-
-
[学习]跟踪ReadProcessMemory从R3到R0(x64)
-
发表于: 2026-1-23 19:07 959
-
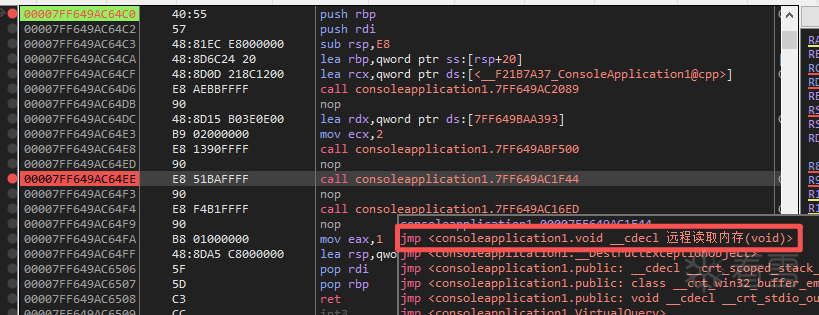
1.编写r3代码, 使用
ReadProcessMemory远程读内存任意读一个进程的内存做测试
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 | void 远程读取内存(){ DWORD pid = 5944; // 目标进程 PID(自行替换) LPCVOID targetAddress = (LPCVOID)0x00400000; // 目标进程中的地址(示例) BYTE buffer[16] = { 0 }; // 读取缓冲区 SIZE_T bytesRead = 0; // 1. 打开目标进程 HANDLE hProcess = OpenProcess( PROCESS_VM_READ | PROCESS_QUERY_INFORMATION, FALSE, pid ); if (!hProcess) { printf("OpenProcess failed, error=%lu\n", GetLastError()); return; } // 2. 读取目标进程内存 BOOL ret = ReadProcessMemory( hProcess, targetAddress, buffer, sizeof(buffer), &bytesRead ); if (!ret) { printf("ReadProcessMemory failed, error=%lu\n", GetLastError()); CloseHandle(hProcess); return; } // 3. 输出读取结果 printf("Read %llu bytes:\n", bytesRead); for (SIZE_T i = 0; i < bytesRead; i++) { printf("%02X ", buffer[i]); } printf("\n"); // 4. 关闭句柄 CloseHandle(hProcess); return;} |
2.用
xdbg打开进程进行跟踪, 找到远程读取内存()函数入口
3.继续找到
远程读取内存()中调用的ReadProcessMemory()函数, 代码中的ReadProcessMemory实际上又调用了kernel32中的ReadProcessMemory, 简称kernel32!ReadProcessMemory()
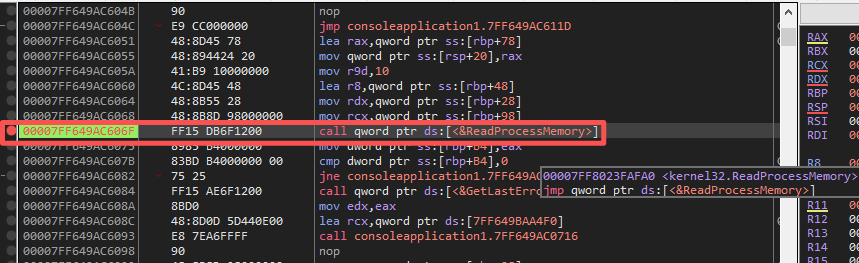
4.跟踪进入
kernel32!ReadProcessMemory()内部发现其又继续调用了ntdll!ZwReadVirtualMemory
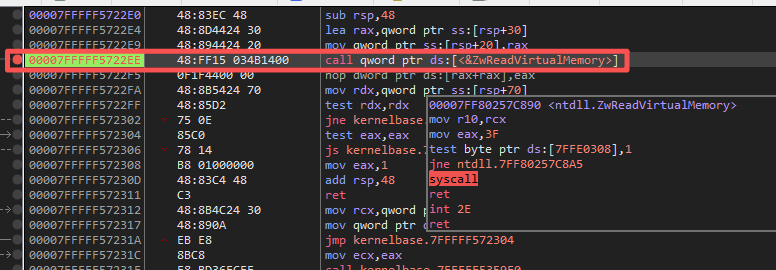
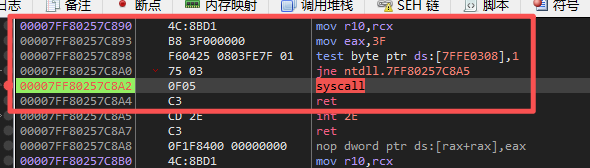
5.进入
ntdll!ZwReadVirtualMemory可以看到使用了syscall快速调用进入了0环, 并且可以看到系统调用号是3F
- 重点说下syscall和sysenter, syscall 和 sysenter 都是快速系统调用指令,但 sysenter 是早期 Intel 的 32 位方案,设计复杂且不对称;syscall 是 AMD 提出的 64 位方案,设计更合理,现代操作系统统一使用 syscall。
- syscall 做了这些事:自动保存:RIP → RCX / RFLAGS → R11, 自动切换:CS / SS / CPL=0, 内核入口地址来自 MSR, 返回用 sysret 自动恢复 RIP / RFLAGS
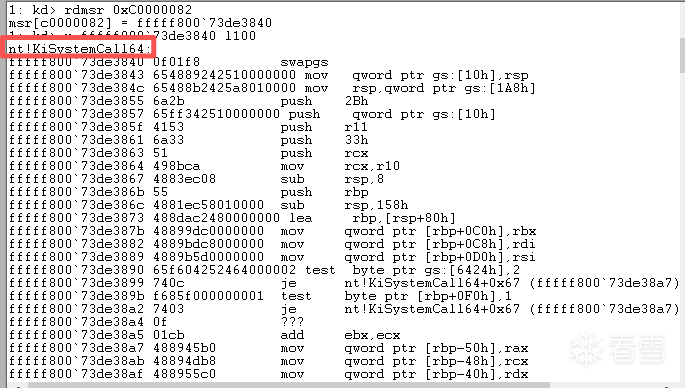
6.查看
IA32_LSTAR:syscall 内核入口, 入口函数是nt!KiSystemCall64, 其中0xC0000082==IA32_LSTAR
1 2 3 4 5 6 | | MSR | 编号 | 作用 | -------------- | -------------- | ------------------------ | IA32_LSTAR | 0xC0000082 | syscall 的 RIP 入口 | IA32_STAR | 0xC0000081 | 用户 / 内核 CS、SS | IA32_FMASK | 0xC0000084 | syscall 时清哪些 RFLAGS | IA32_CSTAR | 0xC0000083 | compat mode(32 位)syscall |
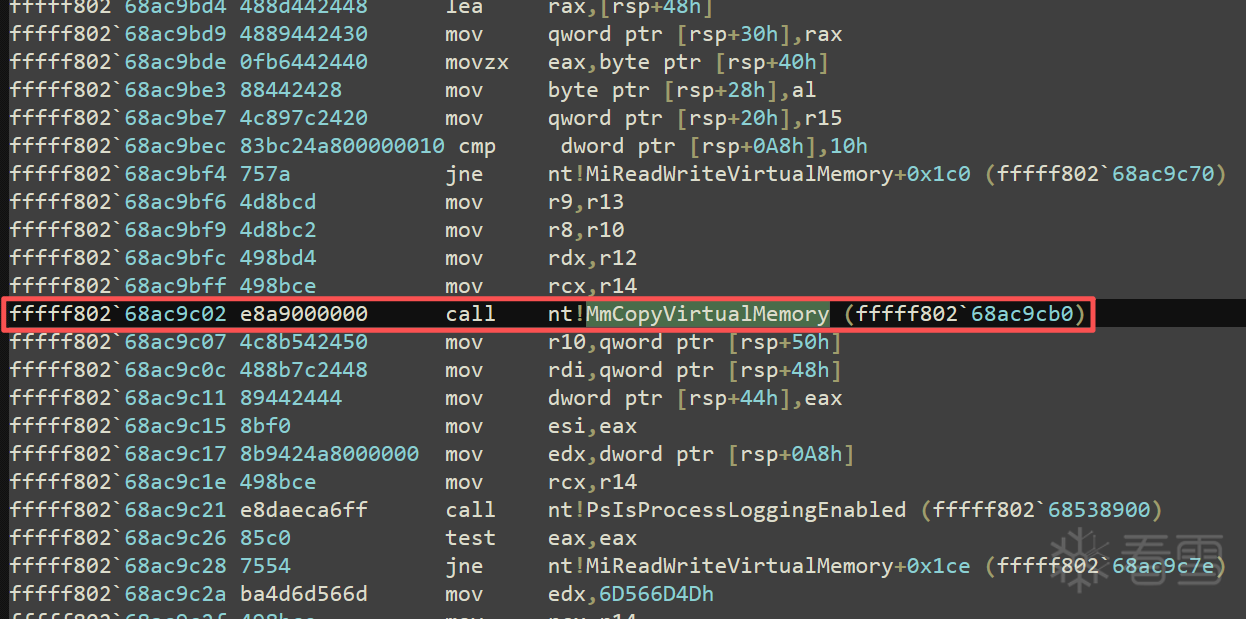
7.分析
nt!KiSystemCall64, 这个函数的头部就是做了些r3转r0的处理: 换栈/保存环境等等
1 2 3 4 5 6 7 8 9 10 | nt!KiSystemCall64:fffff800`73de3840 0f01f8 swapgs //手动切换gs,将r3的TEB切换到r0的KPCRfffff800`73de3843 654889242510000000 mov qword ptr gs:[10h],rsp //保存r3栈fffff800`73de384c 65488b2425a8010000 mov rsp,qword ptr gs:[1A8h] //切换r0栈fffff800`73de3855 6a2b push 2Bh //用户 SSfffff800`73de3857 65ff342510000000 push qword ptr gs:[10h] //用户 RSPfffff800`73de385f 4153 push r11 //RFLAGSfffff800`73de3861 6a33 push 33h //用户 CSfffff800`73de3863 51 push rcx //用户 RIPfffff800`73de3864 498bca mov rcx,r10 //参数修正 |
1 2 3 4 5 6 7 | nt!_KPCR ... +0x010 UserRsp : Uint8B ... +0x180 Prcb : _KPRCB ... +0x028 RspBase : Uint8B |
nt!KiSystemCall64完整代码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 | nt!KiSystemCall64:fffff800`73de3840 0f01f8 swapgsfffff800`73de3843 654889242510000000 mov qword ptr gs:[10h],rspfffff800`73de384c 65488b2425a8010000 mov rsp,qword ptr gs:[1A8h]fffff800`73de3855 6a2b push 2Bhfffff800`73de3857 65ff342510000000 push qword ptr gs:[10h]fffff800`73de385f 4153 push r11fffff800`73de3861 6a33 push 33hfffff800`73de3863 51 push rcxfffff800`73de3864 498bca mov rcx,r10fffff800`73de3867 4883ec08 sub rsp,8fffff800`73de386b 55 push rbpfffff800`73de386c 4881ec58010000 sub rsp,158hfffff800`73de3873 488dac2480000000 lea rbp,[rsp+80h]fffff800`73de387b 48899dc0000000 mov qword ptr [rbp+0C0h],rbxfffff800`73de3882 4889bdc8000000 mov qword ptr [rbp+0C8h],rdifffff800`73de3889 4889b5d0000000 mov qword ptr [rbp+0D0h],rsifffff800`73de3890 65f604252464000002 test byte ptr gs:[6424h],2fffff800`73de3899 740c je nt!KiSystemCall64+0x67 (fffff800`73de38a7)fffff800`73de389b f685f000000001 test byte ptr [rbp+0F0h],1fffff800`73de38a2 7403 je nt!KiSystemCall64+0x67 (fffff800`73de38a7)fffff800`73de38a4 0f ???fffff800`73de38a5 01cb add ebx,ecxfffff800`73de38a7 488945b0 mov qword ptr [rbp-50h],raxfffff800`73de38ab 48894db8 mov qword ptr [rbp-48h],rcxfffff800`73de38af 488955c0 mov qword ptr [rbp-40h],rdxfffff800`73de38b3 65488b0c2588010000 mov rcx,qword ptr gs:[188h]fffff800`73de38bc 488b8920020000 mov rcx,qword ptr [rcx+220h]fffff800`73de38c3 488b8960080000 mov rcx,qword ptr [rcx+860h]fffff800`73de38ca 6548890c2570020000 mov qword ptr gs:[270h],rcxfffff800`73de38d3 658a0c2550080000 mov cl,byte ptr gs:[850h]fffff800`73de38db 65880c2551080000 mov byte ptr gs:[851h],clfffff800`73de38e3 658a0c2578020000 mov cl,byte ptr gs:[278h]fffff800`73de38eb 65880c2552080000 mov byte ptr gs:[852h],clfffff800`73de38f3 650fb604257b020000 movzx eax,byte ptr gs:[27Bh]fffff800`73de38fc 653804257a020000 cmp byte ptr gs:[27Ah],alfffff800`73de3904 7411 je nt!KiSystemCall64+0xd7 (fffff800`73de3917)fffff800`73de3906 658804257a020000 mov byte ptr gs:[27Ah],alfffff800`73de390e b948000000 mov ecx,48hfffff800`73de3913 33d2 xor edx,edxfffff800`73de3915 0f30 wrmsrfffff800`73de3917 650fb6142578020000 movzx edx,byte ptr gs:[278h]fffff800`73de3920 f7c208000000 test edx,8fffff800`73de3926 7413 je nt!KiSystemCall64+0xfb (fffff800`73de393b)fffff800`73de3928 b801000000 mov eax,1fffff800`73de392d 33d2 xor edx,edxfffff800`73de392f b949000000 mov ecx,49hfffff800`73de3934 0f30 wrmsrfffff800`73de3936 e93e010000 jmp nt!KiSystemCall64+0x239 (fffff800`73de3a79)fffff800`73de393b f7c202000000 test edx,2fffff800`73de3941 0f842f010000 je nt!KiSystemCall64+0x236 (fffff800`73de3a76)fffff800`73de3947 65f604257902000004 test byte ptr gs:[279h],4fffff800`73de3950 0f8520010000 jne nt!KiSystemCall64+0x236 (fffff800`73de3a76)fffff800`73de3956 e80e010000 call nt!KiSystemCall64+0x229 (fffff800`73de3a69)fffff800`73de395b 4883c408 add rsp,8fffff800`73de395f e80e010000 call nt!KiSystemCall64+0x232 (fffff800`73de3a72)fffff800`73de3964 4883c408 add rsp,8fffff800`73de3968 e8eeffffff call nt!KiSystemCall64+0x11b (fffff800`73de395b)fffff800`73de396d 4883c408 add rsp,8fffff800`73de3971 e8eeffffff call nt!KiSystemCall64+0x124 (fffff800`73de3964)fffff800`73de3976 4883c408 add rsp,8fffff800`73de397a e8eeffffff call nt!KiSystemCall64+0x12d (fffff800`73de396d)fffff800`73de397f 4883c408 add rsp,8fffff800`73de3983 e8eeffffff call nt!KiSystemCall64+0x136 (fffff800`73de3976)fffff800`73de3988 4883c408 add rsp,8fffff800`73de398c e8eeffffff call nt!KiSystemCall64+0x13f (fffff800`73de397f)fffff800`73de3991 4883c408 add rsp,8fffff800`73de3995 e8eeffffff call nt!KiSystemCall64+0x148 (fffff800`73de3988)fffff800`73de399a 4883c408 add rsp,8fffff800`73de399e e8eeffffff call nt!KiSystemCall64+0x151 (fffff800`73de3991)fffff800`73de39a3 4883c408 add rsp,8fffff800`73de39a7 e8eeffffff call nt!KiSystemCall64+0x15a (fffff800`73de399a)fffff800`73de39ac 4883c408 add rsp,8fffff800`73de39b0 e8eeffffff call nt!KiSystemCall64+0x163 (fffff800`73de39a3)fffff800`73de39b5 4883c408 add rsp,8fffff800`73de39b9 e8eeffffff call nt!KiSystemCall64+0x16c (fffff800`73de39ac)fffff800`73de39be 4883c408 add rsp,8fffff800`73de39c2 e8eeffffff call nt!KiSystemCall64+0x175 (fffff800`73de39b5)fffff800`73de39c7 4883c408 add rsp,8fffff800`73de39cb e8eeffffff call nt!KiSystemCall64+0x17e (fffff800`73de39be)fffff800`73de39d0 4883c408 add rsp,8fffff800`73de39d4 e8eeffffff call nt!KiSystemCall64+0x187 (fffff800`73de39c7)fffff800`73de39d9 4883c408 add rsp,8fffff800`73de39dd e8eeffffff call nt!KiSystemCall64+0x190 (fffff800`73de39d0)fffff800`73de39e2 4883c408 add rsp,8fffff800`73de39e6 e8eeffffff call nt!KiSystemCall64+0x199 (fffff800`73de39d9)fffff800`73de39eb 4883c408 add rsp,8fffff800`73de39ef e8eeffffff call nt!KiSystemCall64+0x1a2 (fffff800`73de39e2)fffff800`73de39f4 4883c408 add rsp,8fffff800`73de39f8 e8eeffffff call nt!KiSystemCall64+0x1ab (fffff800`73de39eb)fffff800`73de39fd 4883c408 add rsp,8fffff800`73de3a01 e8eeffffff call nt!KiSystemCall64+0x1b4 (fffff800`73de39f4)fffff800`73de3a06 4883c408 add rsp,8fffff800`73de3a0a e8eeffffff call nt!KiSystemCall64+0x1bd (fffff800`73de39fd)fffff800`73de3a0f 4883c408 add rsp,8fffff800`73de3a13 e8eeffffff call nt!KiSystemCall64+0x1c6 (fffff800`73de3a06)fffff800`73de3a18 4883c408 add rsp,8fffff800`73de3a1c e8eeffffff call nt!KiSystemCall64+0x1cf (fffff800`73de3a0f)fffff800`73de3a21 4883c408 add rsp,8fffff800`73de3a25 e8eeffffff call nt!KiSystemCall64+0x1d8 (fffff800`73de3a18)fffff800`73de3a2a 4883c408 add rsp,8fffff800`73de3a2e e8eeffffff call nt!KiSystemCall64+0x1e1 (fffff800`73de3a21)fffff800`73de3a33 4883c408 add rsp,8fffff800`73de3a37 e8eeffffff call nt!KiSystemCall64+0x1ea (fffff800`73de3a2a)fffff800`73de3a3c 4883c408 add rsp,8fffff800`73de3a40 e8eeffffff call nt!KiSystemCall64+0x1f3 (fffff800`73de3a33)fffff800`73de3a45 4883c408 add rsp,8fffff800`73de3a49 e8eeffffff call nt!KiSystemCall64+0x1fc (fffff800`73de3a3c)fffff800`73de3a4e 4883c408 add rsp,8fffff800`73de3a52 e8eeffffff call nt!KiSystemCall64+0x205 (fffff800`73de3a45)fffff800`73de3a57 4883c408 add rsp,8fffff800`73de3a5b e8eeffffff call nt!KiSystemCall64+0x20e (fffff800`73de3a4e)fffff800`73de3a60 4883c408 add rsp,8fffff800`73de3a64 e8eeffffff call nt!KiSystemCall64+0x217 (fffff800`73de3a57)fffff800`73de3a69 4883c408 add rsp,8fffff800`73de3a6d e8eeffffff call nt!KiSystemCall64+0x220 (fffff800`73de3a60)fffff800`73de3a72 4883c408 add rsp,8fffff800`73de3a76 0faee8 lfencefffff800`73de3a79 65c604255308000000 mov byte ptr gs:[853h],0 |
8.但是经过对整个函数的观察发现,
nt!KiSystemCall64并没有直接调用KiSystemServiceRepeat也没看到查询SSDT的过程, 但是可以肯定的是微软的原始流程不变,:rax=服务号并且必须要带着服务号访问KeServiceDescriptorTable, 可以得出可疑的位置只有这一大串call链:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 | fffff800`73de3936 e93e010000 jmp nt!KiSystemCall64+0x239 (fffff800`73de3a79)fffff800`73de393b f7c202000000 test edx,2fffff800`73de3941 0f842f010000 je nt!KiSystemCall64+0x236 (fffff800`73de3a76)fffff800`73de3947 65f604257902000004 test byte ptr gs:[279h],4fffff800`73de3950 0f8520010000 jne nt!KiSystemCall64+0x236 (fffff800`73de3a76)fffff800`73de3956 e80e010000 call nt!KiSystemCall64+0x229 (fffff800`73de3a69)fffff800`73de395b 4883c408 add rsp,8fffff800`73de395f e80e010000 call nt!KiSystemCall64+0x232 (fffff800`73de3a72)fffff800`73de3964 4883c408 add rsp,8fffff800`73de3968 e8eeffffff call nt!KiSystemCall64+0x11b (fffff800`73de395b)fffff800`73de396d 4883c408 add rsp,8fffff800`73de3971 e8eeffffff call nt!KiSystemCall64+0x124 (fffff800`73de3964)fffff800`73de3976 4883c408 add rsp,8fffff800`73de397a e8eeffffff call nt!KiSystemCall64+0x12d (fffff800`73de396d)fffff800`73de397f 4883c408 add rsp,8fffff800`73de3983 e8eeffffff call nt!KiSystemCall64+0x136 (fffff800`73de3976)fffff800`73de3988 4883c408 add rsp,8fffff800`73de398c e8eeffffff call nt!KiSystemCall64+0x13f (fffff800`73de397f)fffff800`73de3991 4883c408 add rsp,8fffff800`73de3995 e8eeffffff call nt!KiSystemCall64+0x148 (fffff800`73de3988)fffff800`73de399a 4883c408 add rsp,8fffff800`73de399e e8eeffffff call nt!KiSystemCall64+0x151 (fffff800`73de3991)fffff800`73de39a3 4883c408 add rsp,8fffff800`73de39a7 e8eeffffff call nt!KiSystemCall64+0x15a (fffff800`73de399a)fffff800`73de39ac 4883c408 add rsp,8fffff800`73de39b0 e8eeffffff call nt!KiSystemCall64+0x163 (fffff800`73de39a3)fffff800`73de39b5 4883c408 add rsp,8fffff800`73de39b9 e8eeffffff call nt!KiSystemCall64+0x16c (fffff800`73de39ac)fffff800`73de39be 4883c408 add rsp,8fffff800`73de39c2 e8eeffffff call nt!KiSystemCall64+0x175 (fffff800`73de39b5)fffff800`73de39c7 4883c408 add rsp,8fffff800`73de39cb e8eeffffff call nt!KiSystemCall64+0x17e (fffff800`73de39be)fffff800`73de39d0 4883c408 add rsp,8fffff800`73de39d4 e8eeffffff call nt!KiSystemCall64+0x187 (fffff800`73de39c7)fffff800`73de39d9 4883c408 add rsp,8fffff800`73de39dd e8eeffffff call nt!KiSystemCall64+0x190 (fffff800`73de39d0)fffff800`73de39e2 4883c408 add rsp,8fffff800`73de39e6 e8eeffffff call nt!KiSystemCall64+0x199 (fffff800`73de39d9)fffff800`73de39eb 4883c408 add rsp,8fffff800`73de39ef e8eeffffff call nt!KiSystemCall64+0x1a2 (fffff800`73de39e2)fffff800`73de39f4 4883c408 add rsp,8fffff800`73de39f8 e8eeffffff call nt!KiSystemCall64+0x1ab (fffff800`73de39eb)fffff800`73de39fd 4883c408 add rsp,8fffff800`73de3a01 e8eeffffff call nt!KiSystemCall64+0x1b4 (fffff800`73de39f4)fffff800`73de3a06 4883c408 add rsp,8fffff800`73de3a0a e8eeffffff call nt!KiSystemCall64+0x1bd (fffff800`73de39fd)fffff800`73de3a0f 4883c408 add rsp,8fffff800`73de3a13 e8eeffffff call nt!KiSystemCall64+0x1c6 (fffff800`73de3a06)fffff800`73de3a18 4883c408 add rsp,8fffff800`73de3a1c e8eeffffff call nt!KiSystemCall64+0x1cf (fffff800`73de3a0f)fffff800`73de3a21 4883c408 add rsp,8fffff800`73de3a25 e8eeffffff call nt!KiSystemCall64+0x1d8 (fffff800`73de3a18)fffff800`73de3a2a 4883c408 add rsp,8fffff800`73de3a2e e8eeffffff call nt!KiSystemCall64+0x1e1 (fffff800`73de3a21)fffff800`73de3a33 4883c408 add rsp,8fffff800`73de3a37 e8eeffffff call nt!KiSystemCall64+0x1ea (fffff800`73de3a2a)fffff800`73de3a3c 4883c408 add rsp,8fffff800`73de3a40 e8eeffffff call nt!KiSystemCall64+0x1f3 (fffff800`73de3a33)fffff800`73de3a45 4883c408 add rsp,8fffff800`73de3a49 e8eeffffff call nt!KiSystemCall64+0x1fc (fffff800`73de3a3c)fffff800`73de3a4e 4883c408 add rsp,8fffff800`73de3a52 e8eeffffff call nt!KiSystemCall64+0x205 (fffff800`73de3a45)fffff800`73de3a57 4883c408 add rsp,8fffff800`73de3a5b e8eeffffff call nt!KiSystemCall64+0x20e (fffff800`73de3a4e)fffff800`73de3a60 4883c408 add rsp,8fffff800`73de3a64 e8eeffffff call nt!KiSystemCall64+0x217 (fffff800`73de3a57)fffff800`73de3a69 4883c408 add rsp,8fffff800`73de3a6d e8eeffffff call nt!KiSystemCall64+0x220 (fffff800`73de3a60)fffff800`73de3a72 4883c408 add rsp,8 |
