【文章标题】: 我要学英语爆破激活
【文章作者】: 方向迷失
【软件名称】: 我要学英语
【软件大小】: 53 MB
【下载地址】: http://www.51xueyingyu.com/download.html
【加壳方式】: 无壳
【编写语言】: Microsoft Visual Studio .NET 2005 -- 2008
【使用工具】: OD
--------------------------------------------------------------------------------
【详细过程】
由于是爆破,就不多贴出注册算法代码了。
随便输入激活码,然后点击离线激活。进入离线激活界面随便输入注册码,在OD下 bp MessageBoxA 断点命令,断下后Alt + F返回到
004F810A |. 8945 E4 mov [local.7],eax
单步步过一直返回到004D168E
004D167E |. 6A 03 push 0x3 ; /lParam = 3
004D1680 |. 6A 00 push 0x0 ; |wParam = 0
004D1682 |. 68 BE170000 push 0x17BE ; |Message = MSG(17BE)
004D1687 |. 52 push edx ; |hWnd
004D1688 |> FF15 FCA55400 call dword ptr ds:[<&USER32.SendMessa>; \SendMessageA
004D168E |. 8B46 20 mov eax,dword ptr ds:[esi+0x20]
来到上面这段代码就是显示注册信息的地方了,我们单步步过一直返回到04D10BB
004D109B |> \83F8 14 cmp eax,0x14 ; 注册检测分支代码
004D109E |. 0F85 07010000 jnz LearnEng.004D11AB
004D10A4 |. 68 F8BF5900 push LearnEng.0059BFF8 ; x\nW; Case 14 of switch 004D0E24
004D10A9 |. E8 B288FFFF call LearnEng.004C9960 ; 这里可以先不进去,这call用于检测多断信息,不单单用来计算注册码是否正确的。
004D10AE |. 84C0 test al,al
004D10B0 |. 0F85 4F010000 jnz LearnEng.004D1205
004D10B6 |. E8 35040000 call LearnEng.004D14F0 ; 检测注册码,并显示注册信息,跟进。
004D10BB |. 68 F8BF5900 push LearnEng.0059BFF8 ; x\nW
004D10C0 |. E8 9B88FFFF call LearnEng.004C9960 ; 关键
004D10C5 |. 84C0 test al,al ; 注册码是否正确
004D10C7 |. 0F84 38010000 je LearnEng.004D1205
004D10CD |. 6A 00 push 0x0
004D10CF |. 6A 40 push 0x40
004D10D1 |. 6A 01 push 0x1
004D10D3 |. 51 push ecx
004D10D4 |. 8BCC mov ecx,esp
004D10D6 |. 896424 40 mov dword ptr ss:[esp+0x40],esp
004D10DA |. 68 D80E5700 push LearnEng.00570ED8 ; FLBTEBGHFAIRJNDXFTFQHRIFHQ
004D10DF |. E8 FC15F3FF call LearnEng.004026E0
004D10E4 |. 8D4C24 3C lea ecx,dword ptr ss:[esp+0x3C]
004D10E8 |. E8 B317F5FF call LearnEng.004228A0
004D10ED |. 83C4 08 add esp,0x8
004D10F0 |. C74424 48 080>mov dword ptr ss:[esp+0x48],0x8
004D10F8 |. 8B00 mov eax,dword ptr ds:[eax]
004D10FA |. 50 push eax
004D10FB |. E8 93720200 call LearnEng.004F8393
004D1100 |. 8D4C24 2C lea ecx,dword ptr ss:[esp+0x2C]
004D1104 |. C74424 40 FFF>mov dword ptr ss:[esp+0x40],-0x1
004D110C |. E8 BF16F3FF call LearnEng.004027D0
004D1111 |. 8BCE mov ecx,esi
004D1113 |. E8 A94D0200 call LearnEng.004F5EC1
004D1118 |. 8B0D 60BF5900 mov ecx,dword ptr ds:[0x59BF60]
004D111E |. 8B51 20 mov edx,dword ptr ds:[ecx+0x20]
004D1121 |. 6A 00 push 0x0 ; /lParam = 0
004D1123 |. 6A 00 push 0x0 ; |wParam = 0
004D1125 |. 6A 10 push 0x10 ; |Message = WM_CLOSE
004D1127 |. 52 push edx ; |hWnd
004D1128 |. FF15 FCA55400 call dword ptr ds:[<&USER32.SendMes>; \关闭软件窗口
004D112E |. 8D7424 2C lea esi,dword ptr ss:[esp+0x2C]
004D1132 |. E8 59E7F4FF call LearnEng.0041F890 ; 获取配置信息LearnEnglish.ini
004D1137 |. 8B0D E4BF5900 mov ecx,dword ptr ds:[0x59BFE4]
004D113D |. 8B00 mov eax,dword ptr ds:[eax]
004D113F |. 51 push ecx ; /FileName => "E:\51xueyingyu\LearnEnglish.ini"
