这篇帖子之前写的是别的知识点,但是错误太多,帖子又不好删,就直接在原帖删了重写这篇。
防截屏需要hook一个函数NtGdiBitBlt, 实现代码在附件里
//本来我以为要hook两个函数呢,还有个NtGdiStretchBlt,后来测试发现不用
这个函数在shadowSSdt表里,后面简称SSSDT
本篇帖子系统为win7x86,只是给一个思路和实现,相信大部分人都可以直接移植到X64上,当然也有更好的方式去解决,比如使用驱动框架。
SSSDT表和SSDT表示不同的,在system进程中是没有加载的,我们需要切换进程,比如打开一个绘图工具,或者切换到csrss.exe这个常驻进程
!process 0 0 查看所有进程
.process /p 切换进程
x命令查表
dd命令查SSSDT表
第一行是SSDT表
第二行是SSSDT表
表地址为94726000,函数个数为0x339个
dds命令查看SSSDT表函数,想查看0x339个就输入339对应的十进制数
可以看到现在的函数是Gdi开头的图形相关的
那我们知道了拿SSSDT表的流程了,需要切换到图形相关的进程,才能hook放截屏的两个函数,那我们用代码实现一下吧
需要做的很细的话,还要重载内核,但是因为这篇帖子只是为了做防截屏并不是做ARK或者做其它功能,所以就只说防截屏
代码放在最下面
判断进程为QQ.EXE结尾就直接返回false
hook成功
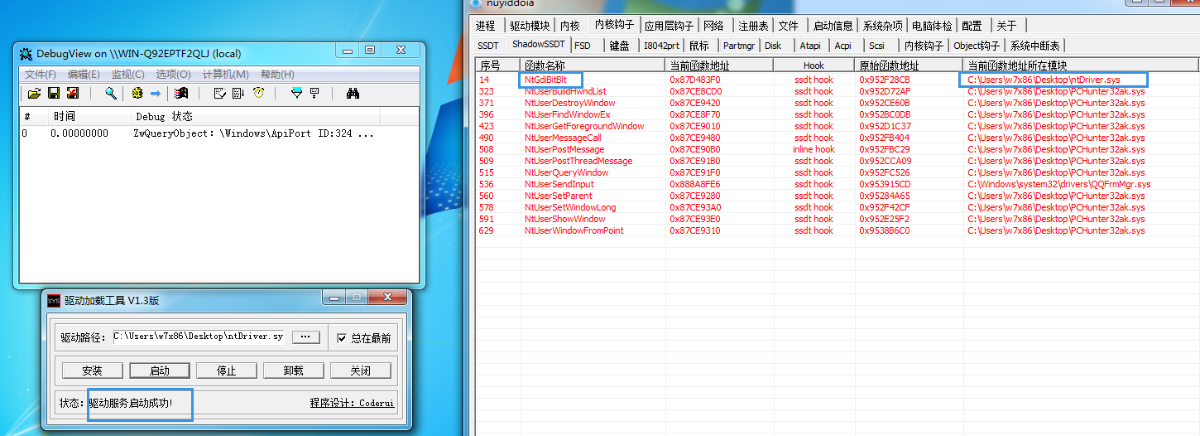
测试截图
截图结果
!process 0 0
PROCESS 855d3920 SessionId: none Cid: 0004 Peb: 00000000 ParentCid: 0000
DirBase: 00185000 ObjectTable: 89201b28 HandleCount: 506.
Image: System
PROCESS 8687ac70 SessionId: 0 Cid: 0140 Peb: 7ffd4000 ParentCid: 0138
DirBase: 3f373060 ObjectTable: 99226d70 HandleCount: 455.
Image: csrss.exe
PROCESS 85761838 SessionId: 1 Cid: 098c Peb: 7ffd6000 ParentCid: 0540
DirBase: 3f3735e0 ObjectTable: 988b79d8 HandleCount: 120.
Image: mspaint.exe
...
...
...
!process 0 0
PROCESS 855d3920 SessionId: none Cid: 0004 Peb: 00000000 ParentCid: 0000
DirBase: 00185000 ObjectTable: 89201b28 HandleCount: 506.
Image: System
PROCESS 8687ac70 SessionId: 0 Cid: 0140 Peb: 7ffd4000 ParentCid: 0138
DirBase: 3f373060 ObjectTable: 99226d70 HandleCount: 455.
Image: csrss.exe
PROCESS 85761838 SessionId: 1 Cid: 098c Peb: 7ffd6000 ParentCid: 0540
DirBase: 3f3735e0 ObjectTable: 988b79d8 HandleCount: 120.
Image: mspaint.exe
...
...