9.通过上面那串call链最终会跳转到
nt!KiSystemServiceRepeat, 而在nt!KiSystemServiceRepeat就发现了其访问SSDT以及解码过程, 最后的r10就是最终调用函数的地址
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 | nt!KiSystemServiceStart:fffff803`16beeb80 4889a390000000 mov qword ptr [rbx+90h],rspfffff803`16beeb87 8bf8 mov edi,eaxfffff803`16beeb89 c1ef07 shr edi,7fffff803`16beeb8c 83e720 and edi,20hfffff803`16beeb8f 25ff0f0000 and eax,0FFFhnt!KiSystemServiceRepeat:fffff807`2a3d2b94 4c8d15e59c3b00 lea r10,[nt!KeServiceDescriptorTable (fffff807`2a78c880)] //r10 = 普通 SSDTfffff807`2a3d2b9b 4c8d1dde1e3a00 lea r11,[nt!KeServiceDescriptorTableShadow (fffff807`2a774a80)] //r11 = Shadow SSDT(Win32k)//选择用哪个 SSDT(关键判断): fffff807`2a3d2ba2 f7437880000000 test dword ptr [rbx+78h],80h //rbx = _KTHREAD [rbx+78h] = ThreadFlagsfffff807`2a3d2ba9 7413 je nt!KiSystemServiceRepeat+0x2a (fffff807`2a3d2bbe)fffff807`2a3d2bab f7437800002000 test dword ptr [rbx+78h],200000h //rbx = _KTHREAD [rbx+78h] = ThreadFlagsfffff807`2a3d2bb2 7407 je nt!KiSystemServiceRepeat+0x27 (fffff807`2a3d2bbb)fffff807`2a3d2bb4 4c8d1d051f3a00 lea r11,[nt!KeServiceDescriptorTableFilter (fffff807`2a774ac0)]fffff807`2a3d2bbb 4d8bd3 mov r10,r11 //若是:GUI / Win32 / Filter 情况 最终使用的 SSDT 都会被放进 r10//系统调用号范围校验(防越界)fffff807`2a3d2bbe 413b443a10 cmp eax,dword ptr [r10+rdi+10h] //eax = syscall number, rdi = table index, [r10+rdi+10h] = ServiceLimitfffff807`2a3d2bc3 0f832c050000 jae nt!KiSystemServiceExitPico+0x160 (fffff807`2a3d30f5)//SSDT 表指针解码fffff807`2a3d2bc9 4d8b143a mov r10,qword ptr [r10+rdi] //r10 = ServiceTableBase SSDT->ServiceTable;//读取 SSDT Entryfffff807`2a3d2bcd 4d631c82 movsxd r11,dword ptr [r10+rax*4]//解码 SSDT Entryfffff807`2a3d2bd1 498bc3 mov rax,r11 //保存原始 entryfffff807`2a3d2bd4 49c1fb04 sar r11,4 //去掉低4位flag 得到函数相对偏移fffff807`2a3d2bd8 4d03d3 add r10,r11 //r10 = ServiceTableBase + Offset //最终 NtXxx 函数地址fffff807`2a3d2bdb 83ff20 cmp edi,20hfffff807`2a3d2bde 7550 jne nt!KiSystemServiceGdiTebAccess+0x49 (fffff807`2a3d2c30)fffff807`2a3d2be0 4c8b9bf0000000 mov r11,qword ptr [rbx+0F0h] |
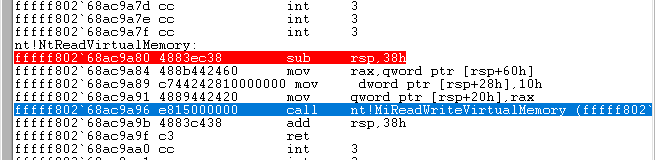
10.但如果尝试在
nt!KiSystemCall64下断点机器会直接卡住或者蓝屏, 因为int 3发生在中断被关闭的状态, 并且这是全系统最高频路径, 一打断点所有CPU核心所有线程会同时命中调试器根本来不及处理系统会立即失控, 但是ReadProcessMemory这个函数在进入r0后最终会调用nt!NtReadVirtualMemory, 所以直接在nt!NtReadVirtualMemory下断, 并且防止频繁命中还要加上pid过滤, 尝试条件下断后可以正常断下跟踪继续跟踪到
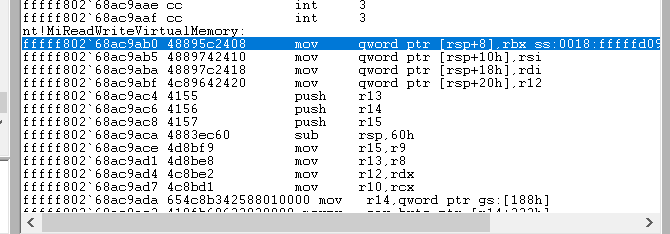
MiReadWriteVirtualMemory
11.在
MiReadWriteVirtualMemory中本身不做memcpy, 它只是校验调度调用真正的内存管理器接口, 核心copy操作在MmCopyVirtualMemory
1 2 3 4 5 6 7 | ZwReadVirtualMemory └─ MiReadWriteVirtualMemory ├─ 参数合法性检查 ├─ 地址范围检查 ├─ 探测用户缓冲区是否可访问 ├─ ObReferenceObjectByHandle (拿 EPROCESS) └─ MmCopyVirtualMemory ← 真正拷贝发生在这里 |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 | nt!MiReadWriteVirtualMemory:fffff802`68ac9ab0 48895c2408 mov qword ptr [rsp+8],rbxfffff802`68ac9ab5 4889742410 mov qword ptr [rsp+10h],rsifffff802`68ac9aba 48897c2418 mov qword ptr [rsp+18h],rdifffff802`68ac9abf 4c89642420 mov qword ptr [rsp+20h],r12fffff802`68ac9ac4 4155 push r13fffff802`68ac9ac6 4156 push r14fffff802`68ac9ac8 4157 push r15fffff802`68ac9aca 4883ec60 sub rsp,60hfffff802`68ac9ace 4d8bf9 mov r15,r9fffff802`68ac9ad1 4d8be8 mov r13,r8fffff802`68ac9ad4 4c8be2 mov r12,rdxfffff802`68ac9ad7 4c8bd1 mov r10,rcxfffff802`68ac9ada 654c8b342588010000 mov r14,qword ptr gs:[188h]fffff802`68ac9ae3 410fb68632020000 movzx eax,byte ptr [r14+232h]fffff802`68ac9aeb 88442440 mov byte ptr [rsp+40h],alfffff802`68ac9aef 84c0 test al,alfffff802`68ac9af1 0f84a3010000 je nt!MiReadWriteVirtualMemory+0x1ea (fffff802`68ac9c9a)fffff802`68ac9af7 4a8d040a lea rax,[rdx+r9]fffff802`68ac9afb 483bc2 cmp rax,rdxfffff802`68ac9afe 0f82be801900 jb nt!MiReadWriteVirtualMemory+0x198112 (fffff802`68c61bc2)fffff802`68ac9b04 48ba0000ffffff7f0000 mov rdx,7FFFFFFF0000hfffff802`68ac9b0e 483bc2 cmp rax,rdxfffff802`68ac9b11 0f87ab801900 ja nt!MiReadWriteVirtualMemory+0x198112 (fffff802`68c61bc2)fffff802`68ac9b17 4b8d0401 lea rax,[r9+r8]fffff802`68ac9b1b 493bc0 cmp rax,r8fffff802`68ac9b1e 0f829e801900 jb nt!MiReadWriteVirtualMemory+0x198112 (fffff802`68c61bc2)fffff802`68ac9b24 483bc2 cmp rax,rdxfffff802`68ac9b27 0f8795801900 ja nt!MiReadWriteVirtualMemory+0x198112 (fffff802`68c61bc2)fffff802`68ac9b2d 488b9c24a0000000 mov rbx,qword ptr [rsp+0A0h]fffff802`68ac9b35 4885db test rbx,rbxfffff802`68ac9b38 0f8428010000 je nt!MiReadWriteVirtualMemory+0x1b6 (fffff802`68ac9c66)fffff802`68ac9b3e 488bcb mov rcx,rbxfffff802`68ac9b41 483bda cmp rbx,rdxfffff802`68ac9b44 7203 jb nt!MiReadWriteVirtualMemory+0x99 (fffff802`68ac9b49)fffff802`68ac9b46 488bca mov rcx,rdxfffff802`68ac9b49 488b01 mov rax,qword ptr [rcx]fffff802`68ac9b4c 488901 mov qword ptr [rcx],raxfffff802`68ac9b4f 0fb6442440 movzx eax,byte ptr [rsp+40h]fffff802`68ac9b54 eb05 jmp nt!MiReadWriteVirtualMemory+0xab (fffff802`68ac9b5b)fffff802`68ac9b56 e9ec000000 jmp nt!MiReadWriteVirtualMemory+0x197 (fffff802`68ac9c47)fffff802`68ac9b5b 33ff xor edi,edifffff802`68ac9b5d 48897c2448 mov qword ptr [rsp+48h],rdifffff802`68ac9b62 8bf7 mov esi,edifffff802`68ac9b64 897c2444 mov dword ptr [rsp+44h],edifffff802`68ac9b68 4d85ff test r15,r15fffff802`68ac9b6b 0f84c6000000 je nt!MiReadWriteVirtualMemory+0x187 (fffff802`68ac9c37)fffff802`68ac9b71 4c8b051818f5ff mov r8,qword ptr [nt!PsProcessType (fffff802`68a1b390)]fffff802`68ac9b78 48897c2438 mov qword ptr [rsp+38h],rdifffff802`68ac9b7d 48897c2430 mov qword ptr [rsp+30h],rdifffff802`68ac9b82 488d4c2458 lea rcx,[rsp+58h]fffff802`68ac9b87 48894c2428 mov qword ptr [rsp+28h],rcxfffff802`68ac9b8c c74424204d6d566d mov dword ptr [rsp+20h],6D566D4Dhfffff802`68ac9b94 440fb6c8 movzx r9d,alfffff802`68ac9b98 8b9424a8000000 mov edx,dword ptr [rsp+0A8h]fffff802`68ac9b9f 498bca mov rcx,r10fffff802`68ac9ba2 e849e4fcff call nt!ObpReferenceObjectByHandleWithTag (fffff802`68a97ff0)fffff802`68ac9ba7 8bf0 mov esi,eaxfffff802`68ac9ba9 89442444 mov dword ptr [rsp+44h],eaxfffff802`68ac9bad 85c0 test eax,eaxfffff802`68ac9baf 0f8882000000 js nt!MiReadWriteVirtualMemory+0x187 (fffff802`68ac9c37)fffff802`68ac9bb5 4d8b96b8000000 mov r10,qword ptr [r14+0B8h]fffff802`68ac9bbc 4c89542450 mov qword ptr [rsp+50h],r10fffff802`68ac9bc1 4c8b742458 mov r14,qword ptr [rsp+58h]fffff802`68ac9bc6 41f686d802000001 test byte ptr [r14+2D8h],1fffff802`68ac9bce 0f85f87f1900 jne nt!MiReadWriteVirtualMemory+0x19811c (fffff802`68c61bcc)fffff802`68ac9bd4 488d442448 lea rax,[rsp+48h]fffff802`68ac9bd9 4889442430 mov qword ptr [rsp+30h],raxfffff802`68ac9bde 0fb6442440 movzx eax,byte ptr [rsp+40h]fffff802`68ac9be3 