc40a9caa88a43845e287e8f40da2056be126b17233669806bfa60799b3d1364e79a78f355fd4f72278650b377e5acc317ff4b2b3821351bcc735543dab0796c716f769c3a28fedc3bca7780e5fff6c87779f3f3cdec6e888b4d21de27df9e7c21fc8a8d9164bfafac6df7d843e59b88ec740fc52a3c50203010001300d06092a864886f70d0101050500038181001f7946581b8812961a383b2d860b89c3f79002d46feb96f2a505bdae57097a070f3533c42fc3e329846886281a2fbd5c87685f59ab6dd71cc98af24256d2fbf980ded749e2c35eb0151ffde993193eace0b4681be4bcee5f663dd71dd06ab64958e02a60d6a69f21290cb496dd8784a4c31ebadb1b3cc5cb0feebdaa2f686ee2") was called from RX@0x4000257f[libc-lib.so]0x257fJNIEnv->NewStringUTF("f189adc92b816b3e9da29ea304d4a7e4") was called from RX@0x4000258d[libc-lib.so]0x258dJNIEnv->GetStringUtfChars("f189adc92b816b3e9da29ea304d4a7e4") was called from RX@0x40002767[libc-lib.so]0x2767JNIEnv->ReleaseStringUTFChars("0") was called from RX@0x400027e1[libc-lib.so]0x27e1JNIEnv->ReleaseStringUTFChars("9e450ea5f3dd0b8a") was called from RX@0x400027ef[libc-lib.so]0x27efJNIEnv->ReleaseStringUTFChars("0") was called from RX@0x400027fd[libc-lib.so]0x27fdJNIEnv->ReleaseStringUTFChars("7.9.178") was called from RX@0x4000280b[libc-lib.so]0x280bJNIEnv->NewByteArray(128) was called from RX@0x400024b9[libc-lib.so]0x24b9JNIEnv->SetByteArrayRegion([B@2a5ca609, 0, 128, unidbg@0x8048d38) was called from RX@0x400024cf[libc-lib.so]0x24cfJNIEnv->ReleaseStringUTFChars("bf0fd95eb2cf2d1750cb5ff9364c5f49") was called from RX@0x4000283d[libc-lib.so]0x283dJNIEnv->ReleaseStringUTFChars("f189adc92b816b3e9da29ea304d4a7e4") was called from RX@0x4000284d[libc-lib.so]0x284dJNIEnv->FindClass(a/c) was called from RX@0x40000b57[libc-lib.so]0xb57JNIEnv->RegisterNatives(a/c, RW@0x40007000[libc-lib.so]0x7000, 1) was called from RX@0x40000b6d[libc-lib.so]0xb6dRegisterNative(a/c, sign(Landroid/content/Context;Ljava/lang/String;Ljava/lang/String;Ljava/lang/String;Ljava/lang/String;Ljava/lang/String;I)[B, RX@0x400025a9[libc-lib.so]0x25a9)Find native function Java_a_c_sign => RX@0x400025a9[libc-lib.so]0x25a9JNIEnv->GetStringUtfChars("bookid=1021617576&isoutbook=0") was called from RX@0x40002519[libc-lib.so]0x2519JNIEnv->ReleaseStringUTFChars("bookid=1021617576&isoutbook=0") was called from RX@0x4000257f[libc-lib.so]0x257fJNIEnv->NewStringUTF("bf0fd95eb2cf2d1750cb5ff9364c5f49") was called from RX@0x4000258d[libc-lib.so]0x258dJNIEnv->GetStringUtfChars("bf0fd95eb2cf2d1750cb5ff9364c5f49") was called from RX@0x400025cf[libc-lib.so]0x25cfJNIEnv->GetStringUtfChars("1641450591209") was called from RX@0x400025df[libc-lib.so]0x25dfJNIEnv->GetStringUtfChars("0") was called from RX@0x400025fb[libc-lib.so]0x25fbJNIEnv->GetStringUtfChars("9e450ea5f3dd0b8a") was called from RX@0x4000260b[libc-lib.so]0x260bJNIEnv->GetStringUtfChars("0") was called from RX@0x4000261b[libc-lib.so]0x261bJNIEnv->FindClass(android/content/ContextWrapper) was called from RX@0x40002629[libc-lib.so]0x2629JNIEnv->GetMethodID(android/content/ContextWrapper.getPackageManager()Landroid/content/pm/PackageManager;) => 0x53f2c391 was called from RX@0x4000263f[libc-lib.so]0x263fJNIEnv->CallObjectMethodV(android.content.ContextWrapper@26ba2a48, getPackageManager() => android.content.pm.PackageManager@17550481) was called from RX@0x40000af5[libc-lib.so]0xaf5JNIEnv->GetMethodID(android/content/ContextWrapper.getPackageName()Ljava/lang/String;) => 0x8bcc2d71 was called from RX@0x40002665[libc-lib.so]0x2665JNIEnv->CallObjectMethodV(android.content.ContextWrapper@26ba2a48, getPackageName() => "com.xx") was called from RX@0x40000af5[libc-lib.so]0xaf5JNIEnv->GetMethodID(android/content/pm/PackageManager.getPackageInfo(Ljava/lang/String;I)Landroid/content/pm/PackageInfo;) => 0x3bca8377 was called from RX@0x4000268f[libc-lib.so]0x268fJNIEnv->CallObjectMethodV(android.content.pm.PackageManager@17550481, getPackageInfo("com.xx", 