004D1140 |. 68 143C5500 push LearnEng.00553C14 ; |0
004D1145 |. 68 C0355500 push LearnEng.005535C0 ; |KillProcess
004D114A |. 50 push eax ; |Section
004D114B |. FF15 6CA35400 call dword ptr ds:[<&KERNEL32.Write>; \写到配置信息
004D1151 |. 8BCE mov ecx,esi
004D1153 |. E8 7816F3FF call LearnEng.004027D0
004D1158 |. 8D4C24 0C lea ecx,dword ptr ss:[esp+0xC]
004D115C |. E8 AF1DF3FF call LearnEng.00402F10
004D1161 |. 8D7424 2C lea esi,dword ptr ss:[esp+0x2C]
004D1165 |. C74424 40 090>mov dword ptr ss:[esp+0x40],0x9
004D116D |. E8 2EE8F4FF call LearnEng.0041F9A0
004D1172 |. C64424 40 0A mov byte ptr ss:[esp+0x40],0xA
004D1177 |. 8B10 mov edx,dword ptr ds:[eax]
004D1179 |. 52 push edx
004D117A |. 8D4424 10 lea eax,dword ptr ss:[esp+0x10]
004D117E |. 68 003D5500 push LearnEng.00553D00 ; %s -C
004D1183 |. 50 push eax
004D1184 |. E8 3715F3FF call LearnEng.004026C0
004D1189 |. 83C4 0C add esp,0xC
004D118C |. 8BCE mov ecx,esi
004D118E |. E8 3D16F3FF call LearnEng.004027D0
004D1193 |. 8B4C24 0C mov ecx,dword ptr ss:[esp+0xC]
004D1197 |. 6A 05 push 0x5 ; /ShowState = SW_SHOW
004D1199 |. 51 push ecx ; |CmdLine
004D119A |. FF15 70A35400 call dword ptr ds:[<&KERNEL32.WinEx>; \重启程序
004D11A0 |. 8D4C24 0C lea ecx,dword ptr ss:[esp+0xC]
004D11A4 |. E8 2716F3FF call LearnEng.004027D0
然后我们在
004D109B |> \83F8 14 cmp eax,0x14
断下点,断下后直接运行,然后重来。
点击激活按钮,断在04D10BB。
跟进
004D10B6 |. E8 35040000 call LearnEng.004D14F0
来到
004D1634 |. 8907 mov dword ptr ds:[edi],eax
004D1636 |. 68 F8BF5900 push LearnEng.0059BFF8 ; x\nW
004D163B |. C64424 34 02 mov byte ptr ss:[esp+0x34],0x2
004D1640 |. E8 6B97FFFF call LearnEng.004CADB0 ; 激活码检测
004D1645 |. 84C0 test al,al
004D1647 75 15 jnz XLearnEng.004D165E
004D1649 |. 8B56 20 mov edx,dword ptr ds:[esi+0x20]
004D164C |. 6A 02 push 0x2 ; /lParam = 2
004D164E |. 6A 00 push 0x0 ; |wParam = 0
004D1650 |. 68 BE170000 push 0x17BE ; |Message = MSG(17BE)
004D1655 |. 52 push edx ; |hWnd
004D1656 |. FF15 FCA55400 call dword ptr ds:[<&USER32.SendMessa>; \SendMessageA
004D165C |. EB 3E jmp XLearnEng.004D169C
004D165E |> 68 F8BF5900 push LearnEng.0059BFF8 ; x\nW
004D1663 |. E8 F882FFFF call LearnEng.004C9960 ; 注册码检测,关键CALL,重启验证会用到。F7跟进。
004D1668 |. 84C0 test al,al
004D166A |. 74 0F je XLearnEng.004D167B
004D166C |. 8B4E 20 mov ecx,dword ptr ds:[esi+0x20]
004D166F |. 6A 00 push 0x0
004D1671 |. 6A 00 push 0x0
004D1673 |. 68 BE170000 push 0x17BE
004D1678 |. 51 push ecx
004D1679 |. EB 0D jmp XLearnEng.004D1688
004D167B |> 8B56 20 mov edx,dword ptr ds:[esi+0x20]
004D167E |. 6A 03 push 0x3 ; /lParam = 3
004D1680 |. 6A 00 push 0x0 ; |wParam = 0
004D1682 |. 68 BE170000 push 0x17BE ; |Message = MSG(17BE)
004D1687 |. 52 push edx ; |hWnd
004D1688 |> FF15 FCA55400 call dword ptr ds:[<&USER32.SendMessa>; \SendMessageA
跟入
004D1663 |. E8 F882FFFF call LearnEng.004C9960 ;
来到
004C99A9 . 8906 mov dword ptr ds:[esi],eax
004C99AB . E8 B04CF5FF call LearnEng.0041E660