88442428 mov byte ptr [rsp+28h],alfffff802`68ac9be7 4c897c2420 mov qword ptr [rsp+20h],r15fffff802`68ac9bec 83bc24a800000010 cmp dword ptr [rsp+0A8h],10hfffff802`68ac9bf4 757a jne nt!MiReadWriteVirtualMemory+0x1c0 (fffff802`68ac9c70)fffff802`68ac9bf6 4d8bcd mov r9,r13fffff802`68ac9bf9 4d8bc2 mov r8,r10fffff802`68ac9bfc 498bd4 mov rdx,r12fffff802`68ac9bff 498bce mov rcx,r14fffff802`68ac9c02 e8a9000000 call nt!MmCopyVirtualMemory (fffff802`68ac9cb0)fffff802`68ac9c07 4c8b542450 mov r10,qword ptr [rsp+50h]fffff802`68ac9c0c 488b7c2448 mov rdi,qword ptr [rsp+48h]fffff802`68ac9c11 89442444 mov dword ptr [rsp+44h],eaxfffff802`68ac9c15 8bf0 mov esi,eaxfffff802`68ac9c17 8b9424a8000000 mov edx,dword ptr [rsp+0A8h]fffff802`68ac9c1e 498bce mov rcx,r14fffff802`68ac9c21 e8daeca6ff call nt!PsIsProcessLoggingEnabled (fffff802`68538900)fffff802`68ac9c26 85c0 test eax,eaxfffff802`68ac9c28 7554 jne nt!MiReadWriteVirtualMemory+0x1ce (fffff802`68ac9c7e)fffff802`68ac9c2a ba4d6d566d mov edx,6D566D4Dhfffff802`68ac9c2f 498bce mov rcx,r14fffff802`68ac9c32 e8a97ca1ff call nt!ObfDereferenceObjectWithTag (fffff802`684e18e0)fffff802`68ac9c37 4885db test rbx,rbxfffff802`68ac9c3a 7409 je nt!MiReadWriteVirtualMemory+0x195 (fffff802`68ac9c45)fffff802`68ac9c3c 48893b mov qword ptr [rbx],rdifffff802`68ac9c3f eb04 jmp nt!MiReadWriteVirtualMemory+0x195 (fffff802`68ac9c45)fffff802`68ac9c41 8b742444 mov esi,dword ptr [rsp+44h]fffff802`68ac9c45 8bc6 mov eax,esifffff802`68ac9c47 4c8d5c2460 lea r11,[rsp+60h]fffff802`68ac9c4c 498b5b20 mov rbx,qword ptr [r11+20h]fffff802`68ac9c50 498b7328 mov rsi,qword ptr [r11+28h]fffff802`68ac9c54 498b7b30 mov rdi,qword ptr [r11+30h]fffff802`68ac9c58 4d8b6338 mov r12,qword ptr [r11+38h]fffff802`68ac9c5c 498be3 mov rsp,r11fffff802`68ac9c5f 415f pop r15fffff802`68ac9c61 415e pop r14fffff802`68ac9c63 415d pop r13fffff802`68ac9c65 c3 retfffff802`68ac9c66 0fb6442440 movzx eax,byte ptr [rsp+40h]fffff802`68ac9c6b e9ebfeffff jmp nt!MiReadWriteVirtualMemory+0xab (fffff802`68ac9b5b)fffff802`68ac9c70 4d8bcc mov r9,r12fffff802`68ac9c73 4d8bc6 mov r8,r14fffff802`68ac9c76 498bd5 mov rdx,r13fffff802`68ac9c79 498bca mov rcx,r10fffff802`68ac9c7c eb84 jmp nt!MiReadWriteVirtualMemory+0x152 (fffff802`68ac9c02)fffff802`68ac9c7e 48897c2428 mov qword ptr [rsp+28h],rdifffff802`68ac9c83 4c89642420 mov qword ptr [rsp+20h],r12fffff802`68ac9c88 448bca mov r9d,edxfffff802`68ac9c8b 4d8bc6 mov r8,r14fffff802`68ac9c8e 498bd2 mov rdx,r10fffff802`68ac9c91 8bce mov ecx,esifffff802`68ac9c93 e8e8f70200 call nt!EtwTiLogReadWriteVm (fffff802`68af9480)fffff802`68ac9c98 eb90 jmp nt!MiReadWriteVirtualMemory+0x17a (fffff802`68ac9c2a)fffff802`68ac9c9a 488b9c24a0000000 mov rbx,qword ptr [rsp+0A0h]fffff802`68ac9ca2 e9b4feffff jmp nt!MiReadWriteVirtualMemory+0xab (fffff802`68ac9b5b)fffff802`68ac9ca7 cc int 3fffff802`68ac9ca8 cc int 3fffff802`68ac9ca9 cc int 3fffff802`68ac9caa cc int 3fffff802`68ac9cab cc int 3fffff802`68ac9cac cc int 3fffff802`68ac9cad cc int 3fffff802`68ac9cae cc int 3fffff802`68ac9caf cc int 3 |
12.进入
MmCopyVirtualMemory, 这不是一个简单memcpy, 而是一个多路径内存拷贝调度器, 核心流程是:
1 2 3 4 5 6 7 8 9 10 11 | 参数检查→ 判断是否同进程→ 判断大小(< 0x200 ?)→ 判断安全 / enclave / VBS→ 选择拷贝路径: ├─ 直接 memcpy(同进程 / 已 attach) ├─ KiStackAttachProcess + memcpy ├─ Probe + Lock + Map ├─ VslDebug / Enclave 路径→ 解除 attach→ 回填 NumberOfBytesCopied |
路径1:是否需要 Attach 源进程
1 2 3 4 | mov rsi, gs:[188h] ; 当前线程 _KTHREADmov rdi, [rsi+0B8h] ; 当前进程 EPROCESScmp rdi, r14 ; 当前进程 == FromProcess ?je no_attach |
如果是最理想状态直接会进入memcpy()这就是最终复制函数
1 2 3 | mov rdx, r10 ; 源地址(已在目标进程上下文)mov rcx, [rsp+48h] ; 目标缓冲call memcpy |
触发条件:
- 已 attach 到正确进程
- 非 enclave
- 权限 OK
- Size 较小
路径 2:Probe + Lock + Map
1 2 3 4 5 | call MmProbeAndLockPages...call memcpy...call MmUnlockPages |
触发条件:
- 用户态地址
- 跨进程
- 大块拷贝
- 需要防止页被换出
这是 “安全但慢” 的路径
路径 3:VBS / Enclave
1 2 | call MiDbgReadWriteEnclavecall VslDebugReadWriteSecureProcess |
说明:
- 目标进程是 Secure / Enclave / VBS
- 普通 memcpy 不允许
- 必须走 hypervisor / secure copy
nt!MmCopyVirtualMemory:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 332 333 334 335 336 337 338 339 340 341 342 343 344 345 346 347 348 349 350 351 352 353 354 355 356 357 358 359 360 361 362 363 364 365 366 367 368 369 370 371 372 373 374 375 376 377 378 379 380 381 382 383 384 385 386 387 388 389 390 391 392 393 394 395 396 397 398 399 400 401 402 403 404 405 406 407 408 409 410 411 412 413 414 415 416 417 418 419 420 421 422 423 424 425 426 427 428 429 430 431 432 433 434 435 436 437 438 439 440 441 442 443 444 445 446 447 448 449 450 451 452 453 454 455 456 457 458 459 460 461 462 463 464 465 466 467 468 469 470 471 472 473 474 475 476 477 478 479 480 481 482 483 484 485 486 487 488 489 490 491 492 493 494 495 496 497 498 499 500 501 502 503 504 505 506 507 508 509 510 511 512 513 514 515 516 517 518 519 520 521 | nt!MmCopyVirtualMemory:fffff802`68ac9cb0 4053 push rbxfffff802`68ac9cb2 56 push rsifffff802`68ac9cb3 57 push rdifffff802`68ac9cb4 4154 push r12fffff802`68ac9cb6 4155 push r13fffff802`68ac9cb8 4156 push r14fffff802`68ac9cba 4157 push r15fffff802`68ac9cbc 4881ec60040000 sub rsp,460hfffff802`68ac9cc3 488b05b6a6e0ff mov rax,qword ptr [nt!_security_cookie (fffff802`688d4380)]fffff802`68ac9cca 4833c4 xor rax,rspfffff802`68ac9ccd 4889842450040000 mov qword ptr [rsp+450h],raxfffff802`68ac9cd5 498bd9 mov rbx,r9fffff802`68ac9cd8 48899c2488000000 mov qword ptr [rsp+88h],rbxfffff802`68ac9ce0 4d8bf8 mov r15,r8fffff802`68ac9ce3 4c89442468 mov qword ptr [rsp+68h],r8fffff802`68ac9ce8 488bf2 mov rsi,rdxfffff802`68ac9ceb 4889542460 mov qword ptr [rsp+60h],rdxfffff802`68ac9cf0 4c8bf1 mov r14,rcxfffff802`68ac9cf3 48894c2458 mov qword ptr [rsp+58h],rcxfffff802`68ac9cf8 48898c24e0000000 mov qword ptr [rsp+0E0h],rcxfffff802`68ac9d00 48899424d0000000 mov qword ptr [rsp+0D0h],rdxfffff802`68ac9d08 4c898424d8000000 mov qword ptr [rsp+0D8h],r8fffff802`68ac9d10 48899c24c0000000 mov qword ptr [rsp+0C0h],rbxfffff802`68ac9d18 488bbc24c0040000 mov rdi,qword ptr [rsp+4C0h]fffff802`68ac9d20 48897c2450 mov qword ptr [rsp+50h],rdifffff802`68ac9d25 488b8424d0040000 mov rax,qword ptr [rsp+4D0h]fffff802`68ac9d2d 4889842490000000 mov qword ptr [rsp+90h],raxfffff802`68ac9d35 33d2 xor edx,edxfffff802`68ac9d37 448d4230 lea r8d,[rdx+30h]fffff802`68ac9d3b 488d8c2470010000 lea rcx,[rsp+170h]fffff802`68ac9d43 e83818bbff call nt!memset (fffff802`6867b580)fffff802`68ac9d48 33d2 xor edx,edxfffff802`68ac9d4a 41b8a8000000 mov r8d,0A8hfffff802`68ac9d50 488d8c24a0010000 lea rcx,[rsp+1A0h]fffff802`68ac9d58 e82318bbff call nt!memset (fffff802`6867b580)fffff802`68ac9d5d 4885ff test rdi,rdifffff802`68ac9d60 0f84dc060000 je nt!MmCopyVirtualMemory+0x792 (fffff802`68aca442)fffff802`68ac9d66 4533ed xor r13d,r13dfffff802`68ac9d69 488b842490000000 mov rax,qword ptr [rsp+90h]fffff802`68ac9d71 4c8928 mov qword ptr [rax],r13fffff802`68ac9d74 44896c2430 mov dword ptr [rsp+30h],r13dfffff802`68ac9d79 4c89ac24b0000000 mov qword ptr [rsp+0B0h],r13fffff802`68ac9d81 4d39ae98030000 cmp qword ptr [r14+398h],r13fffff802`68ac9d88 7508 jne nt!MmCopyVirtualMemory+0xe2 (fffff802`68ac9d92)fffff802`68ac9d8a c744243001000000 mov dword ptr [rsp+30h],1fffff802`68ac9d92 4889b424a0000000 mov qword ptr [rsp+0A0h],rsifffff802`68ac9d9a 48899c24a8000000 mov qword ptr [rsp+0A8h],rbxfffff802`68ac9da2 488bd7 mov rdx,rdifffff802`68ac9da5 4889542440 mov qword ptr [rsp+40h],rdxfffff802`68ac9daa 488d8424a0010000 lea rax,[rsp+1A0h]fffff802`68ac9db2 4889842400010000 mov qword ptr [rsp+100h],raxfffff802`68ac9dba 65488b042588010000 mov rax,qword ptr gs:[188h]fffff802`68ac9dc3 48898424f0000000 mov qword ptr [rsp+0F0h],raxfffff802`68ac9dcb 44896c2438 mov dword ptr [rsp+38h],r13dfffff802`68ac9dd0 4c896c2448 mov qword ptr [rsp+48h],r13fffff802`68ac9dd5 4c89ac24e8000000 mov qword ptr [rsp+0E8h],r13fffff802`68ac9ddd 44896c2478 mov dword ptr [rsp+78h],r13dfffff802`68ac9de2 8b5c2430 mov ebx,dword ptr [rsp+30h]fffff802`68ac9de6 8d041b lea eax,[rbx+rbx]fffff802`68ac9de9 33c3 xor eax,ebxfffff802`68ac9deb 83e002 and eax,2fffff802`68ac9dee 33c3 xor eax,ebxfffff802`68ac9df0 89442430 mov dword ptr [rsp+30h],eaxfffff802`68ac9df4 410fb68ed8020000 movzx ecx,byte ptr [r14+2D8h]fffff802`68ac9dfc f6c101 test cl,1fffff802`68ac9dff 0f85f57d1900 jne nt!MmCopyVirtualMemory+0x197f4a (fffff802`68c61bfa)fffff802`68ac9e05 32c9 xor cl,clfffff802`68ac9e07 84c9 test cl,clfffff802`68ac9e09 0f85f27d1900 jne nt!MmCopyVirtualMemory+0x197f51 (fffff802`68c61c01)fffff802`68ac9e0f 41f687d802000001 test byte ptr [r15+2D8h],1fffff802`68ac9e17 0f85f07d1900 jne nt!MmCopyVirtualMemory+0x197f5d (fffff802`68c61c0d)fffff802`68ac9e1d 488bdf mov rbx,rdifffff802`68ac9e20 482bda sub rbx,rdxfffff802`68ac9e23 4c8d2433 lea r12,[rbx+rsi]fffff802`68ac9e27 33d2 xor edx,edxfffff802`68ac9e29 448d4230 lea r8d,[rdx+30h]fffff802`68ac9e2d 488d8c2410010000 lea rcx,[rsp+110h]fffff802`68ac9e35 e84617bbff call nt!memset (fffff802`6867b580)fffff802`68ac9e3a 65488b342588010000 mov rsi,qword ptr gs:[188h]fffff802`68ac9e43 488bbeb8000000 mov rdi,qword ptr [rsi+0B8h]fffff802`68ac9e4a 493bfe cmp rdi,r14fffff802`68ac9e4d 7412 je nt!MmCopyVirtualMemory+0x1b1 (fffff802`68ac9e61)fffff802`68ac9e4f 4c8d842410010000 lea r8,[rsp+110h]fffff802`68ac9e57 33d2 xor edx,edxfffff802`68ac9e59 498bce mov rcx,r14fffff802`68ac9e5c e88ff1a6ff call nt!KiStackAttachProcess (fffff802`68538ff0)fffff802`68ac9e61 4d8bf5 mov r14,r13fffff802`68ac9e64 458bfd mov r15d,r13dfffff802`68ac9e67 488b4c2458 mov rcx,qword ptr [rsp+58h]fffff802`68ac9e6c 488b8110050000 mov rax,qword ptr [rcx+510h]fffff802`68ac9e73 83b82801000000 cmp dword ptr [rax+128h],0fffff802`68ac9e7a 0f859a7d1900 jne nt!MmCopyVirtualMemory+0x197f6a (fffff802`68c61c1a)fffff802`68ac9e80 4c8b542440 mov r10,qword ptr [rsp+40h]fffff802`68ac9e85 4c89942498000000 mov qword ptr [rsp+98h],r10fffff802`68ac9e8d 483bf9 cmp rdi,rcxfffff802`68ac9e90 740f je nt!MmCopyVirtualMemory+0x1f1 (fffff802`68ac9ea1)fffff802`68ac9e92 33d2 xor edx,edxfffff802`68ac9e94 488d8c2410010000 lea rcx,[rsp+110h]fffff802`68ac9e9c e8efeca6ff call nt!KiUnstackDetachProcess (fffff802`68538b90)fffff802`68ac9ea1 428d0cbd00000000 lea ecx,[r15*4]fffff802`68ac9ea9 8b442430 mov eax,dword ptr [rsp+30h]fffff802`68ac9ead 83e0f3 and eax,0FFFFFFF3hfffff802`68ac9eb0 0bc8 or ecx,eaxfffff802`68ac9eb2 894c2430 mov dword ptr [rsp+30h],ecxfffff802`68ac9eb6 4c8ba42488000000 mov r12,qword ptr [rsp+88h]fffff802`68ac9ebe 4c03e3 add r12,rbxfffff802`68ac9ec1 33d2 xor edx,edxfffff802`68ac9ec3 448d4230 lea r8d,[rdx+30h]fffff802`68ac9ec7 488d8c2440010000 lea rcx,[rsp+140h]fffff802`68ac9ecf e8ac16bbff call nt!memset (fffff802`6867b580)fffff802`68ac9ed4 654c8b3c2588010000 mov r15,qword ptr gs:[188h]fffff802`68ac9edd 498bb7b8000000 mov rsi,qword ptr [r15+0B8h]fffff802`68ac9ee4 488b7c2468 mov rdi,qword ptr [rsp+68h]fffff802`68ac9ee9 483bf7 cmp rsi,rdifffff802`68ac9eec 0f8575050000 jne nt!MmCopyVirtualMemory+0x7b7 (fffff802`68aca467)fffff802`68ac9ef2 4d8bf5 mov r14,r13fffff802`68ac9ef5 418bdd mov ebx,r13dfffff802`68ac9ef8 488b8710050000 mov rax,qword ptr [rdi+510h]fffff802`68ac9eff 83b82801000000 cmp dword ptr [rax+128h],0fffff802`68ac9f06 0f85127f1900 jne nt!MmCopyVirtualMemory+0x19816e (fffff802`68c61e1e)fffff802`68ac9f0c 488b542440 mov rdx,qword ptr [rsp+40h]fffff802`68ac9f11 488bfa mov rdi,rdxfffff802`68ac9f14 48899424b8000000 mov qword ptr [rsp+0B8h],rdxfffff802`68ac9f1c 4c8b742468 mov r14,qword ptr [rsp+68h]fffff802`68ac9f21 493bf6 cmp rsi,r14fffff802`68ac9f24 0f8554050000 jne nt!MmCopyVirtualMemory+0x7ce (fffff802`68aca47e)fffff802`68ac9f2a c1e304 shl ebx,4fffff802`68ac9f2d 8b442430 mov eax,dword ptr [rsp+30h]fffff802`68ac9f31 83e0cf and eax,0FFFFFFCFhfffff802`68ac9f34 0bd8 or ebx,eaxfffff802`68ac9f36 895c2430 mov dword ptr [rsp+30h],ebxfffff802`68ac9f3a f6c30c test bl,0Chfffff802`68ac9f3d 0f85db801900 jne nt!MmCopyVirtualMemory+0x19836e (fffff802`68c6201e)fffff802`68ac9f43 f6c340 test bl,40hfffff802`68ac9f46 0f85d2801900 jne nt!MmCopyVirtualMemory+0x19836e (fffff802`68c6201e)fffff802`68ac9f4c 84db test bl,blfffff802`68ac9f4e 0f88ca801900 js nt!MmCopyVirtualMemory+0x19836e (fffff802`68c6201e)fffff802`68ac9f54 4c8bf2 mov r14,rdxfffff802`68ac9f57 4889542470 mov qword ptr [rsp+70h],rdxfffff802`68ac9f5c 488b842498000000 mov rax,qword ptr [rsp+98h]fffff802`68ac9f64 483bc2 cmp rax,rdxfffff802`68ac9f67 0f82bd801900 jb nt!MmCopyVirtualMemory+0x19837a (fffff802`68c6202a)fffff802`68ac9f6d 493bfe cmp rdi,r14fffff802`68ac9f70 0f82c1801900 jb nt!MmCopyVirtualMemory+0x198387 (fffff802`68c62037)fffff802`68ac9f76 448b7c2438 mov r15d,dword ptr [rsp+38h]fffff802`68ac9f7b 488b742460 mov rsi,qword ptr [rsp+60h]fffff802`68ac9f80 488b4c2450 mov rcx,qword ptr [rsp+50h]fffff802`68ac9f85 4981fe00020000 cmp r14,200hfffff802`68ac9f8c 0f8305050000 jae nt!MmCopyVirtualMemory+0x7e7 (fffff802`68aca497)fffff802`68ac9f92 83e3fd and ebx,0FFFFFFFDhfffff802`68ac9f95 895c2430 mov dword ptr [rsp+30h],ebxfffff802`68ac9f99 488b8424b0000000 mov rax,qword ptr [rsp+0B0h]fffff802`68ac9fa1 4885c0 test rax,raxfffff802`68ac9fa4 0f859a801900 jne nt!MmCopyVirtualMemory+0x198394 (fffff802`68c62044)fffff802`68ac9faa 4981fe00020000 cmp r14,200hfffff802`68ac9fb1 0f87f8050000 ja nt!MmCopyVirtualMemory+0x8ff (fffff802`68aca5af)fffff802`68ac9fb7 488d842450020000 lea rax,[rsp+250h]fffff802`68ac9fbf 4889442448 mov qword ptr [rsp+48h],raxfffff802`68ac9fc4 4d8be6 mov