0x40) => android.content.pm.PackageInfo@180bc464) was called from RX@0x40000af5[libc-lib.so]0xaf5JNIEnv->GetFieldID(android/content/pm/PackageInfo.versionName Ljava/lang/String;) => 0xbcc0232a was called from RX@0x400026c5[libc-lib.so]0x26c5JNIEnv->GetObjectField(android.content.pm.PackageInfo@180bc464, versionName Ljava/lang/String; => "7.9.178") was called from RX@0x400026d3[libc-lib.so]0x26d3JNIEnv->GetStringUtfChars("7.9.178") was called from RX@0x400026e3[libc-lib.so]0x26e3JNIEnv->GetFieldID(android/content/pm/PackageInfo.signatures [Landroid/content/pm/Signature;) => 0x25f17218 was called from RX@0x400026fb[libc-lib.so]0x26fbJNIEnv->GetObjectField(android.content.pm.PackageInfo@180bc464, signatures [Landroid/content/pm/Signature; => [android.content.pm.Signature@3a82f6ef]) was called from RX@0x4000270b[libc-lib.so]0x270bJNIEnv->GetArrayLength([android.content.pm.Signature@3a82f6ef] => 1) was called from RX@0x40002719[libc-lib.so]0x2719JNIEnv->GetObjectArrayElement([android.content.pm.Signature@3a82f6ef], 0) => android.content.pm.Signature@3a82f6ef was called from RX@0x40002727[libc-lib.so]0x2727JNIEnv->GetMethodID(android/content/pm/Signature.toCharsString()Ljava/lang/String;) => 0x7a908191 was called from RX@0x40002745[libc-lib.so]0x2745JNIEnv->CallObjectMethodV(android.content.pm.Signature@3a82f6ef, toCharsString() => "308202253082018ea00302010202044e239460300d06092a864886f70d0101050500305731173015060355040a0c0ec386c3b0c2b5c3a3c396c390c38e311d301b060355040b0c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8311d301b06035504030c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8301e170d3131303731383032303331325a170d3431303731303032303331325a305731173015060355040a0c0ec386c3b0c2b5c3a3c396c390c38e311d301b060355040b0c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8311d301b06035504030c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b830819f300d06092a864886f70d010101050003818d0030818902818100a3d47f8bfd8d54de1dfbc40a9caa88a43845e287e8f40da2056be126b17233669806bfa60799b3d1364e79a78f355fd4f72278650b377e5acc317ff4b2b3821351bcc735543dab0796c716f769c3a28fedc3bca7780e5fff6c87779f3f3cdec6e888b4d21de27df9e7c21fc8a8d9164bfafac6df7d843e59b88ec740fc52a3c50203010001300d06092a864886f70d0101050500038181001f7946581b8812961a383b2d860b89c3f79002d46feb96f2a505bdae57097a070f3533c42fc3e329846886281a2fbd5c87685f59ab6dd71cc98af24256d2fbf980ded749e2c35eb0151ffde993193eace0b4681be4bcee5f663dd71dd06ab64958e02a60d6a69f21290cb496dd8784a4c31ebadb1b3cc5cb0feebdaa2f686ee2") was called from RX@0x40000af5[libc-lib.so]0xaf5JNIEnv->GetStringUtfChars("308202253082018ea00302010202044e239460300d06092a864886f70d0101050500305731173015060355040a0c0ec386c3b0c2b5c3a3c396c390c38e311d301b060355040b0c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8311d301b06035504030c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8301e170d3131303731383032303331325a170d3431303731303032303331325a305731173015060355040a0c0ec386c3b0c2b5c3a3c396c390c38e311d301b060355040b0c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8311d301b06035504030c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b830819f300d06092a864886f70d010101050003818d0030818902818100a3d47f8bfd8d54de1dfbc40a9caa88a43845e287e8f40da2056be126b17233669806bfa60799b3d1364e79a78f355fd4f72278650b377e5acc317ff4b2b3821351bcc735543dab0796c716f769c3a28fedc3bca7780e5fff6c87779f3f3cdec6e888b4d21de27df9e7c21fc8a8d9164bfafac6df7d843e59b88ec740fc52a3c50203010001300d06092a864886f70d0101050500038181001f7946581b8812961a383b2d860b89c3f79002d46feb96f2a505bdae57097a070f3533c42fc3e329846886281a2fbd5c87685f59ab6dd71cc98af24256d2fbf980ded749e2c35eb0151ffde993193eace0b4681be4bcee5f663dd71dd06ab64958e02a60d6a69f21290cb496dd8784a4c31ebadb1b3cc5cb0feebdaa2f686ee2") was called from