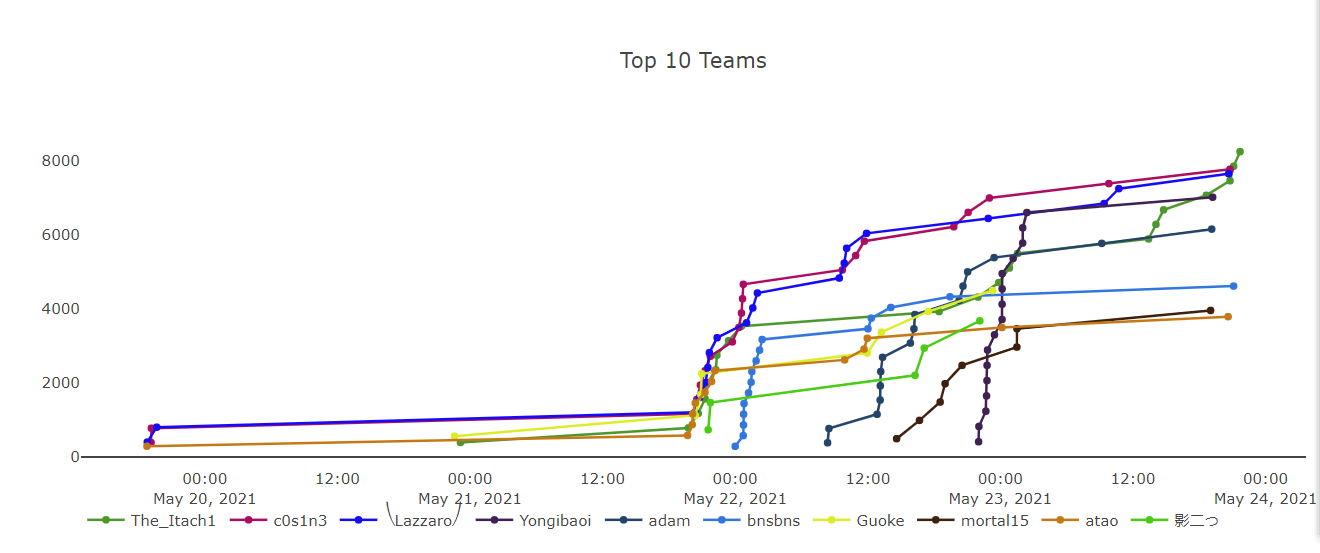
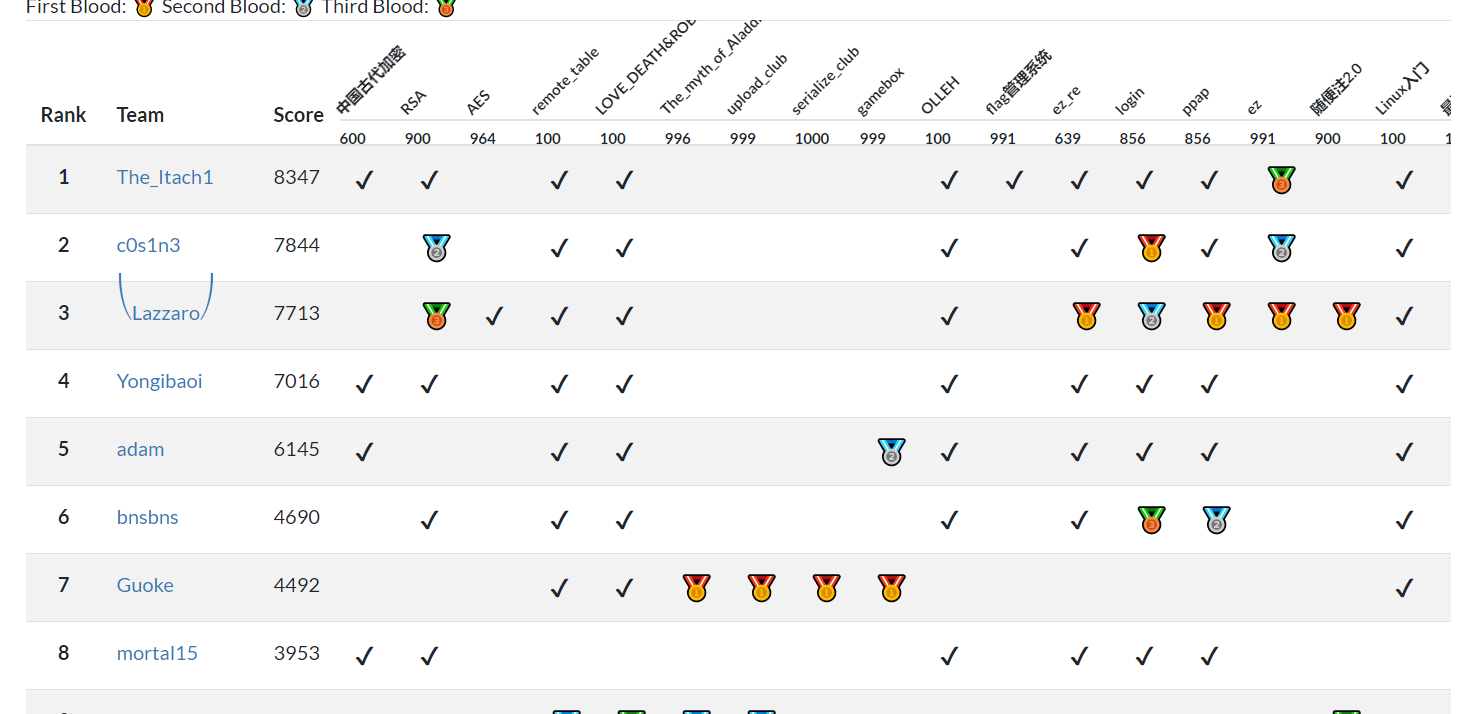
拿了个第一,AK了re,哈哈哈还是可以。
ID:The_Itach1
总排名: 1
分数: 8347
有点可惜,本来可以一血的,被NEEPU给迷惑了,哈哈哈。
ida看,流程,动调比较快
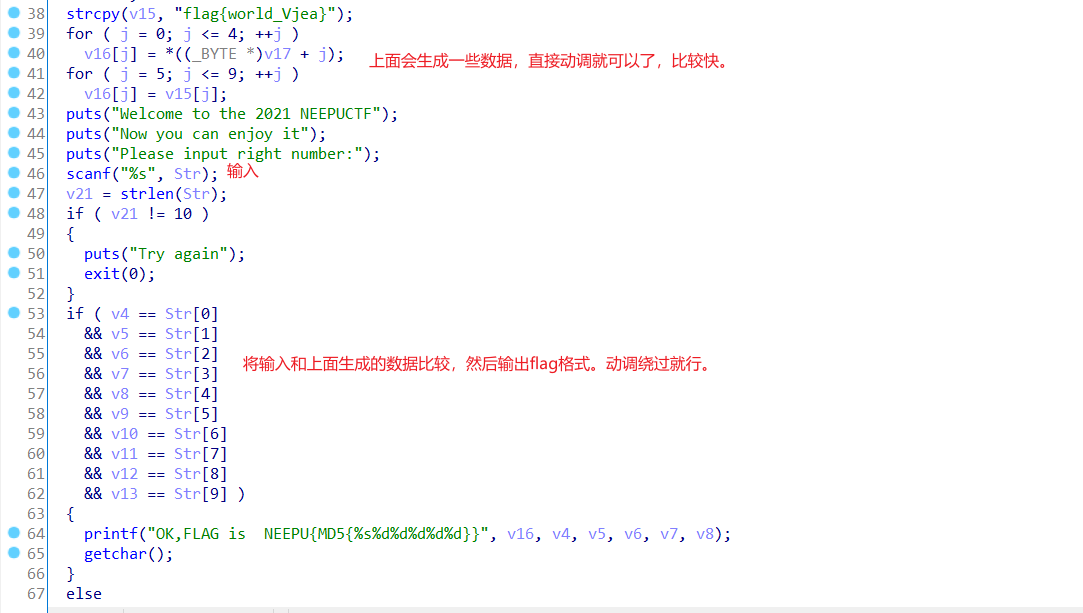
动调绕过得到
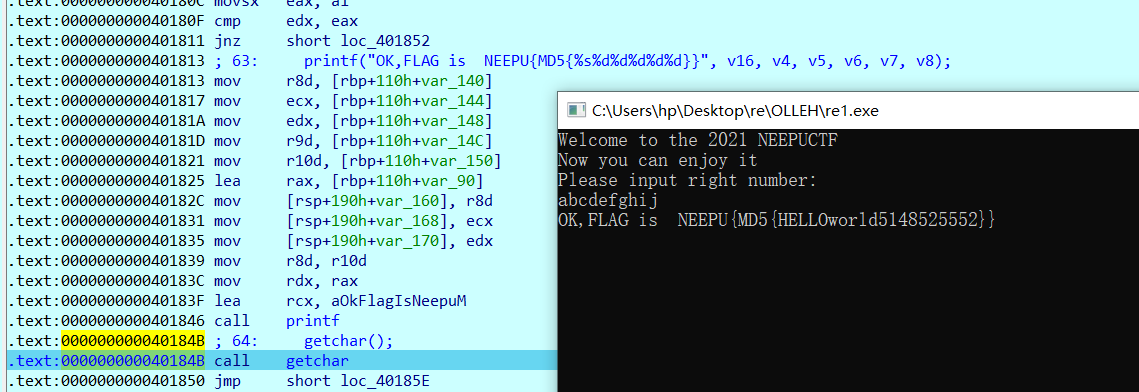
MD5加密一下,故flag为
开始分析是分析exe文件,然后看了里面的一些字符串,什么.net之类的,后来发现flag在dll里面。
用dSspy打开dll,找到加密逻辑,大概就是栅栏,和简单字符处理
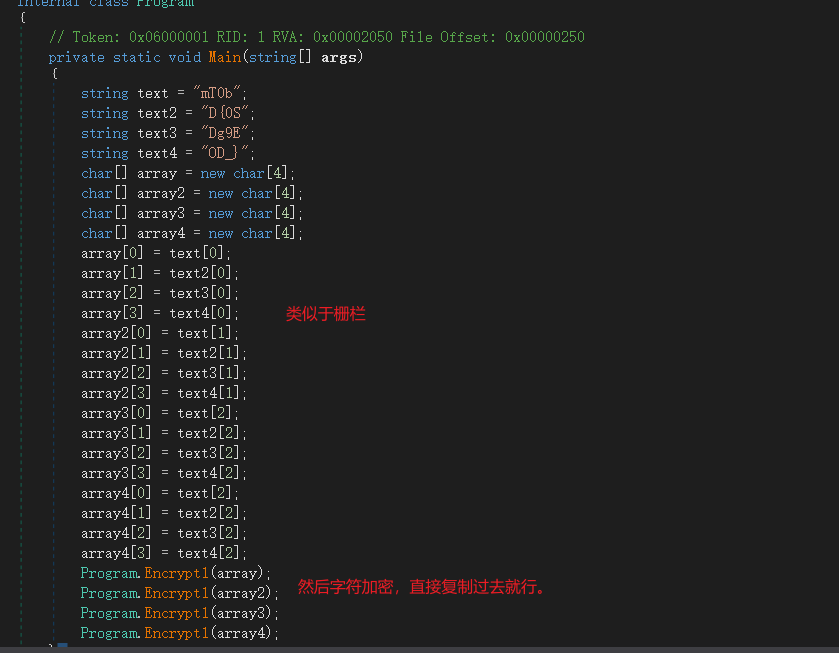
脚本
一个upx加壳程序,直接脱壳没脱起,手动用xdbg脱。
脱壳后ida分析,可以结合动调分析
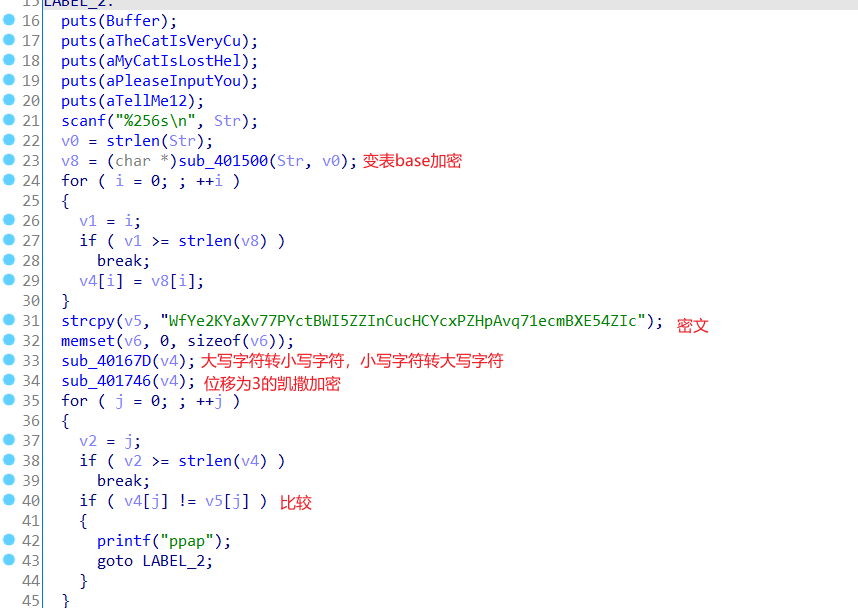
先网上凯撒解密,得到
然后小写转大写
再变表base
一个注册软件,开始用ida看,始终没找到check入口。后来百度发现,这是python写的注册程序,联想到exe转py(2e4K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8r3!0Y4i4K6u0W2j5%4y4V1L8W2)9J5k6h3&6W2N6q4)9J5c8X3@1H3i4K6g2X3x3K6M7#2y4e0t1H3y4e0u0Q4x3V1k6S2M7Y4c8A6j5$3I4W2i4K6u0r3k6r3g2@1j5h3W2D9M7#2)9J5c8U0R3^5x3o6V1K6y4o6t1%4)。
命令
得到一个文件夹,里面有一个retest.pyc
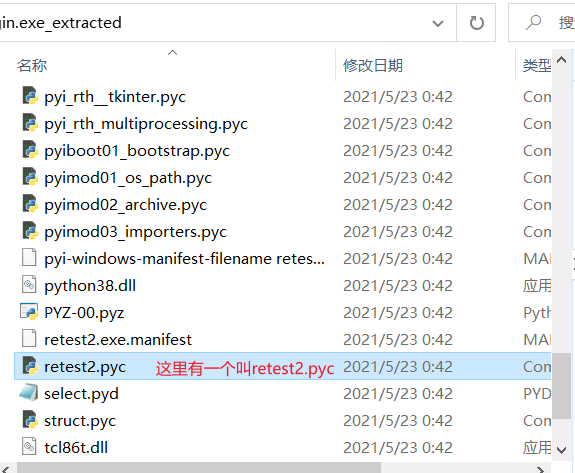
反编译这个pyc,得到的py文件里面就有flag,命令
得到flag
这道题就是加密函数比较多,rc4,变表base,tea,xtea
ida分析
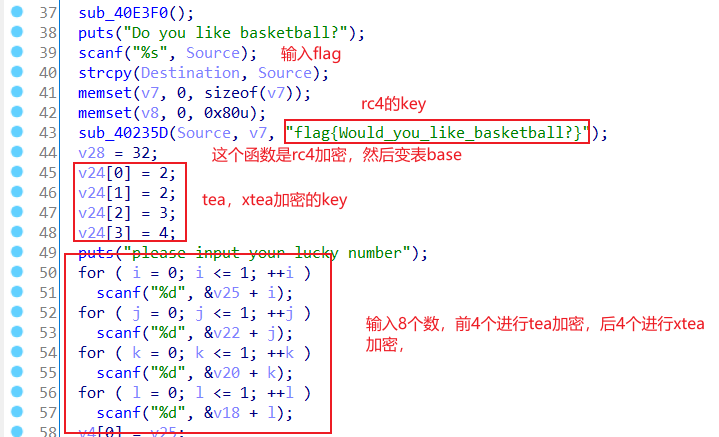
下面是tea,xtea加密
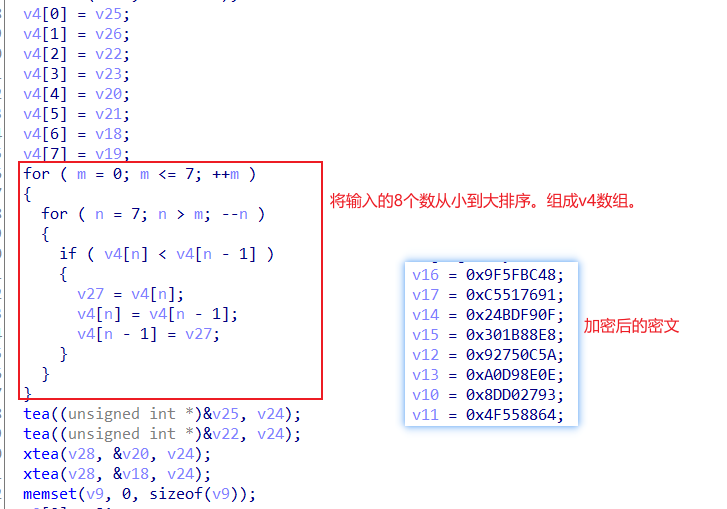
最后的异或处理
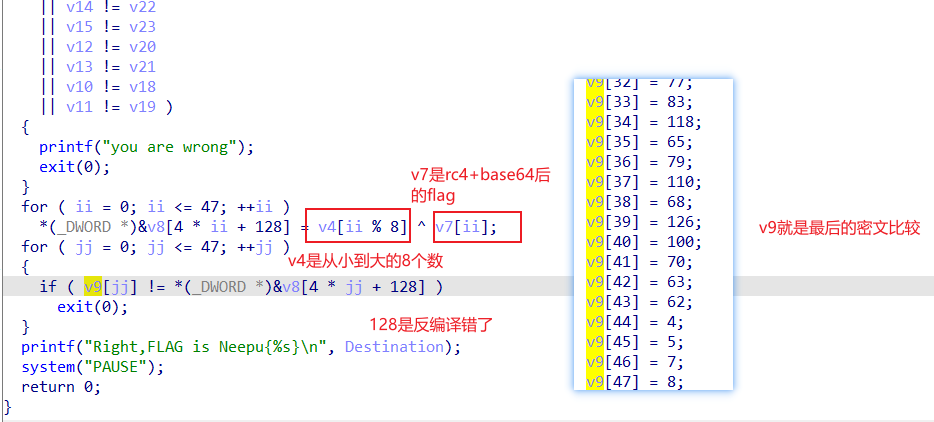
脚本,先得到8个数
tea
xtea
得到v4[]={1 1 3 4 2 5 8 7},排序后v4[]={1,1,2,3,4,5,7,8};
然后异或解密+变表base+rc4
一个腾讯加壳后的apk,脱壳462K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6*7K9s2g2S2L8X3I4S2L8W2)9J5k6i4A6Z5K9h3S2#2i4K6u0W2j5$3!0E0i4K6u0r3M7q4)9J5c8U0b7#2y4e0V1I4y4K6f1@1
