逆向一个注册验证算法,之前有前辈逆向过这个过程:
http://bbs.pediy.com/showthread.php?t=11222
查壳,ASPack 2.X,用工具直接脱掉,加载到OD。
输入命令“bp GetDlgItemTextA”F9跑起来。输入用户、密码后确定,程序跳到:
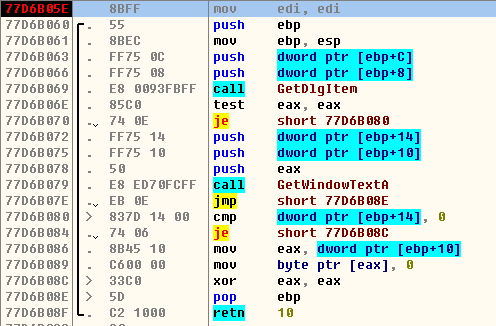
CTRL+F9跳出该函数:
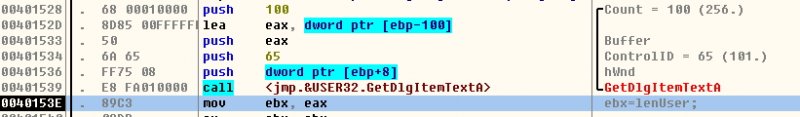
现在查看buffer参数的内容在左下方的内存窗口"CTRL+G"再输入EBP-100查看到了BUFFER的内存,也就是我输到软件里面的帐号,以确定刚刚调用的这个API GetDlgItemTextA是获取帐号用了。。然后单步,一直到1589这个call

发现他压入了刚刚的字符串、字符串长度、句柄,可疑,F7步入函数,观察函数的特征,发现这个函数也调用了GetDlgItemTextA,然后还调用了sprintf,也就是说这个函数获取到我输入的密匙,还有字符串处理。
00401305 /$ 55 push ebp
00401306 |. 89E5 mov ebp, esp
00401308 |. 81EC 2C040000 sub esp, 42C ; 开辟42C个字节空间
0040130E |. 53 push ebx
0040130F |. 56 push esi
00401310 |. 57 push edi
00401311 |. 8DBD FCFEFFFF lea edi, dword ptr [ebp-104]
00401317 |. 8D35 38204000 lea esi, dword ptr [402038]
0040131D |. B9 40000000 mov ecx, 40
00401322 |. F3:A5 rep movs dword ptr es:[edi], dword ptr [esi] ; memcpy(ebp104,402038,sizeof()=0x40);
00401324 |. 8DBD E1FBFFFF lea edi, dword ptr [ebp-41F]
0040132A |. 8D35 38214000 lea esi, dword ptr [402138]
00401330 |. B9 40000000 mov ecx, 40
00401335 |. F3:A5 rep movs dword ptr es:[edi], dword ptr [esi] ; memcpy(ebp41f,402138,40);
00401337 |. 8DBD E1FDFFFF lea edi, dword ptr [ebp-21F]
0040133D |. 8D35 38224000 lea esi, dword ptr [402238]
00401343 |. B9 40000000 mov ecx, 40
00401348 |. F3:A5 rep movs dword ptr es:[edi], dword ptr [esi] ; memcpy(ebp21f,402238,40);
0040134A |. 8DBD E1FCFFFF lea edi, dword ptr [ebp-31F]
00401350 |. 8D35 38234000 lea esi, dword ptr [402338]
00401356 |. B9 40000000 mov ecx, 40
0040135B |. F3:A5 rep movs dword ptr es:[edi], dword ptr [esi] ; memcpy(ebp31f,402338,5);
0040135D |. 8DBD DCFBFFFF lea edi, dword ptr [ebp-424]
00401363 |. 8D35 38244000 lea esi, dword ptr [402438]
00401369 |. B9 05000000 mov ecx, 5
0040136E |. F3:A4 rep movs byte ptr es:[edi], byte ptr [esi] ; memcpy(ebp424,402438,5);
00401370 |. 8DBD D6FBFFFF lea edi, dword ptr [ebp-42A]
00401376 |. 8D35 3D244000 lea esi, dword ptr [40243D]
0040137C |. B9 03000000 mov ecx, 3
00401381 |. F3:66:A5 rep movs word ptr es:[edi], word ptr [esi] ; memcpy(ebp42a,40243d,3);
00401384 |. 8DBD E1FEFFFF lea edi, dword ptr [ebp-11F]
0040138A |. 8D35 43244000 lea esi, dword ptr [402443]
00401390 |. B9 1B000000 mov ecx, 1B
00401395 |. F3:A4 rep movs byte ptr es:[edi], byte ptr [esi] ; memcpy(ebp11f,402443,0x1b);
00401397 |. C745 FC 00000>mov dword ptr [ebp-4], 0 ; int ebp4=0;
0040139E |. 68 00010000 push 100 ; /Count = 100 (256.)