r12,r14fffff802`68ac9fc7 4c89a424c8000000 mov qword ptr [rsp+0C8h],r12fffff802`68ac9fcf 4d85f6 test r14,r14fffff802`68ac9fd2 0f8438040000 je nt!MmCopyVirtualMemory+0x760 (fffff802`68aca410)fffff802`68ac9fd8 4d3bf4 cmp r14,r12fffff802`68ac9fdb 0f829a801900 jb nt!MmCopyVirtualMemory+0x1983cb (fffff802`68c6207b)fffff802`68ac9fe1 4c8d842470010000 lea r8,[rsp+170h]fffff802`68ac9fe9 33d2 xor edx,edxfffff802`68ac9feb 488b4c2458 mov rcx,qword ptr [rsp+58h]fffff802`68ac9ff0 e8fbefa6ff call nt!KiStackAttachProcess (fffff802`68538ff0)fffff802`68ac9ff5 4c8b9424a0000000 mov r10,qword ptr [rsp+0A0h]fffff802`68ac9ffd 440fb68c24c8040000 movzx r9d,byte ptr [rsp+4C8h]fffff802`68aca006 4c3bd6 cmp r10,rsifffff802`68aca009 753b jne nt!MmCopyVirtualMemory+0x396 (fffff802`68aca046)fffff802`68aca00b 4584c9 test r9b,r9bfffff802`68aca00e 7436 je nt!MmCopyVirtualMemory+0x396 (fffff802`68aca046)fffff802`68aca010 488b442450 mov rax,qword ptr [rsp+50h]fffff802`68aca015 4885c0 test rax,raxfffff802`68aca018 7422 je nt!MmCopyVirtualMemory+0x38c (fffff802`68aca03c)fffff802`68aca01a 4803c6 add rax,rsifffff802`68aca01d 48b90000ffffff7f0000 mov rcx,7FFFFFFF0000hfffff802`68aca027 483bc1 cmp rax,rcxfffff802`68aca02a 7705 ja nt!MmCopyVirtualMemory+0x381 (fffff802`68aca031)fffff802`68aca02c 483bc6 cmp rax,rsifffff802`68aca02f 730b jae nt!MmCopyVirtualMemory+0x38c (fffff802`68aca03c)fffff802`68aca031 33c0 xor eax,eaxfffff802`68aca033 a20000ffffff7f0000 mov byte ptr [00007FFFFFFF0000h],alfffff802`68aca03c eb08 jmp nt!MmCopyVirtualMemory+0x396 (fffff802`68aca046)fffff802`68aca03e 448bf8 mov r15d,eaxfffff802`68aca041 e93b050000 jmp nt!MmCopyVirtualMemory+0x8d1 (fffff802`68aca581)fffff802`68aca046 448bc3 mov r8d,ebxfffff802`68aca049 41d1e8 shr r8d,1fffff802`68aca04c 4183e001 and r8d,1fffff802`68aca050 0f855e040000 jne nt!MmCopyVirtualMemory+0x804 (fffff802`68aca4b4)fffff802`68aca056 488bbc24f0000000 mov rdi,qword ptr [rsp+0F0h]fffff802`68aca05e 4883c774 add rdi,74hfffff802`68aca062 4889bc24f8000000 mov qword ptr [rsp+0F8h],rdifffff802`68aca06a 0fba2f05 bts dword ptr [rdi],5fffff802`68aca06e 400f92c6 setb silfffff802`68aca072 408874243e mov byte ptr [rsp+3Eh],silfffff802`68aca077 4585c0 test r8d,r8dfffff802`68aca07a 7529 jne nt!MmCopyVirtualMemory+0x3f5 (fffff802`68aca0a5)fffff802`68aca07c f6c340 test bl,40hfffff802`68aca07f 755c jne nt!MmCopyVirtualMemory+0x42d (fffff802`68aca0dd)fffff802`68aca081 8bc3 mov eax,ebxfffff802`68aca083 c1e802 shr eax,2fffff802`68aca086 83e003 and eax,3fffff802`68aca089 83f802 cmp eax,2fffff802`68aca08c 744f je nt!MmCopyVirtualMemory+0x42d (fffff802`68aca0dd)fffff802`68aca08e 4d8bc4 mov r8,r12fffff802`68aca091 83f801 cmp eax,1fffff802`68aca094 7425 je nt!MmCopyVirtualMemory+0x40b (fffff802`68aca0bb)fffff802`68aca096 498bd2 mov rdx,r10fffff802`68aca099 488b4c2448 mov rcx,qword ptr [rsp+48h]fffff802`68aca09e e89d11bbff call nt!memcpy (fffff802`6867b240)fffff802`68aca0a3 eb66 jmp nt!MmCopyVirtualMemory+0x45b (fffff802`68aca10b)fffff802`68aca0a5 4533c0 xor r8d,r8dfffff802`68aca0a8 410fb6d1 movzx edx,r9bfffff802`68aca0ac 488d8c24a0010000 lea rcx,[rsp+1A0h]fffff802`68aca0b4 e8a7cda6ff call nt!MmProbeAndLockPages (fffff802`68536e60)fffff802`68aca0b9 eb50 jmp nt!MmCopyVirtualMemory+0x45b (fffff802`68aca10b)fffff802`68aca0bb 488d842480000000 lea rax,[rsp+80h]fffff802`68aca0c3 4889442420 mov qword ptr [rsp+20h],raxfffff802`68aca0c8 41b901000000 mov r9d,1fffff802`68aca0ce 488b542448 mov rdx,qword ptr [rsp+48h]fffff802`68aca0d3 498bca mov rcx,r10fffff802`68aca0d6 e8c5202700 call nt!MiDbgReadWriteEnclave (fffff802`68d3c1a0)fffff802`68aca0db eb27 jmp nt!MmCopyVirtualMemory+0x454 (fffff802`68aca104)fffff802`68aca0dd 488d842480000000 lea rax,[rsp+80h]fffff802`68aca0e5 4889442428 mov qword ptr [rsp+28h],raxfffff802`68aca0ea c644242001 mov byte ptr [rsp+20h],1fffff802`68aca0ef 4d8bcc mov r9,r12fffff802`68aca0f2 4c8b442448 mov r8,qword ptr [rsp+48h]fffff802`68aca0f7 498bd2 mov rdx,r10fffff802`68aca0fa 488b4c2458 mov rcx,qword ptr [rsp+58h]fffff802`68aca0ff e898022300 call nt!VslDebugReadWriteSecureProcess (fffff802`68cfa39c)fffff802`68aca104 89442438 mov dword ptr [rsp+38h],eaxfffff802`68aca108 448bf8 mov r15d,eaxfffff802`68aca10b eb5f jmp nt!MmCopyVirtualMemory+0x4bc (fffff802`68aca16c)fffff802`68aca10d 448bf8 mov r15d,eaxfffff802`68aca110 89442438 mov dword ptr [rsp+38h],eaxfffff802`68aca114 4533ed xor r13d,r13dfffff802`68aca117 8b5c2430 mov ebx,dword ptr [rsp+30h]fffff802`68aca11b 4c8b742470 mov r14,qword ptr [rsp+70h]fffff802`68aca120 4c8ba424c8000000 mov r12,qword ptr [rsp+0C8h]fffff802`68aca128 0fb674243e movzx esi,byte ptr [rsp+3Eh]fffff802`68aca12d 488bbc24f8000000 mov rdi,qword ptr [rsp+0F8h]fffff802`68aca135 488b8424d0000000 mov rax,qword ptr [rsp+0D0h]fffff802`68aca13d 4889442460 mov qword ptr [rsp+60h],raxfffff802`68aca142 488b8424d8000000 mov rax,qword ptr [rsp+0D8h]fffff802`68aca14a 4889442468 mov qword ptr [rsp+68h],raxfffff802`68aca14f 488b8424c0000000 mov rax,qword ptr [rsp+0C0h]fffff802`68aca157 4889842488000000 mov qword ptr [rsp+88h],raxfffff802`68aca15f 488b8424e0000000 mov rax,qword ptr [rsp+0E0h]fffff802`68aca167 4889442458 mov qword ptr [rsp+58h],raxfffff802`68aca16c 4084f6 test sil,silfffff802`68aca16f 7504 jne nt!MmCopyVirtualMemory+0x4c5 (fffff802`68aca175)fffff802`68aca171 0fba3705 btr dword ptr [rdi],5fffff802`68aca175 4585ff test r15d,r15dfffff802`68aca178 0f88e1030000 js nt!MmCopyVirtualMemory+0x8af (fffff802`68aca55f)fffff802`68aca17e 8bfb mov edi,ebxfffff802`68aca180 d1ef shr edi,1fffff802`68aca182 83e701 and edi,1fffff802`68aca185 0f858e030000 jne nt!MmCopyVirtualMemory+0x869 (fffff802`68aca519)fffff802`68aca18b 488b742448 mov rsi,qword ptr [rsp+48h]fffff802`68aca190 33d2 xor edx,edxfffff802`68aca192 488d8c2470010000 lea rcx,[rsp+170h]fffff802`68aca19a e8f1e9a6ff call nt!KiUnstackDetachProcess (fffff802`68538b90)fffff802`68aca19f 4c8d842470010000 lea r8,[rsp+170h]fffff802`68aca1a7 33d2 xor edx,edxfffff802`68aca1a9 4c8b7c2468 mov r15,qword ptr [rsp+68h]fffff802`68aca1ae 498bcf mov rcx,r15fffff802`68aca1b1 e83aeea6ff call nt!KiStackAttachProcess (fffff802`68538ff0)fffff802`68aca1b6 488b8424a0000000 mov rax,qword ptr [rsp+0A0h]fffff802`68aca1be 80bc24c804000000 cmp byte ptr [rsp+4C8h],0fffff802`68aca1c6 7459 je nt!MmCopyVirtualMemory+0x571 (fffff802`68aca221)fffff802`68aca1c8 483b442460 cmp rax,qword ptr [rsp+60h]fffff802`68aca1cd 7552 jne nt!MmCopyVirtualMemory+0x571 (fffff802`68aca221)fffff802`68aca1cf 488b442450 mov rax,qword ptr [rsp+50h]fffff802`68aca1d4 4885c0 test rax,raxfffff802`68aca1d7 742a je nt!MmCopyVirtualMemory+0x553 (fffff802`68aca203)fffff802`68aca1d9 488b8c2488000000 mov rcx,qword ptr [rsp+88h]fffff802`68aca1e1 