脱壳后拖到jeb分析
不断分析,找到这个位置
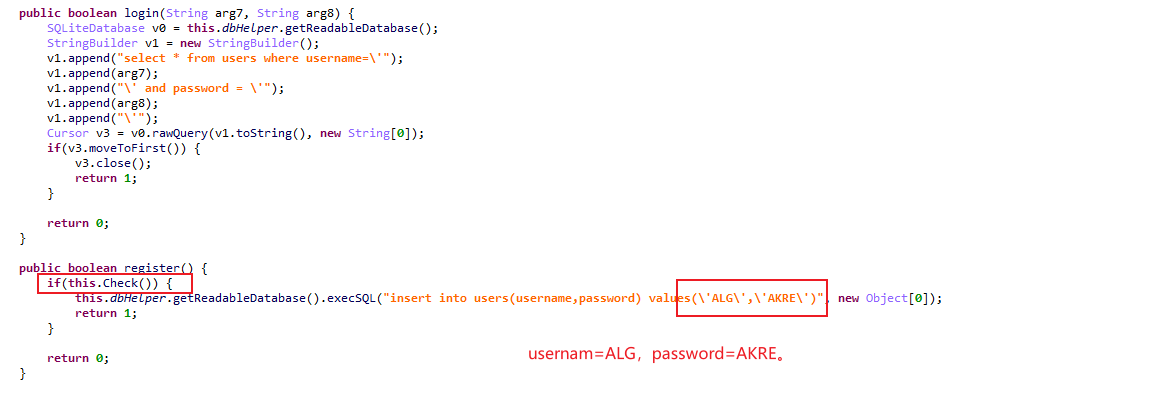
然后直接登录,就可以得到flag了
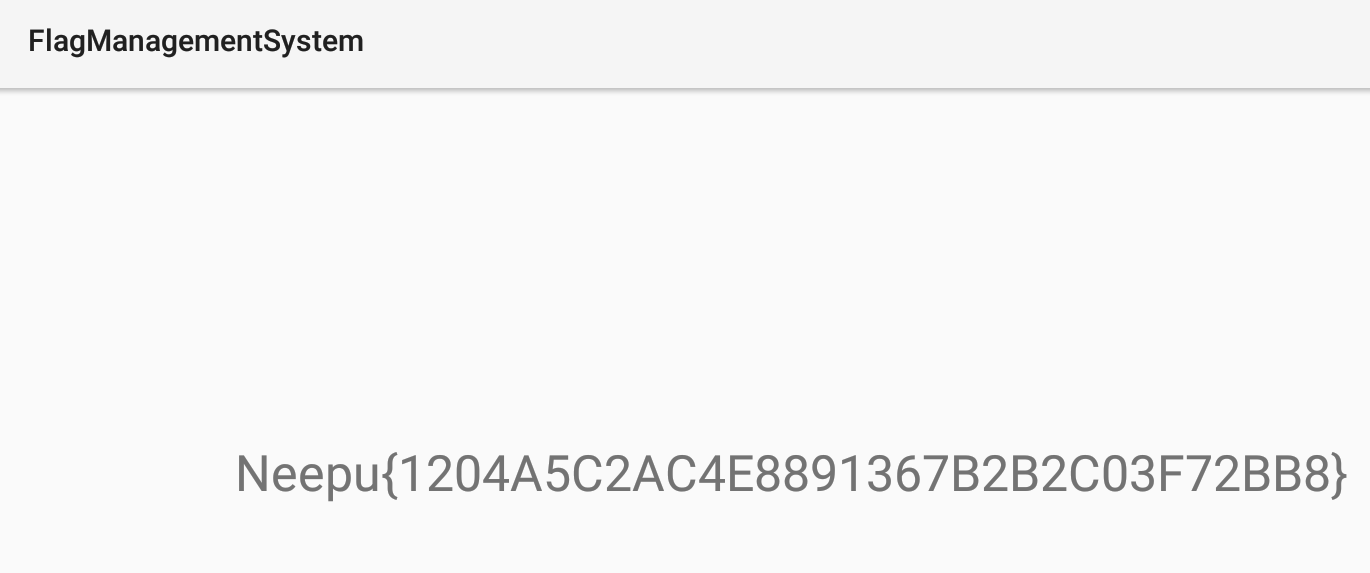
ida打开文件,发现就是一个命令行传入参数切割后要是2333
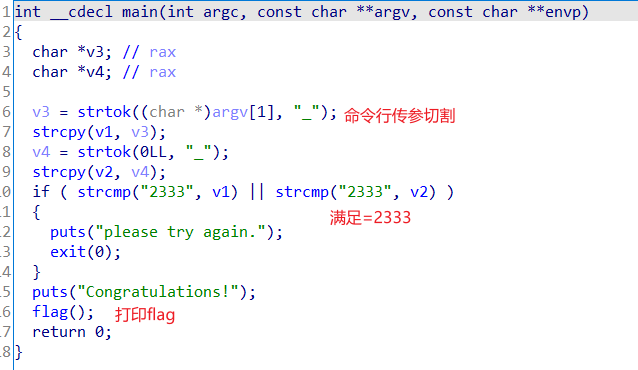
所以直接nc连接,后传入参数2333_2333就行了。
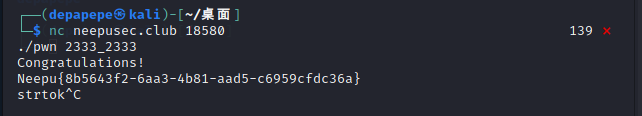
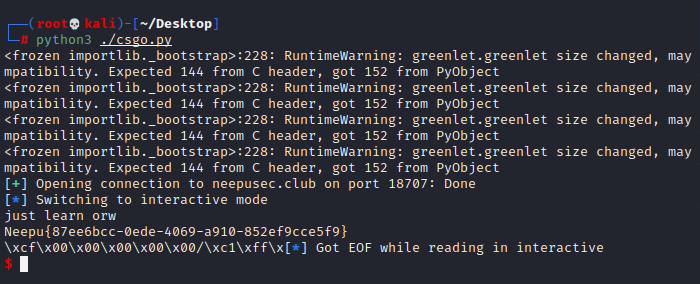
利用write() read() 等系统调用去读取目标主机中的flag
exp
getflag
打开网站查看robots.txt
发现网页,然后查看源码得到flag
乱点,发现有个notfund.html
查看源码发现flag
两个文件
第一个文件使用foremost 分离
得到图片,这是上古卷轴中的龙文

翻译一下是youseethedragon
解开音频文件密码
使用silenteye,分离音频文件中的flag.txt
base64解密得到flag
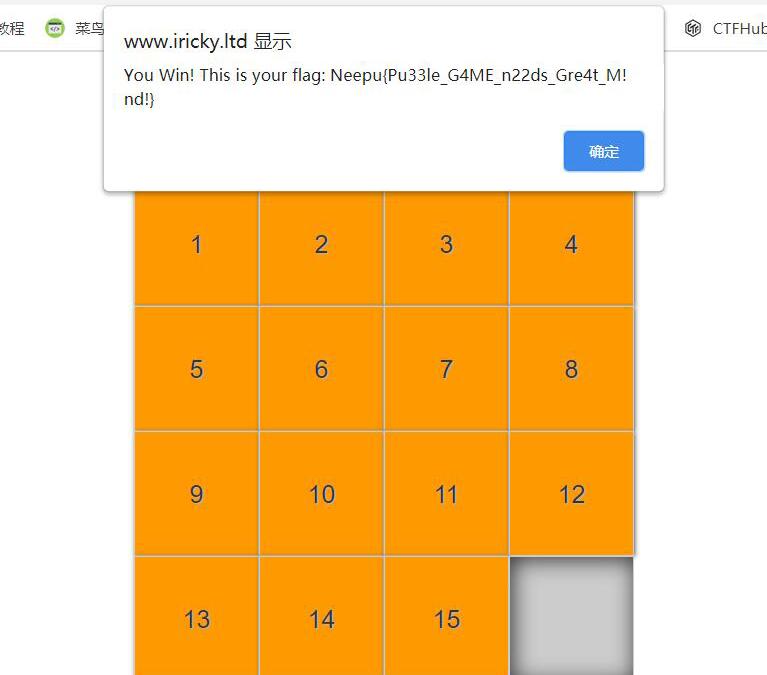
数字华容道,玩出来
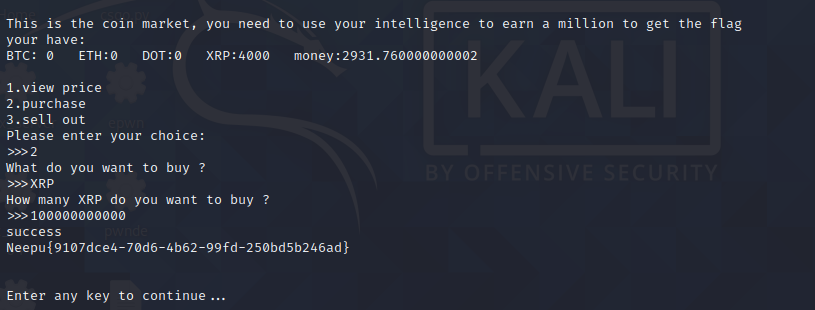
一直买进最后一种硬币
直到最后一种硬币的价格降为负数
然后再继续买进,会反得到钱
最后得到flag
hint.txt说flag在根目录,最后在下面的目录下找到
getflag/etc/neepu.conf:Neepu{ec65303a-594a-471b-842c-55ba49fffc74}
100道嘛,没技术,cv工程师。
flag没保存下来,也不想在弄了。。。
在这里找到flag
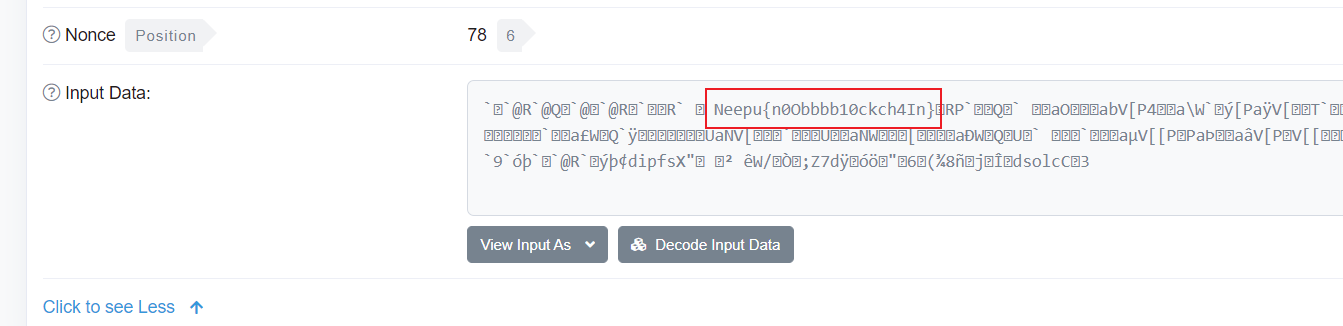
一开始解不出,得到官方hint
得到png文件,改为png.png得到反切密码表
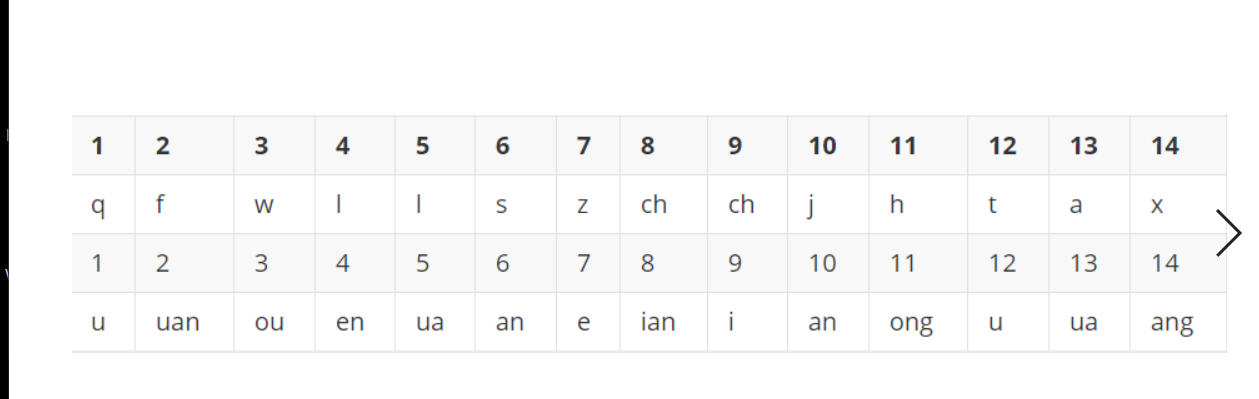
根据该对使得flag有头有尾
查看对的意思,百度搜索得到,对的解密为两个141 分别放在flag头尾
诗使得flag有声有调
根据反切密码的格式,先拿第一排的声母,再拿第二排的韵母,最后加上声调
最后的flag为:
chall1
注意到e很小且diffe = nextprime(random.randint(1,1000))联想到related_message_attack解出m和e
chall2
由于m已知,且整个S在mod (p1+1)条件下,联想到dp泄漏,通常K很小,通过爆破K解出flag
exp
百度网盘:045K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6H3j5h3&6Q4x3X3g2T1j5h3W2V1N6g2)9J5k6h3y4G2L8g2)9J5c8Y4y4Q4x3V1j5I4P5U0y4X3z5h3k6B7d9q4q4t1d9e0u0w2M7r3A6s2K9X3#2t1e0V1p5J5b7b7`.`. 提取码:abcd