RX@0x40002519[libc-lib.so]0x2519JNIEnv->ReleaseStringUTFChars("308202253082018ea00302010202044e239460300d06092a864886f70d0101050500305731173015060355040a0c0ec386c3b0c2b5c3a3c396c390c38e311d301b060355040b0c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8311d301b06035504030c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8301e170d3131303731383032303331325a170d3431303731303032303331325a305731173015060355040a0c0ec386c3b0c2b5c3a3c396c390c38e311d301b060355040b0c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b8311d301b06035504030c14c386c3b0c2b5c3a3c396c390c38ec384c38dc3b830819f300d06092a864886f70d010101050003818d0030818902818100a3d47f8bfd8d54de1dfbc40a9caa88a43845e287e8f40da2056be126b17233669806bfa60799b3d1364e79a78f355fd4f72278650b377e5acc317ff4b2b3821351bcc735543dab0796c716f769c3a28fedc3bca7780e5fff6c87779f3f3cdec6e888b4d21de27df9e7c21fc8a8d9164bfafac6df7d843e59b88ec740fc52a3c50203010001300d06092a864886f70d0101050500038181001f7946581b8812961a383b2d860b89c3f79002d46feb96f2a505bdae57097a070f3533c42fc3e329846886281a2fbd5c87685f59ab6dd71cc98af24256d2fbf980ded749e2c35eb0151ffde993193eace0b4681be4bcee5f663dd71dd06ab64958e02a60d6a69f21290cb496dd8784a4c31ebadb1b3cc5cb0feebdaa2f686ee2") was called from RX@0x4000257f[libc-lib.so]0x257fJNIEnv->NewStringUTF("f189adc92b816b3e9da29ea304d4a7e4") was called from RX@0x4000258d[libc-lib.so]0x258dJNIEnv->GetStringUtfChars("f189adc92b816b3e9da29ea304d4a7e4") was called from RX@0x40002767[libc-lib.so]0x2767JNIEnv->ReleaseStringUTFChars("0") was called from RX@0x400027e1[libc-lib.so]0x27e1JNIEnv->ReleaseStringUTFChars("9e450ea5f3dd0b8a") was called from RX@0x400027ef[libc-lib.so]0x27efJNIEnv->ReleaseStringUTFChars("0") was called from RX@0x400027fd[libc-lib.so]0x27fdJNIEnv->ReleaseStringUTFChars("7.9.178") was called from RX@0x4000280b[libc-lib.so]0x280bJNIEnv->NewByteArray(128) was called from RX@0x400024b9[libc-lib.so]0x24b9JNIEnv->SetByteArrayRegion([B@2a5ca609, 0, 128, unidbg@0x8048d38) was called from RX@0x400024cf[libc-lib.so]0x24cfJNIEnv->ReleaseStringUTFChars("bf0fd95eb2cf2d1750cb5ff9364c5f49") was called from RX@0x4000283d[libc-lib.so]0x283dJNIEnv->ReleaseStringUTFChars("f189adc92b816b3e9da29ea304d4a7e4") was called from RX@0x4000284d[libc-lib.so]0x284d//m39789a(ret.getValue())R7TCs6Tou2X528j+NblfBuhFR2mLg5WEyNivv5UU4IC0wPHa6I06PG69U9DL 3dCj1aYsauB5Fkf6kQJy57OjgGSf2EXDkAcm2Rvoe8vyU7K+oimgA0khxrjZ Tqqj7rjhmQzKcbXBnRQDC3cssqP8oyU0V/kcuXoJmeS5vvMPB8o=//Base64Android.encode(ret.getValue(),2)R7TCs6Tou2X528j+NblfBuhFR2mLg5WEyNivv5UU4IC0wPHa6I06PG69U9DL3dCj1aYsauB5Fkf6kQJy57OjgGSf2EXDkAcm2Rvoe8vyU7K+oimgA0khxrjZTqqj7rjhmQzKcbXBnRQDC3cssqP8oyU0V/kcuXoJmeS5vvMPB8o=//m39789a(ret.getValue())R7TCs6Tou2X528j+NblfBuhFR2mLg5WEyNivv5UU4IC0wPHa6I06PG69U9DL 3dCj1aYsauB5Fkf6kQJy57OjgGSf2EXDkAcm2Rvoe8vyU7K+oimgA0khxrjZ Tqqj7rjhmQzKcbXBnRQDC3cssqP8oyU0V/kcuXoJmeS5vvMPB8o=//Base64Android.encode(ret.getValue(),2)R7TCs6Tou2X528j+NblfBuhFR2mLg5WEyNivv5UU4IC0wPHa6I06PG69U9DL3dCj1aYsauB5Fkf6kQJy57OjgGSf2EXDkAcm2Rvoe8vyU7K+oimgA0khxrjZTqqj7rjhmQzKcbXBnRQDC3cssqP8oyU0V/kcuXoJmeS5vvMPB8o=public static String m39789a(byte[] bArr) { AppMethodBeat.m13386i(132653); int length = bArr.length; StringBuilder sb = new StringBuilder((bArr.length * 3) / 2); int i = length - 3; int i2 = 0; loop0: while (true) { int i3 = 0; while (i2 <= i) { int i4 = ((bArr[i2] & UByte.MAX_VALUE) << 16) | ((bArr[i2 + 1] & UByte.MAX_VALUE) << 8) | (bArr[i2 + 2] & UByte.MAX_VALUE); char[] cArr = f14341a; sb.append(cArr[(i4 >> 18) & 63]); sb.append(cArr[(i4 >> 12) & 63]); sb.append(cArr[(i4 >> 6) & 63]); sb.append(cArr[i4 & 63]); i2 += 3; int i5 = i3 + 1; if (i3 >= 14) { break; } i3 = i5; } sb.append(" "); } int i6 = 0 + length; if (i2 == i6 - 2) { int i7 = ((bArr[i2 + 1] & UByte.MAX_VALUE) << 8) | ((bArr[i2] & UByte.MAX_VALUE) << 