|
|
[讨论]分析
sample without password |
|
|
|
|
|
[求助]PaiMei的“pida_dump.py”和IDA 5.5兼容不好?有别的开源的代码跟踪工具没?
please refer to our project Paimei, our group member solved the problems and now paimei can run with ida pro 6.1 83eK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3j5I4x3#2)9J5k6r3I4S2j5Y4y4Q4x3X3g2F1k6i4c8Q4x3V1k6H3M7X3!0B7k6h3y4@1i4K6u0W2K9s2c8E0L8l9`.`. |
|
|
[原创]简单云查杀客户端源代码
[QUOTE=hawkish;946697]思路很好,花了点时间,用MFC重写了。。。。 KillVirus.rar 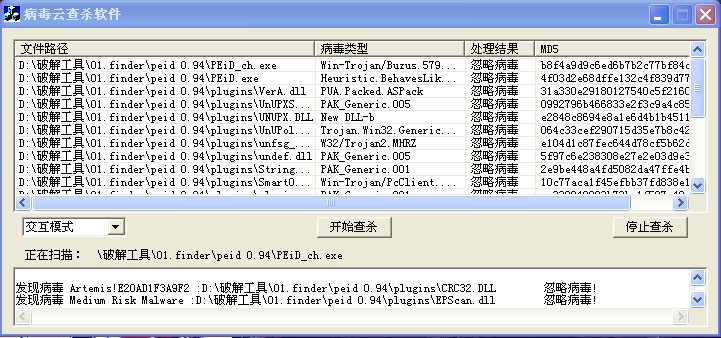 [/QUOTE] [/QUOTE]此工具(由MFC编码)显示这个错误: Microsoft Visual C++ Runtime Library "Runtime Error!" abnormal program termination :( |
|
|
[讨论]iphone开发
可能我问错问题了, 有没有汇编编译器可以使用它来开发iphone应用程序如 masm32? |
|
|
[求助]tasm32 和 masm32
"5b3K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3#2S2M7$3@1K6x3W2)9J5k6h3y4G2L8b7`.`." 误会我写病毒 |
|
|
[下载]Bios Disassembly Ninjutsu Uncovered
Get away from this post if you dont like it. Respect the people bfore other respect you back |
|
|
[讨论]悬赏25万,Conficker病毒作者追踪~~~~
谁有变种A,D样本? |
|
|
|
|
|
[讨论]悬赏25万,Conficker病毒作者追踪~~~~
Problems solve. Procedure unpack: 1. load dll file using ollydbg 2. Press F2 set breakpoint at 1001A00D 3. Press F9 + Press F7 4. Press F2 set breakpoint at 10002EB0 5. Press F9+Press F7 6. Press F2 set breakpoint at 003CF8AD 7. Press F9+Press F7 8. now u can right click and save the content of conficker worm from memory test it using vmware to avoid your system infected. |
|
|
[讨论]悬赏25万,Conficker病毒作者追踪~~~~
The question is: a. How do i set the breakpoint at VirtualProtectEx and dump the segment of this malware? I understand chinese font. Thanks for help. :) |
|
|
[讨论]悬赏25万,Conficker病毒作者追踪~~~~
Hi, all, i downloaded the sample conficker 'atsjshck.rar' [458K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4N6G2L8$3c8E0j5h3&6F1i4K6u0W2j5$3!0E0i4K6u0r3k6X3!0J5N6h3#2Q4x3V1k6K6K9r3!0%4N6r3S2J5k6h3q4V1i4K6u0W2M7r3S2H3i4K6y4r3N6q4)9K6c8o6p5J5x3U0V1%4i4K6g2p5i4K6u0W2 and follow step by step with this posting [8e5K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3g2S2M7X3I4E0j5i4u0U0N6i4y4Q4x3X3g2T1L8r3!0Y4M7%4m8G2N6q4)9J5k6h3y4G2L8g2)9J5c8U0t1H3x3o6W2Q4x3V1j5H3x3g2)9J5c8Y4g2F1M7r3q4U0K9$3W2F1k6#2)9J5k6r3y4G2L8X3k6A6j5$3E0W2M7X3c8G2N6$3&6S2k6s2g2H3i4K6u0W2K9s2c8E0L8q4)9#2c8q4)9J5k6b7`.`. Unfortunately i cannot reach landed until 0x10002EB0. starting from this address, malware will unpack itself in memory. I tried to set the breakpoint at VirtualAlloc and VirtualProtect, still cannot trace until the offset of these functions. Please share with me if you can do it or something iam wrong. thanks |
|
|
[求助]Conficker Unpacking
Nope, the posting not for unpacking conficker. Anyhow, i also understand chinese font. but my keyboard not support it. Thanks anyway |
操作理由
RANk
{{ user_info.golds == '' ? 0 : user_info.golds }}
雪币
{{ experience }}
课程经验
{{ score }}
学习收益
{{study_duration_fmt}}
学习时长
基本信息
荣誉称号:
{{ honorary_title }}
勋章
兑换勋章

证书
证书查询 >
能力值