004C99B0 . 83C4 04 add esp,0x4
004C99B3 . 84C0 test al,al
004C99B5 0F84 0E0D0000 je LearnEng.004CA6C9 ; 这直接按Enter跳到跳转地址
004CA6C9 32C0 xor al,al ; 这里改成mov al,0x1,注册验证不正确都会来到这里把al清0
004CA6CB . 8B4D F4 mov ecx,dword ptr ss:[ebp-0xC]
004CA6CE . 64:890D 00000>mov dword ptr fs:[0],ecx
改完后我们复制到可执行文件,然后我们重启软件并运行。
然后运行后发现这个信息框
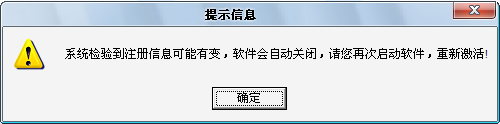
软件另有检测,我们在OD下 bp MessageBoxA 断点命令,然后重启软件并运行。
或者按下,然后ALT+F9返回到用户代码,点击信息框确定按钮就返回。
单步步过一直返回到004068F8
0040687B . 50 push eax
0040687C . 8D8424 D00500>lea eax,dword ptr ss:[esp+0x5D0]
00406883 . 64:A3 0000000>mov dword ptr fs:[0],eax
00406889 . 8B8424 E00500>mov eax,dword ptr ss:[esp+0x5E0]
00406890 . 3D 5C110000 cmp eax,0x115C ; Switch (cases 15..115C)
00406895 . 8BF9 mov edi,ecx ; 这里断下
00406897 0F85 9B000000 jnz LearnEng.00406938 ; 注册信息是否改变,改变则重启。这里我们改jmp
0040689D . 68 F8BF5900 push LearnEng.0059BFF8 ; x\nW; Case 115C of switch 00406890
004068A2 . E8 B9300C00 call LearnEng.004C9960
004068A7 . 0FB6C0 movzx eax,al
004068AA . 3B8424 E40500>cmp eax,dword ptr ss:[esp+0x5E4]
004068B1 0F84 AD010000 je LearnEng.00406A64
004068B7 . 8B35 FCBF5900 mov esi,dword ptr ds:[0x59BFFC]
004068BD . E8 7E940100 call LearnEng.0041FD40
004068C2 . 6A 00 push 0x0
004068C4 . 6A 30 push 0x30
004068C6 . 6A 01 push 0x1
004068C8 . 51 push ecx
004068C9 . 8BCC mov ecx,esp
004068CB . 896424 1C mov dword ptr ss:[esp+0x1C],esp
004068CF . 68 D83E5500 push LearnEng.00553ED8 ; FIIBIMCPIWDVFRHYBWIXFMDXERCFEHAPDLECCQIOFPHBIBJTJIFZDKGTDMAPGMEXETAVIWFFBNCODEAXAFIBCCAPDFBWILFCCWFXFXCGAGABAUGBBRFIHSAACXCVDGCCGUBAFKCRCUEQFK
004068D4 . E8 07BEFFFF call LearnEng.004026E0
004068D9 . 8D4C24 1C lea ecx,dword ptr ss:[esp+0x1C]
004068DD . E8 BEBF0100 call LearnEng.004228A0
004068E2 . 83C4 08 add esp,0x8
004068E5 . C78424 E00500>mov dword ptr ss:[esp+0x5E0],0x0
004068F0 . 8B00 mov eax,dword ptr ds:[eax]
004068F2 . 50 push eax
004068F3 . E8 9B1A0F00 call LearnEng.004F8393 ; 显示注册被改变信息
004068F8 . C78424 D80500>mov dword ptr ss:[esp+0x5D8],-0x1
00406903 . 8B4424 0C mov eax,dword ptr ss:[esp+0xC]
00406907 . 83C0 F0 add eax,-0x10
0040690A . 8D48 0C lea ecx,dword ptr ds:[eax+0xC]
0040690D . 83CA FF or edx,0xFFFFFFFF
00406910 . F0:0FC111 lock xadd dword ptr ds:[ecx],edx
00406914 . 4A dec edx
00406915 . 85D2 test edx,edx
00406917 . 7F 0A jg XLearnEng.00406923
00406919 . 8B08 mov ecx,dword ptr ds:[eax]
0040691B . 8B11 mov edx,dword ptr ds:[ecx]
0040691D . 50 push eax
0040691E . 8B42 04 mov eax,dword ptr ds:[edx+0x4]
00406921 . FFD0 call eax
00406923 > 8B4F 20 mov ecx,dword ptr ds:[edi+0x20]
00406926 . 6A 00 push 0x0 ; /lParam = 0
00406928 . 6A 00 push 0x0 ; |wParam = 0
0040692A . 6A 10 push 0x10 ; |Message = WM_CLOSE
0040692C . 51 push ecx ; |hWnd
0040692D . FF15 FCA55400 call dword ptr ds:[<&USER32.SendMess>; \关闭软件窗口
改完复制到可执行文件后,软件重启,我们发现没显示那信息框了,而且
试下功能,大部分都没问题,不过有一处
这一处看来是有另外的验证
右键->搜索引擎->搜索ASCII
找到“中没有教材,现在是否下载?”
来到这里
004C3F1F . 68 ACFC5600 push LearnEng.0056FCAC ; 【%s】中没有教材,现在是否下载?
004C3F8C . 8D4C24 18 lea ecx,dword ptr ss:[esp+0x18]
004C3F90 . E8 7BEFF3FF call LearnEng.00402F10
004C3F95 . 8DB7 640F0000 lea esi,dword ptr ds:[edi+0xF64]
004C3F9B . 56 push esi
004C3F9C . 8D8F 600F0000 lea ecx,dword ptr ds:[edi+0xF60]
004C3FA2 . 51 push ecx
004C3FA3 . 8D9F 5C0F0000 lea ebx,dword ptr ds:[edi+0xF5C]
004C3FA9 . 8BCD mov ecx,ebp
004C3FAB . 8D97 AC000000 lea edx,dword ptr ds:[edi+0xAC]
004C3FB1 . C74424 60 020>mov dword ptr ss:[esp+0x60],0x2
004C3FB9 . E8 A2ADFFFF call LearnEng.004BED60
004C3FBE . 8B16 mov edx,dword ptr ds:[esi]
004C3FC0 . 8B03 mov eax,dword ptr ds:[ebx]
004C3FC2 . 8B8F 28010000 mov ecx,dword ptr ds:[edi+0x128]
004C3FC8 . 52 push edx
004C3FC9 . 50 push eax
004C3FCA . 51 push ecx
004C3FCB . 8D5424 24 lea edx,dword ptr ss:[esp+0x24]
004C3FCF . 68 C4F45600 push LearnEng.0056F4C4 ; %s\%s\%s.rls
004C3FD4 . 52 push edx
004C3FD5 . E8 E6E6F3FF call LearnEng.004026C0 ; 读取加密文本文件,在Read目录下
004C3FDA . 83C4 14 add esp,0x14
004C3FDD . 8D4424 1C lea eax,dword ptr ss:[esp+0x1C]
004C3FE1 . 50 push eax
004C3FE2 . E8 D9BAF7FF call LearnEng.0043FAC0 ; 读取lec文件
004C3FE7 . 51 push ecx
004C3FE8 . C64424 5C 03 mov byte ptr ss:[esp+0x5C],0x3
004C3FED . 8D5424 1C lea edx,dword ptr ss:[esp+0x1C]
004C3FF1 . 8BCC mov ecx,esp
004C3FF3 . 896424 18 mov dword ptr ss:[esp+0x18],esp
004C3FF7 . 52 push edx
004C3FF8 . E8 63EEF3FF call LearnEng.00402E60
004C3FFD . 8D4424 20 lea eax,dword ptr ss:[esp+0x20]
004C4001 . 50 push eax
004C4002 . E8 D9BFF7FF call LearnEng.0043FFE0 ; 解密文本,这里跟进去
004C4007 . 8B4C24 20 mov ecx,dword ptr ss:[esp+0x20]
004C400B . 898F 680F0000 mov dword ptr ds:[edi+0xF68],ecx
004C4011 . 8D8F 6C0F0000 lea ecx,dword ptr ds:[edi+0xF6C]
004C4017 . 8D4424 2C lea eax,dword ptr ss:[esp+0x2C]
004C401B . E8 50DBF7FF call LearnEng.00441B70
004C4020 . 8BDF mov ebx,edi
004C4022 . E8 990F0000 call LearnEng.004C4FC0 ; 显示已解密的限制文本
004C4027 . 8D4C24 1C lea ecx,dword ptr ss:[esp+0x1C]
004C402B . C64424 58 02 mov byte ptr ss:[esp+0x58],0x2
004C4030 . E8 4BBEF7FF call LearnEng.0043FE80
004C4035 . 8D4C24 18 lea ecx,dword ptr ss:[esp+0x18]
004C4039 . C74424 58 FFF>mov dword ptr ss:[esp+0x58],-0x1
004C4041 . E8 8AE7F3FF call LearnEng.004027D0
004C4046 > 8BCF mov ecx,edi
004C4048 . E8 B8180300 call LearnEng.004F5905
004C404D . 8B5424 64 mov edx,dword ptr ss:[esp+0x64]
004C4051 . C702 00000000 mov dword ptr ds:[edx],0x0
进入0043FFE0来到这里
00440613 |. 394E 0C |cmp dword ptr ds:[esi+0xC],ecx ; 是否隐藏文本
00440616 0F8E A6000000 jle LearnEng.004406C2 ; 这里把jie改成jmp
复制到可执行文件后我们来看看
已经没问题了!
感谢chixiaojie 提出以下几个暗装
这里只能选第一章
在004C9960断下点,执行返回到
004A26C5 |. 84C0 test al,al
来到
004A28FC |. 51 push ecx
004A28FD |. 8D43 7C lea eax,dword ptr ds:[ebx+0x7C] ; 赋值章节指针文本到eax
004A2900 |. 8BCC mov ecx,esp
004A2902 |. 896424 28 mov dword ptr ss:[esp+0x28],esp
004A2906 |. 50 push eax
004A2907 |. E8 5405F6FF call LearnEng.00402E60 ; 以明文显示章节指针文本
004A290C |. 8D8C24 800000>lea ecx,dword ptr ss:[esp+0x80]
004A2913 |. E8 680DFAFF call LearnEng.00443680 ; 显示章节单词,这里跟进
0044380D |. 51 push ecx
0044380E |. 83C0 10 add eax,0x10
00443811 |. 57 push edi
00443812 |. 8906 mov dword ptr ds:[esi],eax ; 赋值章节数
00443814 |. E8 77030000 call LearnEng.00443B90 ; 这里就是没注册把章节改成1,跟进
跟进00443B90后我们要注意LearnEnglish.lec文件不能为空,直接用nop填空跳转执行到下面程序会崩溃
00443BEA |. 84C0 test al,al ; Credit\LearnEnglish.lec是否存在
00443BEC |. 0F84 EB020000 je LearnEng.00443EDD
用原来未修改的LearnEnglish.exe进行随便离线激活,然后就生成LearnEnglish.lec了,不过在启动时它会验证是否正确,不正确就删除,我们要防止删除,防止在验证lec文件时程序崩溃。
重新载入程序,断下bp DeleteFileW
断下后一直返回到
00406A99 . 8BF9 mov edi,ecx
00406A9B /EB 61 je XLearnEng.00406AFE ; 这里改成jmp
00406A9D . 83F8 0D cmp eax,0xD
00406AA0 . 74 41 je XLearnEng.00406AE3
00406AA2 . 83F8 12 cmp eax,0x12
00406AA5 . 74 3C je XLearnEng.00406AE3
00406AA7 . 83F8 0E cmp eax,0xE
00406AAA . 74 05 je XLearnEng.00406AB1
00406AAC . 83F8 0F cmp eax,0xF
00406AAF . 75 4D jnz XLearnEng.00406AFE
00406AB1 > 8B35 FCBF5900 mov esi,dword ptr ds:[0x59BFFC]
00406AB7 . E8 84920100 call LearnEng.0041FD40 ; 文件删除
00406ABC . 8B4424 0C mov eax,dword ptr ss:[esp+0xC]
00406AC0 . 8B08 mov ecx,dword ptr ds:[eax]
00406AC2 . 6A 00 push 0x0
00406AC4 . 6A 10 push 0x10
00406AC6 . 51 push ecx
00406AC7 . E8 C7180F00 call LearnEng.004F8393
00406ACC . 8B57 20 mov edx,dword ptr ds:[edi+0x20]
00406ACF . 6A 00 push 0x0 ; /lParam = 0
00406AD1 . 6A 00 push 0x0 ; |wParam = 0
00406AD3 . 6A 10 push 0x10 ; |Message = WM_CLOSE
00406AD5 . 52 push edx ; |hWnd
00406AD6 . FF15 FCA55400 call dword ptr ds:[<&USER32.SendMessageA>; \SendMessageA
00406ADC . 5F pop edi
00406ADD . 33C0 xor eax,eax
00406ADF . 5E pop esi
00406AE0 . C2 0800 retn 0x8
00406AE3 > 8B35 FCBF5900 mov esi,dword ptr ds:[0x59BFFC]
00406AE9 . E8 52920100 call LearnEng.0041FD40 ; 文件删除
00406AEE . 8B47 20 mov eax,dword ptr ds:[edi+0x20]
00406AF1 . 6A 00 push 0x0 ; /lParam = 0
00406AF3 . 6A 00 push 0x0 ; |wParam = 0
00406AF5 . 6A 10 push 0x10 ; |Message = WM_CLOSE
00406AF7 . 50 push eax ; |hWnd
00406AF8 . FF15 FCA55400 call dword ptr ds:[<&USER32.SendMessageA>; \SendMessageA
00406AFE > 5F pop edi
00406AFF . 33C0 xor eax,eax
00406B01 . 5E pop esi
00406B02 . C2 0800 retn 0x8
在这两处跳转用nop填空,以免把章节改成第一章
00444313 /0F84 34040000 je LearnEng.0044474D
00444440 /0F84 8B000000 je LearnEng.004444D1
然后这里跟上面那段代码基本一样,就是少了lea eax,dword ptr ds:[ebx+0x7C]初始选择章节的赋值。
这里用于二次检测,未激活软件就把章节改成1,我们把lea eax,dword ptr ds:[ebx+0x7C]加上去。
004A2943 51 push ecx
004A2944 8BCC mov ecx,esp
004A2946 896424 28 mov dword ptr ss:[esp+0x28],esp
004A294A |. 50 push eax
004A294B |. E8 1005F6FF call LearnEng.00402E60
004A2950 |. 8D8C24 800000>lea ecx,dword ptr ss:[esp+0x80]
004A2957 |. E8 240DFAFF call LearnEng.00443680
找个空地方,把这些代码复制上去
lea eax,dword ptr ds:[ebx+0x7C]
push ecx
mov ecx,esp
mov dword ptr ss:[esp+0x28],esp
然后在004A2943 jmp 到空代码处再jmp回004A294A
004A2943 /E9 7E680A00 jmp LearnEng.005491C6
004A2948 |90 nop
004A2949 |90 nop
004A294A |. |50 push eax
004A294B |. |E8 1005F6FF call LearnEng.00402E60
004A2950 |. |8D8C24 800000>lea ecx,dword ptr ss:[esp+0x80]
004A2957 |. |E8 240DFAFF call LearnEng.00443680
005491C6 8D43 7C lea eax,dword ptr ds:[ebx+0x7C]
005491C9 51 push ecx
005491CA 8BCC mov ecx,esp
005491CC 896424 28 mov dword ptr ss:[esp+0x28],esp
005491D0 ^ E9 7597F5FF jmp LearnEng.004A294A
我们复制到可执行文件看看
OK,已没问题了。
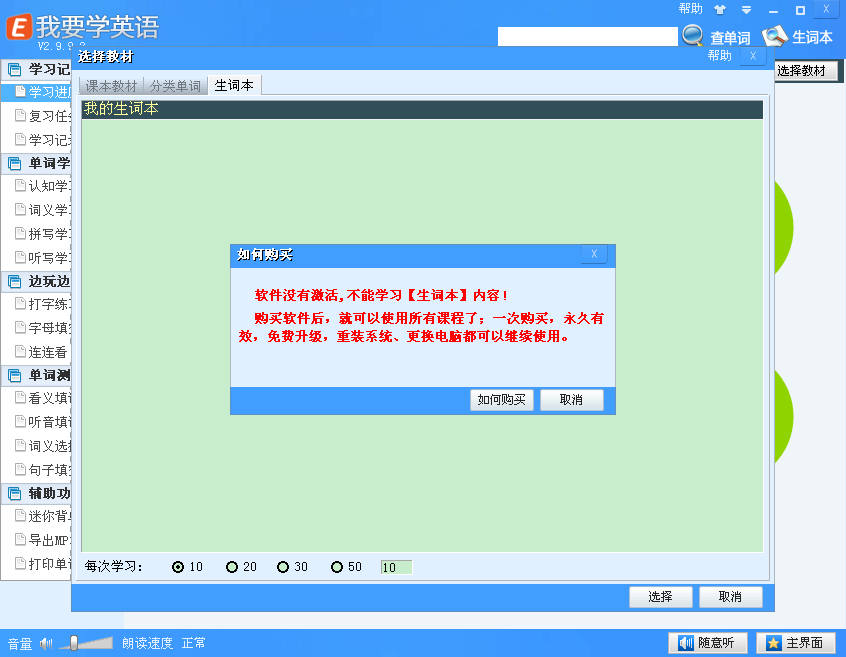
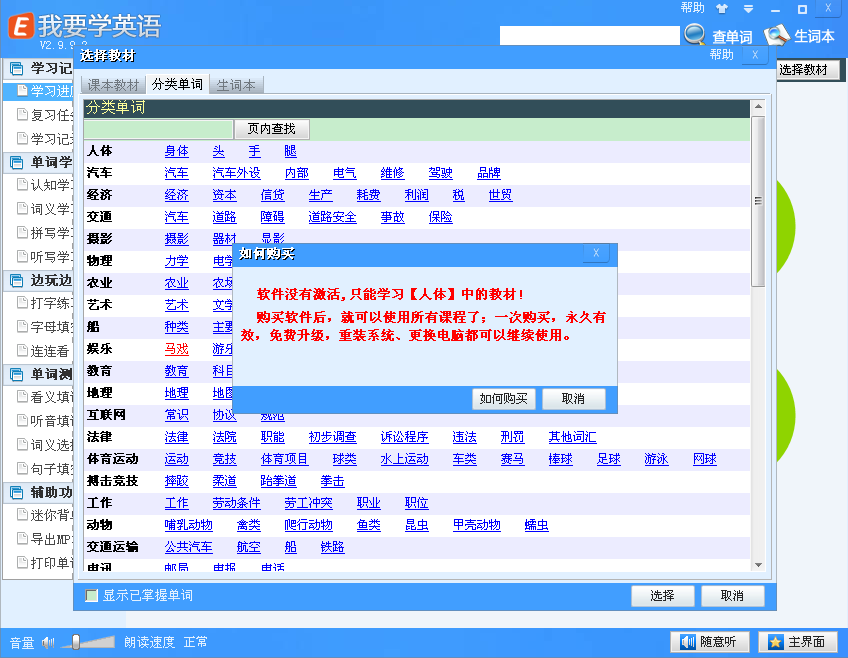
这些地方点击创建教材或修改教材就会弹出购买的窗口
右键搜索ASCII,找到“如何购买”,在开头断下点
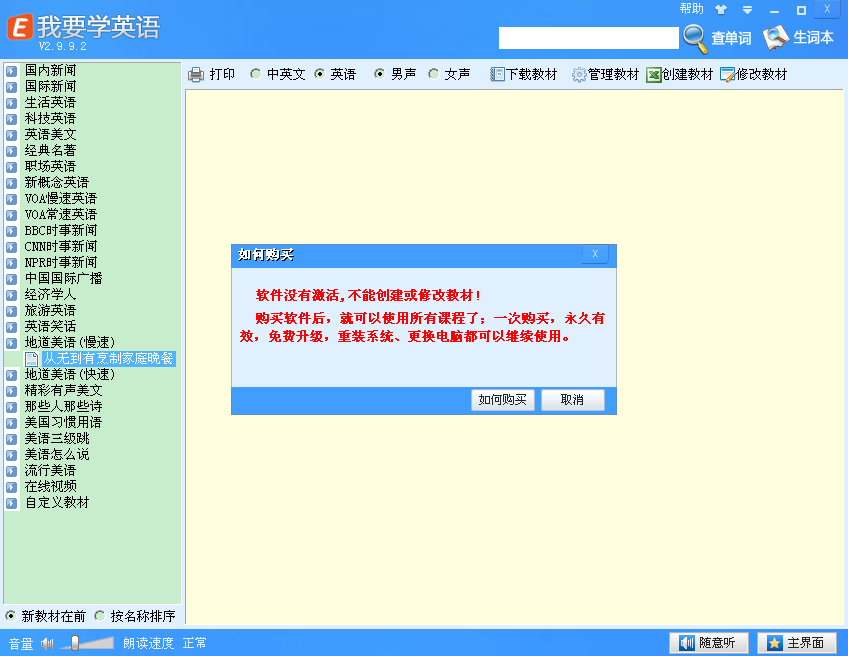
首先创建教材的:
断下后一直执行返回到
004C482B |> \399F D00F0000 cmp dword ptr ds:[edi+0xFD0],ebx
004C4831 |. 75 1C jnz XLearnEng.004C484F ; 以下代码就是弹出购买窗口,这里改jmp
004C4833 |. A1 60BF5900 mov eax,dword ptr ds:[0x59BF60]
004C4838 |. 8B48 20 mov ecx,dword ptr ds:[eax+0x20]
004C483B |. 53 push ebx ; /lParam
004C483C |. 6A 1F push 0x1F ; |wParam = 1F
004C483E |. 68 5C150000 push 0x155C ; |Message = MSG(155C)
004C4843 |. 51 push ecx ; |hWnd
004C4844 |. FF15 FCA55400 call dword ptr ds:[<&USER32.SendMessageA>; \SendMessageA
004C484A |. E9 BB050000 jmp LearnEng.004C4E0A
修改教材的:
断下后一直执行返回到
004C4E77 |. /75 1D jnz XLearnEng.004C4E96 ; 以下代码就是弹出购买窗口,这里改jmp
004C4E79 |. |A1 60BF5900 mov eax,dword ptr ds:[0x59BF60]
004C4E7E |. |8B48 20 mov ecx,dword ptr ds:[eax+0x20]
004C4E81 |. |6A 00 push 0x0 ; /lParam = 0
004C4E83 |. |6A 1F push 0x1F ; |wParam = 1F
004C4E85 |. |68 5C150000 push 0x155C ; |Message = MSG(155C)
004C4E8A |. |51 push ecx ; |hWnd
004C4E8B |. |FF15 FCA55400 call dword ptr ds:[<&USER32.SendMessageA>; \SendMessageA
004C4E91 |. |E9 CE000000 jmp LearnEng.004C4F64
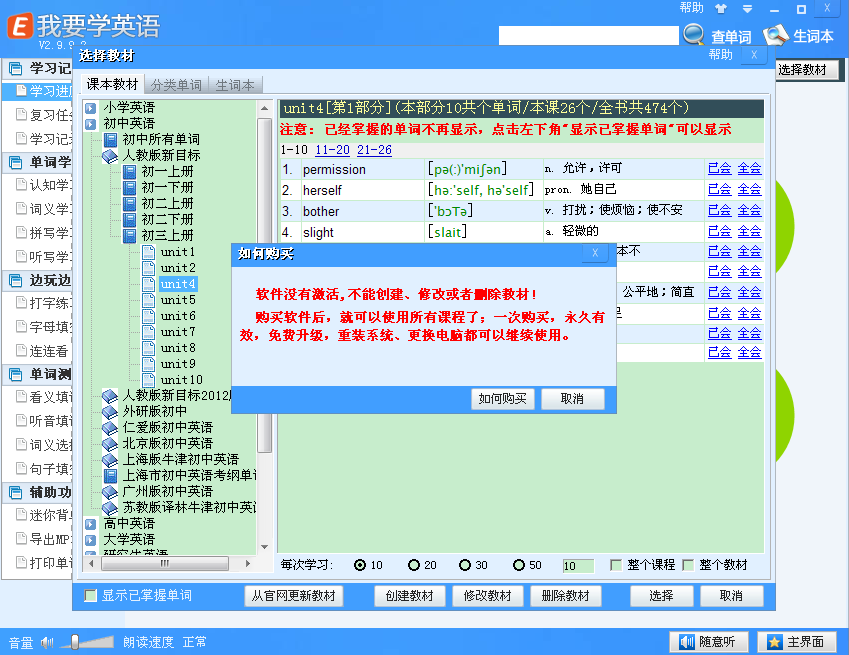
断下后一直执行返回到
0049D5F9 |> \83BB 50020000>cmp dword ptr ds:[ebx+0x250],0x0
0049D600 |. 75 17 jnz XLearnEng.0049D619 ; 以下代码就是弹出购买窗口,这里改jmp
0049D602 |. 8B53 20 mov edx,dword ptr ds:[ebx+0x20]
0049D605 |. 6A 00 push 0x0
0049D607 |. 6A 01 push 0x1
0049D609 |. 68 5C150000 push 0x155C
0049D60E |. 52 push edx
0049D60F |. FFD7 call edi
0049D611 |. 83C8 FF or eax,0xFFFFFFFF
0049D695 |. /75 17 jnz XLearnEng.0049D6AE ; 以下代码就是弹出购买窗口,这里改jmp
0049D697 |. |8B4B 20 mov ecx,dword ptr ds:[ebx+0x20]
0049D69A |. |6A 00 push 0x0
0049D69C |. |6A 02 push 0x2
0049D69E |. |68 5C150000 push 0x155C
0049D6A3 |. |51 push ecx
0049D6A4 |. |FFD7 call edi
断下后一直执行返回到
004AFCCE > \807C24 34 00 cmp byte ptr ss:[esp+0x34],0x0
004AFCD3 . 74 2B je XLearnEng.004AFD00 ; 以下代码就是弹出购买窗口,这里改jmp
004AFCD5 . 8BCF mov ecx,edi
004AFCD7 . E8 24B2F5FF call LearnEng.0040AF00
004AFCDC . 8B50 20 mov edx,dword ptr ds:[eax+0x20]
004AFCDF . 6A 00 push 0x0 ; /lParam = 0
004AFCE1 . 6A 04 push 0x4 ; |wParam = 4
004AFCE3 . 68 5C150000 push 0x155C ; |Message = MSG(155C)
004AFCE8 . 52 push edx ; |hWnd
004AFCE9 . FF15 FCA55400 call dword ptr ds:[<&USER32.SendMessageA>; \SendMessageA
004AFCEF . 8D4C24 14 lea ecx,dword ptr ss:[esp+0x14]
End...
分析文档.doc
[注意]传递专业知识、拓宽行业人脉——看雪讲师团队等你加入!