4803c1 add rax,rcxfffff802`68aca1e4 48ba0000ffffff7f0000 mov rdx,7FFFFFFF0000hfffff802`68aca1ee 483bc2 cmp rax,rdxfffff802`68aca1f1 7705 ja nt!MmCopyVirtualMemory+0x548 (fffff802`68aca1f8)fffff802`68aca1f3 483bc1 cmp rax,rcxfffff802`68aca1f6 730b jae nt!MmCopyVirtualMemory+0x553 (fffff802`68aca203)fffff802`68aca1f8 33c0 xor eax,eaxfffff802`68aca1fa a20000ffffff7f0000 mov byte ptr [00007FFFFFFF0000h],alfffff802`68aca203 eb1c jmp nt!MmCopyVirtualMemory+0x571 (fffff802`68aca221)fffff802`68aca205 448bf8 mov r15d,eaxfffff802`68aca208 f644243002 test byte ptr [rsp+30h],2fffff802`68aca20d 740d je nt!MmCopyVirtualMemory+0x56c (fffff802`68aca21c)fffff802`68aca20f 488b8c2400010000 mov rcx,qword ptr [rsp+100h]fffff802`68aca217 e8447fa2ff call nt!MmUnlockPages (fffff802`684f2160)fffff802`68aca21c e960030000 jmp nt!MmCopyVirtualMemory+0x8d1 (fffff802`68aca581)fffff802`68aca221 84db test bl,blfffff802`68aca223 7876 js nt!MmCopyVirtualMemory+0x5eb (fffff802`68aca29b)fffff802`68aca225 8bc3 mov eax,ebxfffff802`68aca227 c1e804 shr eax,4fffff802`68aca22a 83e003 and eax,3fffff802`68aca22d 83f802 cmp eax,2fffff802`68aca230 7469 je nt!MmCopyVirtualMemory+0x5eb (fffff802`68aca29b)fffff802`68aca232 4d8bc4 mov r8,r12fffff802`68aca235 83f801 cmp eax,1fffff802`68aca238 743a je nt!MmCopyVirtualMemory+0x5c4 (fffff802`68aca274)fffff802`68aca23a 488bd6 mov rdx,rsifffff802`68aca23d 488bb424a8000000 mov rsi,qword ptr [rsp+0A8h]fffff802`68aca245 488bce mov rcx,rsifffff802`68aca248 e8f30fbbff call nt!memcpy (fffff802`6867b240)fffff802`68aca24d 458bfd mov r15d,r13dfffff802`68aca250 44896c2438 mov dword ptr [rsp+38h],r13dfffff802`68aca255 4c89a42480000000 mov qword ptr [rsp+80h],r12fffff802`68aca25d 4181ff050000c0 cmp r15d,0C0000005hfffff802`68aca264 746b je nt!MmCopyVirtualMemory+0x621 (fffff802`68aca2d1)fffff802`68aca266 4585ff test r15d,r15dfffff802`68aca269 0f8890000000 js nt!MmCopyVirtualMemory+0x64f (fffff802`68aca2ff)fffff802`68aca26f e990000000 jmp nt!MmCopyVirtualMemory+0x654 (fffff802`68aca304)fffff802`68aca274 488d842480000000 lea rax,[rsp+80h]fffff802`68aca27c 4889442420 mov qword ptr [rsp+20h],raxfffff802`68aca281 4533c9 xor r9d,r9dfffff802`68aca284 488b542448 mov rdx,qword ptr [rsp+48h]fffff802`68aca289 488bb424a8000000 mov rsi,qword ptr [rsp+0A8h]fffff802`68aca291 488bce mov rcx,rsifffff802`68aca294 e8071f2700 call nt!MiDbgReadWriteEnclave (fffff802`68d3c1a0)fffff802`68aca299 eb2d jmp nt!MmCopyVirtualMemory+0x618 (fffff802`68aca2c8)fffff802`68aca29b 488d842480000000 lea rax,[rsp+80h]fffff802`68aca2a3 4889442428 mov qword ptr [rsp+28h],raxfffff802`68aca2a8 c644242000 mov byte ptr [rsp+20h],0fffff802`68aca2ad 4d8bcc mov r9,r12fffff802`68aca2b0 4c8b442448 mov r8,qword ptr [rsp+48h]fffff802`68aca2b5 488bb424a8000000 mov rsi,qword ptr [rsp+0A8h]fffff802`68aca2bd 488bd6 mov rdx,rsifffff802`68aca2c0 498bcf mov rcx,r15fffff802`68aca2c3 e8d4002300 call nt!VslDebugReadWriteSecureProcess (fffff802`68cfa39c)fffff802`68aca2c8 89442438 mov dword ptr [rsp+38h],eaxfffff802`68aca2cc 448bf8 mov r15d,eaxfffff802`68aca2cf eb8c jmp nt!MmCopyVirtualMemory+0x5ad (fffff802`68aca25d)fffff802`68aca2d1 488b8c2480000000 mov rcx,qword ptr [rsp+80h]fffff802`68aca2d9 482b8c2488000000 sub rcx,qword ptr [rsp+88h]fffff802`68aca2e1 4803ce add rcx,rsifffff802`68aca2e4 488b842490000000 mov rax,qword ptr [rsp+90h]fffff802`68aca2ec 488908 mov qword ptr [rax],rcxfffff802`68aca2ef 41bf0d000080 mov r15d,8000000Dhfffff802`68aca2f5 44897c2438 mov dword ptr [rsp+38h],r15dfffff802`68aca2fa e982020000 jmp nt!MmCopyVirtualMemory+0x8d1 (fffff802`68aca581)fffff802`68aca2ff e97d020000 jmp nt!MmCopyVirtualMemory+0x8d1 (fffff802`68aca581)fffff802`68aca304 e9be000000 jmp nt!MmCopyVirtualMemory+0x717 (fffff802`68aca3c7)fffff802`68aca309 8b5c2430 mov ebx,dword ptr [rsp+30h]fffff802`68aca30d f6c302 test bl,2fffff802`68aca310 7476 je nt!MmCopyVirtualMemory+0x6d8 (fffff802`68aca388)fffff802`68aca312 488d8c24a0010000 lea rcx,[rsp+1A0h]fffff802`68aca31a e8417ea2ff call nt!MmUnlockPages (fffff802`684f2160)fffff802`68aca31f 83e3fd and ebx,0FFFFFFFDhfffff802`68aca322 895c2430 mov dword ptr [rsp+30h],ebxfffff802`68aca326 33d2 xor edx,edxfffff802`68aca328 488d8c2470010000 lea rcx,[rsp+170h]fffff802`68aca330 e85be8a6ff call nt!KiUnstackDetachProcess (fffff802`68538b90)fffff802`68aca335 4533ed xor r13d,r13dfffff802`68aca338 448b7c2438 mov r15d,dword ptr [rsp+38h]fffff802`68aca33d 4c8b742470 mov r14,qword ptr [rsp+70h]fffff802`68aca342 488bb424d0000000 mov rsi,qword ptr [rsp+0D0h]fffff802`68aca34a 4889742460 mov qword ptr [rsp+60h],rsifffff802`68aca34f 488b8424d8000000 mov rax,qword ptr [rsp+0D8h]fffff802`68aca357 4889442468 mov qword ptr [rsp+68h],raxfffff802`68aca35c 488b8424c0000000 mov rax,qword ptr [rsp+0C0h]fffff802`68aca364 4889842488000000 mov qword ptr [rsp+88h],raxfffff802`68aca36c 488b8424e0000000 mov rax,qword ptr [rsp+0E0h]fffff802`68aca374 4889442458 mov qword ptr [rsp+58h],raxfffff802`68aca379 488b4c2450 mov rcx,qword ptr [rsp+50h]fffff802`68aca37e 488b542440 mov rdx,qword ptr [rsp+40h]fffff802`68aca383 e9fdfbffff jmp nt!MmCopyVirtualMemory+0x2d5 (fffff802`68ac9f85)fffff802`68aca388 488b442450 mov rax,qword ptr [rsp+50h]fffff802`68aca38d 482b442470 sub rax,qword ptr [rsp+70h]fffff802`68aca392 488b8c2490000000 mov rcx,qword ptr [rsp+90h]fffff802`68aca39a 488901 mov qword ptr [rcx],raxfffff802`68aca39d 837c247801 cmp dword ptr [rsp+78h],1fffff802`68aca3a2 7513 jne nt!MmCopyVirtualMemory+0x707 (fffff802`68aca3b7)fffff802`68aca3a4 488b8424e8000000 mov rax,qword ptr [rsp+0E8h]fffff802`68aca3ac 482b8424c0000000 sub rax,qword ptr [rsp+0C0h]fffff802`68aca3b4 488901 mov qword ptr [rcx],raxfffff802`68aca3b7 41bf0d000080 mov r15d,8000000Dhfffff802`68aca3bd 44897c2438 mov dword ptr [rsp+38h],r15dfffff802`68aca3c2 e9ba010000 jmp nt!MmCopyVirtualMemory+0x8d1 (fffff802`68aca581)fffff802`68aca3c7 33d2 xor edx,edxfffff802`68aca3c9 488d8c2470010000 lea rcx,[rsp+170h]fffff802`68aca3d1 e8bae7a6ff call nt!KiUnstackDetachProcess (fffff802`68538b90)fffff802`68aca3d6 85ff test edi,edifffff802`68aca3d8 0f856f010000 jne nt!MmCopyVirtualMemory+0x89d (fffff802`68aca54d)fffff802`68aca3de 4d2bf4 sub r14,r12fffff802`68aca3e1 4c89742470 mov qword ptr [rsp+70h],r14fffff802`68aca3e6 488b542440 mov rdx,qword ptr [rsp+40h]fffff802`68aca3eb 492bd4 sub rdx,r12fffff802`68aca3ee 4889542440 mov qword ptr [rsp+40h],rdxfffff802`68aca3f3 4c01a424a0000000 add qword ptr [rsp+0A0h],r12fffff802`68aca3fb 4903f4 add rsi,r12fffff802`68aca3fe 4889b424a8000000 mov qword ptr [rsp+0A8h],rsifffff802`68aca406 488b742460 mov rsi,qword ptr [rsp+60h]fffff802`68aca40b e9bffbffff jmp nt!MmCopyVirtualMemory+0x31f (fffff802`68ac9fcf)fffff802`68aca410 4885d2 test rdx,rdxfffff802`68aca413 4c8b742458 mov r14,qword ptr [rsp+58h]fffff802`68aca418 4c8b7c2468 mov r15,qword ptr [rsp+68h]fffff802`68aca41d 0f85cd771900 jne nt!MmCopyVirtualMemory+0x197f40 (fffff802`68c61bf0)fffff802`68aca423 4883bc24b000000000 cmp qword ptr [rsp+0B0h],0fffff802`68aca42c 0f856c7c1900 jne nt!MmCopyVirtualMemory+0x1983ee (fffff802`68c6209e)fffff802`68aca432 488b842490000000 mov rax,qword ptr [rsp+90h]fffff802`68aca43a 488b4c2450 mov rcx,qword ptr [rsp+50h]fffff802`68aca43f 488908 mov qword ptr [rax],rcxfffff802`68aca442 33c0 xor eax,eaxfffff802`68aca444 488b8c2450040000 mov rcx,qword ptr [rsp+450h]fffff802`68aca44c 4833cc xor rcx,rspfffff802`68aca44f e82c90b7ff call nt!