004013A3 |. 8D85 E1FCFFFF lea eax, dword ptr [ebp-31F] ; |
004013A9 |. 50 push eax ; |Buffer
004013AA |. 6A 66 push 66 ; |ControlID = 66 (102.)
004013AC |. FF75 08 push dword ptr [ebp+8] ; |hWnd
004013AF |. E8 84030000 call <jmp.&USER32.GetDlgItemTextA> ; \GetDlgItemTextA
004013B4 |. 09C0 or eax, eax
004013B6 |. 0F84 48010000 je 00401504 ; if(eax==0)return;
004013BC |. B8 CF110000 mov eax, 11CF ; eax=11cf;
004013C1 |. 0FB68D E1FCFF>movzx ecx, byte ptr [ebp-31F] ; ecx=ebp31F[0]
004013C8 |. 99 cdq
004013C9 |. F7F9 idiv ecx ; edx,eax/ecs=eax..........edx
004013CB |. 83FA 17 cmp edx, 17
004013CE |. 74 07 je short 004013D7 ; if(eax%ecx!=0x17)
004013D0 |. 31C0 xor eax, eax ; { eax=0;
004013D2 |. E9 2D010000 jmp 00401504 ; }else
004013D7 |> 31DB xor ebx, ebx ; { ebx=0;
004013D9 |. EB 0B jmp short 004013E6 ; while(ebx<ebpC)
004013DB |> 8B45 10 /mov eax, dword ptr [ebp+10] ; ebp4+=ebp10[ebx++];
004013DE |. 0FBE0418 |movsx eax, byte ptr [eax+ebx]
004013E2 |. 0145 FC |add dword ptr [ebp-4], eax
004013E5 |. 43 |inc ebx
004013E6 |> 3B5D 0C cmp ebx, dword ptr [ebp+C]
004013E9 |.^ 7C F0 \jl short 004013DB ; 此处循环,在else逻辑内
004013EB |. 31DB xor ebx, ebx ; ebx=0;
004013ED |. E9 83000000 jmp 00401475 ; 跳转循环判断
004013F2 |> 8B55 10 /mov edx, dword ptr [ebp+10] ; edx=[ebp10][0].....while(ebx<ebpC)循环体内
004013F5 |. 0FBE3C1A |movsx edi, byte ptr [edx+ebx]
004013F9 |. 8B75 FC |mov esi, dword ptr [ebp-4] ; esi=ebp4
004013FC |. 89D9 |mov ecx, ebx ; ecx=ebx;
004013FE |. C1E1 02 |shl ecx, 2 ; ecx*=4;
00401401 |. 89DA |mov edx, ebx ; edx=ebx;
00401403 |. 42 |inc edx ; edx++;
00401404 |. 29D1 |sub ecx, edx ; ecx-=edx;
00401406 |. 0FB68C0D E1FE>|movzx ecx, byte ptr [ebp+ecx-11F] ; ecx=ebp11f[ecx]
0040140E |. 89FA |mov edx, edi ; edx=edi
00401410 |. 31CA |xor edx, ecx ; edx^=ecx
00401412 |. 89F1 |mov ecx, esi ; ecx=esi
00401414 |. 0FAFCB |imul ecx, ebx ; ecx*=ebx
00401417 |. 29F1 |sub ecx, esi ; ecx=esi
00401419 |. 89CE |mov esi, ecx ; esi=ecx
0040141B |. 83F6 FF |xor esi, FFFFFFFF ; esi=~esi;
0040141E |. 8DB432 4D0100>|lea esi, dword ptr [edx+esi+14D]
00401425 |. 8B4D 0C |mov ecx, dword ptr [ebp+C]
00401428 |. 89DA |mov edx, ebx
0040142A |. 83C2 03 |add edx, 3
0040142D |. 0FAFCA |imul ecx, edx
00401430 |. 0FAFCF |imul ecx, edi
00401433 |. 89F0 |mov eax, esi
00401435 |. 01C8 |add eax, ecx
00401437 |. B9 0A000000 |mov ecx, 0A
0040143C |. 31D2 |xor edx, edx
0040143E |. F7F1 |div ecx
00401440 |. 83C2 30 |add edx, 30