16); char[] cArr2 = f14341a; sb.append(cArr2[(i7 >> 18) & 63]); sb.append(cArr2[(i7 >> 12) & 63]); sb.append(cArr2[(i7 >> 6) & 63]); sb.append(ContainerUtils.KEY_VALUE_DELIMITER); } else if (i2 == i6 - 1) { int i8 = (bArr[i2] & UByte.MAX_VALUE) << 16; char[] cArr3 = f14341a; sb.append(cArr3[(i8 >> 18) & 63]); sb.append(cArr3[(i8 >> 12) & 63]); sb.append("=="); } String sb2 = sb.toString(); AppMethodBeat.m13385o(132653); return sb2; }public static String m39789a(byte[] bArr) { AppMethodBeat.m13386i(132653); int length = bArr.length; StringBuilder sb = new StringBuilder((bArr.length * 3) / 2); int i = length - 3; int i2 = 0; loop0: while (true) { int i3 = 0; while (i2 <= i) { int i4 = ((bArr[i2] & UByte.MAX_VALUE) << 16) | ((bArr[i2 + 1] & UByte.MAX_VALUE) << 8) | (bArr[i2 + 2] & UByte.MAX_VALUE); char[] cArr = f14341a; sb.append(cArr[(i4 >> 18) & 63]); sb.append(cArr[(i4 >> 12) & 63]); sb.append(cArr[(i4 >> 6) & 63]); sb.append(cArr[i4 & 63]); i2 += 3; int i5 = i3 + 1; if (i3 >= 14) { break; } i3 = i5; } sb.append(" "); } int i6 = 0 + length; if (i2 == i6 - 2) { int i7 = ((bArr[i2 + 1] & UByte.MAX_VALUE) << 8) | ((bArr[i2] & UByte.MAX_VALUE) << 16); char[] cArr2 = f14341a; sb.append(cArr2[(i7 >> 18) & 63]); sb.append(cArr2[(i7 >> 12) & 63]); sb.append(cArr2[(i7 >> 6) & 63]); sb.append(ContainerUtils.KEY_VALUE_DELIMITER); } else if (i2 == i6 - 1) { int i8 = (bArr[i2] & UByte.MAX_VALUE) << 16; char[] cArr3 = f14341a; sb.append(cArr3[(i8 >> 18) & 63]); sb.append(cArr3[(i8 >> 12) & 63]); sb.append("=="); } String sb2 = sb.toString(); AppMethodBeat.m13385o(132653); return sb2; }public static String m39789a(byte[] array) { System.out.println(leviathan.bytesToHexString(array)); final int length = array.length; final StringBuilder sb = new StringBuilder(array.length * 3 / 2); int i = 0; Label_0025: while (true) { int n = 0; while (i <= length - 3) { final int n2 = (array[i] & 0xFF) << 16 | (array[i + 1] & 0xFF) << 8 | (array[i + 2] & 0xFF); final char[] a = f14341a; sb.append(a[n2 >> 18 & 0x3F]); sb.append(a[n2 >> 12 & 0x3F]); sb.append(a[n2 >> 6 & 0x3F]); sb.append(a[n2 & 0x3F]); i += 3; if (n >= 14) { sb.append(" "); continue Label_0025; } ++n; } break; } final int n3 = 0 + length; if (i == n3 - 2) { final int n4 = (array[i + 1] & 0xFF) << 8 | (array[i] & 0xFF) << 16; final char[] a2 = f14341a; sb.append(a2[n4 >> 18 & 0x3F]); sb.append(a2[n4 >> 12 & 0x3F]); sb.append(a2[n4 >> 6 & 0x3F]); sb.append("="); } else if (i == n3 - 1) { final int n5 = (array[i] & 0xFF) << 16; final char[] a3 = f14341a; sb.append(a3[n5 >> 18 & 0x3F]); sb.append(a3[n5 >> 12 & 0x3F]); sb.append("=="); } final String string = sb.toString(); return string; }public static String m39789a(byte[] array) { System.out.println(leviathan.bytesToHexString(array)); final int length = array.length; final StringBuilder sb = new StringBuilder(array.length * 3 / 2); int i = 0; Label_0025: while (true) { int n = 0; while (i <= length - 3) { final int n2 = (array[i] & 0xFF) << 16 | (array[i + 1] & 0xFF) << 8 | (array[i + 2] & 0xFF); final char[] a = f14341a; sb.append(a[n2 >> 18 & 0x3F]); sb.append(a[n2 >> 12 & 0x3F]); sb.append(a[n2 >> 6 & 0x3F]); sb.append(a[n2 & 0x3F]); i += 3; if (n >= 14) { sb.append(" "); continue Label_0025; } ++n; } break; } final int n3 = 0 + length; if (i == n3 - 2) { final int n4 = (array[i + 1] & 0xFF) << 8 | (array[i] & 0xFF) << 16; final char[] a2 = f14341a; sb.append(a2[n4 >> 18 & 0x3F]); sb.append(a2[n4 >> 12 & 0x3F]); sb.append(a2[n4 >> 6 & 0x3F]); sb.append("="); } else if (i == n3 - 1) { final int n5 = (array[i] & 0xFF) << 16; final char[] a3 = f14341a; sb.append(a3[n5 >> 18 & 0x3F]); sb.append(a3[n5 >> 12 & 0x3F]); sb.append("=="); } final String string = sb.toString(); return string; }xHook.register("libc-lib.so", "strcat", new ReplaceCallback() { @Override public HookStatus onCall(Emulator<?