_security_check_cookie (fffff802`68643480)fffff802`68aca454 4881c460040000 add rsp,460hfffff802`68aca45b 415f pop r15fffff802`68aca45d 415e pop r14fffff802`68aca45f 415d pop r13fffff802`68aca461 415c pop r12fffff802`68aca463 5f pop rdifffff802`68aca464 5e pop rsifffff802`68aca465 5b pop rbxfffff802`68aca466 c3 retfffff802`68aca467 4c8d842440010000 lea r8,[rsp+140h]fffff802`68aca46f 33d2 xor edx,edxfffff802`68aca471 488bcf mov rcx,rdifffff802`68aca474 e877eba6ff call nt!KiStackAttachProcess (fffff802`68538ff0)fffff802`68aca479 e974faffff jmp nt!MmCopyVirtualMemory+0x242 (fffff802`68ac9ef2)fffff802`68aca47e 33d2 xor edx,edxfffff802`68aca480 488d8c2440010000 lea rcx,[rsp+140h]fffff802`68aca488 e803e7a6ff call nt!KiUnstackDetachProcess (fffff802`68538b90)fffff802`68aca48d 488b542440 mov rdx,qword ptr [rsp+40h]fffff802`68aca492 e993faffff jmp nt!MmCopyVirtualMemory+0x27a (fffff802`68ac9f2a)fffff802`68aca497 f6c302 test bl,2fffff802`68aca49a 0f84f2faffff je nt!MmCopyVirtualMemory+0x2e2 (fffff802`68ac9f92)fffff802`68aca4a0 41bc00e00000 mov r12d,0E000hfffff802`68aca4a6 493bcc cmp rcx,r12fffff802`68aca4a9 0f8615fbffff jbe nt!MmCopyVirtualMemory+0x314 (fffff802`68ac9fc4)fffff802`68aca4af e913fbffff jmp nt!MmCopyVirtualMemory+0x317 (fffff802`68ac9fc7)fffff802`68aca4b4 4c89ac24a0010000 mov qword ptr [rsp+1A0h],r13fffff802`68aca4bc 418bd2 mov edx,r10dfffff802`68aca4bf 8bca mov ecx,edxfffff802`68aca4c1 81e1ff0f0000 and ecx,0FFFhfffff802`68aca4c7 4881c1ff0f0000 add rcx,0FFFhfffff802`68aca4ce 4903cc add rcx,r12fffff802`68aca4d1 48c1e90c shr rcx,0Chfffff802`68aca4d5 6683c106 add cx,6fffff802`68aca4d9 66c1e103 shl cx,3fffff802`68aca4dd 66898c24a8010000 mov word ptr [rsp+1A8h],cxfffff802`68aca4e5 664489ac24aa010000 mov word ptr [rsp+1AAh],r13wfffff802`68aca4ee 498bc2 mov rax,r10fffff802`68aca4f1 482500f0ffff and rax,0FFFFFFFFFFFFF000hfffff802`68aca4f7 48898424c0010000 mov qword ptr [rsp+1C0h],raxfffff802`68aca4ff 81e2ff0f0000 and edx,0FFFhfffff802`68aca505 899424cc010000 mov dword ptr [rsp+1CCh],edxfffff802`68aca50c 4489a424c8010000 mov dword ptr [rsp+1C8h],r12dfffff802`68aca514 e93dfbffff jmp nt!MmCopyVirtualMemory+0x3a6 (fffff802`68aca056)fffff802`68aca519 c7442428200000c0 mov dword ptr [rsp+28h],0C0000020hfffff802`68aca521 44896c2420 mov dword ptr [rsp+20h],r13dfffff802`68aca526 4533c9 xor r9d,r9dfffff802`68aca529 33d2 xor edx,edxfffff802`68aca52b 458d4101 lea r8d,[r9+1]fffff802`68aca52f 488d8c24a0010000 lea rcx,[rsp+1A0h]fffff802`68aca537 e854c79fff call nt!MmMapLockedPagesSpecifyCache (fffff802`684c6c90)fffff802`68aca53c 488bf0 mov rsi,raxfffff802`68aca53f 4885c0 test rax,raxfffff802`68aca542 0f8548fcffff jne nt!MmCopyVirtualMemory+0x4e0 (fffff802`68aca190)fffff802`68aca548 e93e7b1900 jmp nt!MmCopyVirtualMemory+0x1983db (fffff802`68c6208b)fffff802`68aca54d 488d8c24a0010000 lea rcx,[rsp+1A0h]fffff802`68aca555 e8067ca2ff call nt!MmUnlockPages (fffff802`684f2160)fffff802`68aca55a e97ffeffff jmp nt!MmCopyVirtualMemory+0x72e (fffff802`68aca3de)fffff802`68aca55f f6c302 test bl,2fffff802`68aca562 0f858b000000 jne nt!MmCopyVirtualMemory+0x943 (fffff802`68aca5f3)fffff802`68aca568 488b4c2450 mov rcx,qword ptr [rsp+50h]fffff802`68aca56d 492bce sub rcx,r14fffff802`68aca570 488b842490000000 mov rax,qword ptr [rsp+90h]fffff802`68aca578 488908 mov qword ptr [rax],rcxfffff802`68aca57b 41bf0d000080 mov r15d,8000000Dhfffff802`68aca581 33d2 xor edx,edxfffff802`68aca583 488d8c2470010000 lea rcx,[rsp+170h]fffff802`68aca58b e800e6a6ff call nt!KiUnstackDetachProcess (fffff802`68538b90)fffff802`68aca590 4883bc24b000000000 cmp qword ptr [rsp+0B0h],0fffff802`68aca599 740c je nt!MmCopyVirtualMemory+0x8f7 (fffff802`68aca5a7)fffff802`68aca59b 33d2 xor edx,edxfffff802`68aca59d 488b4c2448 mov rcx,qword ptr [rsp+48h]fffff802`68aca5a2 e8f9bad4ff call nt!ExFreePool (fffff802`688160a0)fffff802`68aca5a7 418bc7 mov eax,r15dfffff802`68aca5aa e995feffff jmp nt!MmCopyVirtualMemory+0x794 (fffff802`68aca444)fffff802`68aca5af 41bc00000100 mov r12d,10000hfffff802`68aca5b5 493bd4 cmp rdx,r12fffff802`68aca5b8 7703 ja nt!MmCopyVirtualMemory+0x90d (fffff802`68aca5bd)fffff802`68aca5ba 4c8be2 mov r12,rdxfffff802`68aca5bd 41b84d6d5277 mov r8d,77526D4Dhfffff802`68aca5c3 498bd4 mov rdx,r12fffff802`68aca5c6 b901000000 mov ecx,1fffff802`68aca5cb e840bad4ff call nt!ExAllocatePoolWithTag (fffff802`68816010)fffff802`68aca5d0 4889442448 mov qword ptr [rsp+48h],raxfffff802`68aca5d5 4885c0 test rax,raxfffff802`68aca5d8 0f84757a1900 je nt!MmCopyVirtualMemory+0x1983a3 (fffff802`68c62053)fffff802`68aca5de 4c89a424b0000000 mov qword ptr [rsp+0B0h],r12fffff802`68aca5e6 488b542440 mov rdx,qword ptr [rsp+40h]fffff802`68aca5eb 4d3bf4 cmp r14,r12fffff802`68aca5ee e9b6feffff jmp nt!MmCopyVirtualMemory+0x7f9 (fffff802`68aca4a9)fffff802`68aca5f3 83e3fd and ebx,0FFFFFFFDhfffff802`68aca5f6 895c2430 mov dword ptr [rsp+30h],ebxfffff802`68aca5fa 33d2 xor edx,edxfffff802`68aca5fc 488d8c2470010000 lea rcx,[rsp+170h]fffff802`68aca604 e887e5a6ff call nt!KiUnstackDetachProcess (fffff802`68538b90)fffff802`68aca609 488b542440 mov rdx,qword ptr [rsp+40h]fffff802`68aca60e e968f9ffff jmp nt!MmCopyVirtualMemory+0x2cb (fffff802`68ac9f7b)fffff802`68aca613 cc int 3fffff802`68aca614 cc int 3fffff802`68aca615 cc int 3fffff802`68aca616 cc int 3fffff802`68aca617 cc int 3fffff802`68aca618 cc int 3fffff802`68aca619 cc int 3fffff802`68aca61a cc int 3fffff802`68aca61b cc int 3fffff802`68aca61c cc int 3fffff802`68aca61d cc int 3fffff802`68aca61e cc int 3fffff802`68aca61f cc int 3 |
总结 ReadProcessMemory总体路线如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 | kernel32!ReadProcessMemory ↓ntdll!ZwReadVirtualMemory ↓syscall ↓nt!KiSystemCall64 ↓nt!KiSystemServiceRepeat ↓nt!KiSystemServiceStart ↓nt!NtReadVirtualMemory ↓nt!MiReadWriteVirtualMemory ↓nt!MmCopyVirtualMemory →分支1: 直接memcpy() →分支2: Probe + Lock + Map →分支3: VBS / Enclave |
[培训]Windows内核深度攻防:从Hook技术到Rootkit实战!
最后于 2026-1-24 00:30
被mb_binusgki编辑
,原因:
赞赏
他的文章
赞赏
雪币:
留言: