外面跑了一个星期,回来看到我的北斗变形程序好多疑问,我想补充说明一下:
一、程序肯定有不完善的地方,需要改进,因此公布出来征求意见,大家可以把变形后不能运行的原程序传给我,方便我改进。我只是业余研究,没有任何商业目的。我的QQ:85495610。
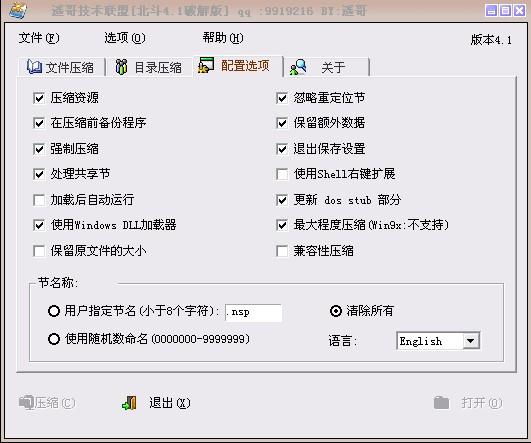
二、如果变形的时候提示“选项错误或者文件格式不对”,那是压缩选项选择不对,程序的压缩选项如下图,一定要按照这些设置,因为我的程序有针对性的。最好把需要变形的程序和bx02.exe放在同一目录下。运行变形后的程序时最好把360之类的软件关闭掉。
三、如果昨天能运行,今天不能运行,最大的可能是你今天运行的时候同时打开了OD,因为我的程序是可以检测OD的,在OD里是更不能运行变形后的程序的。详见我的文章《反StrongOD的原理和实例》http://bbs.pediy.com/showthread.php?t=139657。
四、我提供的变形后的calc.exe和notepad.exe是XP的SP2系统里的,如果用在64位或者linux系统,我想肯定会出错。我系统里装有XP的SP2和SP3、WINDOWS 7.0和WINDOWS 2003,在这些系统里我测试过这二个变形后的程序,可以正常运行。
五、变形程序里的DEL和REN是DOS命令,如果你的系统连这二条命令都不能执行的话,就不要考虑用这个变形程序了。
六、附件中的calc_yuanxing.exe是程序的原形。就是还没有变形过的shellcode脱壳代码,运用VMP变形的一个好处就是每变形一次,就会产生一个不同的变形代码。这段shellcode脱壳代码非常简单,总共只有约300 byte,经过VMP变形可以达到5000 byte。代码中我就用了二个反调试。一个就是NtQueryObject反调试,另外一个是ZwClose反调试。附件中的calc_ya.exe和notepad_ya.exe是经过北斗压缩过还没有变形的程序,方便大家测试。
calc_yuanxing.exe程序代码说明:
01020000 calc_yua.<ModuleE> 8BFF mov edi,edi ; ntdll.7C930228
01020002 55 push ebp
01020003 8BEC mov ebp,esp
01020005 81EC 00010000 sub esp,100
0102000B 51 push ecx
0102000C 52 push edx
0102000D 53 push ebx
0102000E 56 push esi
0102000F 57 push edi
01020010 E8 00000000 call calc_yua.01020015
01020015 5B pop ebx
01020016 81C3 EB0C0000 add ebx,0CEB ; ebx为数据区内存地址
0102001C 8BCB mov ecx,ebx
0102001E 83C1 10 add ecx,10
01020021 33D2 xor edx,edx
01020023 8331 56 xor dword ptr ds:[ecx],56 ; 解密数据区的字符
01020026 41 inc ecx
01020027 42 inc edx
01020028 83FA 15 cmp edx,15
0102002B ^ 75 F6 jnz short calc_yua.01020023
0102002D 33C9 xor ecx,ecx
0102002F 64:8B71 30 mov esi,dword ptr fs:[ecx+30]
01020033 8B76 0C mov esi,dword ptr ds:[esi+C]
01020036 8B76 1C mov esi,dword ptr ds:[esi+1C]
01020039 8B46 08 mov eax,dword ptr ds:[esi+8]
0102003C 8B7E 20 mov edi,dword ptr ds:[esi+20]
0102003F 8B36 mov esi,dword ptr ds:[esi]
01020041 66:394F 18 cmp word ptr ds:[edi+18],cx
01020045 ^ 75 F2 jnz short calc_yua.01020039
01020047 50 push eax
01020048 8F45 FC pop dword ptr ss:[ebp-4] ; [ebp-4]为kernel32.dll的基址
0102004B 68 0EB45C23 push 235CB40E
01020050 810424 9F1DD81D add dword ptr ss:[esp],1DD81D9F
01020057 FF75 FC push dword ptr ss:[ebp-4]
0102005A 6A 00 push 0
0102005C E8 9F0B0000 call calc_yua.01020C00
01020061 8945 F8 mov dword ptr ss:[ebp-8],eax ; [ebp-8]为LoadLibraryA内存地址
01020064 833B 00 cmp dword ptr ds:[ebx],0
01020067 74 2C je short calc_yua.01020095
01020069 0FB70B movzx ecx,word ptr ds:[ebx]
0102006C 03CB add ecx,ebx
0102006E 51 push ecx
0102006F FF55 F8 call dword ptr ss:[ebp-8]
01020072 8BF8 mov edi,eax
01020074 0FB74B 02 movzx ecx,word ptr ds:[ebx+2]
01020078 03CB add ecx,ebx
0102007A 8339 00 cmp dword ptr ds:[ecx],0
0102007D 74 11 je short calc_yua.01020090
0102007F FF31 push dword ptr ds:[ecx]
01020081 57 push edi
01020082 6A 00 push 0
01020084 E8 770B0000 call calc_yua.01020C00
01020089 8901 mov dword ptr ds:[ecx],eax ; 取得各API函数的内存值,用于反调试
0102008B 83C1 04 add ecx,4
0102008E ^ EB EA jmp short calc_yua.0102007A
01020090 83C3 04 add ebx,4
01020093 ^ EB CF jmp short calc_yua.01020064
01020095 83EB 0C sub ebx,0C
01020098 FF75 F8 push dword ptr ss:[ebp-8]
0102009B 8F83 5C010000 pop dword ptr ds:[ebx+15C] ; 脱壳用的LoadLibraryA
010200A1 FF73 50 push dword ptr ds:[ebx+50]
010200A4 8F83 60010000 pop dword ptr ds:[ebx+160] ; 脱壳用的GetProcAddress
010200AA FF73 34 push dword ptr ds:[ebx+34]
010200AD 8F83 64010000 pop dword ptr ds:[ebx+164] ; 脱壳用的VirtualProtect
010200B3 FF73 30 push dword ptr ds:[ebx+30]
010200B6 8F83 68010000 pop dword ptr ds:[ebx+168] ; 脱壳用的VirtualAlloc
010200BC FF73 38 push dword ptr ds:[ebx+38]
010200BF 8F83 6C010000 pop dword ptr ds:[ebx+16C] ; 脱壳用的VirtualFree
010200C5 FF73 40 push dword ptr ds:[ebx+40]
010200C8 8F83 70010000 pop dword ptr ds:[ebx+170] ; 脱壳用的ExitProcess
010200CE 6A 40 push 40 ; 申请内存,用于NtQueryObject反调试和解压代码
010200D0 68 00100000 push 1000
010200D5 68 00200000 push 2000
010200DA 6A 00 push 0
010200DC FF53 30 call dword ptr ds:[ebx+30] ; kernel32.VirtualAlloc
010200DF 8983 9C000000 mov dword ptr ds:[ebx+9C],eax
010200E5 6A 40 push 40 ; 申请内存,用于放置压缩体代码
010200E7 68 00100000 push 1000
010200EC FFB3 A8000000 push dword ptr ds:[ebx+A8]
010200F2 6A 00 push 0
010200F4 FF53 30 call dword ptr ds:[ebx+30] ; kernel32.VirtualAlloc
010200F7 8983 A8000000 mov dword ptr ds:[ebx+A8],eax
010200FD 6A 00 push 0 ; NtQueryObject反调试开始
010200FF 68 00200000 push 2000
01020104 FFB3 9C000000 push dword ptr ds:[ebx+9C]
0102010A 6A 03 push 3
0102010C 6A 00 push 0
0102010E FF93 88000000 call dword ptr ds:[ebx+88] ; ntdll.ZwQueryObject
01020114 36:8B8B 9C000000 mov ecx,dword ptr ss:[ebx+9C]
0102011B 33D2 xor edx,edx
0102011D 81FA E01F0000 cmp edx,1FE0
01020123 74 51 je short calc_yua.01020176
01020125 8039 44 cmp byte ptr ds:[ecx],44
01020128 75 3E jnz short calc_yua.01020168
0102012A 8079 02 65 cmp byte ptr ds:[ecx+2],65
0102012E 75 38 jnz short calc_yua.01020168
01020130 8079 04 62 cmp byte ptr ds:[ecx+4],62
01020134 75 32 jnz short calc_yua.01020168
01020136 8079 06 75 cmp byte ptr ds:[ecx+6],75
0102013A 75 2C jnz short calc_yua.01020168
0102013C 8079 08 67 cmp byte ptr ds:[ecx+8],67
01020140 75 26 jnz short calc_yua.01020168
01020142 8079 0A 4F cmp byte ptr ds:[ecx+A],4F
01020146 75 20 jnz short calc_yua.01020168
01020148 8079 0C 62 cmp byte ptr ds:[ecx+C],62
0102014C 75 1A jnz short calc_yua.01020168
0102014E 8079 0E 6A cmp byte ptr ds:[ecx+E],6A
01020152 75 14 jnz short calc_yua.01020168
01020154 8079 10 65 cmp byte ptr ds:[ecx+10],65
01020158 75 0E jnz short calc_yua.01020168
0102015A 8079 12 63 cmp byte ptr ds:[ecx+12],63
0102015E 75 08 jnz short calc_yua.01020168
01020160 8079 14 74 cmp byte ptr ds:[ecx+14],74
01020164 75 02 jnz short calc_yua.01020168
01020166 EB 04 jmp short calc_yua.0102016C
01020168 41 inc ecx
01020169 42 inc edx
0102016A ^ EB B1 jmp short calc_yua.0102011D
0102016C 83E9 58 sub ecx,58
0102016F 8339 00 cmp dword ptr ds:[ecx],0
01020172 75 02 jnz short calc_yua.01020176
01020174 EB 05 jmp short calc_yua.0102017B
01020176 6A 00 push 0
01020178 FF53 40 call dword ptr ds:[ebx+40] ; kernel32.ExitProcess
0102017B 8BBB A8000000 mov edi,dword ptr ds:[ebx+A8] ; 将压缩体代码放入内存中
01020181 8BF3 mov esi,ebx
01020183 2BB3 A4000000 sub esi,dword ptr ds:[ebx+A4]
01020189 03B3 F0000000 add esi,dword ptr ds:[ebx+F0]
0102018F 81C6 E0060000 add esi,6E0
01020195 33C0 xor eax,eax
01020197 833E 00 cmp dword ptr ds:[esi],0
0102019A 74 0C je short calc_yua.010201A8
0102019C FF36 push dword ptr ds:[esi]
0102019E 8F07 pop dword ptr ds:[edi]
010201A0 83C6 04 add esi,4
010201A3 83C7 04 add edi,4
010201A6 ^ EB EF jmp short calc_yua.01020197
010201A8 FFB3 9C000000 push dword ptr ds:[ebx+9C] ; 将解压代码放入内存中
010201AE 8BF3 mov esi,ebx
010201B0 2BB3 A4000000 sub esi,dword ptr ds:[ebx+A4]
010201B6 03B3 F0000000 add esi,dword ptr ds:[ebx+F0]
010201BC 56 push esi
010201BD E8 8E090000 call calc_yua.01020B50
010201C2 60 pushad ; 开始解压
010201C3 8BEB mov ebp,ebx
010201C5 81C5 B0000000 add ebp,0B0
010201CB 8BD5 mov edx,ebp
010201CD 2B55 10 sub edx,dword ptr ss:[ebp+10]
010201D0 8955 10 mov dword ptr ss:[ebp+10],edx
010201D3 0155 40 add dword ptr ss:[ebp+40],edx
010201D6 8DB5 84000000 lea esi,dword ptr ss:[ebp+84]
010201DC 0116 add dword ptr ds:[esi],edx
010201DE 0155 04 add dword ptr ss:[ebp+4],edx
010201E1 8B36 mov esi,dword ptr ds:[esi]
010201E3 8BBB A8000000 mov edi,dword ptr ds:[ebx+A8]
010201E9 FFB5 BC000000 push dword ptr ss:[ebp+BC]
010201EF FFB5 B8000000 push dword ptr ss:[ebp+B8]
010201F5 8BD6 mov edx,esi
010201F7 8BCF mov ecx,edi
010201F9 8B83 9C000000 mov eax,dword ptr ds:[ebx+9C]
010201FF 05 A9050000 add eax,5A9
01020204 FFD0 call eax
01020206 61 popad ; 解压结束
01020207 68 00800000 push 8000
0102020C 6A 00 push 0
0102020E FFB3 9C000000 push dword ptr ds:[ebx+9C]
01020214 FF53 38 call dword ptr ds:[ebx+38] ; kernel32.VirtualFree
01020217 68 00800000 push 8000
0102021C 6A 00 push 0
0102021E FFB3 A8000000 push dword ptr ds:[ebx+A8]
01020224 FF53 38 call dword ptr ds:[ebx+38] ; kernel32.VirtualFree
01020227 33C9 xor ecx,ecx
01020229 51 push ecx
0102022A 51 push ecx
0102022B 51 push ecx
0102022C 51 push ecx
0102022D 51 push ecx
0102022E 51 push ecx
0102022F 51 push ecx
01020230 51 push ecx
01020231 83C4 20 add esp,20
01020234 68 88A9CBED push EDCBA988
01020239 FF93 90000000 call dword ptr ds:[ebx+90] ; ntdll.ZwClose反调试
0102023F 837C24 F0 00 cmp dword ptr ss:[esp-10],0
01020244 ^ 75 DE jnz short calc_yua.01020224
01020246 8B83 A0000000 mov eax,dword ptr ds:[ebx+A0]
0102024C 05 5FC30000 add eax,0C35F ; 设置入口点的值为数据区相应值加0C35F
01020251 8BD3 mov edx,ebx
01020253 2B93 A4000000 sub edx,dword ptr ds:[ebx+A4]
01020259 03C2 add eax,edx
0102025B 8BCB mov ecx,ebx
0102025D 81E9 000D0000 sub ecx,0D00
01020263 83C1 05 add ecx,5
01020266 50 push eax
01020267 2BC1 sub eax,ecx
01020269 C641 FB E9 mov byte ptr ds:[ecx-5],0E9
0102026D 8941 FC mov dword ptr ds:[ecx-4],eax ; 设置现入口点,使其跳至入口点,DLL用
01020270 58 pop eax
01020271 5F pop edi
01020272 5E pop esi
01020273 5B pop ebx
01020274 5A pop edx
01020275 59 pop ecx
01020276 81C4 00010000 add esp,100
0102027C 5D pop ebp
0102027D FFE0 jmp eax ; 跳至入口点
[招生]系统0day安全班,企业级设备固件漏洞挖掘,Linux平台漏洞挖掘!