...
kd> .process /p 8687ac70
Implicit process is now 8687ac70
.cache forcedecodeuser done
kd> .process /p 8687ac70
Implicit process is now 8687ac70
.cache forcedecodeuser done
kd> x nt!kes*des*table**
83fbea00 nt!KeServiceDescriptorTableShadow = <no type information>
83fbe9c0 nt!KeServiceDescriptorTable = <no type information>
kd> x nt!kes*des*table**
83fbea00 nt!KeServiceDescriptorTableShadow = <no type information>
83fbe9c0 nt!KeServiceDescriptorTable = <no type information>
kd> dd 83fbea00
83fbea00 83ed2d9c 00000000 00000191 83ed33e4
83fbea10 94726000 00000000 00000339 9472702c
83fbea20 00000000 00000000 83fbea24 00000340
83fbea30 00000340 855eeeb0 00000007 00000000
83fbea40 855eede8 855e9550 855e96e0 855e9618
83fbea50 00000000 855e9488 00000000 00000000
83fbea60 83ecc809 83ed9eed 83ee83a5 00000003
83fbea70 85535000 85536000 00000120 ffffffff
kd> dd 83fbea00
83fbea00 83ed2d9c 00000000 00000191 83ed33e4
83fbea10 94726000 00000000 00000339 9472702c
83fbea20 00000000 00000000 83fbea24 00000340
83fbea30 00000340 855eeeb0 00000007 00000000
83fbea40 855eede8 855e9550 855e96e0 855e9618
83fbea50 00000000 855e9488 00000000 00000000
83fbea60 83ecc809 83ed9eed 83ee83a5 00000003
83fbea70 85535000 85536000 00000120 ffffffff
kd> dds 94726000 L2
94726000 946b3d37 win32k!NtGdiAbortDoc
94726004 946cbc23 win32k!NtGdiAbortPath
kd> dds 94726000 L2
94726000 946b3d37 win32k!NtGdiAbortDoc
94726004 946cbc23 win32k!NtGdiAbortPath
HANDLE GetCsrPid() {
HANDLE Process, hObject;
HANDLE CsrId = (HANDLE)0;
OBJECT_ATTRIBUTES obj;
CLIENT_ID cid;
UCHAR Buff[0x100];
POBJECT_NAME_INFORMATION ObjName = (PVOID)&Buff;
PSYSTEM_HANDLE_INFORMATION_EX Handles;
ULONG r;
Handles = GetInfoTable(SystemHandleInformation);
if (!Handles) return CsrId;
for (r = 0; r < Handles->NumberOfHandles; r++){
//Port object
InitializeObjectAttributes(&obj, NULL, OBJ_KERNEL_HANDLE, NULL, NULL);
cid.UniqueProcess = (HANDLE)Handles->Information[r].ProcessId;
cid.UniqueThread = 0;
if (NT_SUCCESS(NtOpenProcess(&Process, PROCESS_DUP_HANDLE, &obj, &cid))){
if (NT_SUCCESS(ZwDuplicateObject(Process, (HANDLE)Handles->Information[r].Handle, NtCurrentProcess(), &hObject, 0, 0, DUPLICATE_SAME_ACCESS))){
if (NT_SUCCESS(ZwQueryObject(hObject, ObjectNameInformation, ObjName, 0x100, NULL))){
if (ObjName->Name.Buffer && !wcsncmp(L"\\Windows\\ApiPort", ObjName->Name.Buffer, 20)){
CsrId = (HANDLE)Handles->Information[r].ProcessId;
KdPrintEx((DPFLTR_IHVDRIVER_ID, DPFLTR_ERROR_LEVEL, "ZwQueryObject:%wZ ID:%d Type::%d\n", &ObjName->Name, Handles->Information[r].ProcessId, Handles->Information[r].ObjectTypeNumber));
}
}
ZwClose(hObject);
}
ZwClose(Process);
}
}
ExFreePool(Handles);
return CsrId;
}
HANDLE GetCsrPid() {
HANDLE Process, hObject;
HANDLE CsrId = (HANDLE)0;
OBJECT_ATTRIBUTES obj;
CLIENT_ID cid;
UCHAR Buff[0x100];
POBJECT_NAME_INFORMATION ObjName = (PVOID)&Buff;
PSYSTEM_HANDLE_INFORMATION_EX Handles;
ULONG r;
Handles = GetInfoTable(SystemHandleInformation);
if (!Handles) return CsrId;
for (r = 0; r < Handles->NumberOfHandles; r++){
//Port object
InitializeObjectAttributes(&obj, NULL, OBJ_KERNEL_HANDLE, NULL, NULL);
cid.UniqueProcess = (HANDLE)Handles->Information[r].ProcessId;
cid.UniqueThread = 0;
if (NT_SUCCESS(NtOpenProcess(&Process, PROCESS_DUP_HANDLE, &obj, &cid))){
if (NT_SUCCESS(ZwDuplicateObject(Process, (HANDLE)Handles->Information[r].Handle, NtCurrentProcess(), &hObject, 0, 0, DUPLICATE_SAME_ACCESS))){
if (NT_SUCCESS(ZwQueryObject(hObject, ObjectNameInformation, ObjName, 0x100, NULL))){
if (ObjName->Name.Buffer && !wcsncmp(L"\\Windows\\ApiPort", ObjName->Name.Buffer, 20)){
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课
最后于 2022-3-31 11:50
被breeze911编辑
,原因: 之前上传的文件有两行代码删注释的时候不小心删掉了,重新上传的没问题了