Neepu{a4db343d5faf70bc4fb88dd8d4dc86de}
Neepu{a4db343d5faf70bc4fb88dd8d4dc86de}
void Encrypt1(char *string1)
{
int num = 16;
for (int i = 0; i < num; i++)
{
bool flag = string1[i] >= 'a' && string1[i] <= 'z';
if (flag)
{
bool flag2 = string1[i] >= 'a' && string1[i] <= 'y';
if (flag2)
{
string1[i] -= '\u001f';
}
else
{
string1[i] = 'A';
}
}
else
{
bool flag3 = string1[i] >= 'A' && string1[i] <= 'Z';
if (flag3)
{
bool flag4 = string1[i] >= 'A' && string1[i] <= 'Y';
if (flag4)
{
string1[i] += '!';
}
else
{
string1[i] = 'a';
}
}
else
{
bool flag5 = string1[i] >= '0' && string1[i] <= '9';
if (flag5)
{
bool flag6 = string1[i] == '9';
if (flag6)
{
string1[i] = '0';
}
else
{
string1[i] += '\u0001';
}
}
}
}
}
}
int main(void)
{
char text[] = "mDDOT{gDO09_bSE}";
Encrypt1(text);
printf("%s",text);
}
//Neepu{Hep10_Ctf}
void Encrypt1(char *string1)
{
int num = 16;
for (int i = 0; i < num; i++)
{
bool flag = string1[i] >= 'a' && string1[i] <= 'z';
if (flag)
{
bool flag2 = string1[i] >= 'a' && string1[i] <= 'y';
if (flag2)
{
string1[i] -= '\u001f';
}
else
{
string1[i] = 'A';
}
}
else
{
bool flag3 = string1[i] >= 'A' && string1[i] <= 'Z';
if (flag3)
{
bool flag4 = string1[i] >= 'A' && string1[i] <= 'Y';
if (flag4)
{
string1[i] += '!';
}
else
{
string1[i] = 'a';
}
}
else
{
bool flag5 = string1[i] >= '0' && string1[i] <= '9';
if (flag5)
{
bool flag6 = string1[i] == '9';
if (flag6)
{
string1[i] = '0';
}
else
{
string1[i] += '\u0001';
}
}
}
}
}
}
int main(void)
{
char text[] = "mDDOT{gDO09_bSE}";
Encrypt1(text);
printf("%s",text);
}
//Neepu{Hep10_Ctf}
TcVb2HVxUs77MVzqYTF5WWFkZrzEZVzuMWEmXsn71bzjYUB54WFz
TcVb2HVxUs77MVzqYTF5WWFkZrzEZVzuMWEmXsn71bzjYUB54WFz
int main(void)
{
char flag[]="TcVb2HVxUs77MVzqYTF5WWFkZrzEZVzuMWEmXsn71bzjYUB54WFz";
int i;
for(i=0;i<53;i++)
{
if(flag[i]>=65&&flag[i]<=90)
{
flag[i]=flag[i]+32;
continue;
}
if(flag[i]<=122&&flag[i]>=97)
{
flag[i]=flag[i]-32;
}
}
printf("%s",flag);
}
//tCvB2hvXuS77mvZQytf5wwfKzRZezvZUmweMxSN71BZJyub54wfZ
int main(void)
{
char flag[]="TcVb2HVxUs77MVzqYTF5WWFkZrzEZVzuMWEmXsn71bzjYUB54WFz";
int i;
for(i=0;i<53;i++)
{
if(flag[i]>=65&&flag[i]<=90)
{
flag[i]=flag[i]+32;
continue;
}
if(flag[i]<=122&&flag[i]>=97)
{
flag[i]=flag[i]-32;
}
}
printf("%s",flag);
}
//tCvB2hvXuS77mvZQytf5wwfKzRZezvZUmweMxSN71BZJyub54wfZ
import base64
import string
str1 ='tCvB2hvXuS77mvZQytf5wwfKzRZezvZUmweMxSN71BZJyub54wfZ'
string1 = 'abcdefghijklmnopqrstuvwxyz0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ+/'
string2 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
print(base64.b64decode(str1.translate(str.maketrans(string1, string2))))
import base64