00401443 |. 88941D FCFEFF>|mov byte ptr [ebp+ebx-104], dl
0040144A |. 0FB6BC1D FCFE>|movzx edi, byte ptr [ebp+ebx-104]
00401452 |. 81F7 ACAD0000 |xor edi, 0ADAC
00401458 |. 89DE |mov esi, ebx
0040145A |. 83C6 02 |add esi, 2
0040145D |. 89F8 |mov eax, edi
0040145F |. 0FAFC6 |imul eax, esi
00401462 |. B9 0A000000 |mov ecx, 0A
00401467 |. 99 |cdq
00401468 |. F7F9 |idiv ecx
0040146A |. 83C2 30 |add edx, 30
0040146D |. 88941D FCFEFF>|mov byte ptr [ebp+ebx-104], dl
00401474 |. 43 |inc ebx
00401475 |> 3B5D 0C cmp ebx, dword ptr [ebp+C]
00401478 |.^ 0F8C 74FFFFFF \jl 004013F2 ; for2此处循环在else分支内
0040147E |. 8D85 FCFEFFFF lea eax, dword ptr [ebp-104]
00401484 |. 50 push eax
00401485 |. 6A 54 push 54
00401487 |. 8D85 DCFBFFFF lea eax, dword ptr [ebp-424]
0040148D |. 50 push eax ; |Format
0040148E |. 8D85 E1FBFFFF lea eax, dword ptr [ebp-41F] ; |
00401494 |. 50 push eax ; |s
00401495 |. E8 CE020000 call <jmp.&USER32.wsprintfA> ; \wsprintfA
0040149A |. 8B7D 0C mov edi, dword ptr [ebp+C]
0040149D |. 89F8 mov eax, edi
0040149F |. 0FAF45 FC imul eax, dword ptr [ebp-4]
004014A3 |. B9 64000000 mov ecx, 64
004014A8 |. 99 cdq
004014A9 |. F7F9 idiv ecx
004014AB |. 89D7 mov edi, edx
004014AD |. 83C7 30 add edi, 30
004014B0 |. 57 push edi
004014B1 |. 8DBD E1FBFFFF lea edi, dword ptr [ebp-41F]
004014B7 |. 57 push edi
004014B8 |. 8DBD D6FBFFFF lea edi, dword ptr [ebp-42A]
004014BE |. 57 push edi ; |Format
004014BF |. 8DBD E1FDFFFF lea edi, dword ptr [ebp-21F] ; |
004014C5 |. 57 push edi ; |s
004014C6 |. E8 9D020000 call <jmp.&USER32.wsprintfA> ; \wsprintfA
004014CB |. 83C4 20 add esp, 20
004014CE |. 8D8D E1FDFFFF lea ecx, dword ptr [ebp-21F]
004014D4 |. 83C8 FF or eax, FFFFFFFF
004014D7 |> 40 /inc eax
004014D8 |. 803C01 00 |cmp byte ptr [ecx+eax], 0
004014DC |.^ 75 F9 \jnz short 004014D7
004014DE |. 50 push eax
004014DF |. 8D85 E1FCFFFF lea eax, dword ptr [ebp-31F]
004014E5 |. 50 push eax
004014E6 |. 8D85 E1FDFFFF lea eax, dword ptr [ebp-21F]
004014EC |. 50 push eax
004014ED |. E8 D0FDFFFF call 004012C2
004014F2 |. 83C4 0C add esp, 0C
004014F5 |. 83F8 00 cmp eax, 0
004014F8 |. 75 07 jnz short 00401501
004014FA |. B8 00000000 mov eax, 0
004014FF |. EB 03 jmp short 00401504
00401501 |> 31C0 xor eax, eax
00401503 |. 40 inc eax
00401504 |> 5F pop edi
00401505 |. 5E pop esi
00401506 |. 5B pop ebx
00401507 |. C9 leave
00401508 \. C3 retn
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课