> emulator, HookContext context, long originFunction) { Pointer pointer1 = context.getPointerArg(0); Pointer pointer = context.getPointerArg(1); String str = pointer0.getString(0); String str1 = pointer1.getString(0); System.out.println("strcat=" + str + ":" + str1); return HookStatus.RET(emulator, originFunction); } @Override public void postCall(Emulator<?> emulator, HookContext context) { System.out.println("strcat=" + ", ret=" + context.getPointerArg(0).getString(0)); } }, true);xHook.register("libc-lib.so", "strcat", new ReplaceCallback() { @Override public HookStatus onCall(Emulator<?> emulator, HookContext context, long originFunction) { Pointer pointer1 = context.getPointerArg(0); Pointer pointer = context.getPointerArg(1); String str = pointer0.getString(0); String str1 = pointer1.getString(0); System.out.println("strcat=" + str + ":" + str1); return HookStatus.RET(emulator, originFunction); } @Override public void postCall(Emulator<?> emulator, HookContext context) { System.out.println("strcat=" + ", ret=" + context.getPointerArg(0).getString(0)); } }, true);xHook.register("libc-lib.so", "DES_ede3_cbc_encrypt", new ReplaceCallback() { @Override public HookStatus onCall(Emulator<?> emulator, HookContext context, long originFunction) { Pointer pointer0 = context.getPointerArg(0); Pointer pointer3 = context.getPointerArg(3); Pointer pointer4 = context.getPointerArg(4); Pointer pointer5 = context.getPointerArg(5); Pointer pointer6 = context.getPointerArg(6); byte[] str = pointer0.getByteArray(0,8); byte[] str3 = pointer3.getByteArray(0,8); byte[] str4 = pointer4.getByteArray(0,8); byte[] str5 = pointer5.getByteArray(0,8); byte[] str6 = pointer6.getByteArray(0,8); Inspector.inspect(str, "memcpy src=" + pointer0); Inspector.inspect(str3, "memcpy v3=" + pointer3); Inspector.inspect(str4, "memcpy v4=" + pointer4); Inspector.inspect(str5, "memcpy v5=" + pointer5); Inspector.inspect(str6, "memcpy v6=" + pointer6);// System.out.println("DES_ede3_cbc_encrypt=" + str + ":" + str3+":"+str4 +":"+str5+":"+str6); return HookStatus.RET(emulator, originFunction); } @Override public void postCall(Emulator<?> emulator, HookContext context) {// System.out.println("DES_ede3_cbc_encrypt=" + ", ret=" + context.getPointerArg(0).getString(0)); } }, true);xHook.register("libc-lib.so", "DES_ede3_cbc_encrypt", new ReplaceCallback() { @Override public HookStatus onCall(Emulator<?> emulator, HookContext context, long originFunction) { Pointer pointer0 = context.getPointerArg(0); Pointer pointer3 = context.getPointerArg(3); Pointer pointer4 = context.getPointerArg(4); Pointer pointer5 = context.getPointerArg(5); Pointer pointer6 = context.getPointerArg(6); byte[] str = pointer0.getByteArray(0,8); byte[] str3 = pointer3.getByteArray(0,8); byte[] str4 = pointer4.getByteArray(0,8); byte[] str5 = pointer5.getByteArray(0,8); byte[] str6 = pointer6.getByteArray(0,8); Inspector.inspect(str, "memcpy src=" + pointer0); Inspector.inspect(str3, "memcpy v3=" + pointer3); Inspector.inspect(str4, "memcpy v4=" + pointer4); Inspector.inspect(str5, "memcpy v5=" + pointer5); Inspector.inspect(str6, "memcpy v6=" + pointer6);// System.out.println("DES_ede3_cbc_encrypt=" + str + ":" + str3+":"+str4 +":"+str5+":"+str6); return HookStatus.RET(emulator, originFunction); } @Override public void postCall(Emulator<?> emulator, HookContext context) {// System.out.println("DES_ede3_cbc_encrypt=" + ", ret=" + context.getPointerArg(0).getString(0)); } }, true);[17:48:46 063]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 063]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 063]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 064]memcpy v6=unidbg@0xbffff480, md5=2e9ec317e197819358fbc43afca7d837, hex=3031323334353637size: 80000: 30 31 32 33 34 35 36 37 01234567^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 067]memcpy src=unidbg@0xbffff490, md5=af22f93ebcfbe719516ed5198566bfe9, hex=7a63657c31363431size: 80000: 7A 63 65 7C 31 36 34 31 zce|1641^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 067]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 067]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 067]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 068]memcpy v6=unidbg@0xbffff480, md5=bb5eac7391e75091af9cd5079c461b67, hex=47b4c2b3a4e8bb65size: 80000: 47 B4 C2 B3 A4 E8 BB 65 G......e^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 068]memcpy src=unidbg@0xbffff490, md5=7848ac6c12f2f4d327802cd176ac5772, hex=3435303539313230size: 80000: 34 35 30 35 39 31 32 30 45059120^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 068]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 070]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 070]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 070]memcpy v6=unidbg@0xbffff480, md5=baa8e3fb252aee490431254a5717d676, hex=f9dbc8fe35b95f06size: 80000: F9 DB C8 FE 35 B9 5F 06 ....5._.^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 071]memcpy src=unidbg@0xbffff490, md5=9064ae0c2b1da5f5ce4ab89da47fdf84, hex=397c307c39653435size: 80000: 39 7C 30 7C 39 65 34 35 9|0|9e45^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 071]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 071]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 071]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 071]memcpy v6=unidbg@0xbffff480, md5=32c93a641f13a755bf0351cf834d391e, hex=e84547698b839584size: 80000: E8 45 47 69 8B 83 95 84 .EGi....^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 071]memcpy src=unidbg@0xbffff490, md5=d8f51a6751018766110c703a4ec683cc, hex=3065613566336464size: 80000: 30 65 61 35 66 33 64 64 0ea5f3dd^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 072]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 072]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 072]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 072]memcpy v6=unidbg@0xbffff480, md5=e4041e6bb89cb6fa65bb1e1e9931bfe6, hex=c8d8afbf9514e080size: 80000: C8 D8 AF BF 95 14 E0 80 ........^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 073]memcpy src=unidbg@0xbffff490, md5=d1354fdcee14fd741630488ec469f587, hex=306238617c317c37size: 80000: 30 62 38 61 7C 31 7C 37 0b8a|1|7^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 073]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 073]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 073]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 073]memcpy v6=unidbg@0xbffff480, md5=7b92bd69841bb6940288ad15cc2d6f51, hex=b4c0f1dae88d3a3csize: 80000: B4 C0 F1 DA E8 8D 3A 3C ......:<^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 074]memcpy src=unidbg@0xbffff490, md5=0b118370d01046b8dd7d424c62736733, hex=2e392e3137387c30size: 80000: 2E 39 2E 31 37 38 7C 30 .9.178|0^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 074]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 074]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 074]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 074]memcpy v6=unidbg@0xbffff480, md5=be9e6d23aa1673ecd64454aceed715a3, hex=6ebd53d0cbddd0a3size: 80000: 6E BD 53 D0 CB DD D0 A3 n.S.....^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 075]memcpy src=unidbg@0xbffff490, md5=2123366ad8ef13c3b1c60c9942a0cf62, hex=7c62663066643935size: 80000: 7C 62 66 30 66 64 39 35 |bf0fd95^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 075]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 075]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 075]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 075]memcpy v6=unidbg@0xbffff480, md5=100457bc026ef3ba622f06c133bac14a, hex=d5a62c6ae0791647size: 80000: D5 A6 2C 6A E0 79 16 47 ..,j.y.G^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 075]memcpy src=unidbg@0xbffff490, md5=fb9842ea1ba2429f73b3b371399253cf, hex=6562326366326431size: 80000: 65 62 32 63 66 32 64 31 eb2cf2d1^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 076]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 076]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 076]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 076]memcpy v6=unidbg@0xbffff480, md5=9529b4cda652c51d4fa7d31b71e9c6a1, hex=fa910272e7b3a380size: 80000: FA 91 02 72 E7 B3 A3 80 ...r....^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 076]memcpy src=unidbg@0xbffff490, md5=d8c9b448f3b3b06be3cf184444d65210, hex=3735306362356666size: 80000: 37 35 30 63 62 35 66 66 750cb5ff^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 076]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 077]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 077]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 077]memcpy v6=unidbg@0xbffff480, md5=c035c2c6d97c6be7b07576e1c186d78b, hex=649fd845c3900726size: 80000: 64 9F D8 45 C3 90 07 26 d..E...&^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 077]memcpy src=unidbg@0xbffff490, md5=83cecf0241c488028fb908e9e93990ec, hex=3933363463356634size: 80000: 39 33 36 34 63 35 66 34 9364c5f4^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 077]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 077]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 078]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 078]memcpy v6=unidbg@0xbffff480, md5=8966f02efec8d51bd3a6a118bccf2057, hex=d91be87bcbf253b2size: 80000: D9 1B E8 7B CB F2 53 B2 ...{..S.^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 078]memcpy src=unidbg@0xbffff490, md5=4c82a29f8d6555410b5aa470eacf4f60, hex=397c663138396164size: 80000: 39 7C 66 31 38 39 61 64 9|f189ad^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 078]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 078]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 079]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 079]memcpy v6=unidbg@0xbffff480, md5=18cdd13b7aaf46150bd973bea901dd15, hex=bea229a0034921c6size: 80000: BE A2 29 A0 03 49 21 C6 ..)..I!.^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 079]memcpy src=unidbg@0xbffff490, md5=142f4c4991a2701942ff4667ca0ff143, hex=6339326238313662size: 80000: 63 39 32 62 38 31 36 62 c92b816b^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 079]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 079]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 080]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 080]memcpy v6=unidbg@0xbffff480, md5=e452af0097e0b69bfcb0b0147e8a6aa0, hex=b8d94eaaa3eeb8e1size: 80000: B8 D9 4E AA A3 EE B8 E1 ..N.....^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 080]memcpy src=unidbg@0xbffff490, md5=999f4d65efbaabf5aeaa49dbfc040ac7, hex=3365396461323965size: 80000: 33 65 39 64 61 32 39 65 3e9da29e^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 080]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 080]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 081]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 081]memcpy v6=unidbg@0xbffff480, md5=70a57703e3c3cd8a08f251219fc0c0d4, hex=990cca71b5c19d14size: 80000: 99 0C CA 71 B5 C1 9D 14 ...q....^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 081]memcpy src=unidbg@0xbffff490, md5=95e5fff13ce7c5e70115fc3973376d3d, hex=6133303464346137size: 80000: 61 33 30 34 64 34 61 37 a304d4a7^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 081]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 081]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 081]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 082]memcpy v6=unidbg@0xbffff480, md5=872400f9cd80b45059b121ff47ad88ef, hex=030b772cb2a3fca3size: 80000: 03 0B 77 2C B2 A3 FC A3 ..w,....^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 082]memcpy src=unidbg@0xbffff490, md5=bac52abca69fc8ba330f5328eee30c27, hex=6534060606060606size: 80000: 65 34 06 06 06 06 06 06 e4......^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 082]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 082]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 082]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 082]memcpy v6=unidbg@0xbffff480, md5=e8f6f77bf6276dacec2da2bfbf84dfc2, hex=253457f91cb97a09size: 80000: 25 34 57 F9 1C B9 7A 09 %4W...z.^-----------------------------------------------------------------------------^[17:48:46 063]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 063]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 063]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 064]memcpy v6=unidbg@0xbffff480, md5=2e9ec317e197819358fbc43afca7d837, hex=3031323334353637size: 80000: 30 31 32 33 34 35 36 37 01234567^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 067]memcpy src=unidbg@0xbffff490, md5=af22f93ebcfbe719516ed5198566bfe9, hex=7a63657c31363431size: 80000: 7A 63 65 7C 31 36 34 31 zce|1641^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 067]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 067]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 067]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 068]memcpy v6=unidbg@0xbffff480, md5=bb5eac7391e75091af9cd5079c461b67, hex=47b4c2b3a4e8bb65size: 80000: 47 B4 C2 B3 A4 E8 BB 65 G......e^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 068]memcpy src=unidbg@0xbffff490, md5=7848ac6c12f2f4d327802cd176ac5772, hex=3435303539313230size: 80000: 34 35 30 35 39 31 32 30 45059120^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 068]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 070]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 070]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 070]memcpy v6=unidbg@0xbffff480, md5=baa8e3fb252aee490431254a5717d676, hex=f9dbc8fe35b95f06size: 80000: F9 DB C8 FE 35 B9 5F 06 ....5._.^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 071]memcpy src=unidbg@0xbffff490, md5=9064ae0c2b1da5f5ce4ab89da47fdf84, hex=397c307c39653435size: 80000: 39 7C 30 7C 39 65 34 35 9|0|9e45^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 071]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 071]memcpy v4=unidbg@0xbffff518, md5=e3e90fb9215af3c1234464ee1e03fa59, hex=209c4c080d4d0043size: 80000: 20 9C 4C 08 0D 4D 00 43 .L..M.C^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 071]memcpy v5=unidbg@0xbffff498, md5=59cdb4763bce351d1c97d71662a0a67f, hex=14804cd4044dc746size: 80000: 14 80 4C D4 04 4D C7 46 ..L..M.F^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 071]memcpy v6=unidbg@0xbffff480, md5=32c93a641f13a755bf0351cf834d391e, hex=e84547698b839584size: 80000: E8 45 47 69 8B 83 95 84 .EGi....^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 071]memcpy src=unidbg@0xbffff490, md5=d8f51a6751018766110c703a4ec683cc, hex=3065613566336464size: 80000: 30 65 61 35 66 33 64 64 0ea5f3dd^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<[17:48:46 072]memcpy v3=unidbg@0xbffff598, md5=7e504a51a397f262e2e74221ac9c0ed2, hex=105cbc14004d0409size: 80000: 10 5C BC 14 00 4D 04 09 .\...M..^-----------------------------------------------------------------------------^>-----------------------------------------------------------------------------<