import string
str1 ='tCvB2hvXuS77mvZQytf5wwfKzRZezvZUmweMxSN71BZJyub54wfZ'
string1 = 'abcdefghijklmnopqrstuvwxyz0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ+/'
string2 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
print(base64.b64decode(str1.translate(str.maketrans(string1, string2))))
python pyinstxtractor.py [filename]
python pyinstxtractor.py [filename]
uncompyle6 -o C:\Users\hp\Downloads\xxx.py C:\Users\hp\Downloads\xxx.pyc
uncompyle6 -o C:\Users\hp\Downloads\xxx.py C:\Users\hp\Downloads\xxx.pyc
Neepu{vrey_good!!!!!}
void decrypt(unsigned int *code , unsigned int *key)
{
unsigned int delta=0x9e3779b9;
unsigned int v0,v1,sum=0xC6EF3720,i;// sum=0xC6EF3720
v0=code[0];
v1=code[1];
for(i=0;i<32;i++)
{
v1-=( (v0<<4)+key[2] ) ^ (v0+sum) ^ ( (v0>>5)+key[3] );
v0-=( (v1<<4)+key[0] ) ^ (v1+sum) ^ ( (v1>>5)+key[1] );
sum-=delta;
}
code[0]=v0;
code[1]=v1;
}
int main()
{
unsigned int key[4]={2,2,3,4};
unsigned int code[2]={0x24BDF90F,0x301B88E8};
decrypt(code,key);
printf("%x %x",code[0],code[1]);
}
void decrypt(unsigned int *code , unsigned int *key)
{
unsigned int delta=0x9e3779b9;
unsigned int v0,v1,sum=0xC6EF3720,i;// sum=0xC6EF3720
v0=code[0];
v1=code[1];
for(i=0;i<32;i++)
{
v1-=( (v0<<4)+key[2] ) ^ (v0+sum) ^ ( (v0>>5)+key[3] );
v0-=( (v1<<4)+key[0] ) ^ (v1+sum) ^ ( (v1>>5)+key[1] );
sum-=delta;
}
code[0]=v0;
code[1]=v1;
}
int main()
{
unsigned int key[4]={2,2,3,4};
unsigned int code[2]={0x24BDF90F,0x301B88E8};
decrypt(code,key);
printf("%x %x",code[0],code[1]);
}
void decrypt(unsigned int r ,unsigned int *code ,unsigned int *key)
{
unsigned int v0,v1,i,delta=0x9e3779b9;
unsigned int sum=delta*r;
v0=code[0];
v1=code[1];
for(i=0;i<r;i++)
{
v1-=( ((v0<<4) ^(v0>>5)) +v0 ) ^ ( sum + key[ (sum>>11)&3 ]);
sum-=delta;
v0-=( ((v1<<4) ^ (v1>>5)) +v1 ) ^ ( sum + key[sum&3] );
}
code[0]=v0;
code[1]=v1;
}
int main()
{
unsigned int key[4]={2,2,3,4};
unsigned int r=32;
unsigned int code[2]={0x8DD02793,0x4F558864};
decrypt(r,code,key);
printf("%x %x",code[0],code[1]);
}
void decrypt(unsigned int r ,unsigned int *code ,unsigned int *key)
{
unsigned int v0,v1,i,delta=0x9e3779b9;
unsigned int sum=delta*r;
v0=code[0];
v1=code[1];
for(i=0;i<r;i++)
{
v1-=( ((v0<<4) ^(v0>>5)) +v0 ) ^ ( sum + key[ (sum>>11)&3 ]);
sum-=delta;
v0-=( ((v1<<4) ^ (v1>>5)) +v1 ) ^ ( sum + key[sum&3] );
}
code[0]=v0;
code[1]=v1;
}
int main()
{
unsigned int key[4]={2,2,3,4};
unsigned int r=32;
unsigned int code[2]={0x8DD02793,0x4F558864};
decrypt(r,code,key);
printf("%x %x",code[0],code[1]);
}
int main()
{
int v9[48];
int v7[48]={0};
int v4[]={1,1,2,3,4,5,7,8};
char a[]={0xa5,0x4c,0xb6,0xea,0xd0,0xb9,0xb6,0x50,0x40,0xa4,0xda,0x37,0xe4,0xa,0x98,0xf7,0x5e,0x42,0x7f,0x1f,0x2,0xca,0x4e,0x9c,0x96,0xb4,0xdb,0x90,0xa7,0x15,0x12};
char key[]={0x94,0x75,0x81,0xd2,0xfd,0x81,0x9b,0x62,0x73,0xe4,0x91,0x58,0x86,0x6f,0xd8,0xb5,0x3f,0x31,0x14,0x7a,0x76,0xa8,0x2f,0xf0,0xfa,0x97,0xff,0xb5,0xf9,0x33,0x38};
int i;
v9[0] = 81;
v9[1] = 116;
v9[2] = 91;
v9[3] = 49;
v9[4] = 50;
v9[5] = 81;
v9[6] = 100;
v9[7] = 61;
v9[8] = 85;
v9[9] = 77;
v9[10] = 96;
v9[11] = 98;
v9[12] = 84;
v9[13] = 107;
v9[14] = 72;
v9[15] = 59;
v9[16] = 52;
v9[17] = 96;
v9[18] = 83;
v9[19] = 122;
v9[20] = 61;
v9[21] = 52;
v9[22] = 50;
v9[23] = 107;
v9[24] = 71;
v9[25] = 89;
v9[26] = 58;
v9[27] = 96;
v9[28] = 93;
v9[29] = 78;
v9[30] = 49;
v9[31] = 75;
v9[32] = 77;
v9[33] = 83;
v9[34] = 118;
v9[35] = 65;
v9[36] = 79;
v9[37] = 110;
v9[38] = 68;
v9[39] = 126;
v9[40] = 100;
v9[41] = 70;
v9[42] = 63;
v9[43] = 62;
v9[44] = 4;
v9[45] = 5;
v9[46] = 7;
v9[47] = 8;
for(i=0;i<48;i++)
{
v7[i]=v9[i]^v4[i%8];
printf("%c",v7[i]);
}
printf("\nNeepu{");
for(i=0;i<31;i++)
{
printf("%c",a[i]^key[i]);
}
printf("}");
}
//PuY26Tc5TLbaPnO35aQy915cFX8cYK6CLRtBKkCveG==
//Neepu{1978-8-23@Kobe@Basketball
int main()
{
int v9[48];
int v7[48]={0};
int v4[]={1,1,2,3,4,5,7,8};
char a[]={0xa5,0x4c,0xb6,0xea,0xd0,0xb9,0xb6,0x50,0x40,0xa4,0xda,0x37,0xe4,0xa,0x98,0xf7,0x5e,0x42,0x7f,0x1f,0x2,0xca,0x4e,0x9c,0x96,0xb4,0xdb,0x90,0xa7,0x15,0x12};
char key[]={0x94,0x75,0x81,0xd2,0xfd,0x81,0x9b,0x62,0x73,0xe4,0x91,0x58,0x86,0x6f,0xd8,0xb5,0x3f,0x31,0x14,0x7a,0x76,0xa8,0x2f,0xf0,0xfa,0x97,0xff,0xb5,0xf9,0x33,0x38};
int i;
v9[0] = 81;
v9[1] = 116;
v9[2] = 91;
v9[3] = 49;
v9[4] = 50;
v9[5] = 81;
v9[6] = 100;
v9[7] = 61;
v9[8] = 85;
v9[9] = 77;
v9[10] = 96;
v9[11] = 98;
v9[12] = 84;
v9[13] = 107;
v9[14] = 72;
v9[15] = 59;
v9[16] = 52;
v9[17] = 96;
v9[18] = 83;
v9[19] = 122;
v9[20] = 61;
v9[21] = 52;
v9[22] = 50;
v9[23] = 107;
v9[24] = 71;
v9[25] = 89;
v9[26] = 58;
v9[27] = 96;
v9[28] = 93;
v9[29] = 78;
v9[30] = 49;
v9[31] = 75;
v9[32] = 77;
v9[33] = 83;
v9[34] = 118;
v9[35] = 65;
v9[36] = 79;
v9[37] = 110;
v9[38] = 68;
v9[39] = 126;
v9[40] = 100;
v9[41] = 70;
v9[42] = 63;
v9[43] = 62;
v9[44] = 4;
v9[45] = 5;
v9[46] = 7;
v9[47] = 8;
for(i=0;i<48;i++)
{
v7[i]=v9[i]^v4[i%8];
printf("%c",v7[i]);
}
printf("\nNeepu{");
for(i=0;i<31;i++)
{
printf("%c",a[i]^key[i]);
}
printf("}");
}
//PuY26Tc5TLbaPnO35aQy915cFX8cYK6CLRtBKkCveG==
//Neepu{1978-8-23@Kobe@Basketball
from pwn import *
context(arch = 'amd64', os = 'linux')
p = remote('neepusec.club', 18707)
shellcode=
sc=asm(shellcode,arch='amd64',os='linux')
payload = sc
p.send(payload)
p.interactive()
from pwn import *
context(arch = 'amd64', os = 'linux')
p = remote('neepusec.club', 18707)
shellcode=
[培训]传播安全知识、拓宽行业人脉——看雪讲师团队等你加入!
最后于 2021-5-25 21:59
被kanxue编辑
,原因: